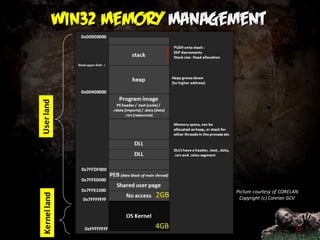
The document covers topics related to binary inspection and manipulation, specifically focusing on malware analysis and reverse engineering in x86 architecture. It discusses key concepts such as assembly language, CPU registers, common instructions, and the structure of processes and memory. The presentation highlights the evolution from static to dynamic analysis and emphasizes the use of Python for binary manipulation and analysis.





![Yeah, but what is reversing ???
Kind of a reconstruction
Code Binary
int main(int argc, char **argv) push ebp
{ mov ebp, esp
int gv = 0; // global mov dword_403394, 0
[…] […]
6](https://image.slidesharecdn.com/thewalking0xdead-130328073216-phpapp01/85/The-walking-0xDEAD-6-320.jpg)

![At the beginning, there was c0de
#include "stdafx.h"
#include <iostream>
using namespace std;
int add(int x, int y)
{
return x + y;
}
int main()
{
int a = 0, b = 0;
cout << "Enter a: ";
[…]
return 0;
}
8](https://image.slidesharecdn.com/thewalking0xdead-130328073216-phpapp01/85/The-walking-0xDEAD-8-320.jpg)
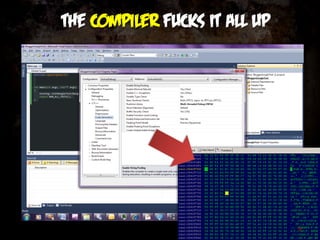







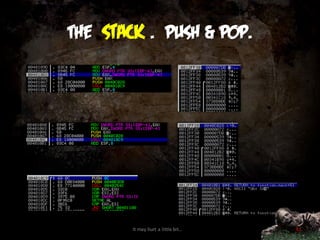
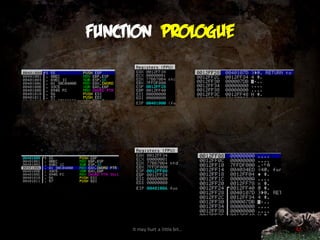
![Some common instructions
Read
mov eax, [ecx]
mov eax, [00401000]
Write
mov ebx, 0x20
mov [ebx+0x1C], ecx
It may hurt a little bit… 17](https://image.slidesharecdn.com/thewalking0xdead-130328073216-phpapp01/85/The-walking-0xDEAD-17-320.jpg)

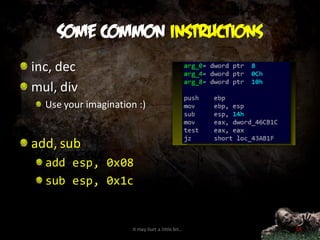
![Some common instructions
lea dst, src
lea eax, [esi*2]
lea ecx, [esi+ecx]
shl, shr
shl eax, 2
It may hurt a little bit… 20](https://image.slidesharecdn.com/thewalking0xdead-130328073216-phpapp01/85/The-walking-0xDEAD-20-320.jpg)

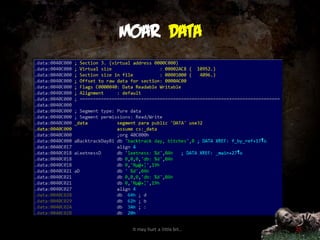
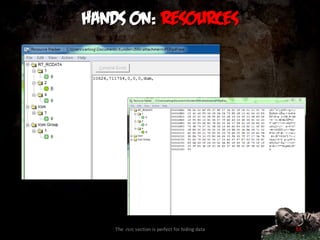
![Important segments
.data: statically allocated *initialized*
int g = 1; char str[] = „yomamma“;
.bss: statically allocated *UNinitialized*
int var; char *ptr;
.rdata: read-only data (const c = 0)
It may hurt a little bit… 23](https://image.slidesharecdn.com/thewalking0xdead-130328073216-phpapp01/85/The-walking-0xDEAD-23-320.jpg)