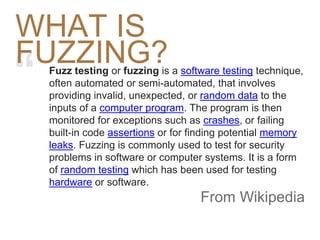
The document is a detailed exploration of reverse engineering and fuzzing techniques related to binary exploitation, including methods for buffer overflows, return-oriented programming, and utilizing the Z3 solver for fuzz testing. It features a self-introduction of a speaker with experience in various hacking contests and tools, emphasizing the importance of understanding low-level programming, memory management, and application vulnerabilities. The text serves as both a tutorial and a set of exam questions on these hacking concepts.





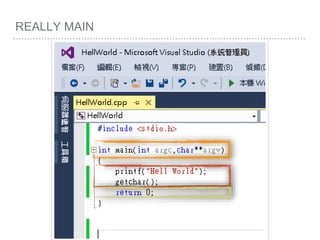
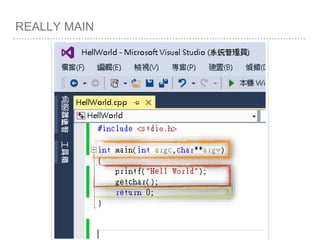
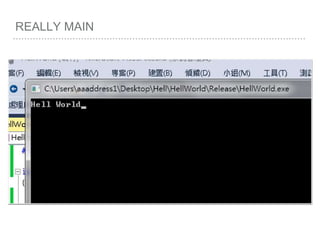
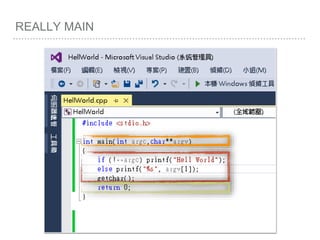
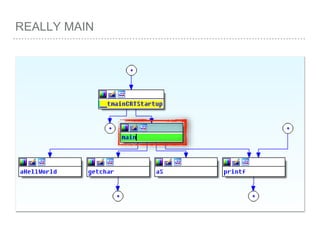
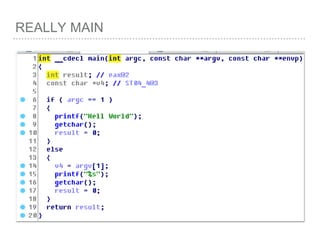
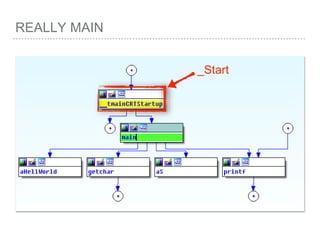
