The document presents an introduction to binary exploitation by Gábor Pék, who discusses his background in virtualization and malware security. It covers fundamental concepts including compilers, native binaries, program memory layout, and types of bugs, along with examples of function calls and memory management. The document also addresses memory corruption errors, common vulnerabilities, and various protections and exploitation techniques.





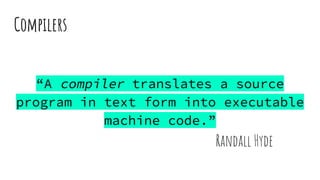
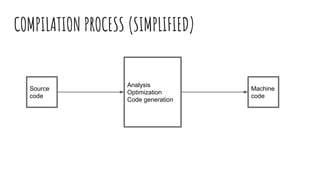
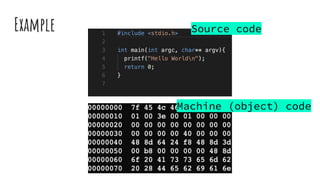
![Basic x86 system
Source: [1]](https://image.slidesharecdn.com/anintroductiontobinaryexploitation-190215010851/85/Hacker-Thursdays-An-introduction-to-binary-exploitation-12-320.jpg)
![Cpu registers (32-bit)
Source: [1]](https://image.slidesharecdn.com/anintroductiontobinaryexploitation-190215010851/85/Hacker-Thursdays-An-introduction-to-binary-exploitation-13-320.jpg)


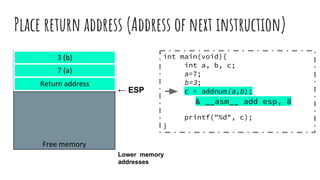
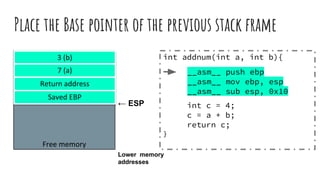
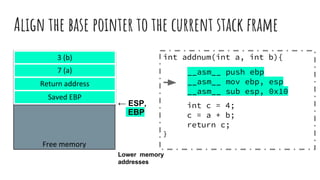
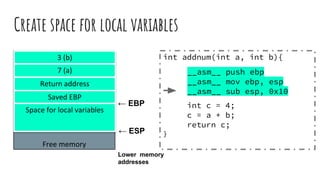
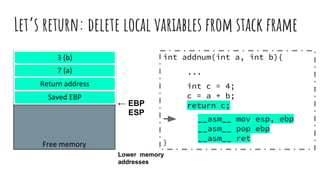
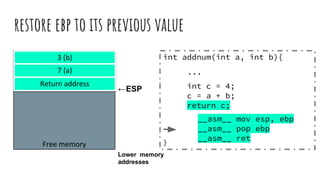
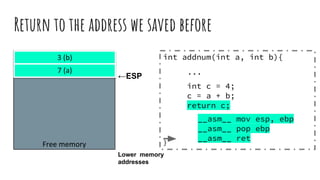
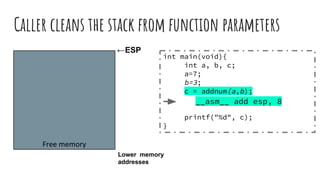





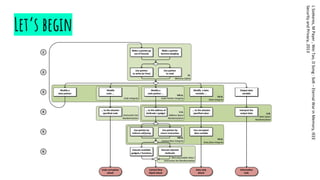
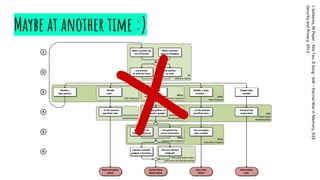
![Readings
[1] Randall Hyde: Write Great Code, Volume 2 - Thinking
low-level, writing high-level, No Starch Press, 2006
[2] L Szekeres, M Payer , Wei Tao, D Song : SoK – Eternal
War in Memory, IEEE Security and Privacy, 2013
[3] Intel® 64 and IA-32 Architectures Software Developer
Manuals, 2016](https://image.slidesharecdn.com/anintroductiontobinaryexploitation-190215010851/85/Hacker-Thursdays-An-introduction-to-binary-exploitation-41-320.jpg)