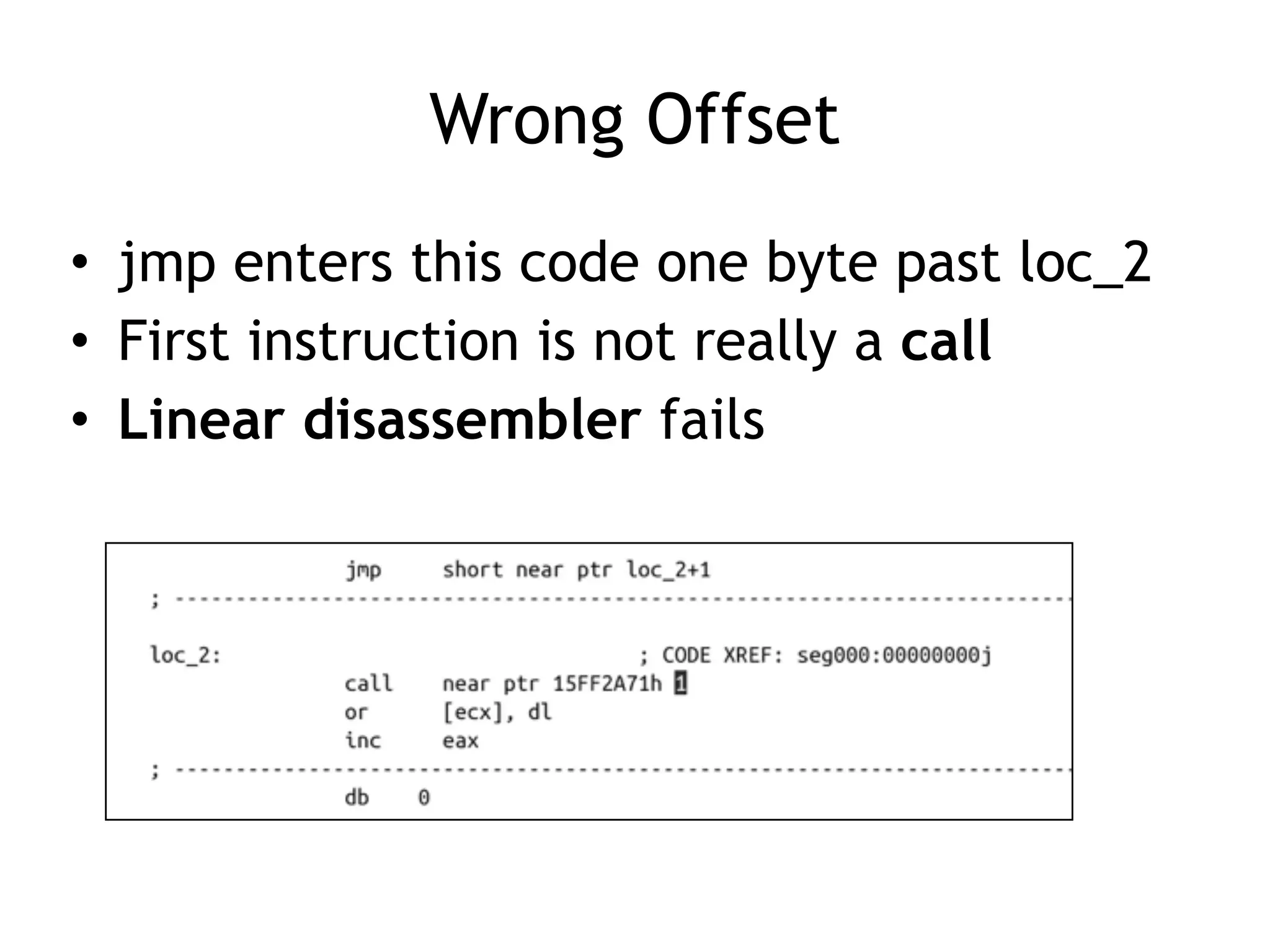
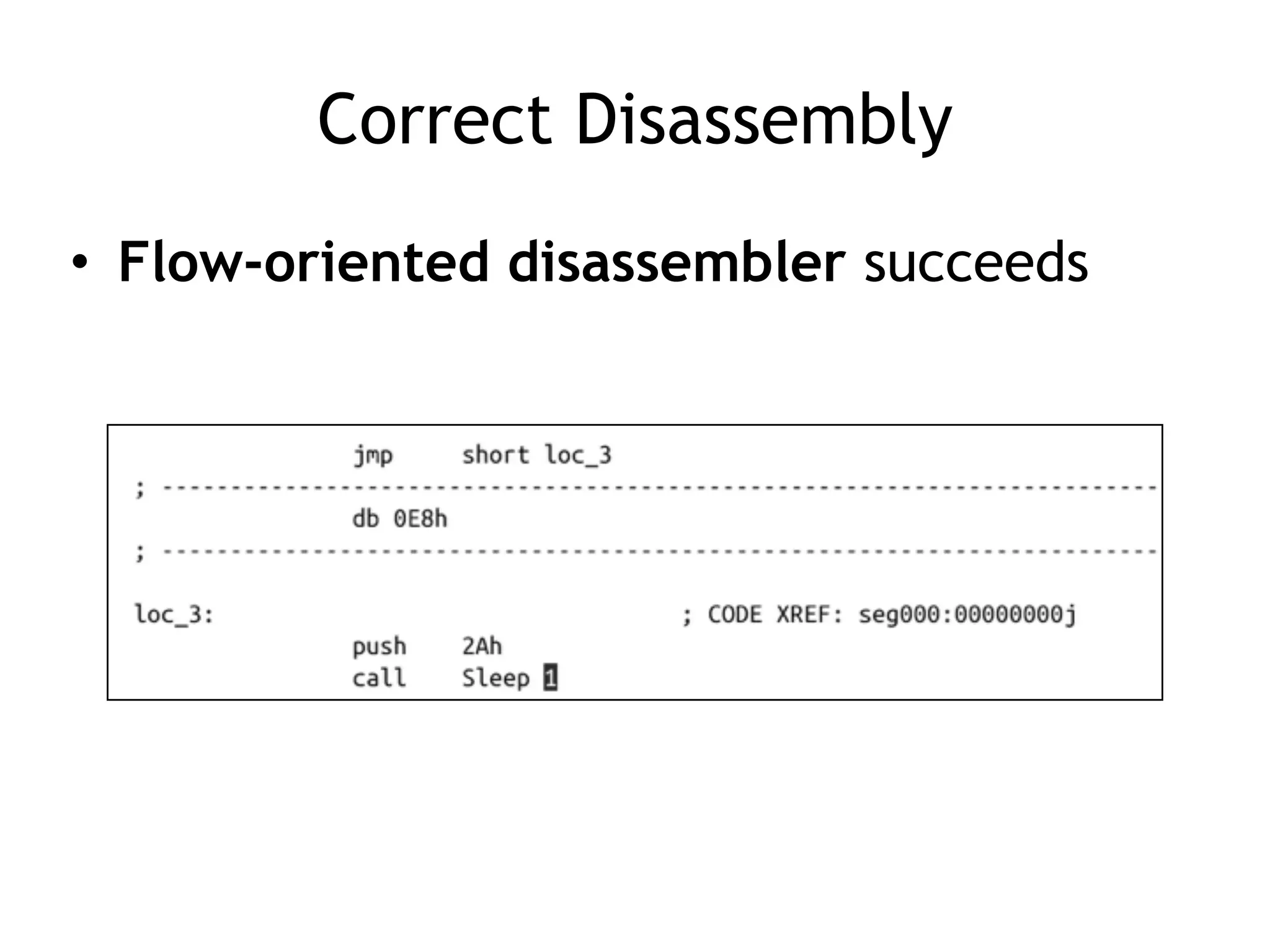
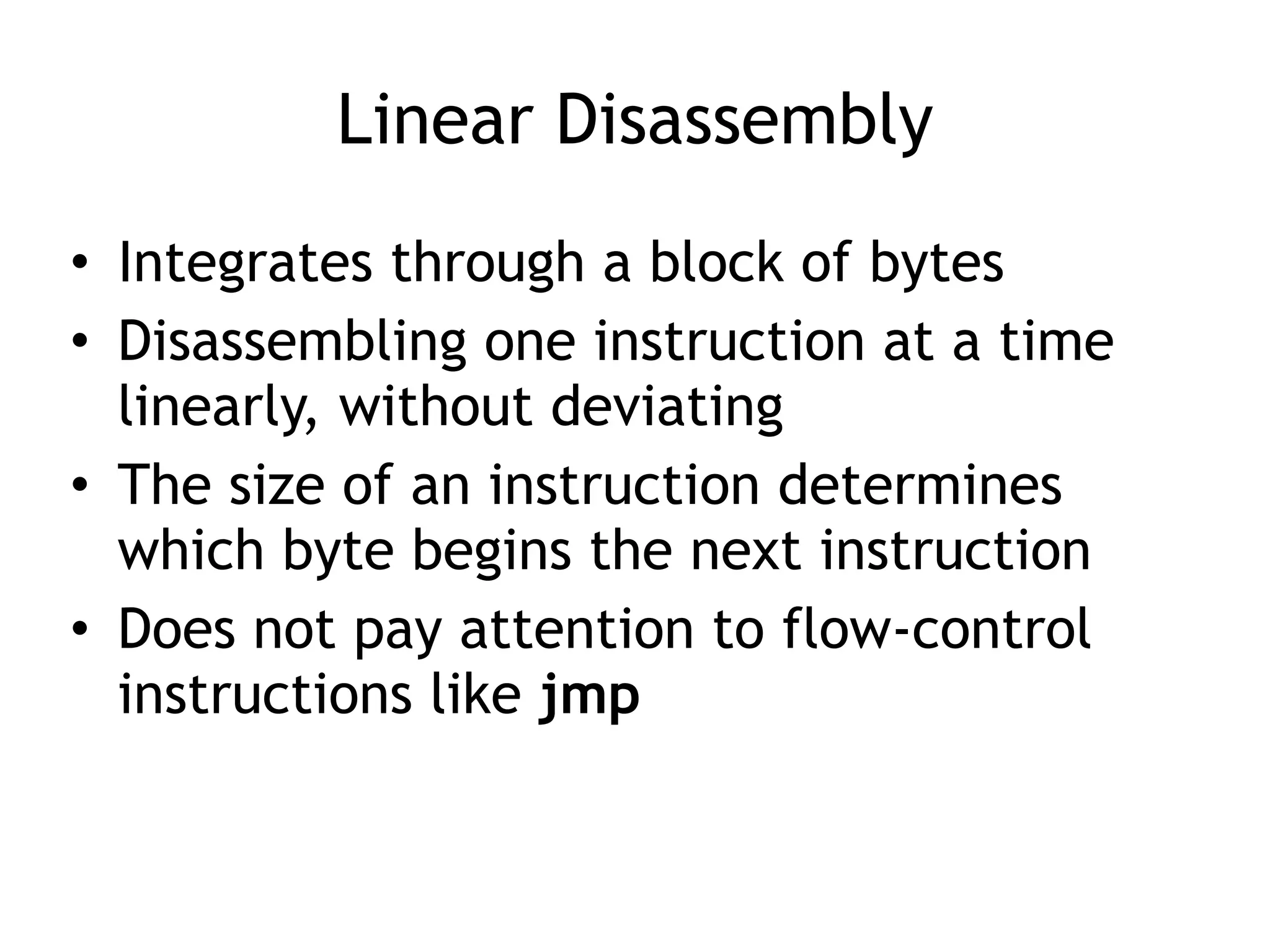
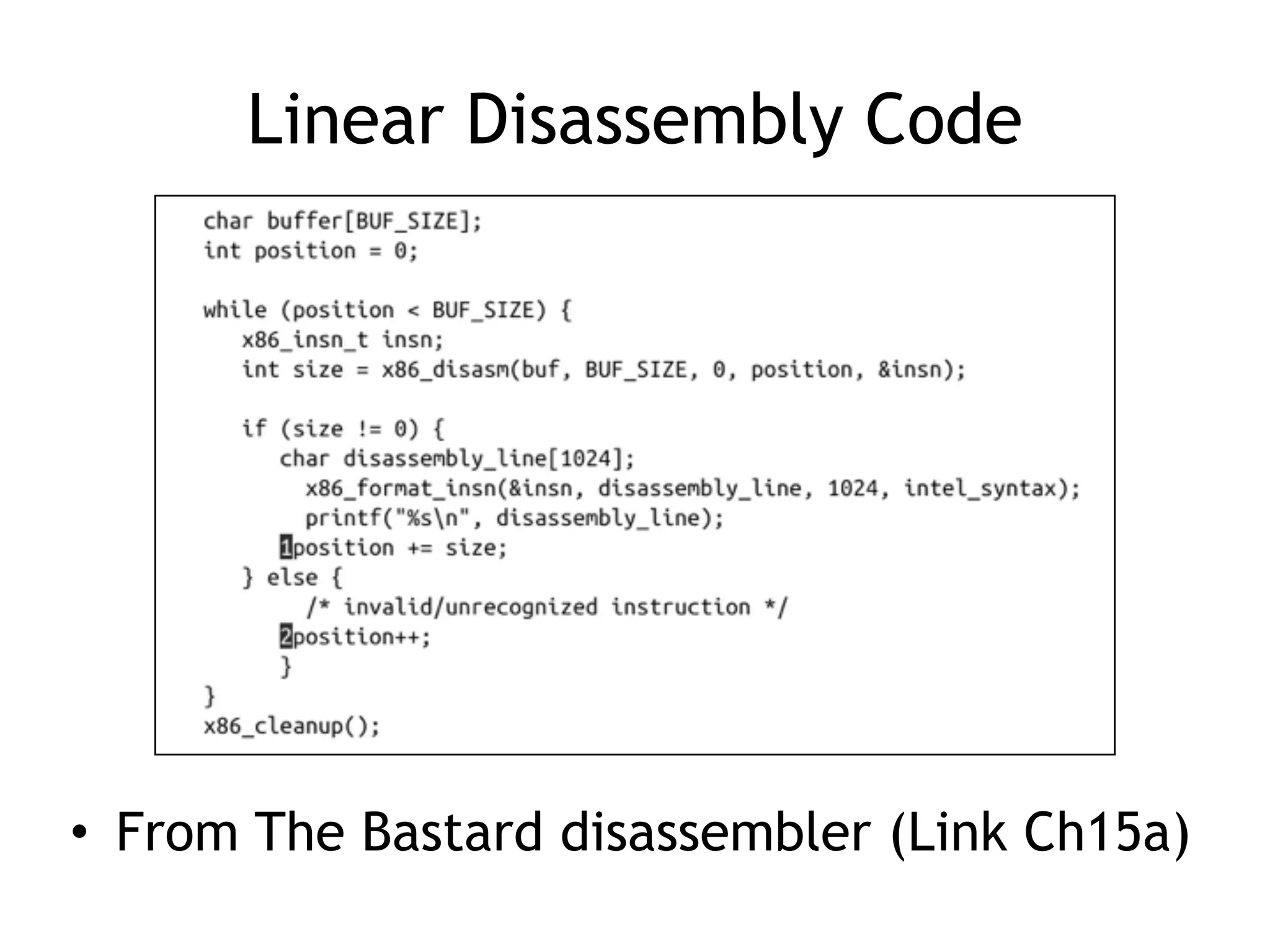
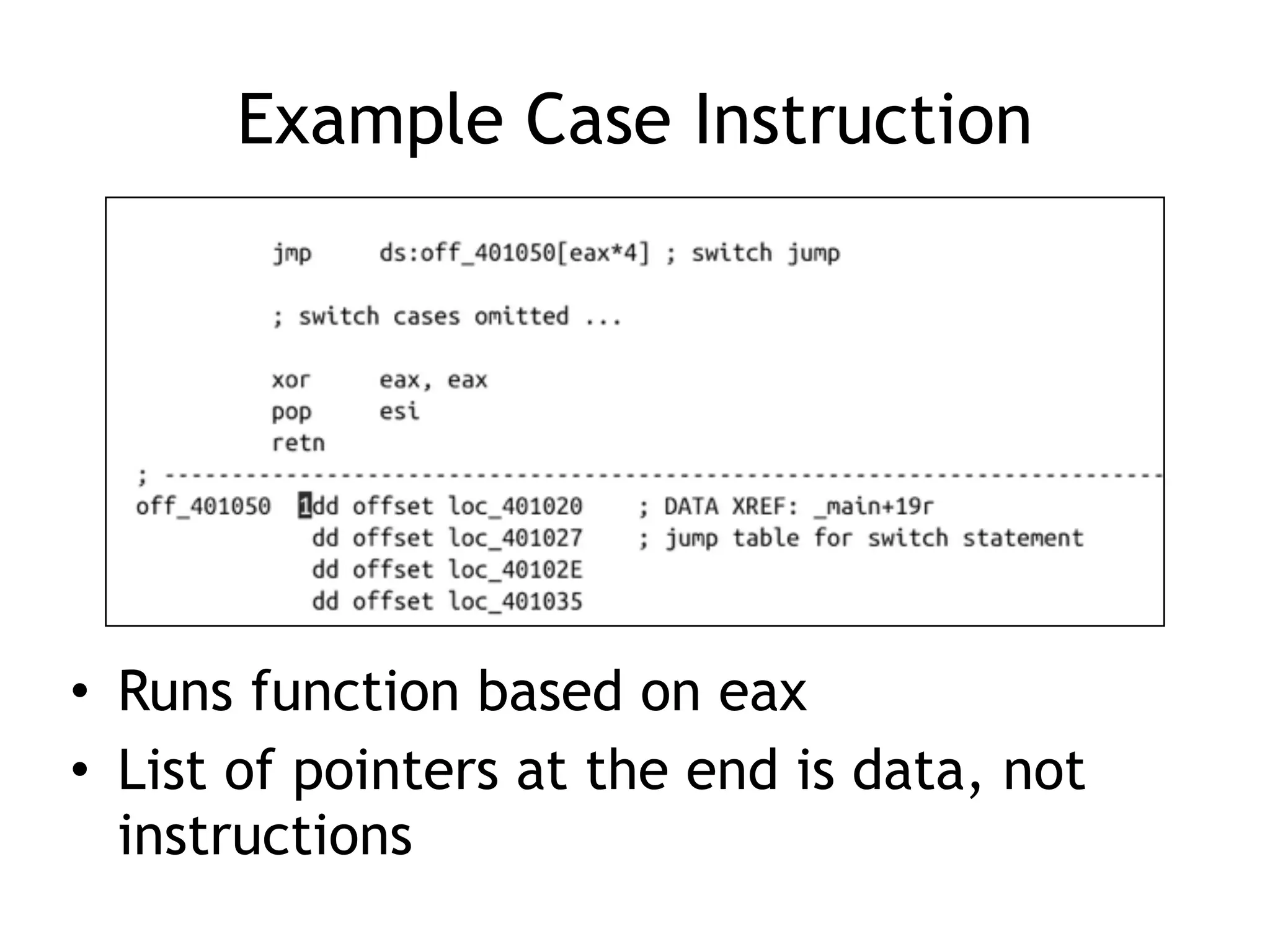