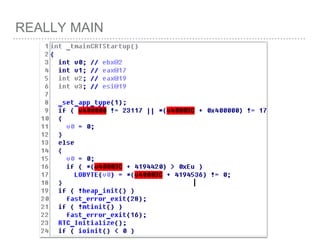





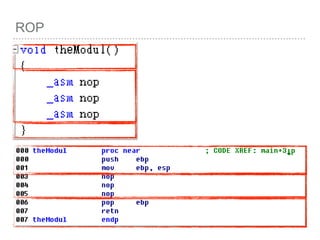
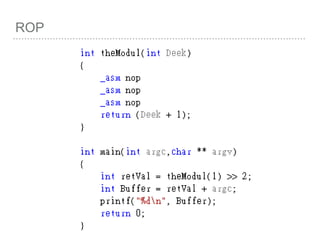
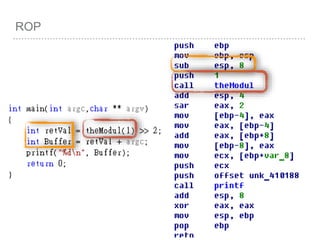
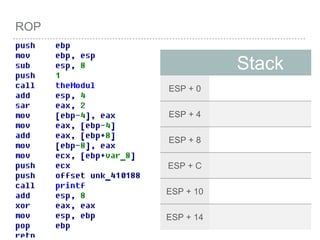
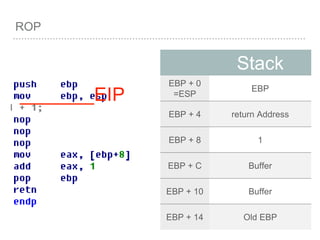
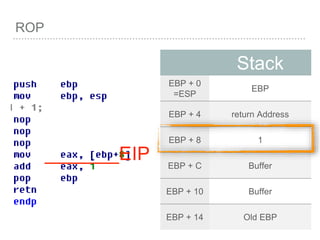
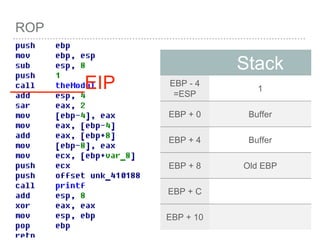
![ROP
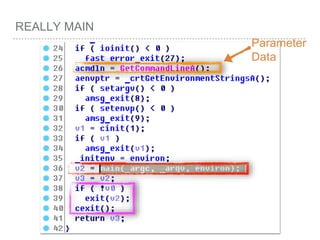
[EBP+0 ] = Pointer to old EBP
[EBP+4 ] = Return Address
[EBP+8 ] = First Parameter
[EBP+C ] = Second Parameter
[EBP+10 ] = Third Parameter
…etc
[EBP+8 + 4*index] =
Parameter[index]](https://image.slidesharecdn.com/2015-151129180103-lva1-app6892/85/NTUSTxTDOH-27-320.jpg)
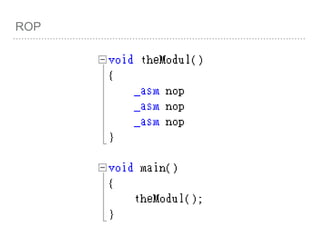
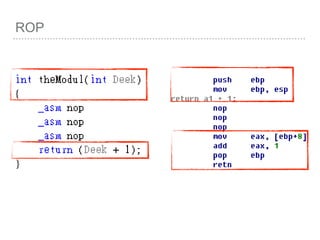
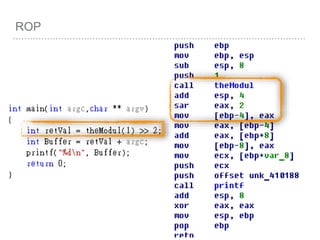
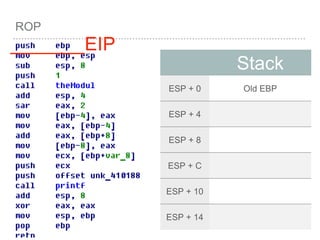
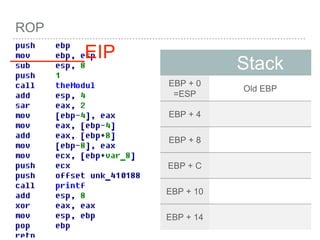
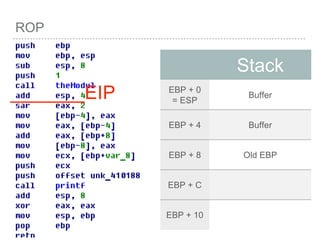
![ROP
VOID
FUNC()
