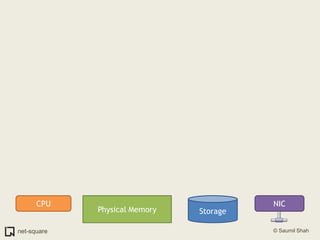
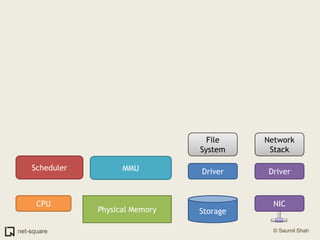
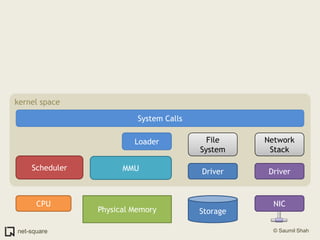
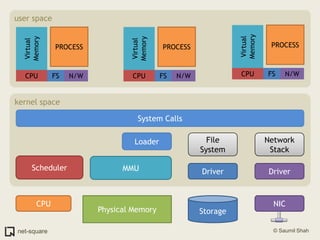
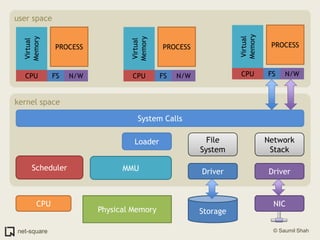
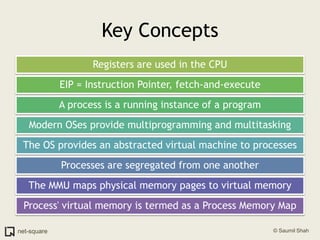
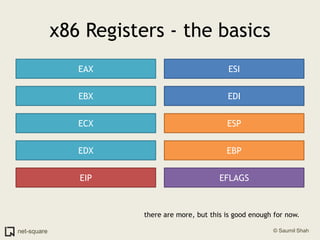
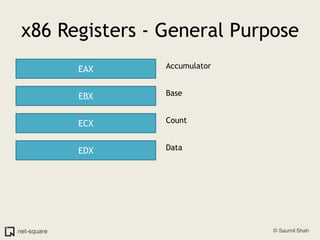
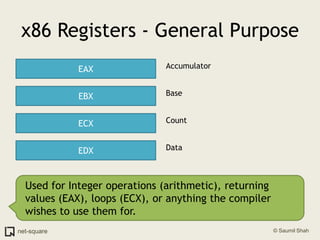
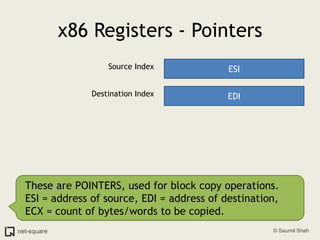
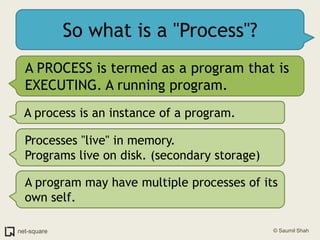
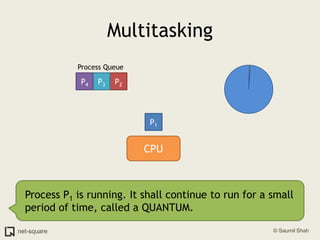
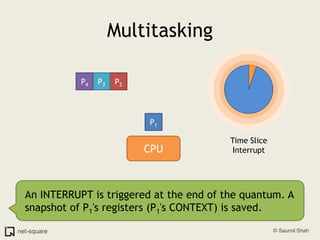
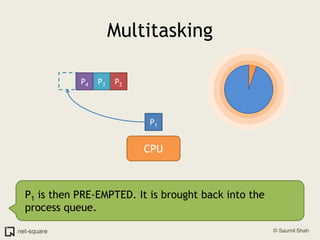
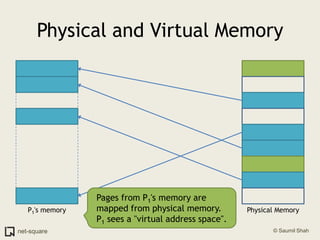
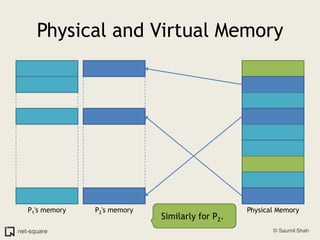
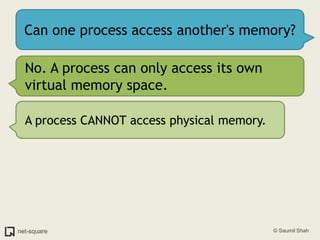
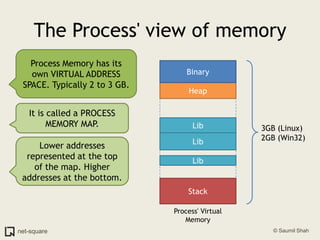
The document provides an introduction to operating systems and key concepts such as processes, virtual memory, and multitasking. It discusses how the CPU uses registers to perform computations and access memory. It explains that an operating system allows multiple programs to run simultaneously through time-slicing and context-switching between processes. Each process has its own virtual address space and sees its own "virtual machine" presented by the operating system.










