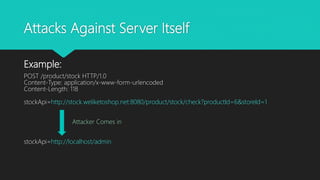
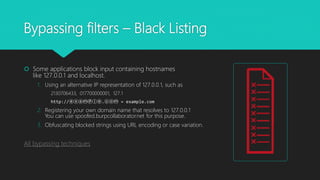
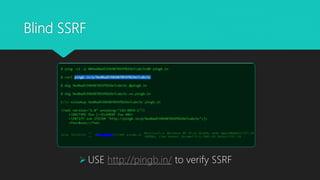
This document provides an overview of server-side request forgery (SSRF) vulnerabilities, including what SSRF is, its impact, common attacks, bypassing filters, and mitigations. SSRF allows an attacker to induce the application to make requests to internal or external servers from the server side, bypassing access controls. This can enable attacks on the server itself or other backend systems and escalate privileges. The document discusses techniques for exploiting trust relationships and bypassing blacklists/whitelists to perform SSRF attacks. It also covers blind SSRF and ways to detect them using out-of-band techniques. Mitigations include avoiding user input that can trigger server requests, sanitizing input, whitelist