{
INT A =
0;
INT B =
1;
INT C =
2;
[EBP - 4] =0
[EBP - 8] =1
[EBP - C] =2
push EBP
mov
EBP,ESP
SUB ESP,
LEN](https://image.slidesharecdn.com/2015-151129180103-lva1-app6892/85/NTUSTxTDOH-28-320.jpg)
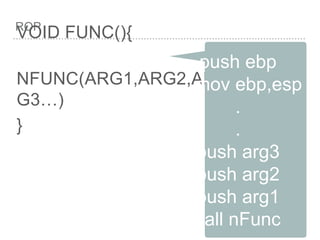
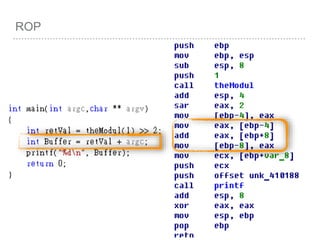
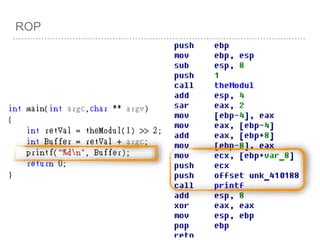

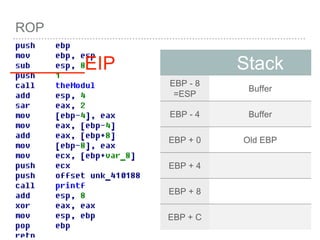
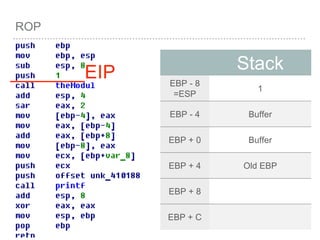
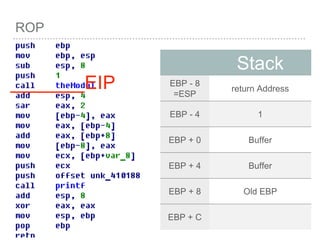
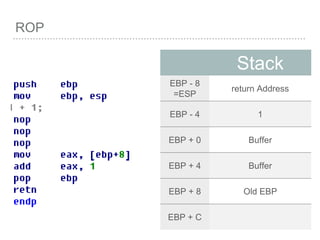
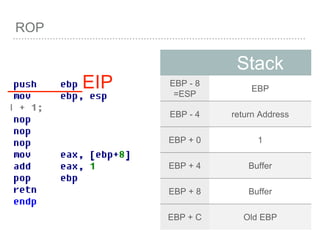
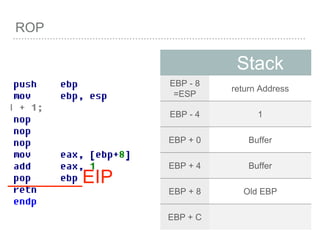
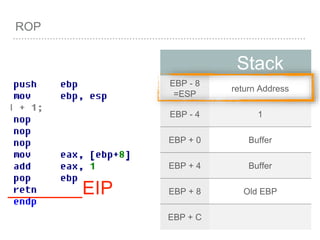


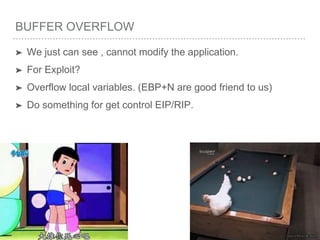
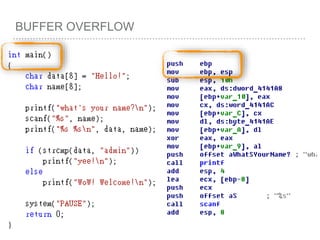
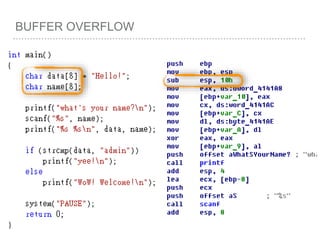
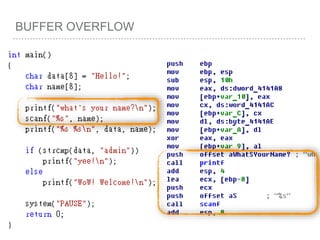
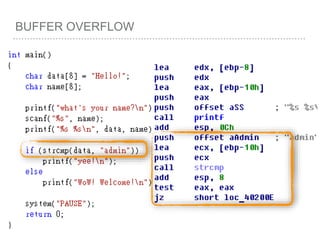
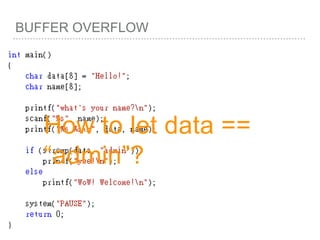
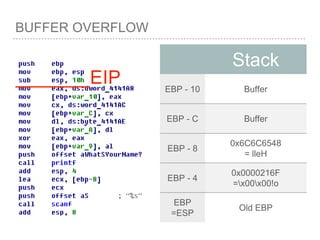
