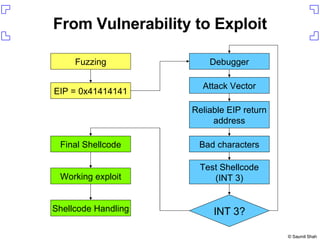
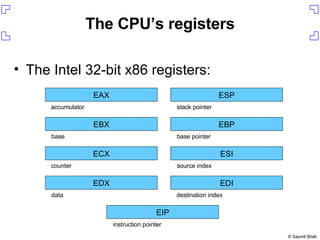
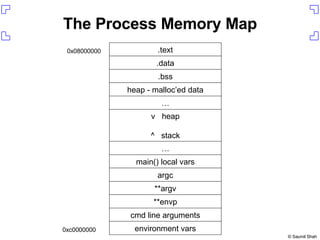
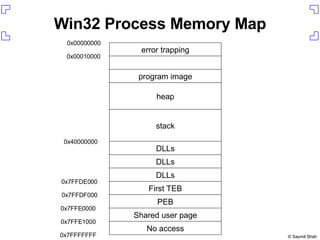
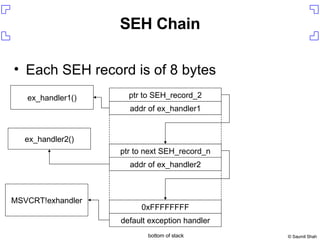
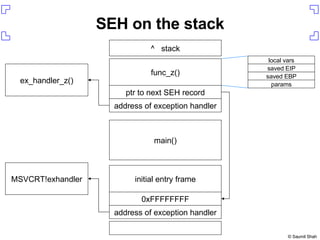
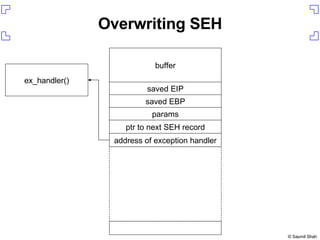
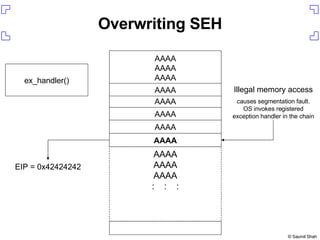
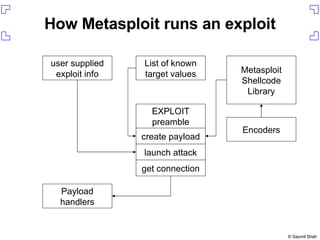
The document discusses exploiting a buffer overflow vulnerability in Internet Explorer's VML implementation (MS06-055) to execute arbitrary code. It describes overwriting the structured exception handler to gain control of the instruction pointer, using heap spraying to load a buffer in memory, and having the instruction pointer jump to the buffer to execute shellcode and spawn a command shell. Metasploit is introduced as an open-source framework for developing exploits.

![Saumil Shah - “krafty” ceo, net-square solutions [email_address] author: “Web Hacking - Attacks and Defense” # who am i # who am i 16:08 up 4:26, 1 user, load averages: 0.28 0.40 0.33 USER TTY FROM LOGIN@ IDLE WHAT saumil console - 11:43 0:05 bash](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-2-320.jpg)

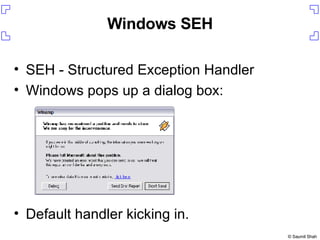
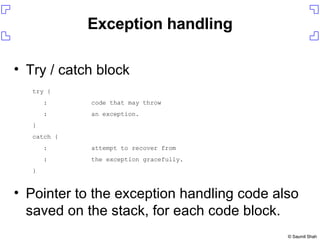
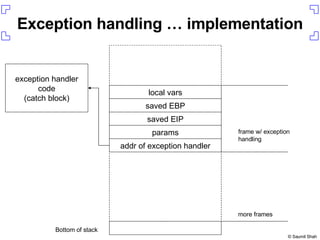
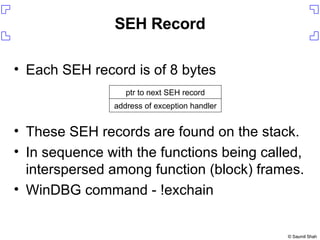


![Setting up the exploit On your host Run daemon.pl to serve up ie_vml1.html On the Windows box start up iexplore start up WinDBG press F6 in WinDBG and attach to iexplore.exe $ ./daemon.pl ie_vml1.html [*] Starting HTTP server on 8080 0:005> gh](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-18-320.jpg)
![Crashing IE Surf to http://192.168.7.xxx:8080/ The SEH record is overwritten. (18c.584): Access violation - code c0000005 (first chance) First chance exceptions are reported before any exception handling. This exception may be expected and handled. eax=0013b4c4 ebx=001df20c ecx=0013b4b8 edx=00004141 esi=0000259e edi=00140000 eip=5deded1e esp=0013b4a0 ebp=0013b6c8 iopl=0 nv up ei pl nz na po nc cs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000206 *** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Program Files\Common Files\Microsoft Shared\VGX\vgx.dll - vgx!$DllMain$_gdiplus+0x30e8d: 5deded1e 668917 mov [edi],dx ds:0023:00140000=6341 0:000> !exchain 0013e420: 41414141 Invalid exception stack at 41414141](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-19-320.jpg)




![Heap Spraying Technique pioneered by Skylined Make a VERY large NOP sled Append shellcode at its end Create multiple instances of this NOP sled in the heap memory using Javascript arrays… a[0] = str; a[1] = str… The heap gets “sprayed” with our payloads. Land somewhere in the NOPs, and you win.](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-24-320.jpg)
![Heap Spraying NOP sled shellcode NOP sled shellcode NOP sled shellcode <script> : spray = build_large_nopsled(); a = new Array(); for(i = 0; i < 100; i++) a[i] = spray + shellcode; : </script> <html> : exploit trigger condition goes here : </html> a[7] a[8] a[9]](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-25-320.jpg)

![ie_vml2 On your host Run daemon.pl to serve up ie_vml2.html On the Windows box start up iexplore start up WinDBG press F6 in WinDBG and attach to iexplore.exe $ ./daemon.pl ie_vml2.html [*] Starting HTTP server on 8080 0:005> gh](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-27-320.jpg)























![Thank You! Saumil Shah [email_address] http://net-square.com +91 98254 31192](https://image.slidesharecdn.com/writing-metasploit-plugins387/85/Writing-Metasploit-Plugins-58-320.jpg)