This document discusses return-oriented programming (ROP) attacks and variants. It begins with an introduction to ROP attacks, explaining that they circumvent data execution prevention by chaining small snippets of executable code (called gadgets) that end in return instructions. It then covers different ROP attack techniques like using arithmetic, comparison, and loop gadgets to achieve Turing completeness. The document discusses challenges like handling null bytes and describes variants like jump-oriented programming (JOP) that uses indirect jumps. It also covers creating alphanumeric ROP shellcode by selecting printable addresses. In the end, it provides tips for effectively searching gadgets.




![ROP attacks
x86 stack layout
. Registers ebp and esp point to base and top of the
stack respective
. EBP used to access local and passed paramters
eg . [ebp + 8] first parameter (EBP + 4) for ret
address
. ESP used are a pointer for popping values out from
stack](https://image.slidesharecdn.com/advanceropattacks-120829002617-phpapp02/85/Advance-ROP-Attacks-5-320.jpg)
![ROP attacks
• RET x86 instruction
• Pops a value from the stack into EIP
• Used to return control from a function
• RET can have a argument eg RET 8
• RET 8 == EIP = stack[top], add ESP , 8](https://image.slidesharecdn.com/advanceropattacks-120829002617-phpapp02/85/Advance-ROP-Attacks-6-320.jpg)




![ROP Basics(load and store gadgets)
• storing and loading values from and into
memory
• Primitive example pop eax; ret / pop ebx ret/ pop r32, ret
• To memory store pop eax, pop edx, ret / mov [eax], edx; ret](https://image.slidesharecdn.com/advanceropattacks-120829002617-phpapp02/85/Advance-ROP-Attacks-11-320.jpg)



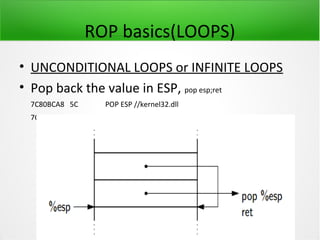
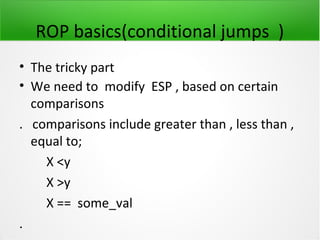
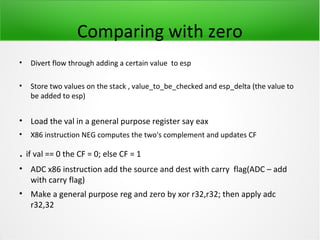
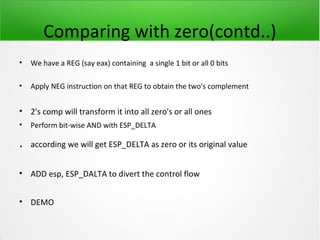



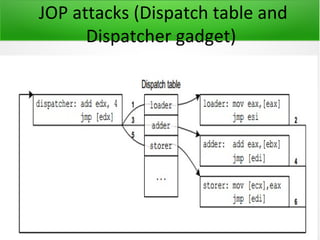
![JUMP oriented Programming
Attacks
• Dispatcher gadget increments a REG by certain value to make it point to next loc to
jump on
• Add ebx, 4 ; JMP [ebx]
• Here , EBX points to the Dispatcher table
• Same gadgets as in ROP attacks](https://image.slidesharecdn.com/advanceropattacks-120829002617-phpapp02/85/Advance-ROP-Attacks-24-320.jpg)



![Alphanumeric ROP
Shellcode(gadgets)
• Gadgets used for decoding addresses should be printable(bytes should be
in range of 0x21 - 0x7e
• We also need a memory region which has a printable address to store the
decoded gadgets addresses marked as r/w
. From reg to mem we have urlmon.dll
0x772C2E5E MOV DWORD PTR DS:[ECX],EAX
. ESP related CRYPTUI.dll 0x775513E30 XCHG EAX,ESP
. MSCTF.DLL 0x74722973 POP EAX
. Mshtml.dll 0x7D504962 ADD EAX,ECX
. msimtf.dll MEM to reg 0x74714263 MOV EAX,DWORD PTR DS:[ECX]
. All of the dll's loaded by internet explorer](https://image.slidesharecdn.com/advanceropattacks-120829002617-phpapp02/85/Advance-ROP-Attacks-29-320.jpg)


