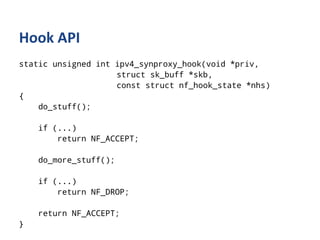
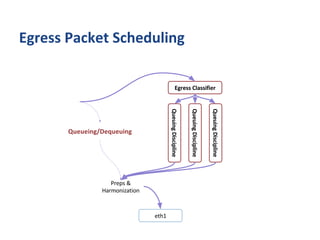
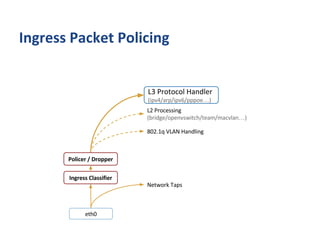
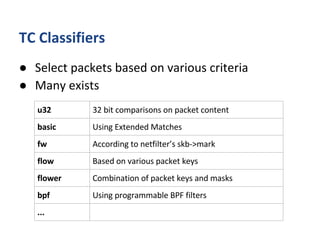
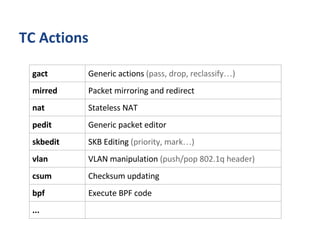
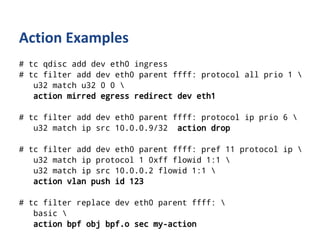
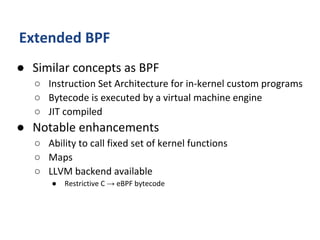
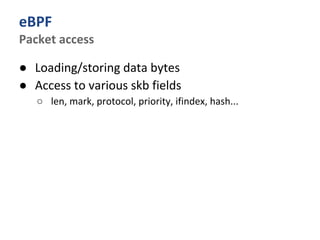
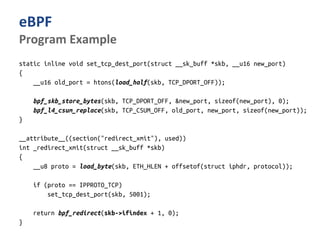
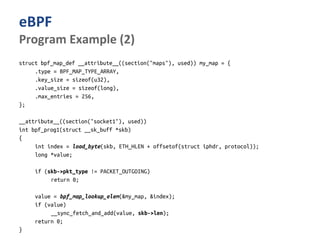
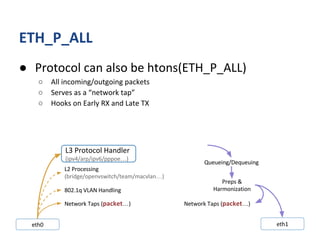
The document outlines various networking concepts and methods in C, specifically related to socket programming and packet filtering in Linux. It includes snippets for setting socket options, registering network hooks, creating filters with Traffic Control (tc), and using BPF (Berkeley Packet Filter) for packet manipulation. Overall, it provides a technical overview of how to interact with network packets at a low level using system calls and kernel functions.








![●
○
●
○
●
○
●
struct sockaddr_ll {
unsigned short sll_family;
unsigned short sll_protocol;
int sll_ifindex;
unsigned short sll_hatype;
unsigned char sll_pkttype;
unsigned char sll_halen;
unsigned char sll_addr[8];
};](https://image.slidesharecdn.com/ktlv-linux-hooking-netstack-160822071909/85/Specializing-the-Data-Path-Hooking-into-the-Linux-Network-Stack-15-320.jpg)
![●
○ setsockopt(s, SOL_SOCKET, SO_ATTACH_FILTER, …)
●
# sudo tcpdump -d arp
(000) ldh [12]
(001) jeq #0x806 jt 2 jf 3
(002) ret #262144
(003) ret #0
# sudo tcpdump -dd arp
{ 0x28, 0, 0, 0x0000000c },
{ 0x15, 0, 1, 0x00000806 },
{ 0x6, 0, 0, 0x00040000 },
{ 0x6, 0, 0, 0x00000000 },](https://image.slidesharecdn.com/ktlv-linux-hooking-netstack-160822071909/85/Specializing-the-Data-Path-Hooking-into-the-Linux-Network-Stack-16-320.jpg)




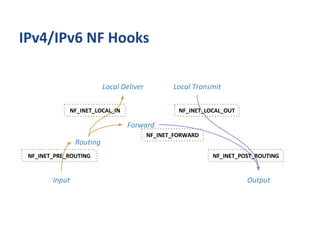


![static struct nf_hook_ops ipv4_synproxy_ops[] = {
{
.hook = ipv4_synproxy_hook,
.pf = NFPROTO_IPV4,
.hooknum = NF_INET_LOCAL_IN,
.priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1,
.priv = NULL,
},
{
.hook = ipv4_synproxy_hook,
.pf = NFPROTO_IPV4,
.hooknum = NF_INET_POST_ROUTING,
.priority = NF_IP_PRI_CONNTRACK_CONFIRM - 1,
.priv = NULL,
},
};](https://image.slidesharecdn.com/ktlv-linux-hooking-netstack-160822071909/85/Specializing-the-Data-Path-Hooking-into-the-Linux-Network-Stack-24-320.jpg)