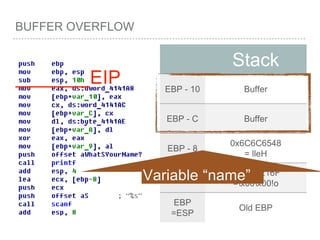
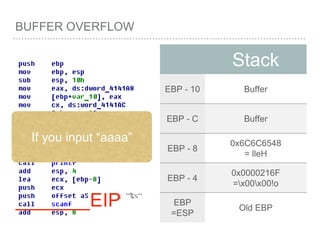
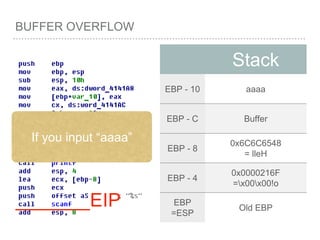
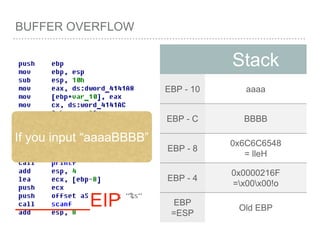
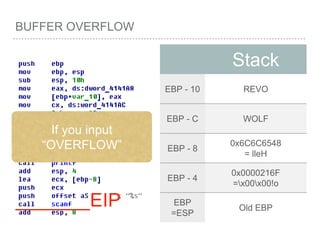
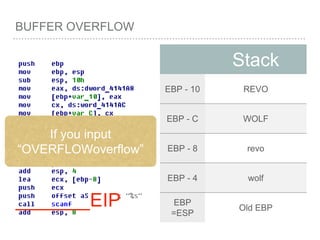
![BUFFER OVERFLOW
[EBP-8]
[EBP-10]](https://image.slidesharecdn.com/2015-151129180103-lva1-app6892/85/NTUSTxTDOH-52-320.jpg)
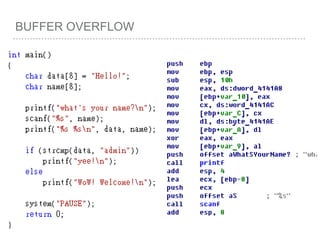
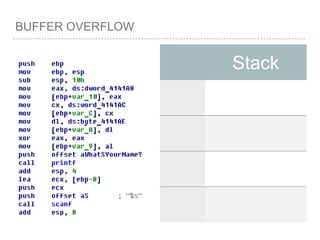
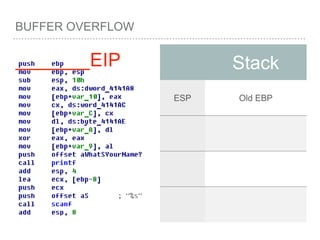
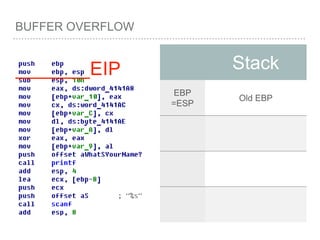
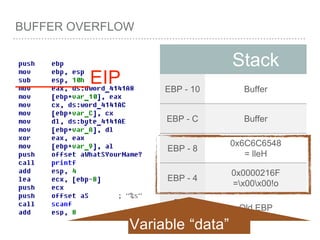
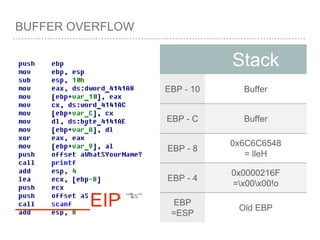
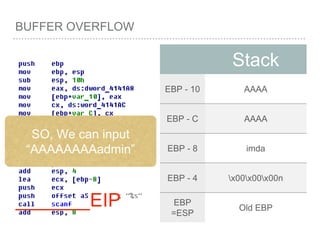
![BUFFER OVERFLOW
[EBP-8]
[EBP-10]](https://image.slidesharecdn.com/2015-151129180103-lva1-app6892/85/NTUSTxTDOH-59-320.jpg)











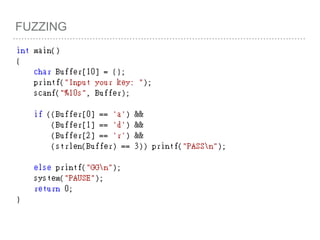
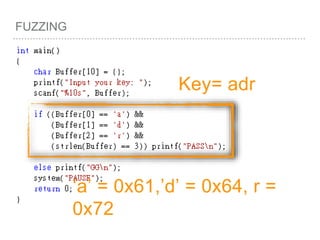