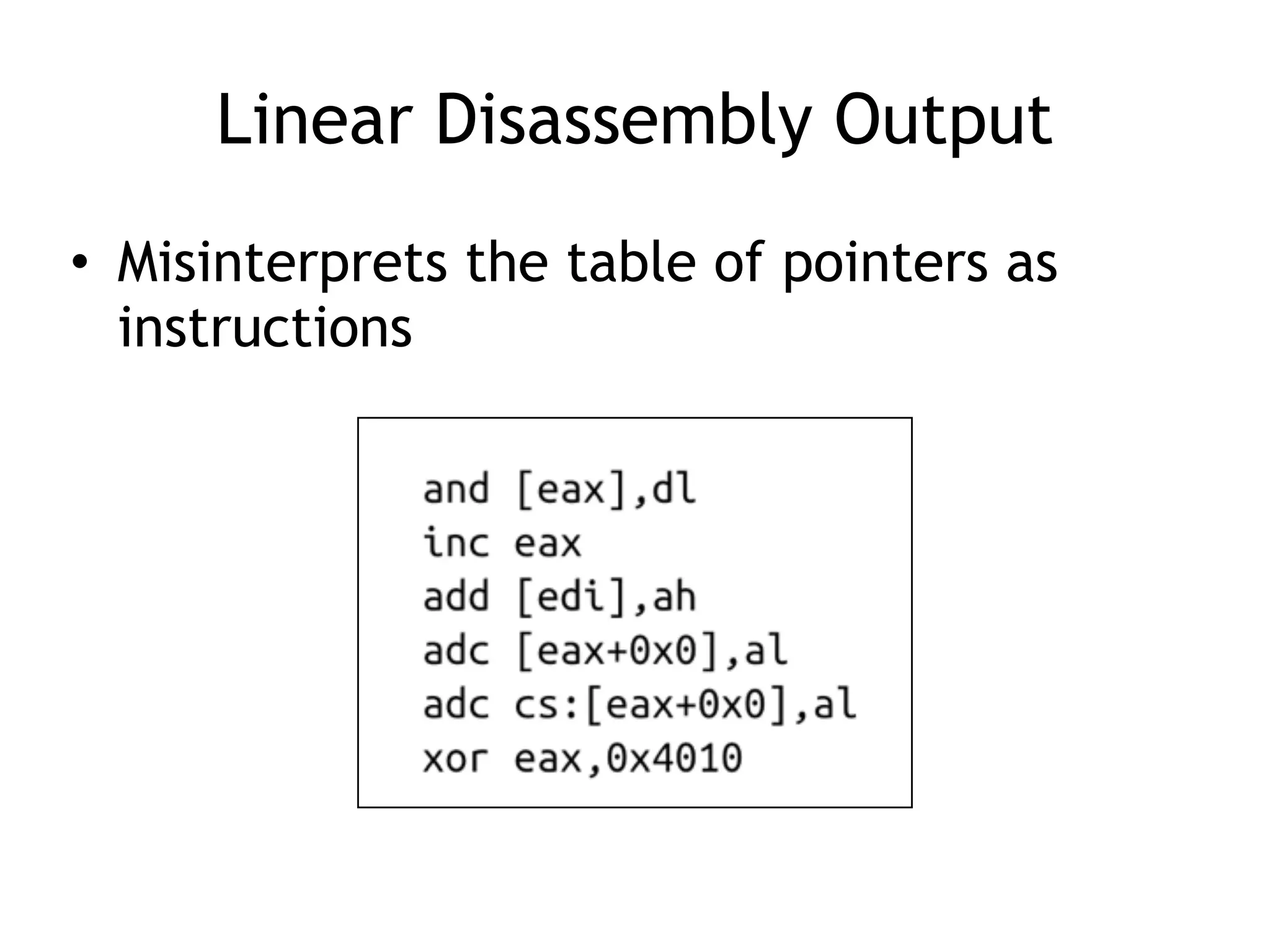
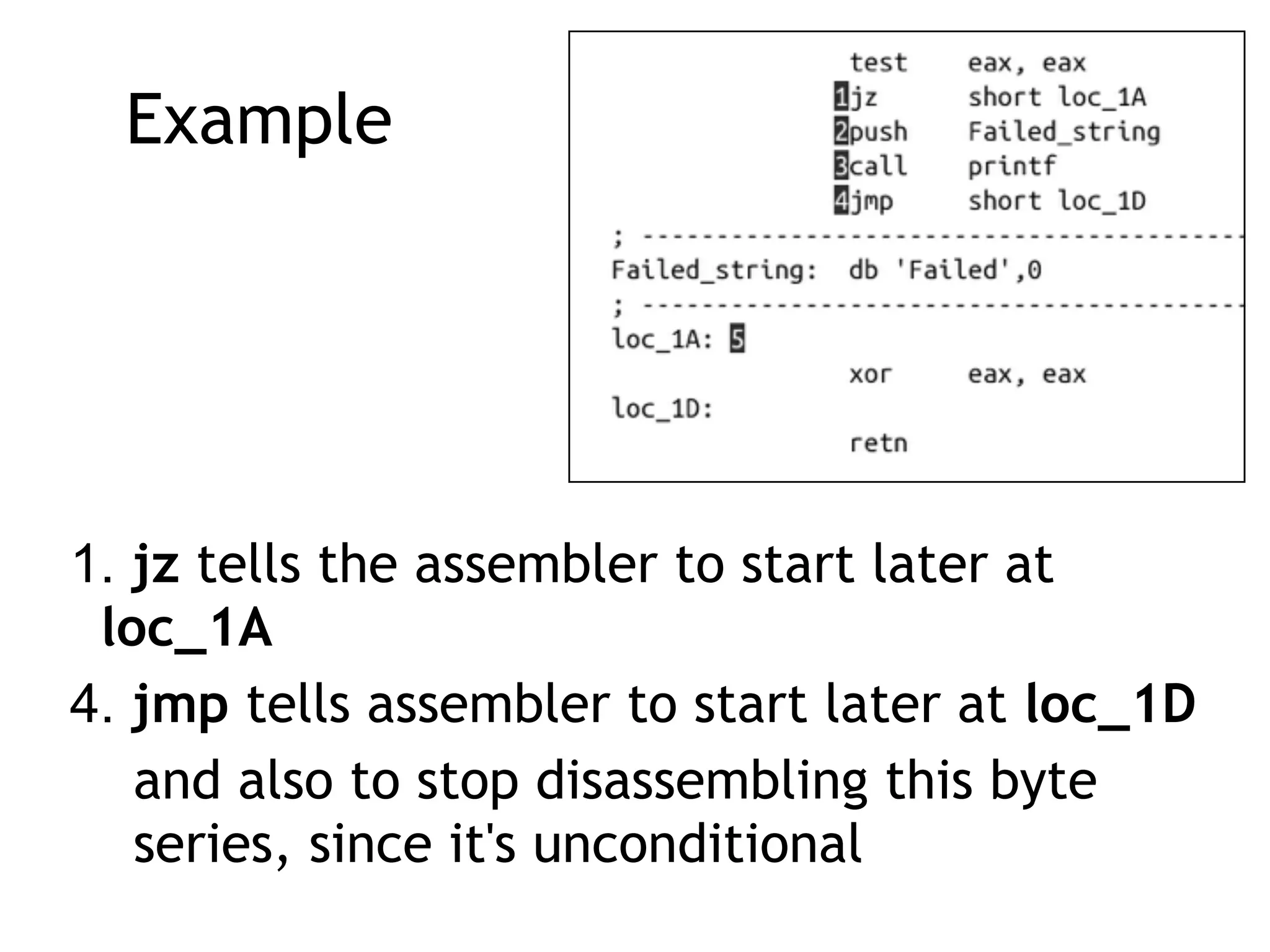
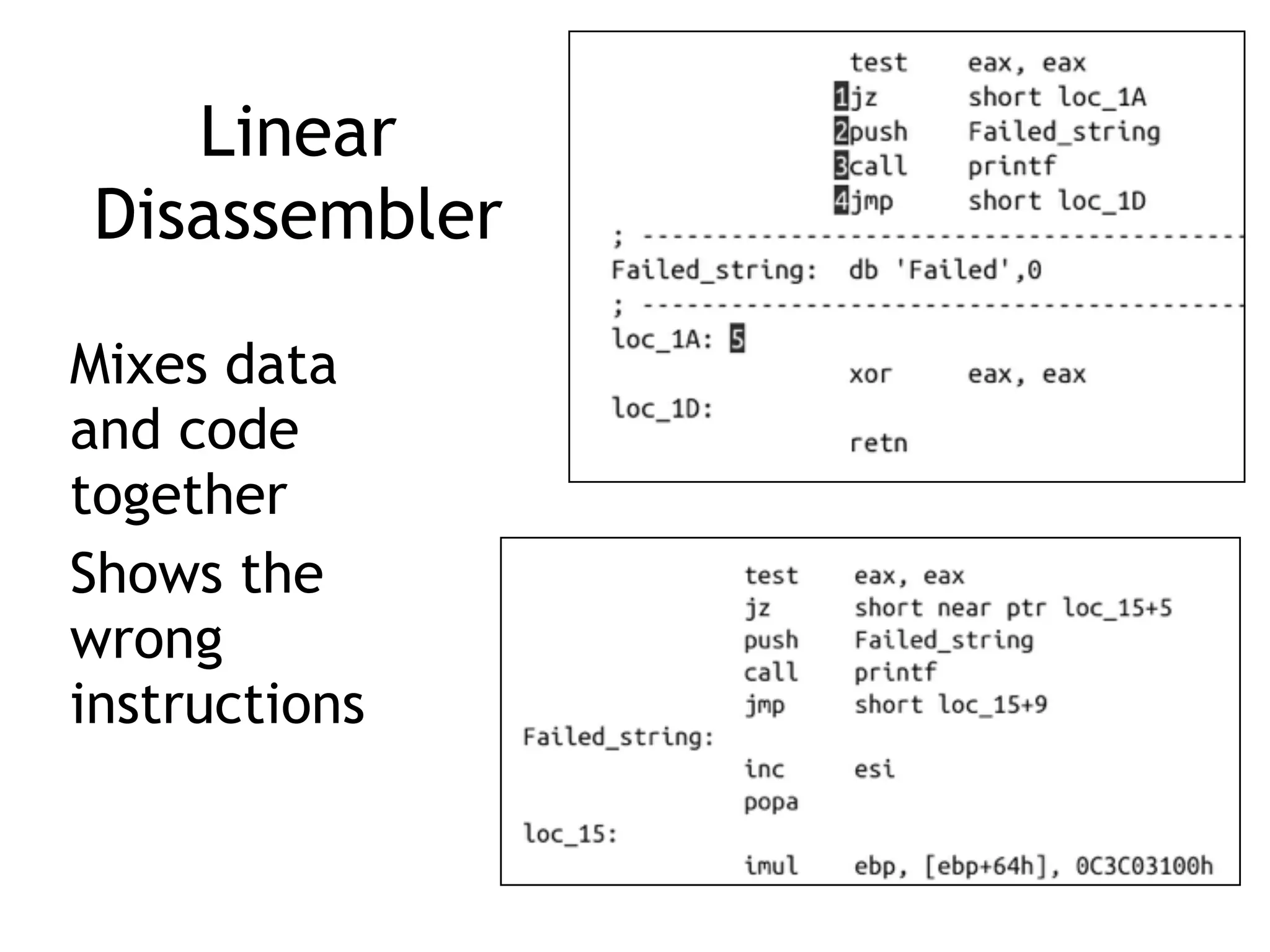
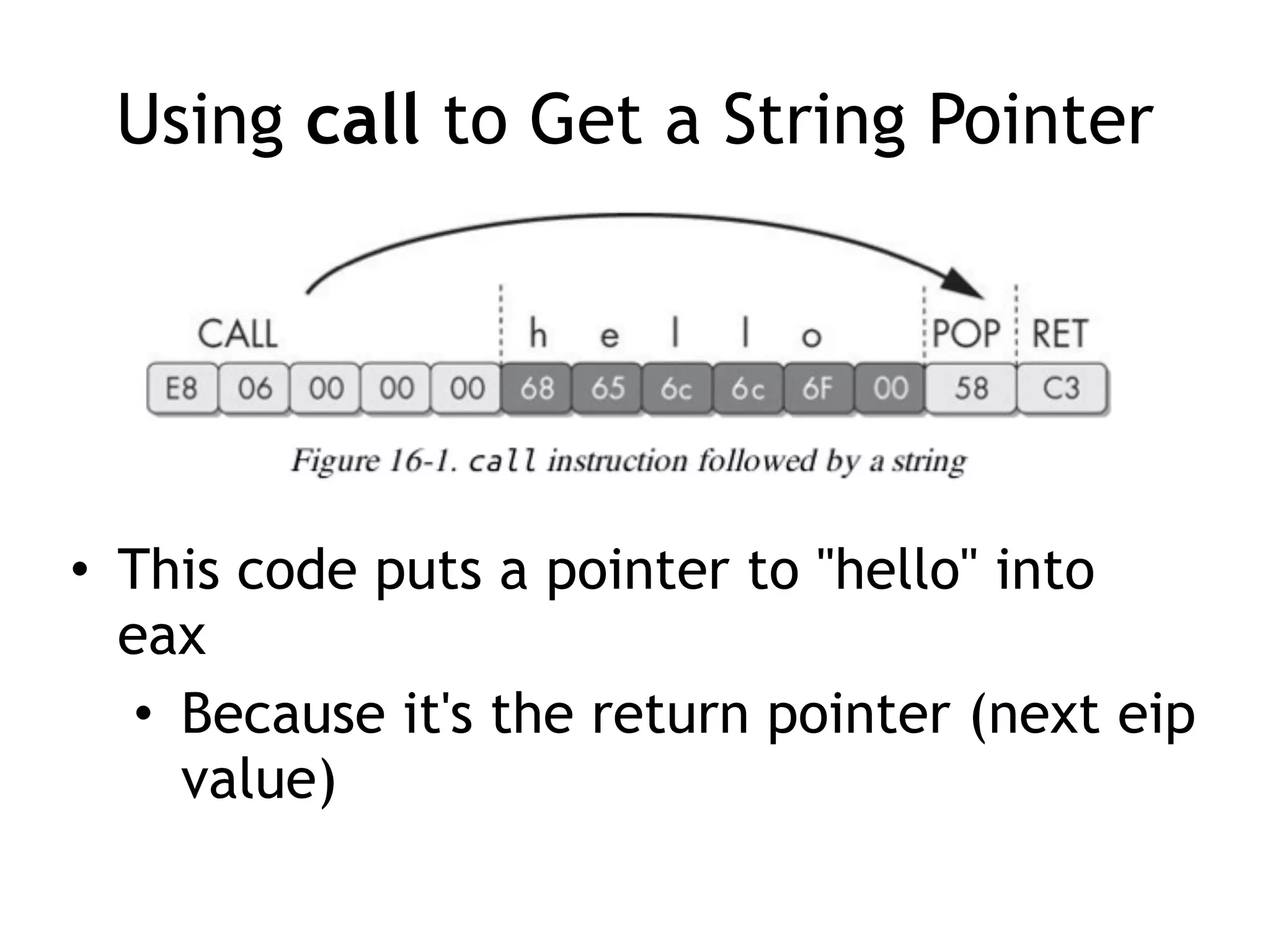
