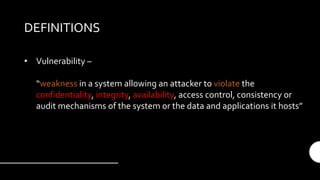
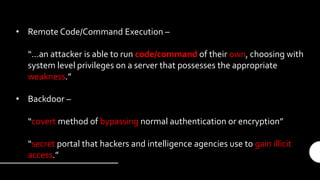
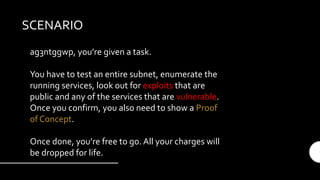
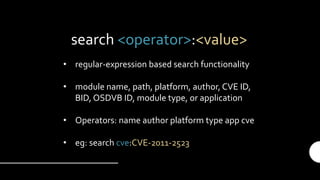
The document provides an introduction and overview of the Metasploit Framework. It defines key terms like vulnerability, exploit, and payload. It outlines the scenario of testing a subnet to find vulnerabilities. It describes the main features of msfconsole like searching for modules, using specific modules, and configuring options. It promotes understanding and proper use, emphasizing that Metasploit alone does not make someone a hacker.