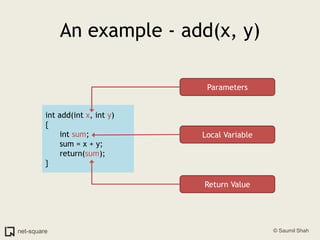
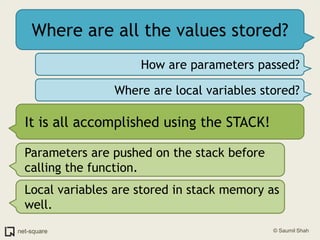
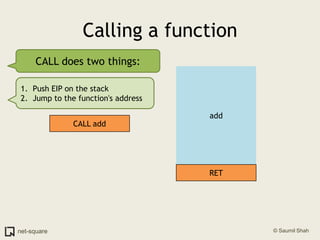
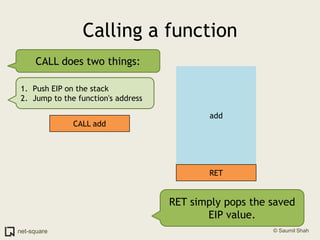
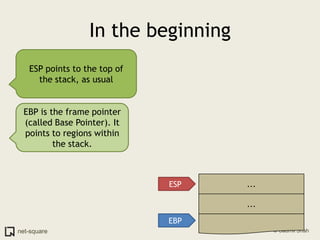
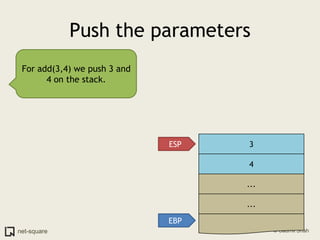
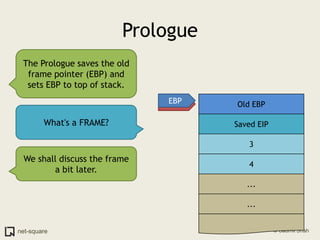
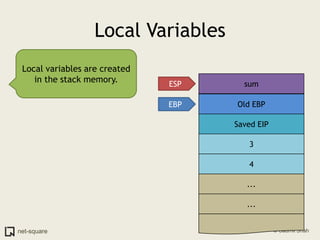
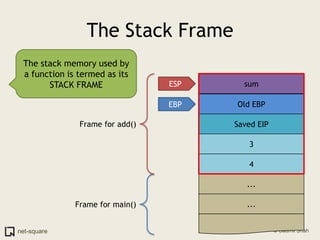
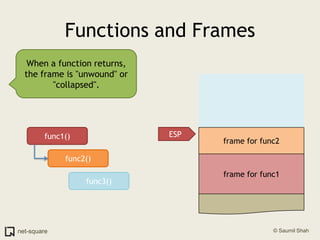
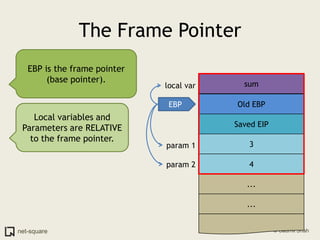
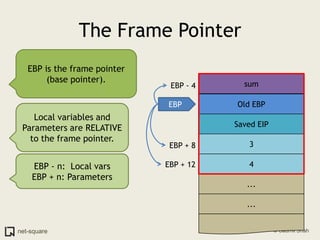
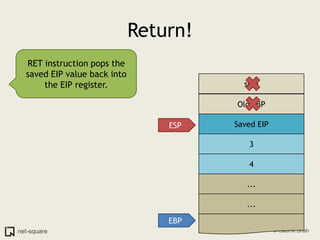
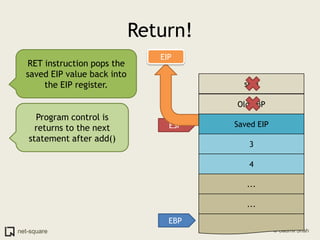
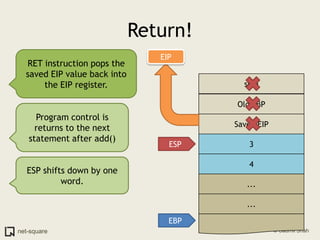
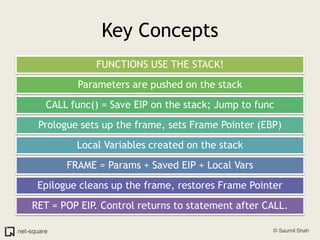
A function is a reusable block of code that can be called from different parts of a program. Functions accept parameters as input and may return a value. When a function is called, its parameters and local variables are stored on the stack. Each function call creates a stack frame that contains its parameters, local variables, and return address. This allows functions to maintain separate variable scopes while sharing the call stack.