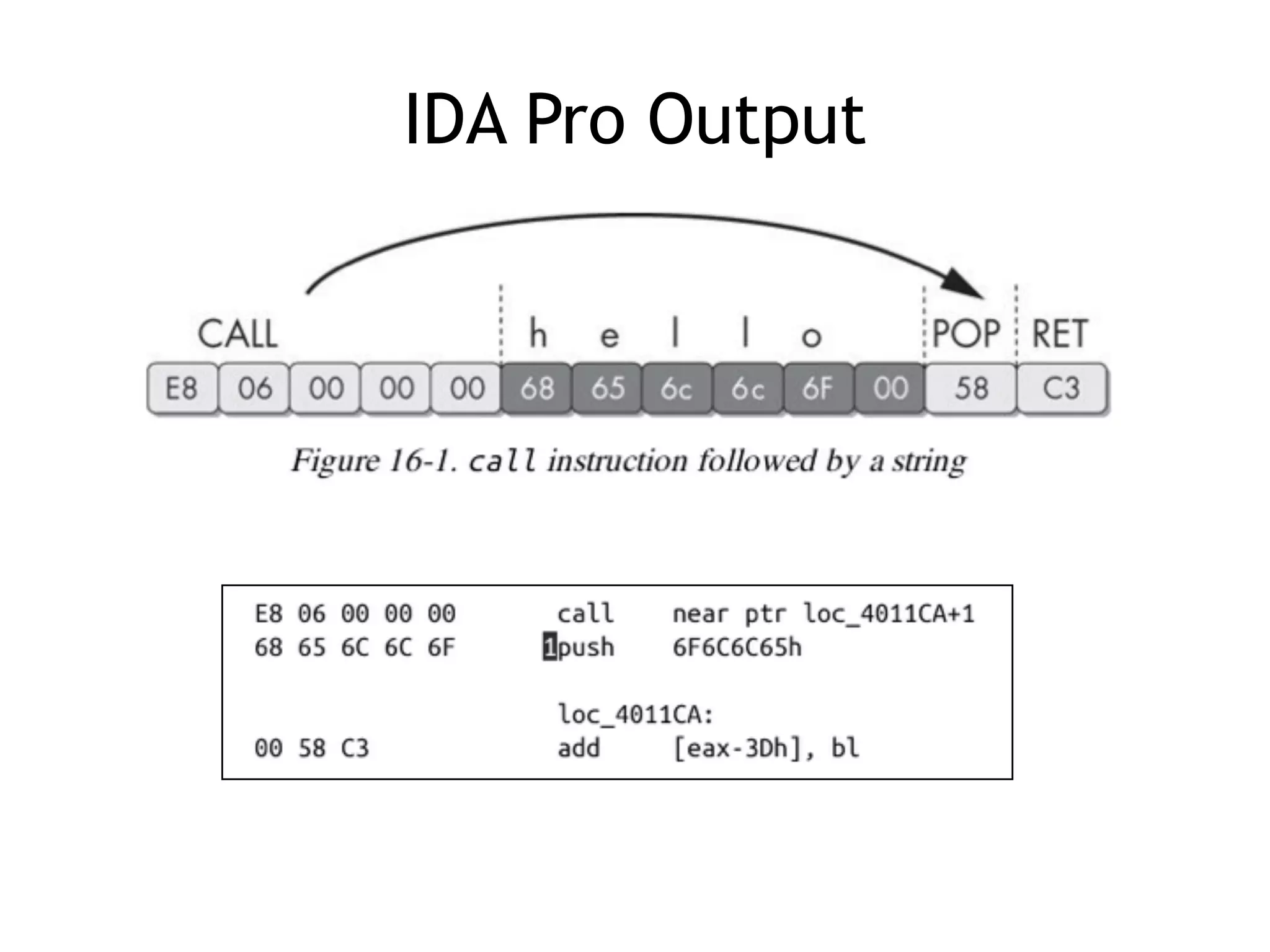
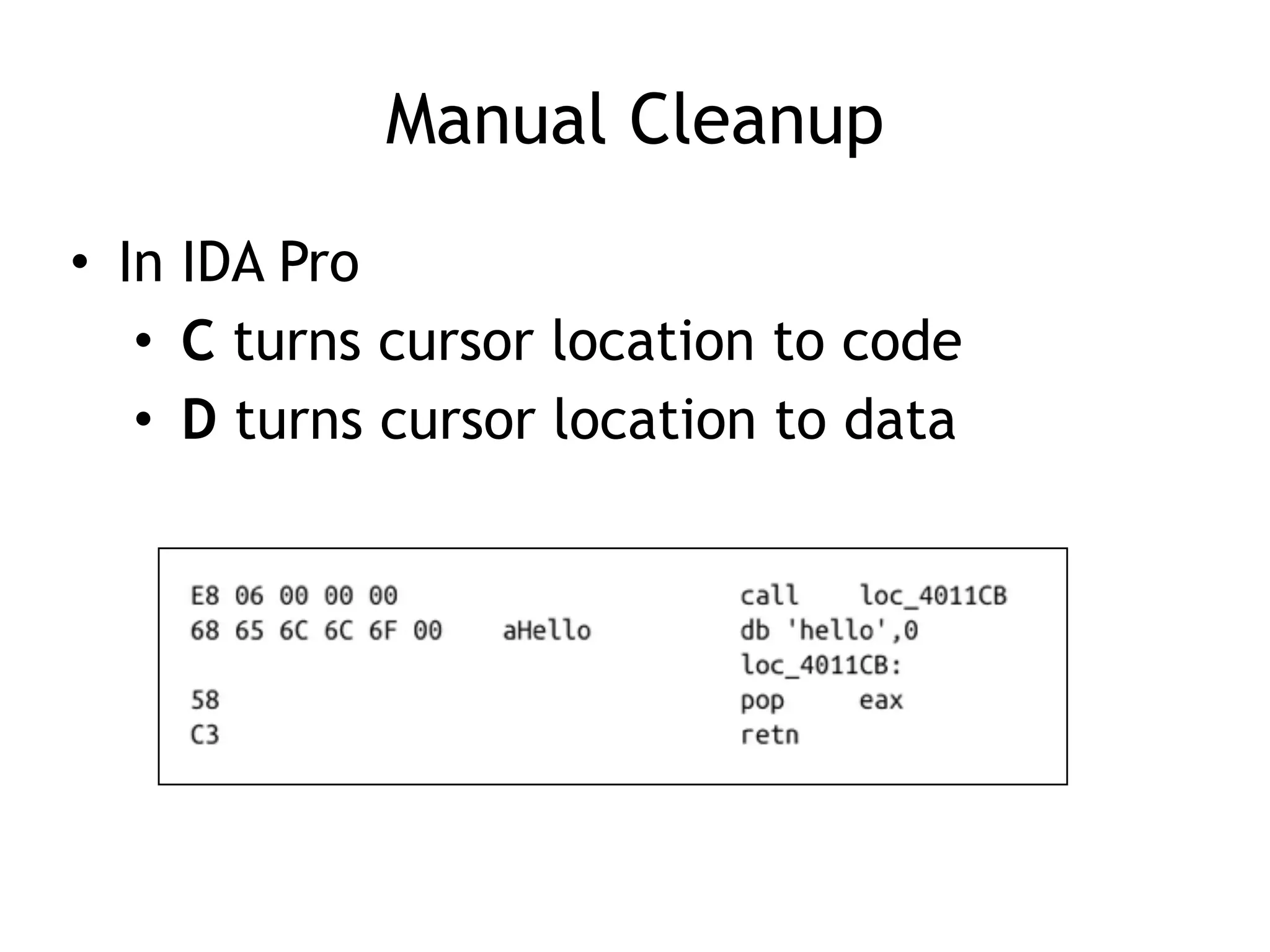
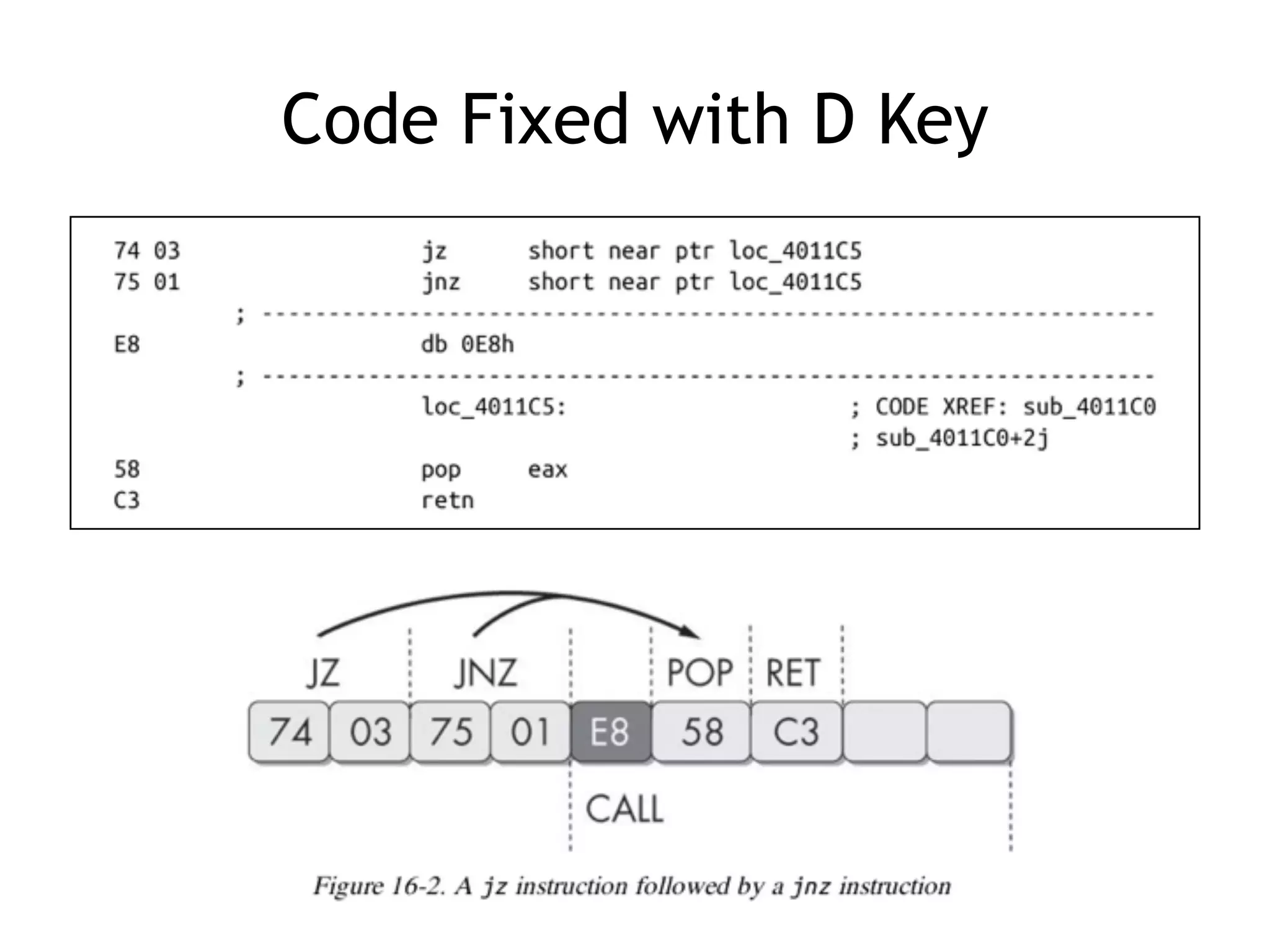
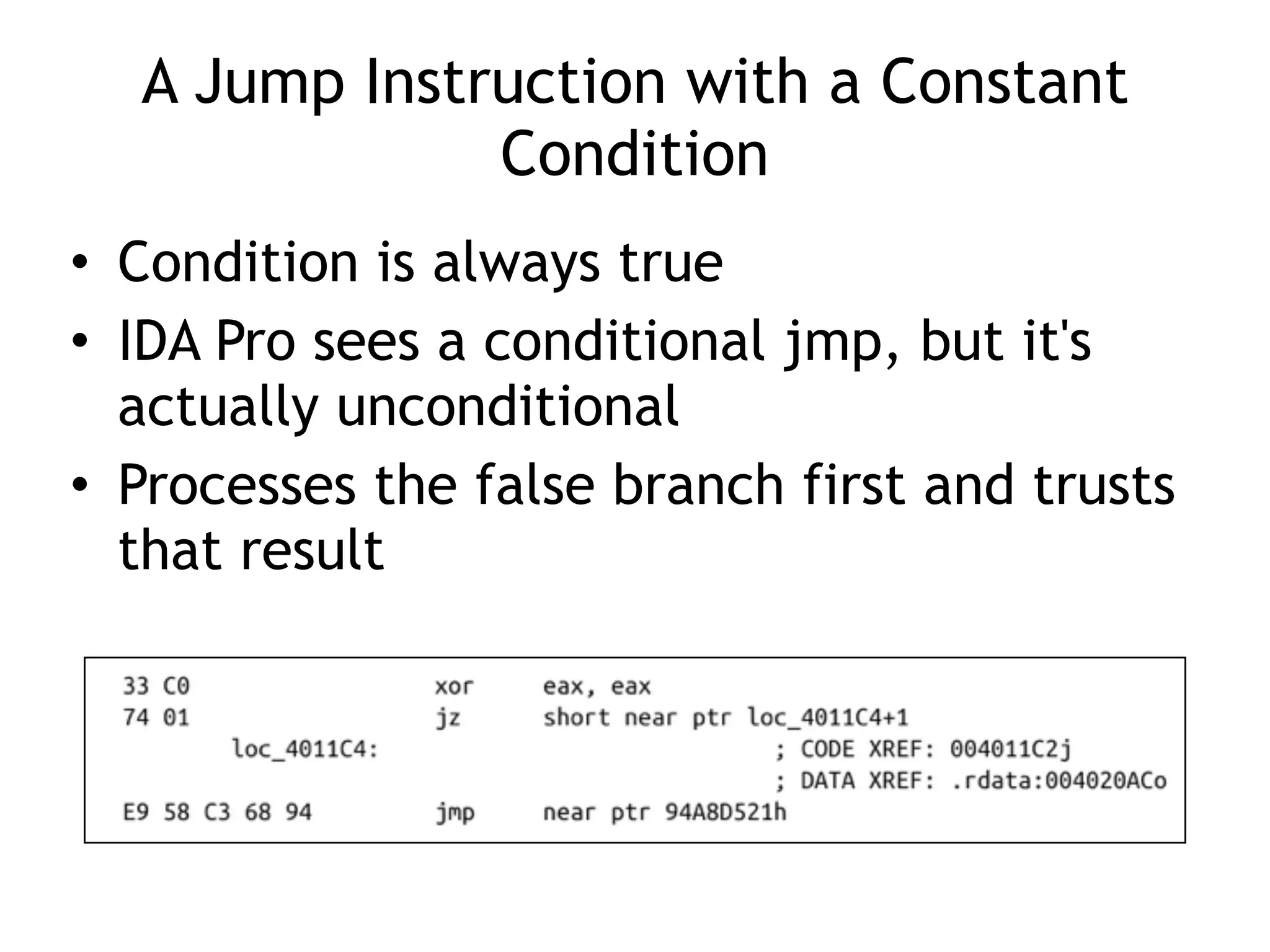
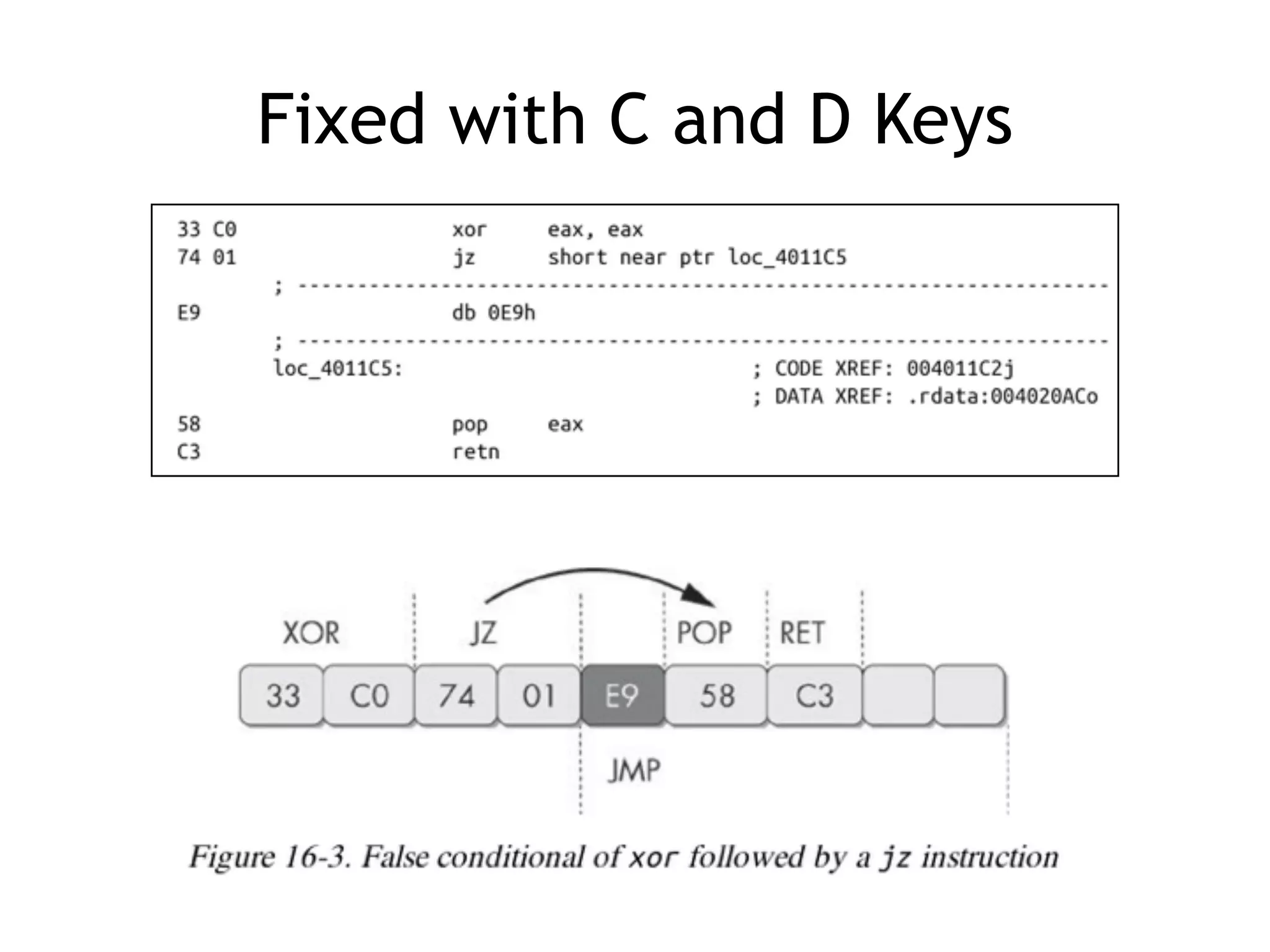
