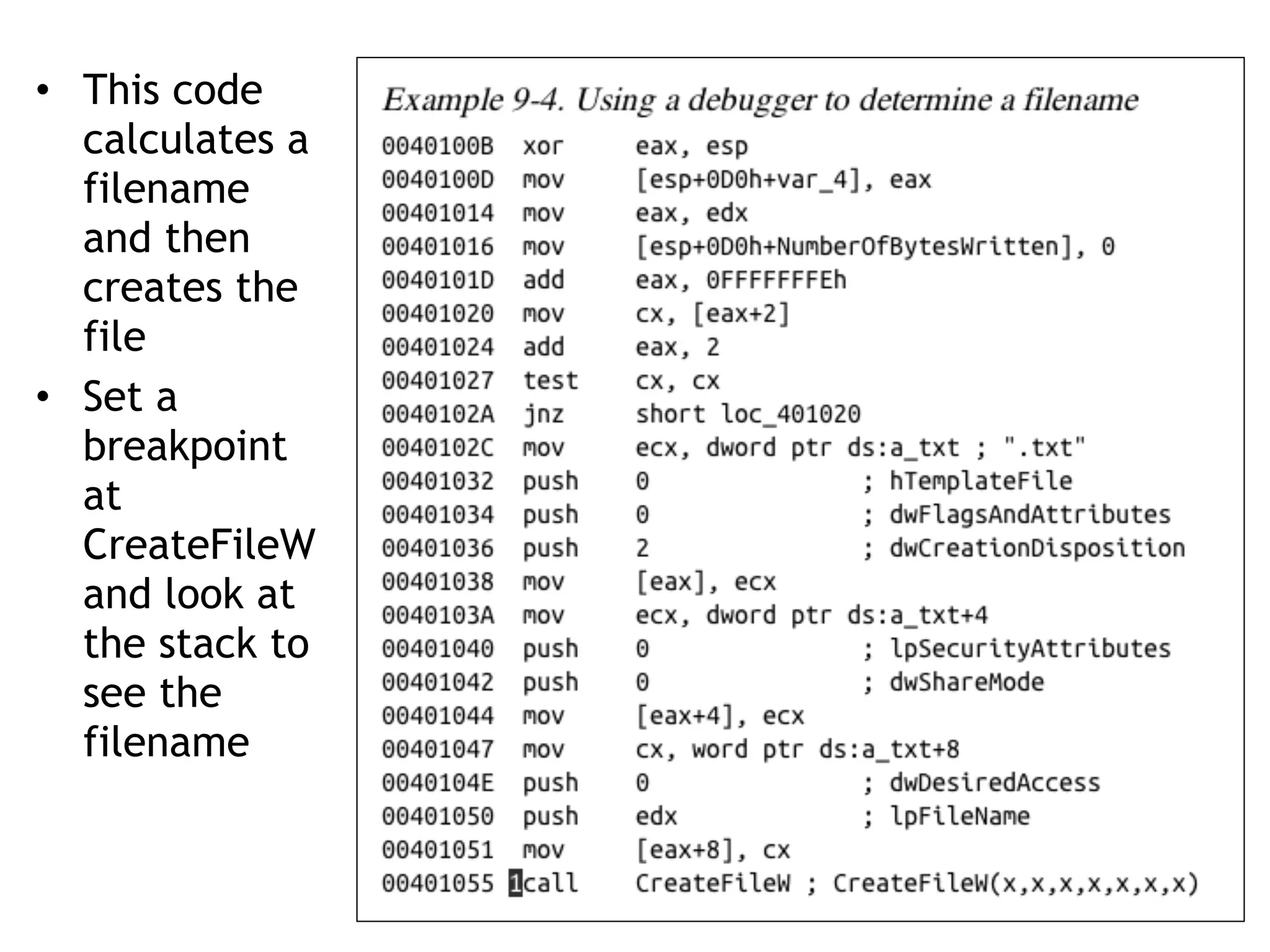
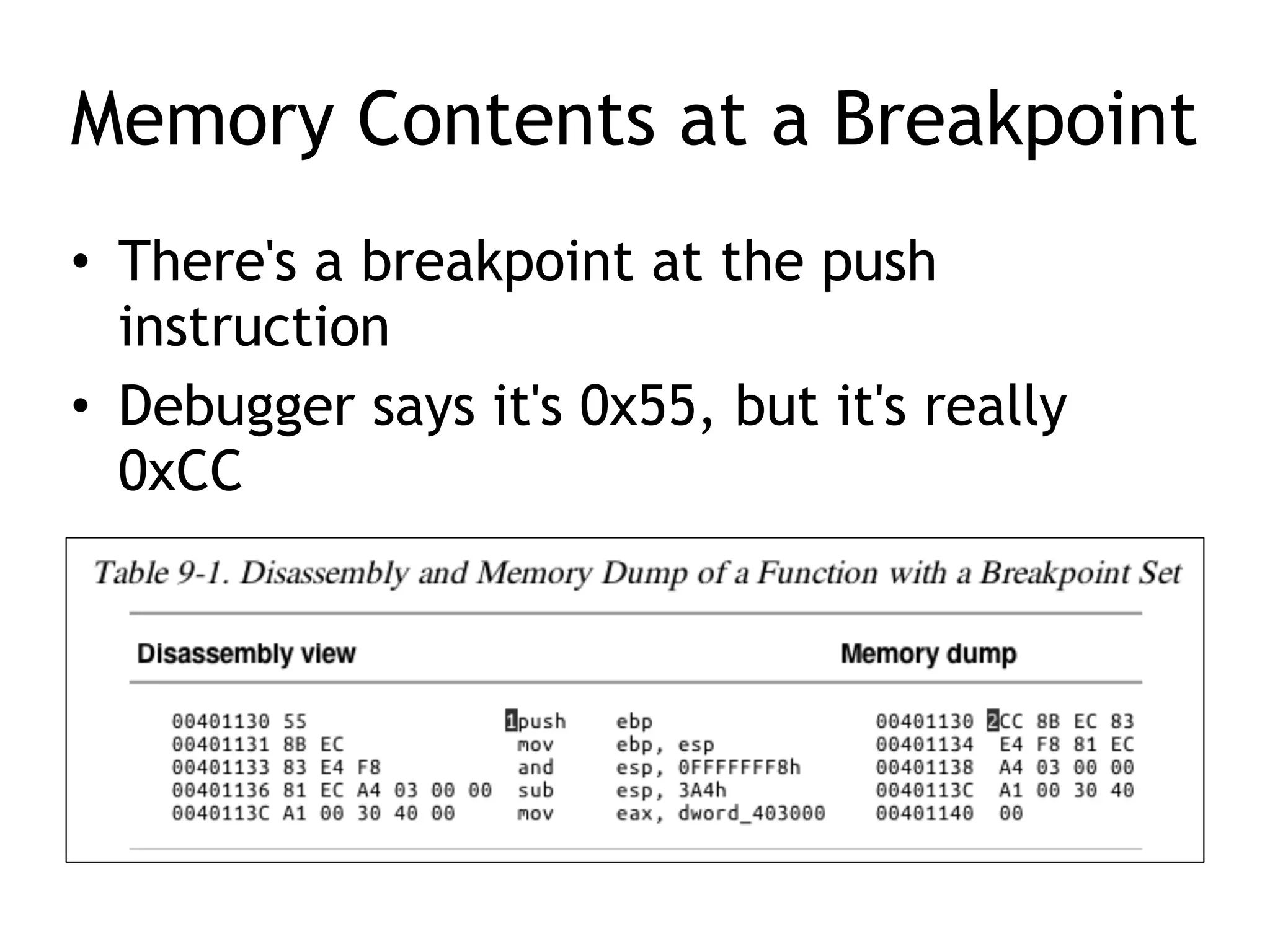
Chapter 8 of 'Practical Malware Analysis' covers the differences between disassemblers and debuggers, highlighting tools like OllyDbg for user-mode debugging and Windbg for kernel-mode debugging. It explains single-stepping, breakpoints, and exceptions, detailing how debuggers manage program execution and the various types of breakpoints that can be set. The chapter emphasizes practical applications of debugging in malware analysis, including modifying execution and handling exceptions.