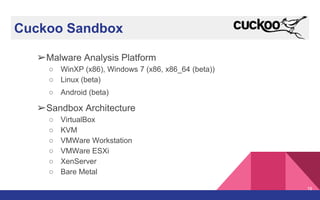
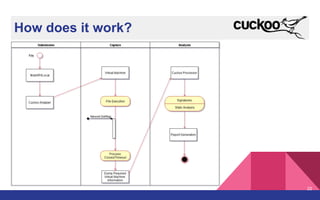
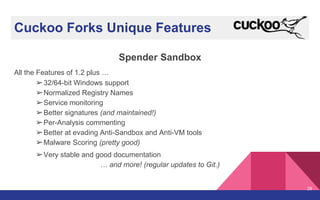
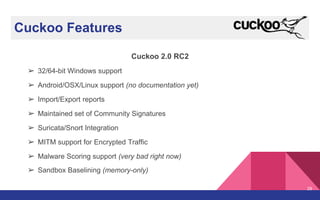
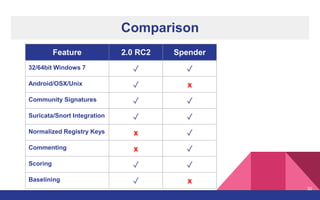
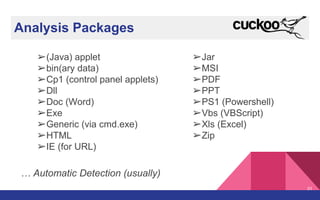
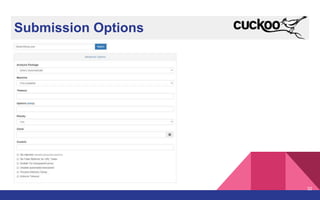
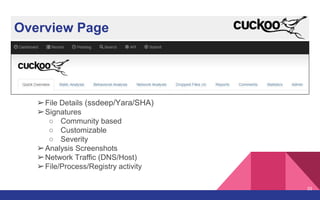
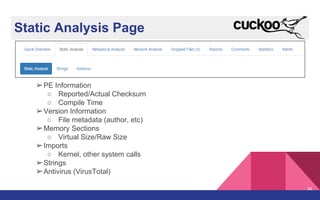
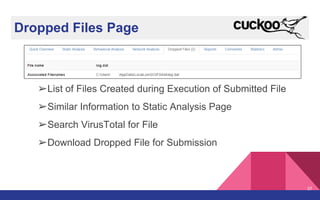
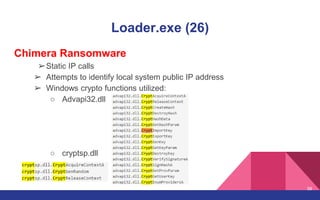
The document presents a detailed overview of dynamic malware analysis using Cuckoo Sandbox, including its architecture, various types of analysis (dynamic and static), and countermeasures against detection. It covers the challenges in analyzing malware, such as evasion techniques used by malware authors, and provides practical insights on how to set up a malware analysis environment. Additionally, it introduces tools like vmcloak and pafish to enhance the effectiveness of malware analysis.