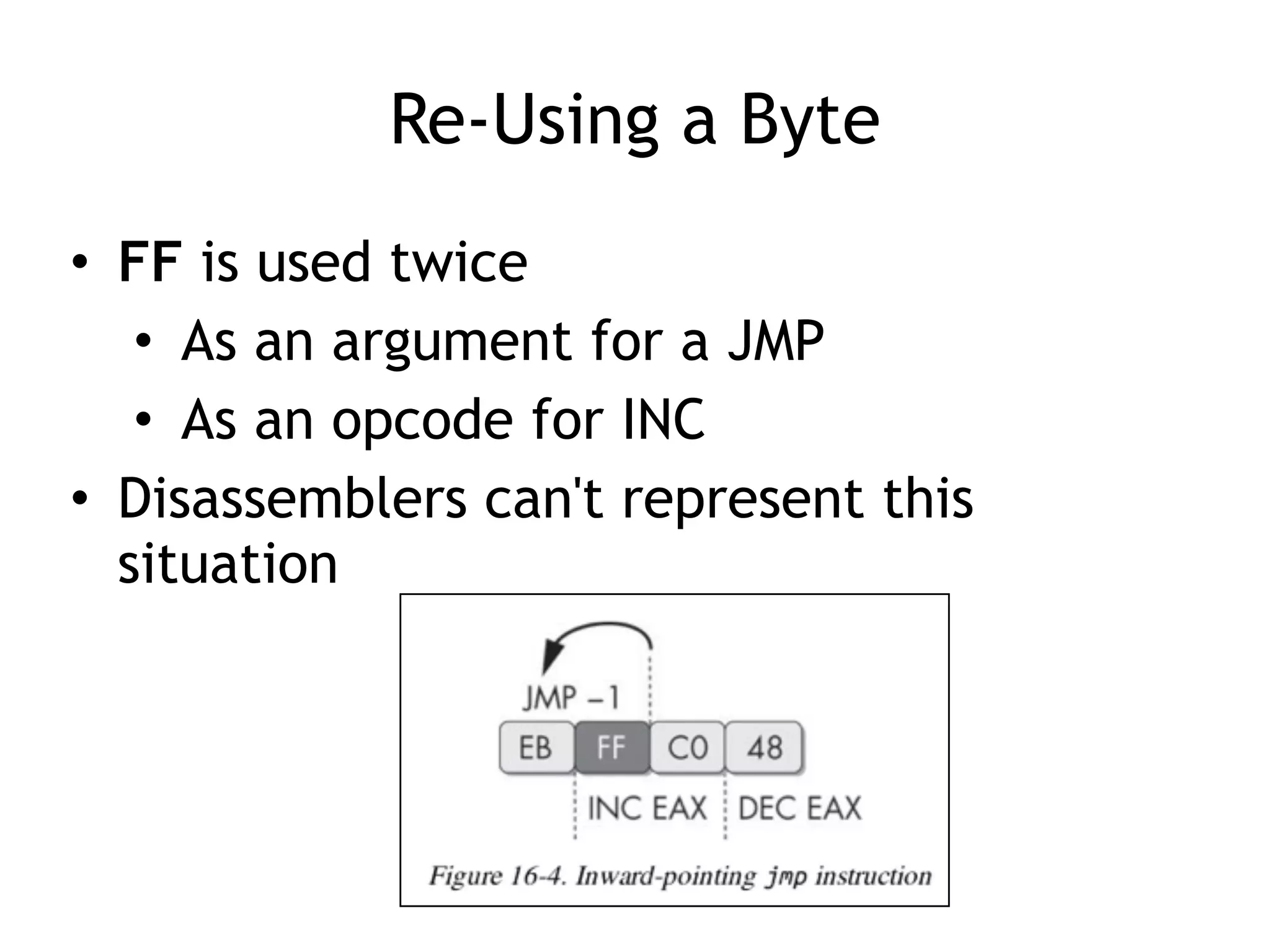
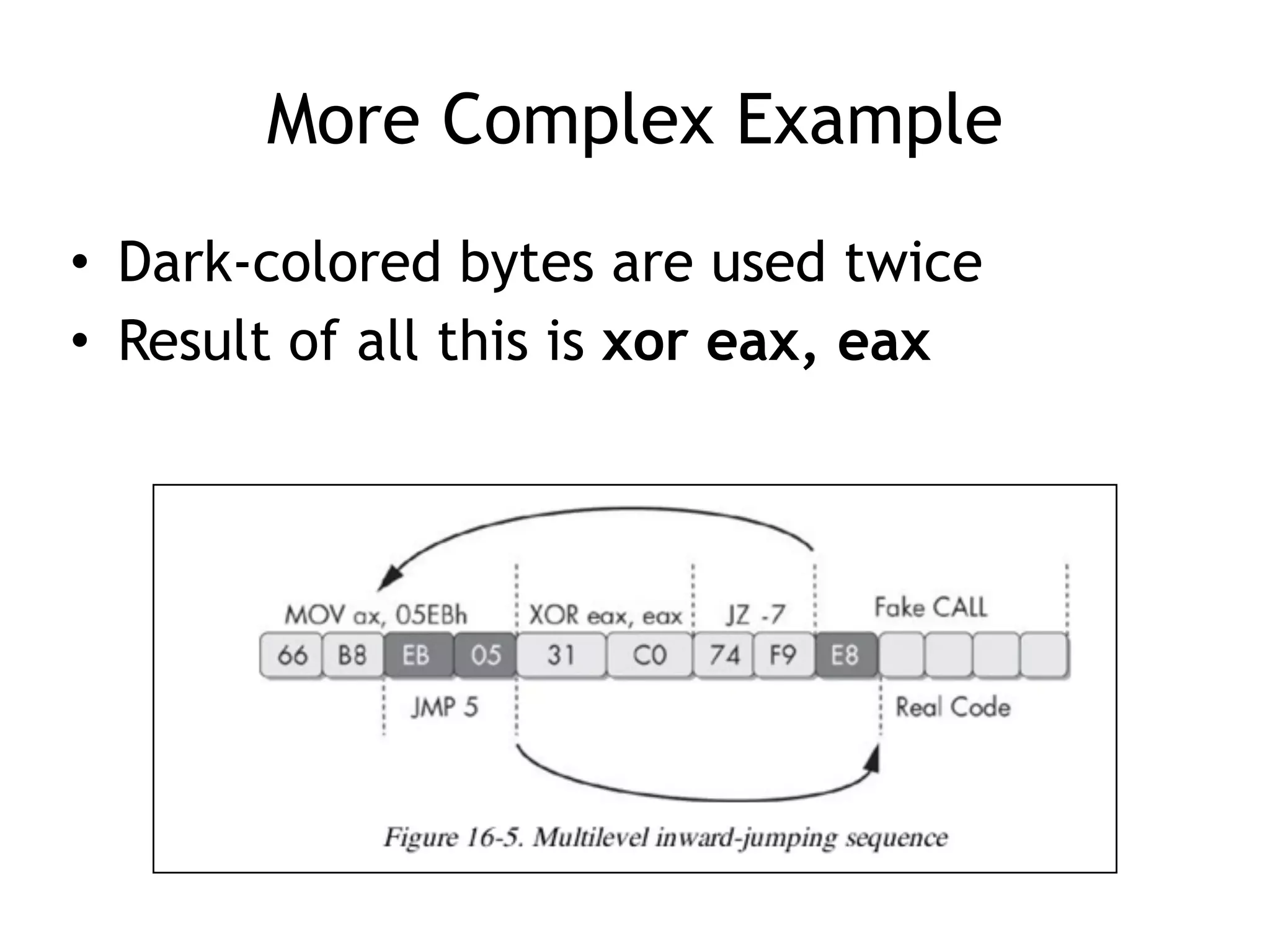
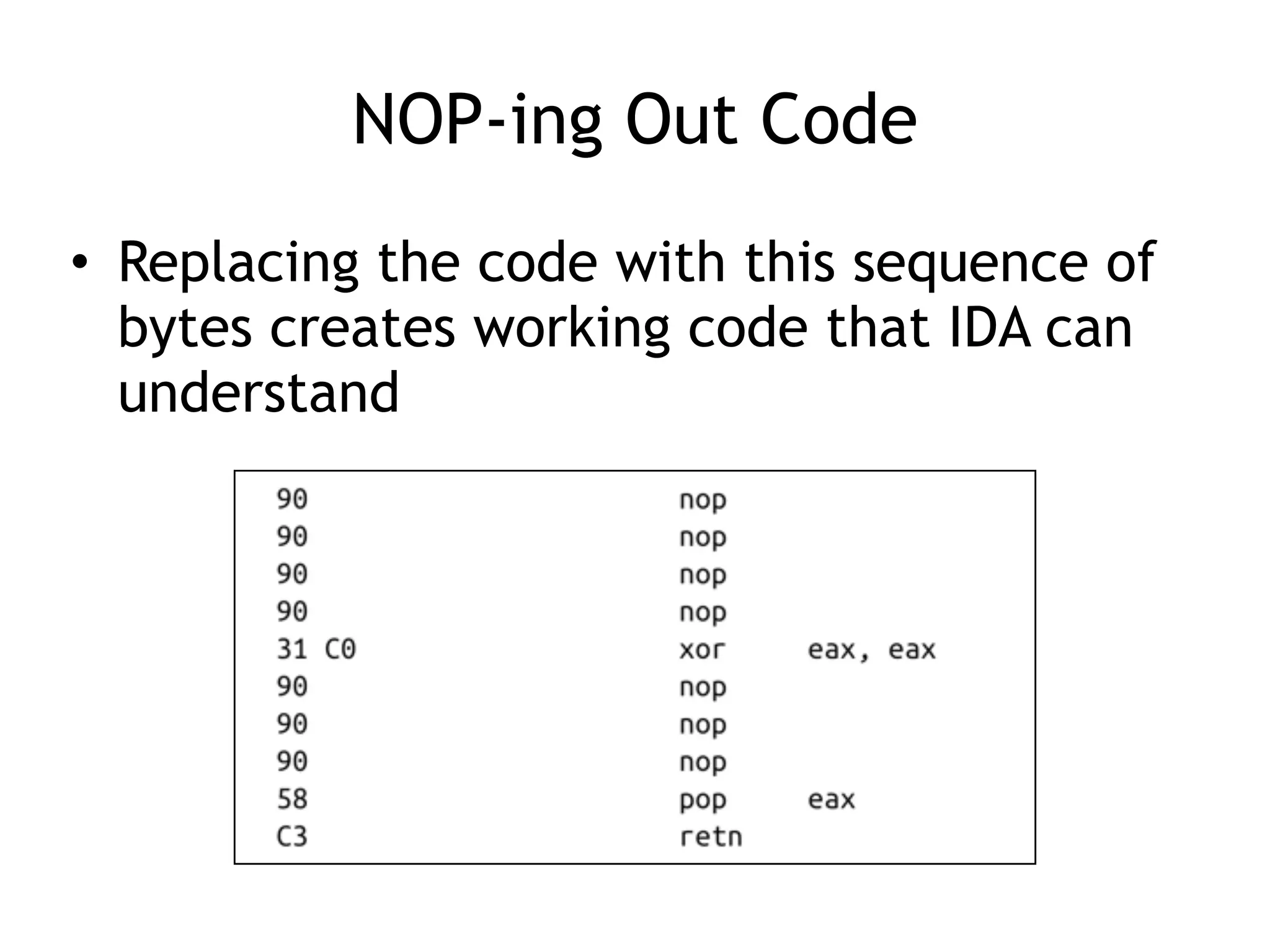
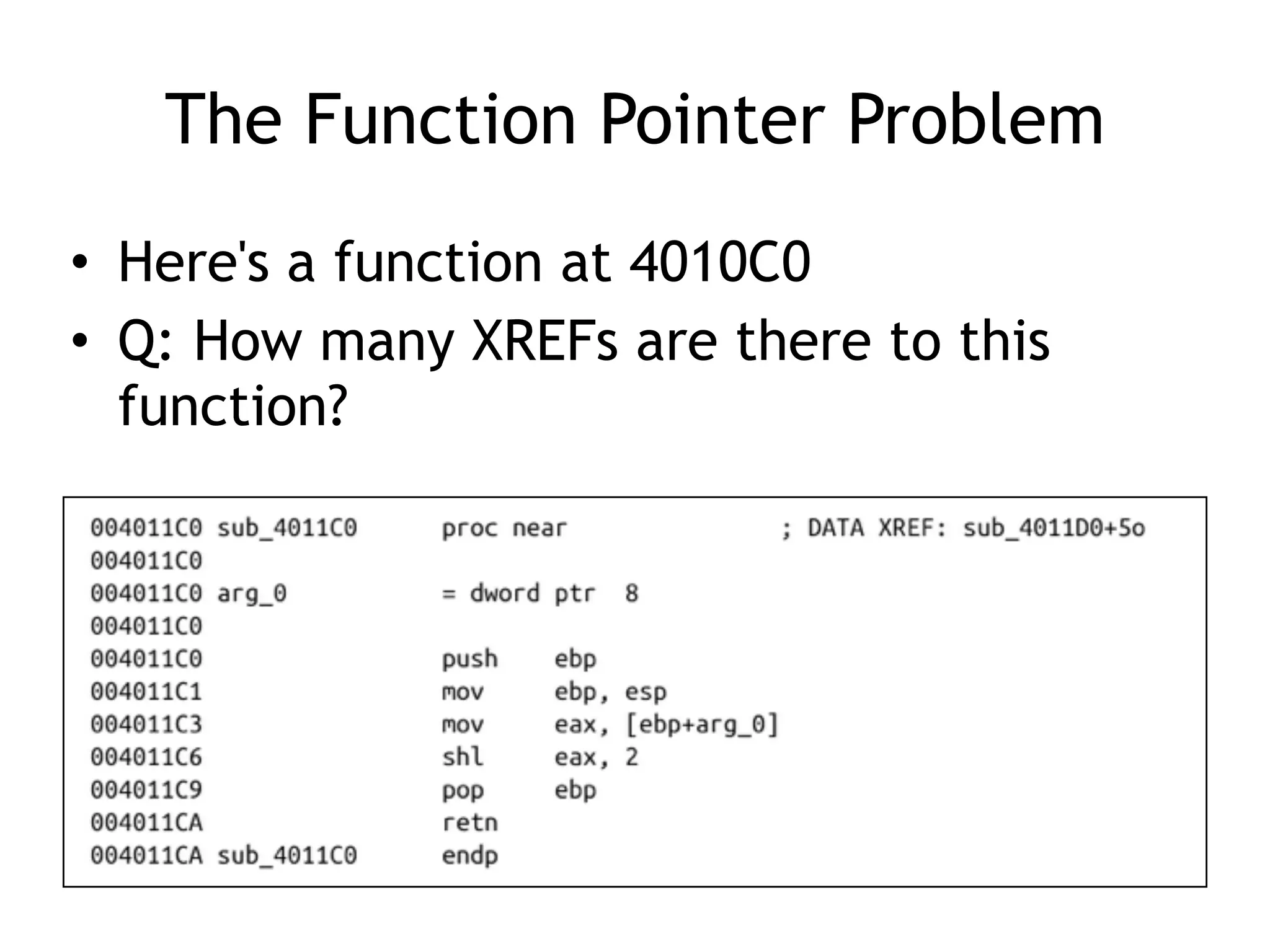
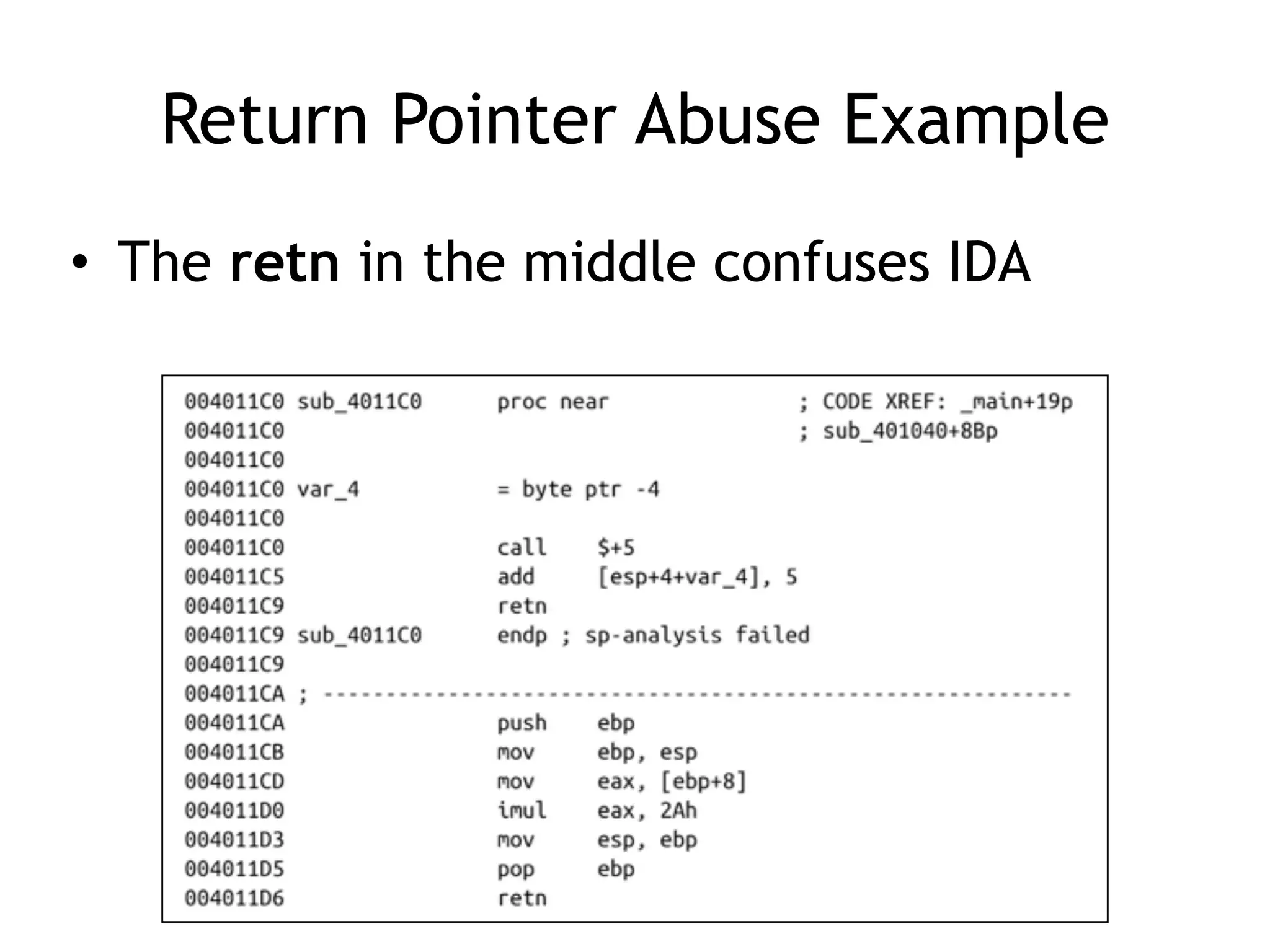