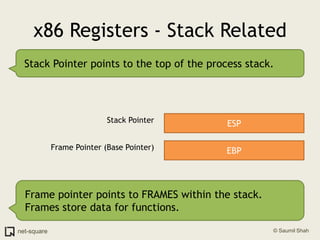














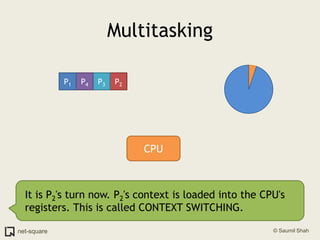
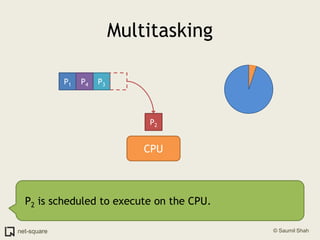
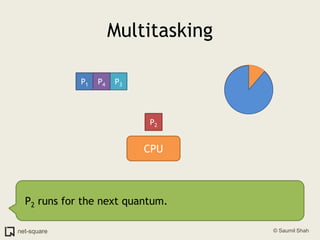

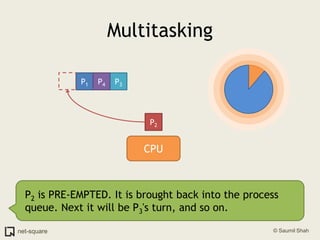



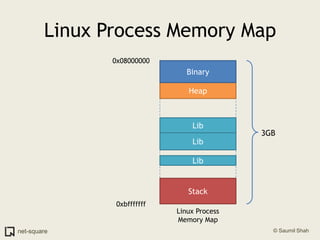
![An exampleHere's how to view a process' memory map in Linux. The process here is PID 1110.saumil@localhost:$ pmap 11101110: /home/nweb/nweb 8181 /home/nweb 08048000 8K read/exec /home/nweb/nweb0804a000 4K read/write /home/nweb/nweb0804b000 8K read/write/exec [ anon ]40000000 72K read/exec /lib/ld-2.3.1.so40012000 4K read/write /lib/ld-2.3.1.so40013000 4K read/write [ anon ]40019000 1204K read/exec /lib/i686/libc-2.3.1.so40146000 16K read/write /lib/i686/libc-2.3.1.so4014a000 8K read/write [ anon ]bfffe000 8K read/write/exec [ anon ] total 1336K](https://image.slidesharecdn.com/osprimer-110501154131-phpapp02/85/Operating-Systems-A-Primer-59-320.jpg)