Embed presentation
Download to read offline



![Slack Channels --> AWS creds
● slack channel list
● aws s3api list-buckets — query “Buckets[].Name”](https://image.slidesharecdn.com/owningacompanythroughtheirlogs-200717160737/75/Owning-a-company-through-their-logs-8-2048.jpg)




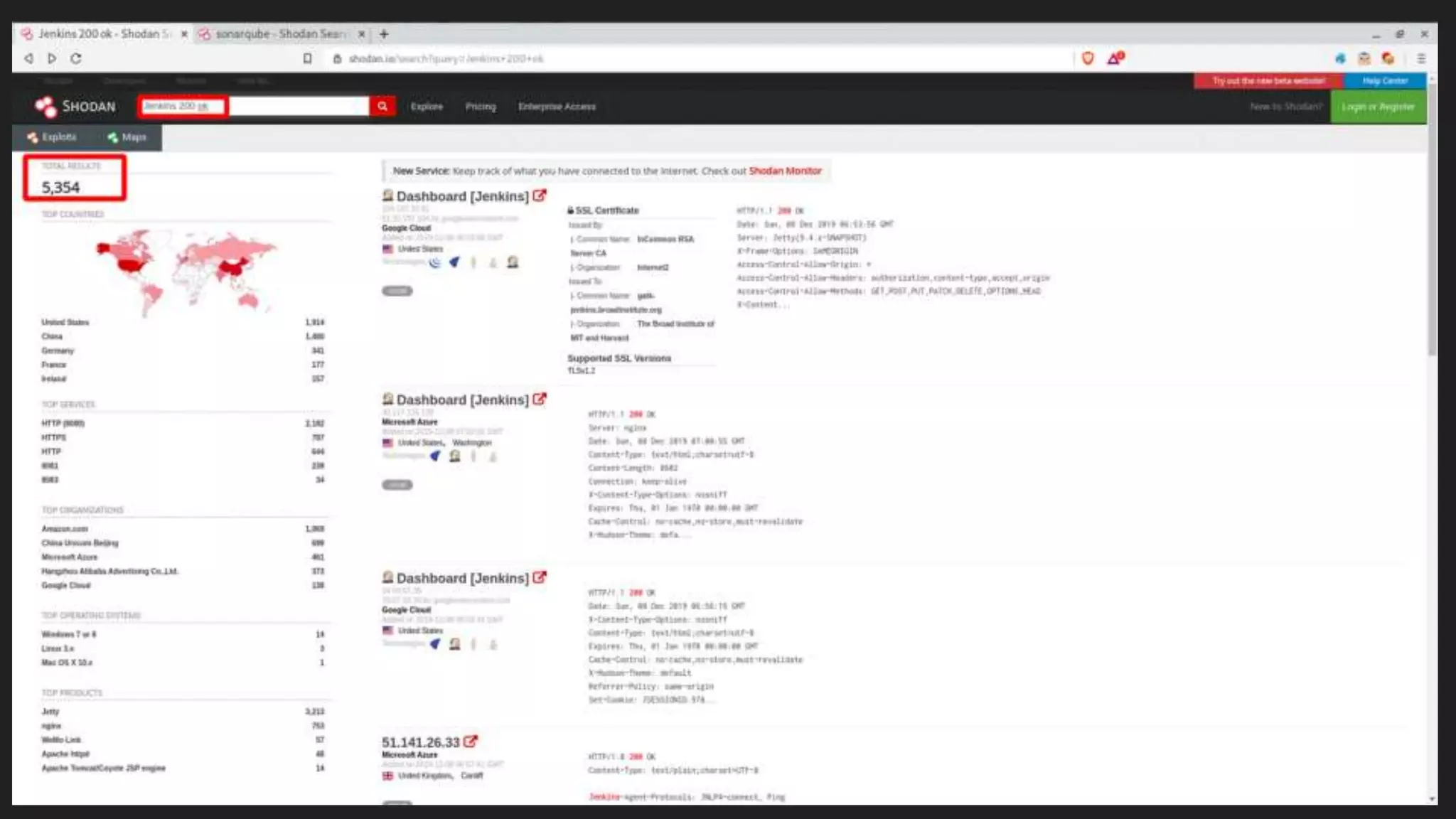
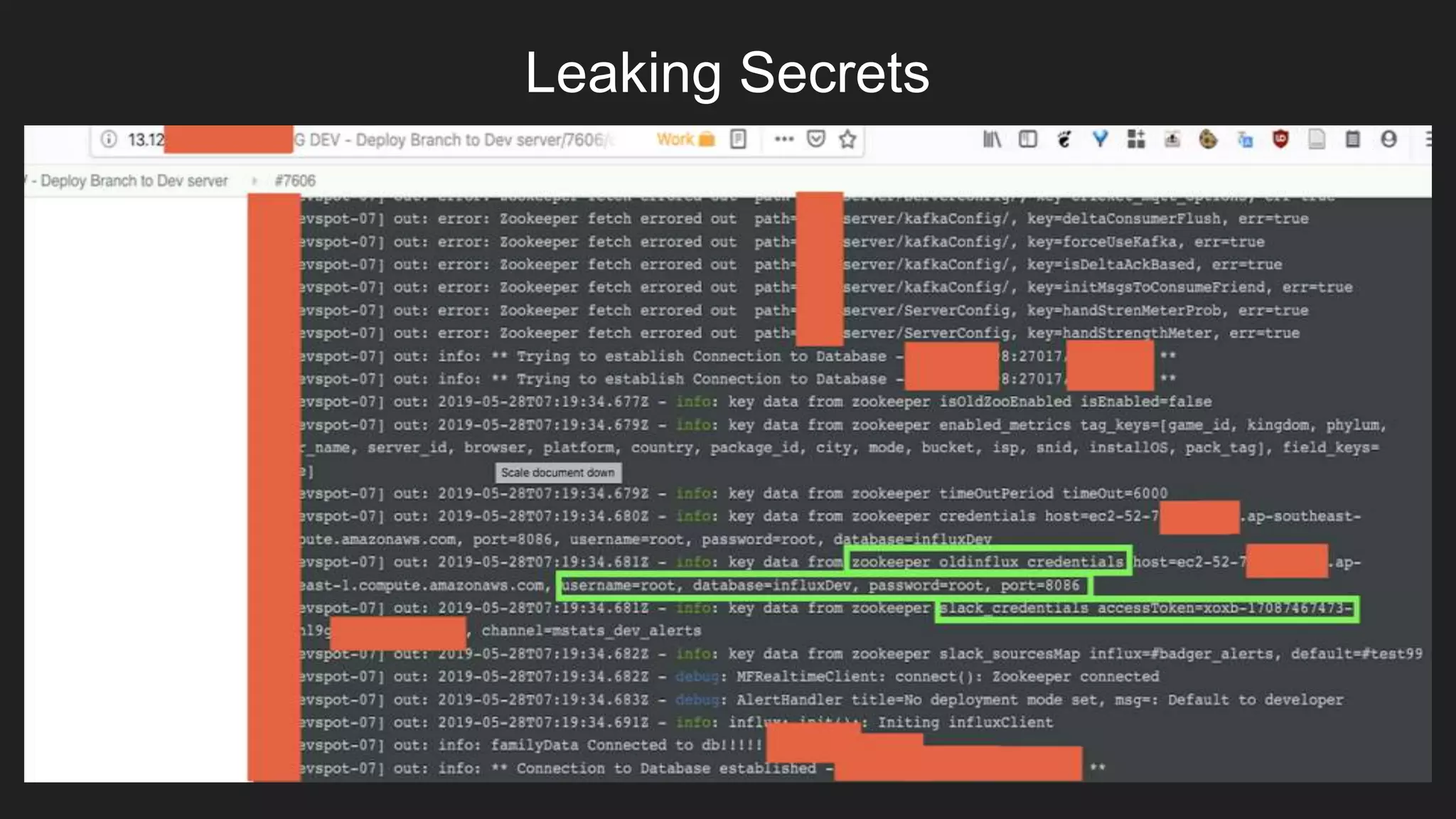
A security engineer discusses how logs and passive reconnaissance can reveal sensitive information like AWS credentials. The engineer searched for open Jenkins and SonarQube instances which led to discovering Slack channels containing AWS access keys. Key lessons are to know your boundaries, automate mundane tasks, don't presume systems mask secrets, and persistence is important in security work.







![Slack Channels --> AWS creds
● slack channel list
● aws s3api list-buckets — query “Buckets[].Name”](https://image.slidesharecdn.com/owningacompanythroughtheirlogs-200717160737/75/Owning-a-company-through-their-logs-8-2048.jpg)