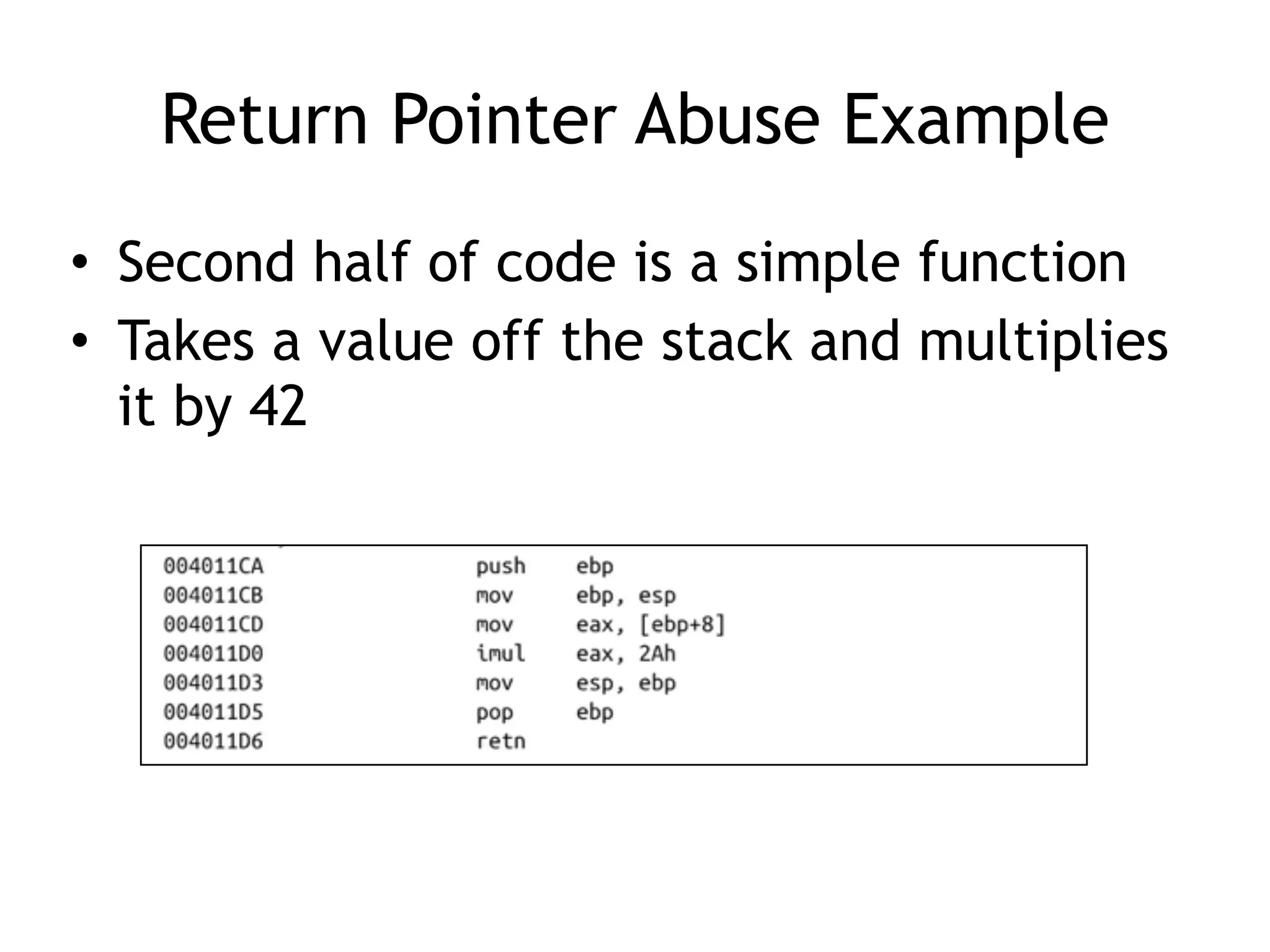
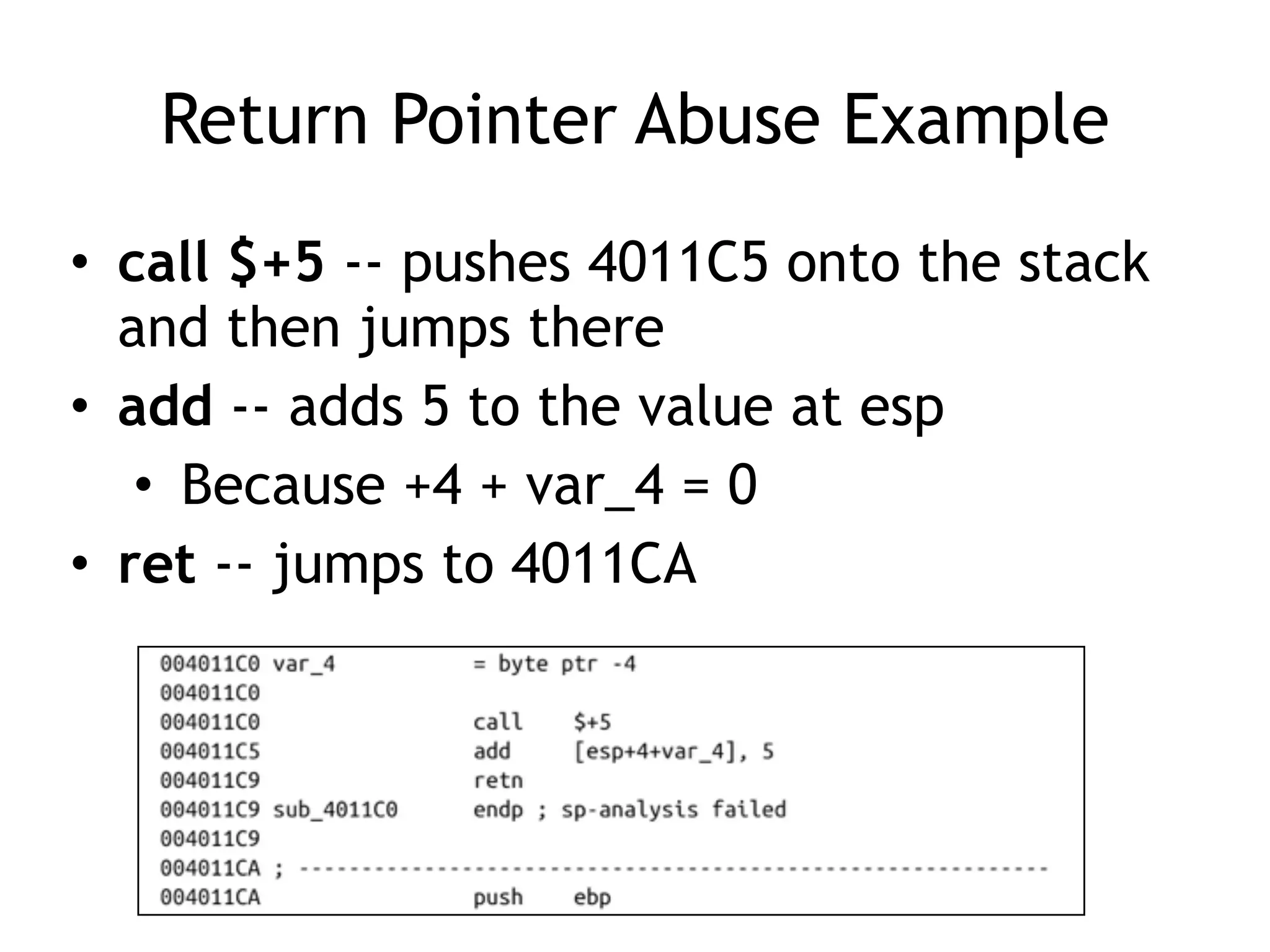
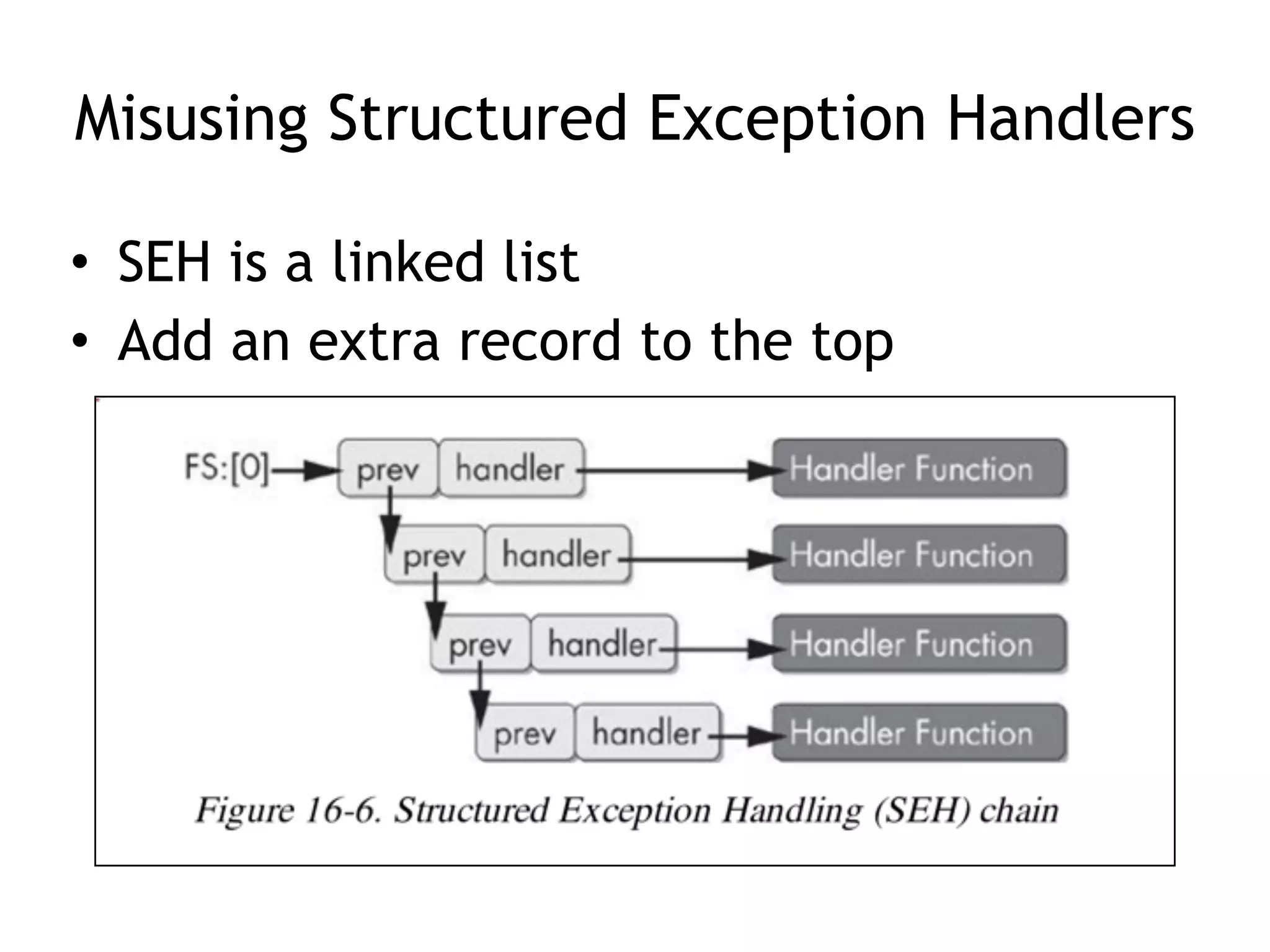
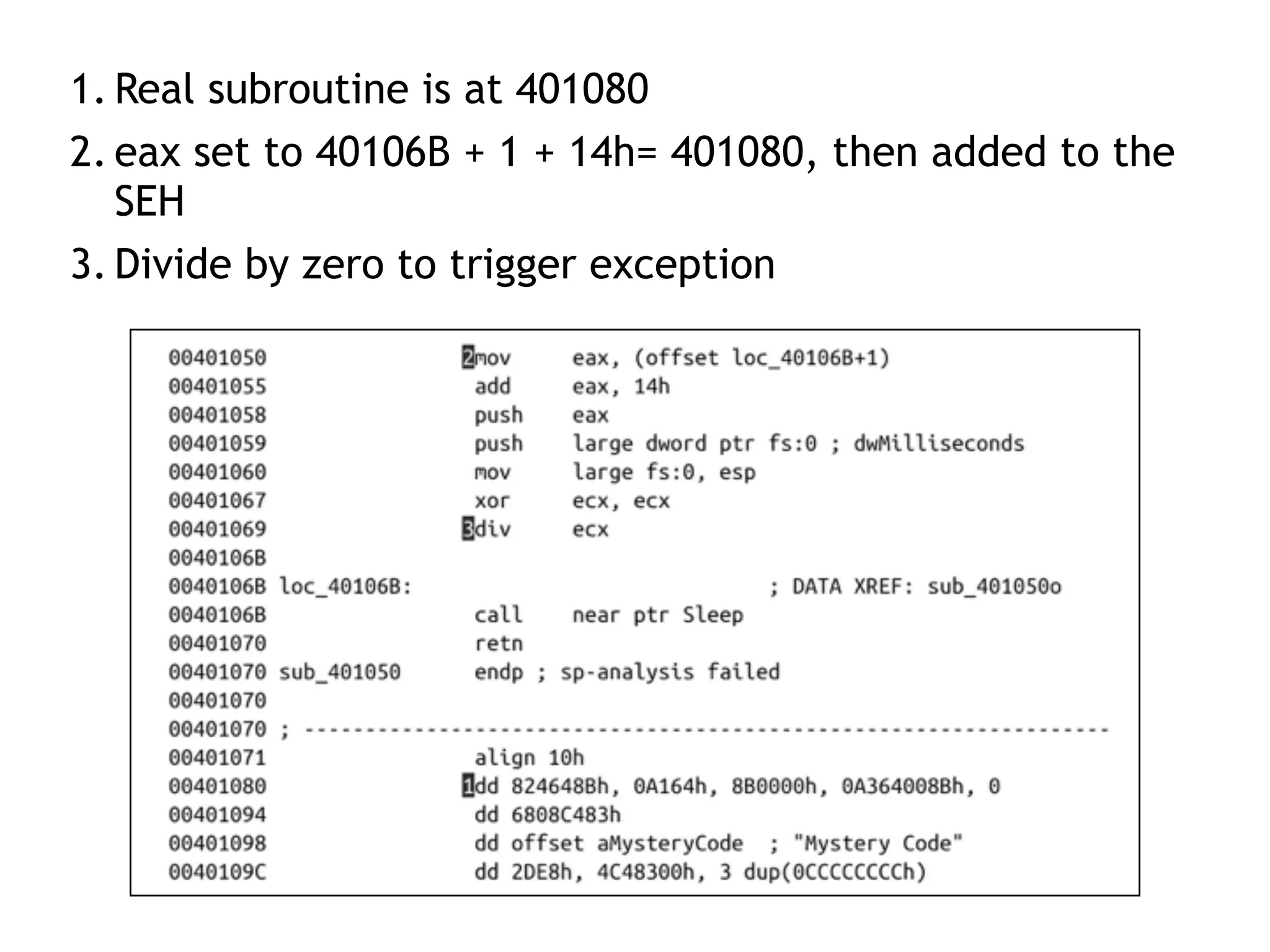
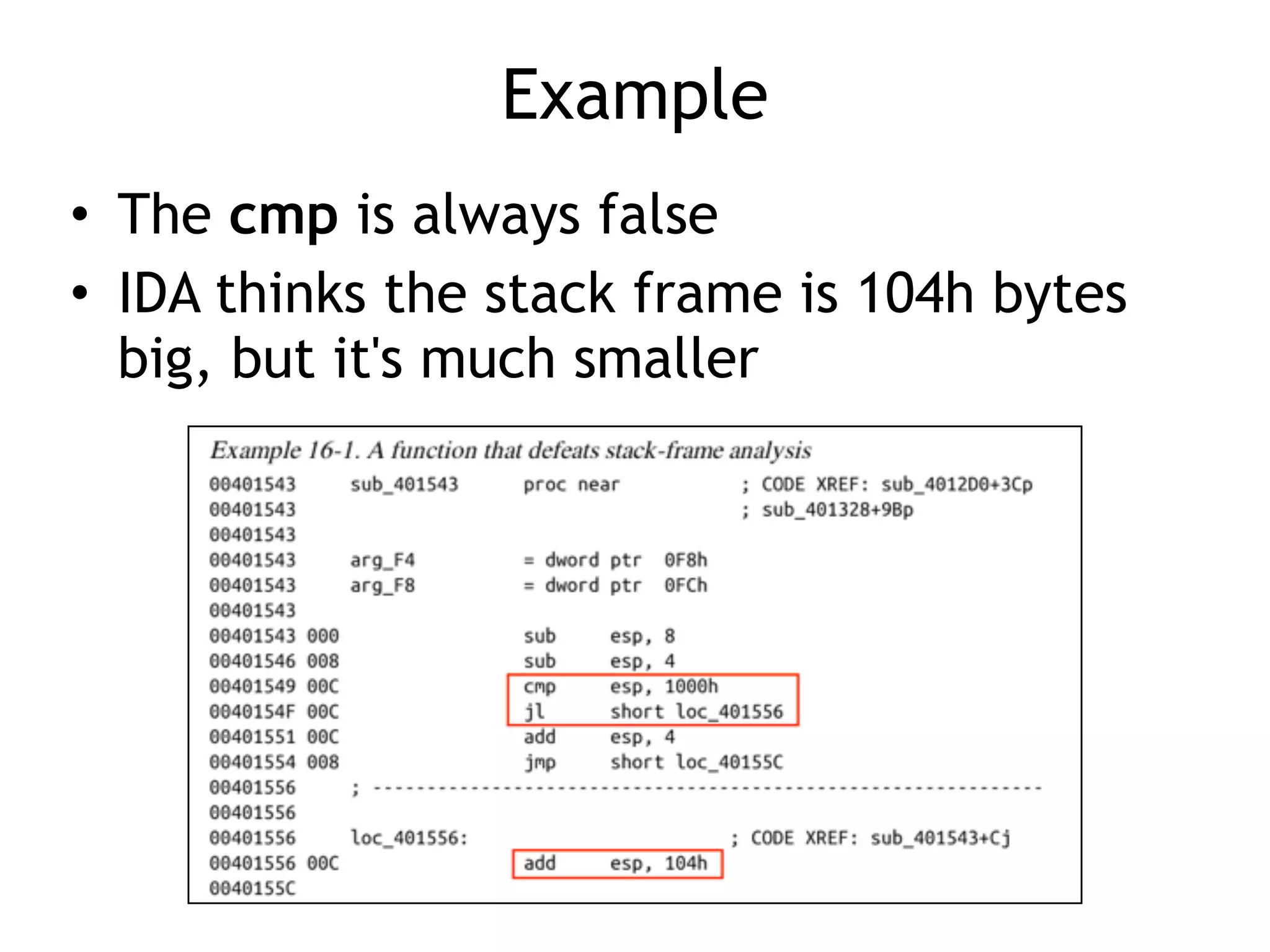
The document discusses various anti-disassembly techniques used by malware authors to obscure disassembly and prevent automated analysis. These include using jump instructions to trick linear disassemblers into the wrong offset, abusing return pointers and structured exception handlers, and misleading analysis of stack frames. Flow-oriented disassembly is more robust but can still be confused by techniques like impossible disassembly combinations and obscuring true flow control. Manual cleanup in a tool like IDA Pro is often needed to recover the correct disassembly.