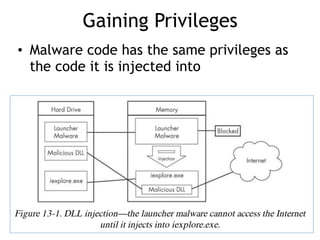
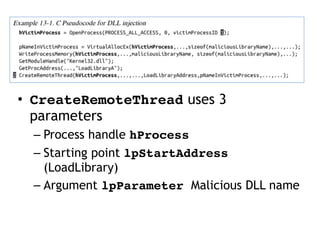
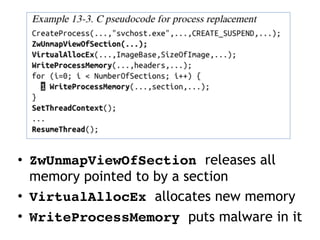
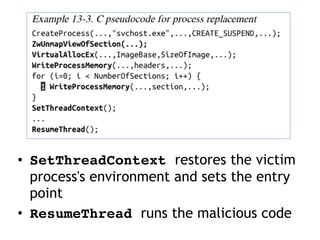
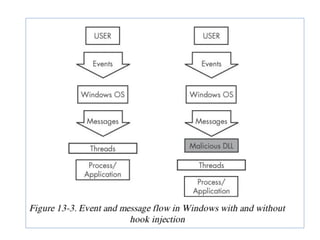
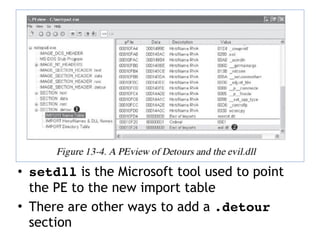
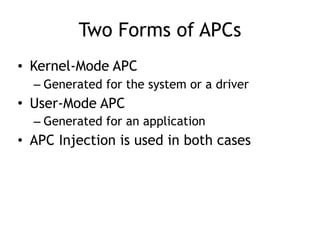
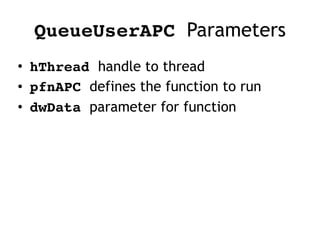
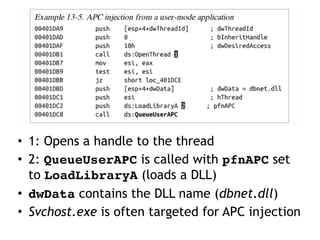
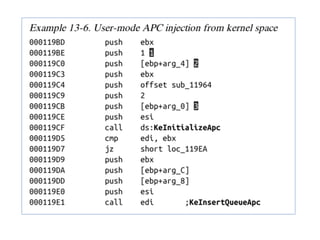
This document discusses various covert techniques used by malware to launch and conceal itself, including process injection, process replacement, and APC injection. Process injection techniques like DLL injection and direct injection allow malware to inject malicious code into running processes to hide its behavior and bypass security mechanisms. Process replacement involves overwriting the memory of a running process with malware code to disguise itself. APC injection uses asynchronous procedure calls to direct a thread to execute malicious code when it is in an alterable state.