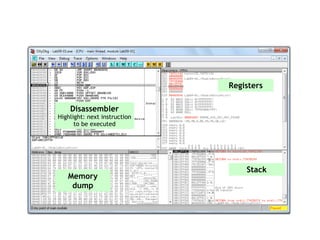
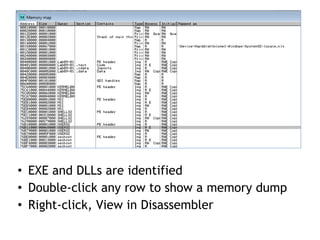
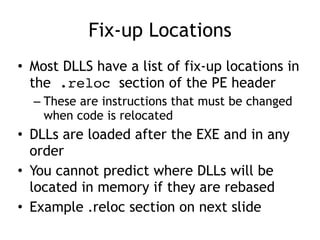
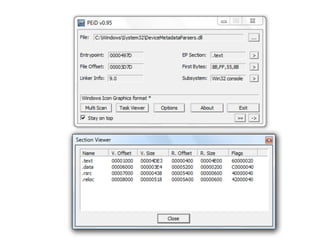
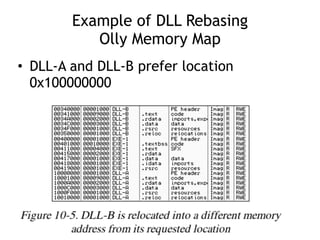
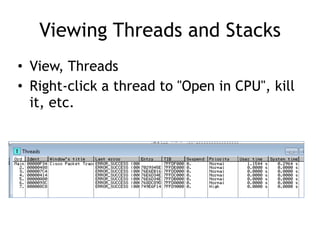
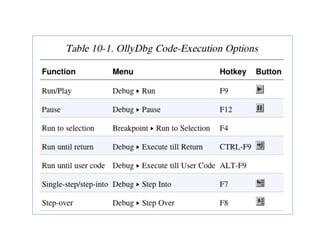
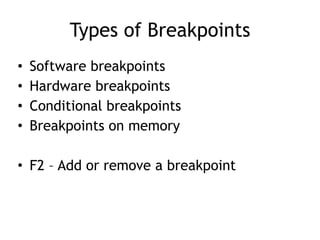
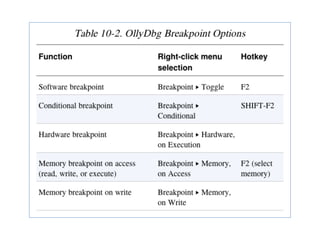
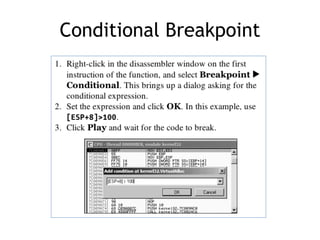
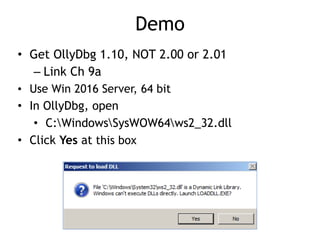
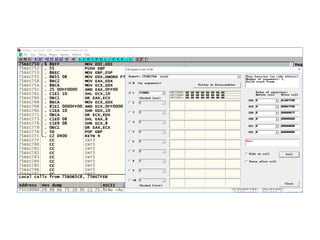
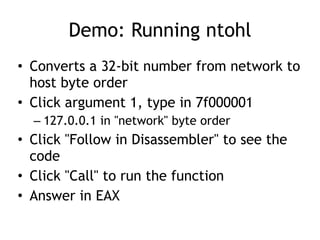
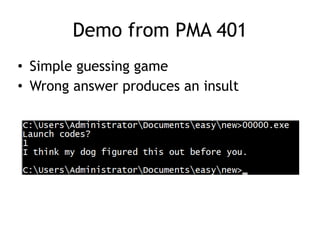
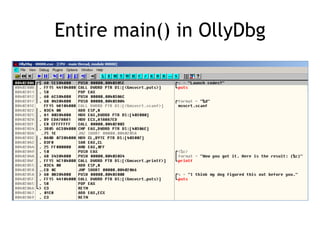
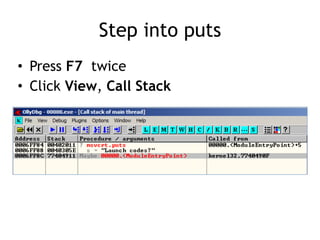
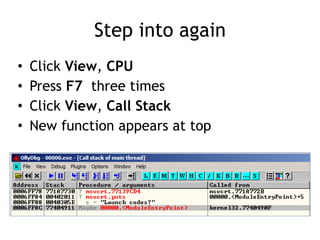
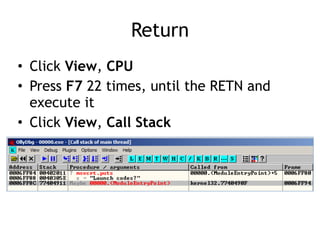
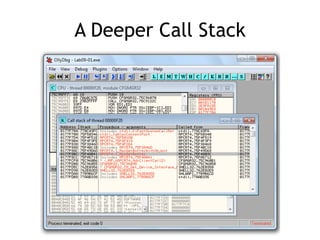
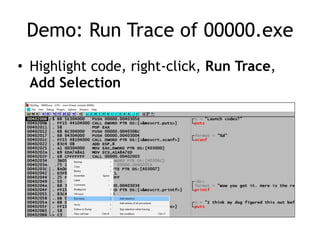
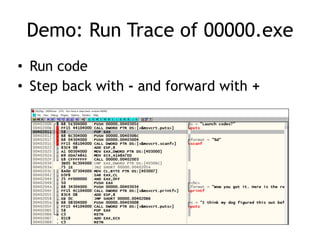
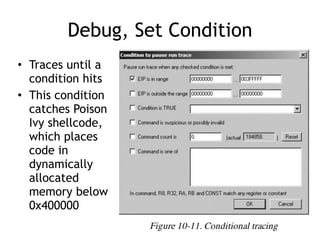
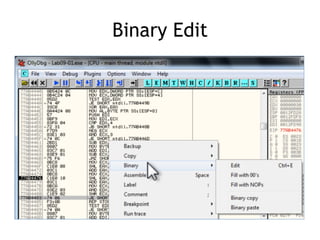
OllyDbg is a free debugger that can be used to analyze malware. It was originally developed over a decade ago for cracking software but is now widely used for malware analysis and exploit development. OllyDbg allows users to load EXEs and DLLs directly or attach to running processes to debug malware. It provides useful interfaces like a disassembler, register and memory views. OllyDbg also supports setting various breakpoints, calling functions, modifying data, and tracing program execution which helps analysts understand malware behavior.