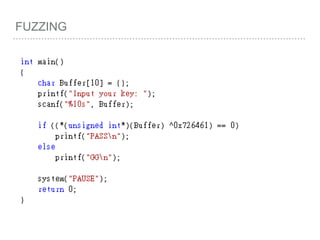
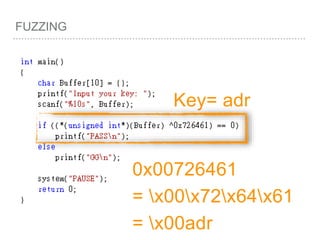
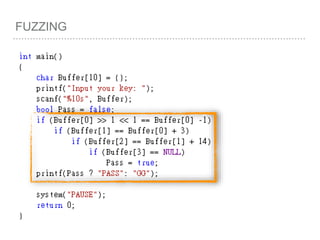

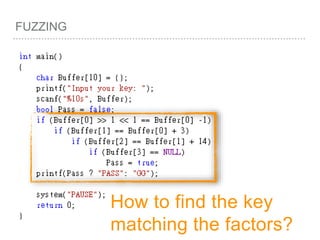


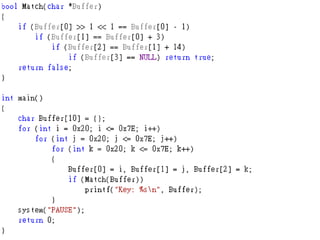
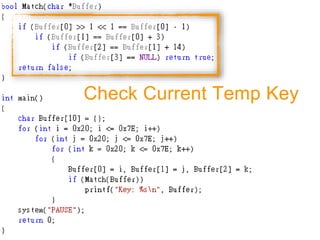
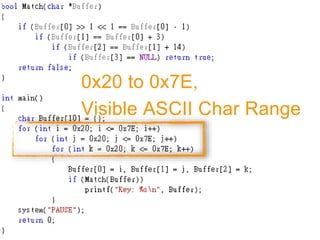
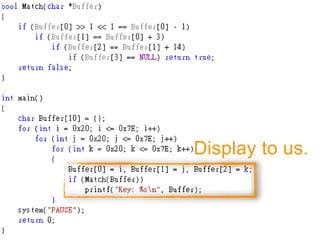
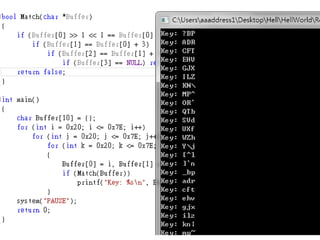




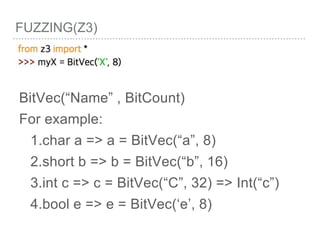
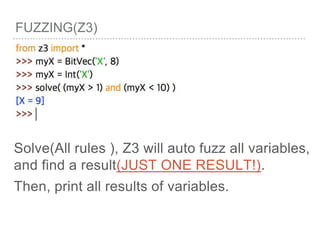
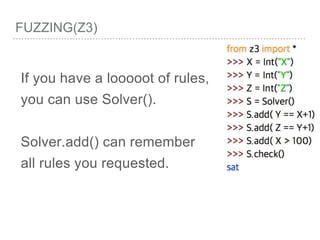
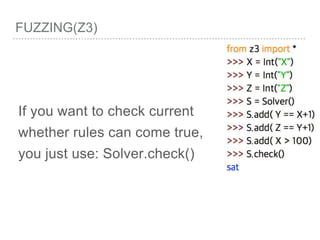
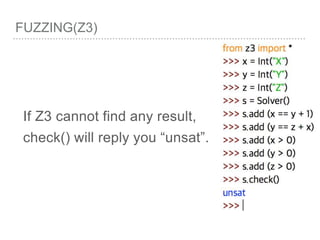
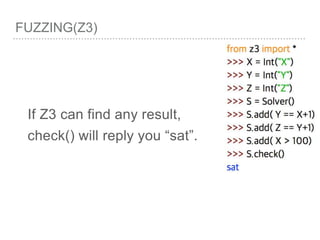
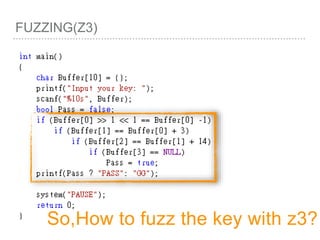
![FUZZING(Z3)
Finally, if you get “sat”,
you can use: Solver.model()
It will save a result in it.
Use model[Variable Name],
and get the answer by String](https://image.slidesharecdn.com/2015-151129180103-lva1-app6892/85/NTUSTxTDOH-117-320.jpg)