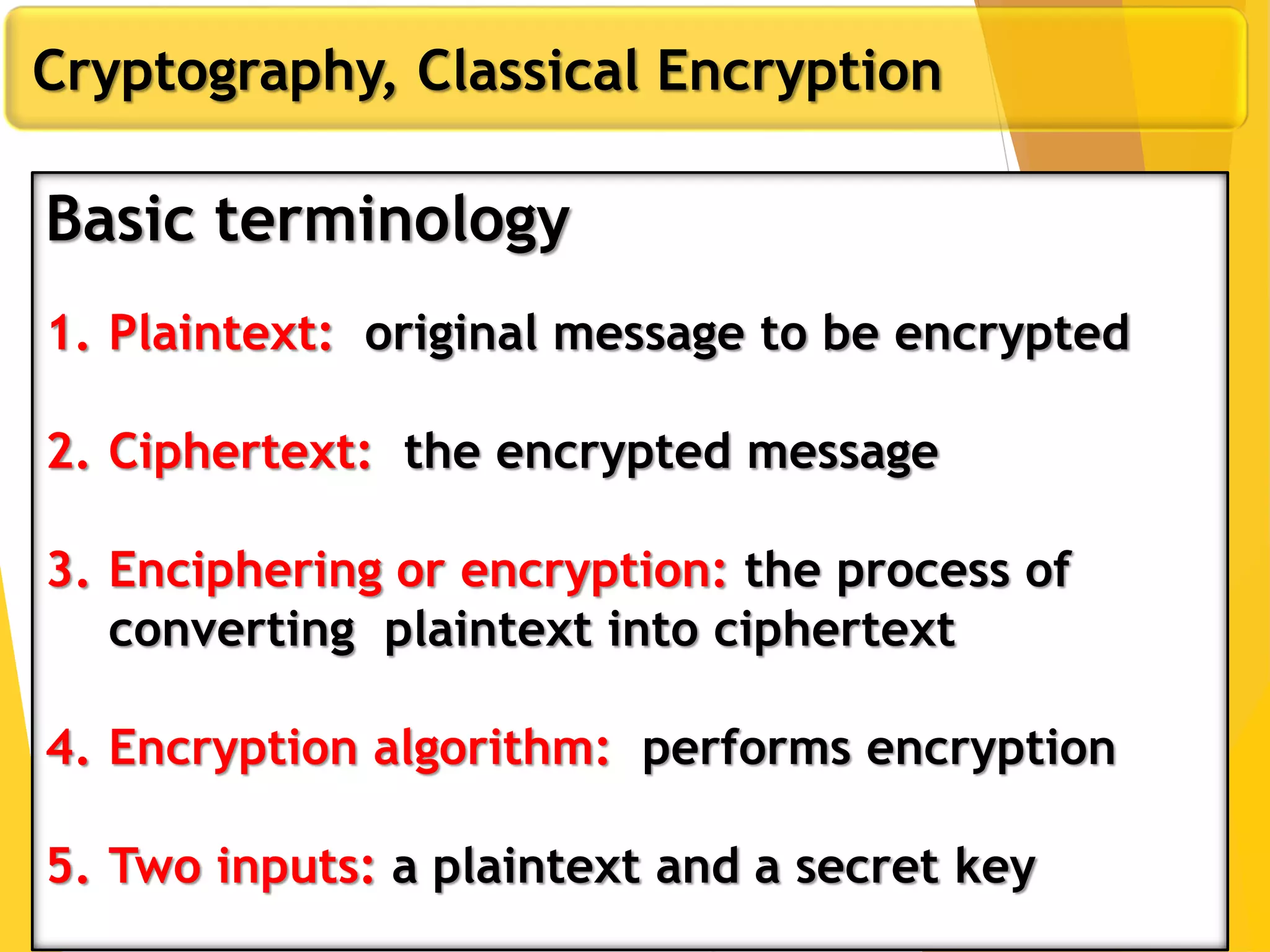
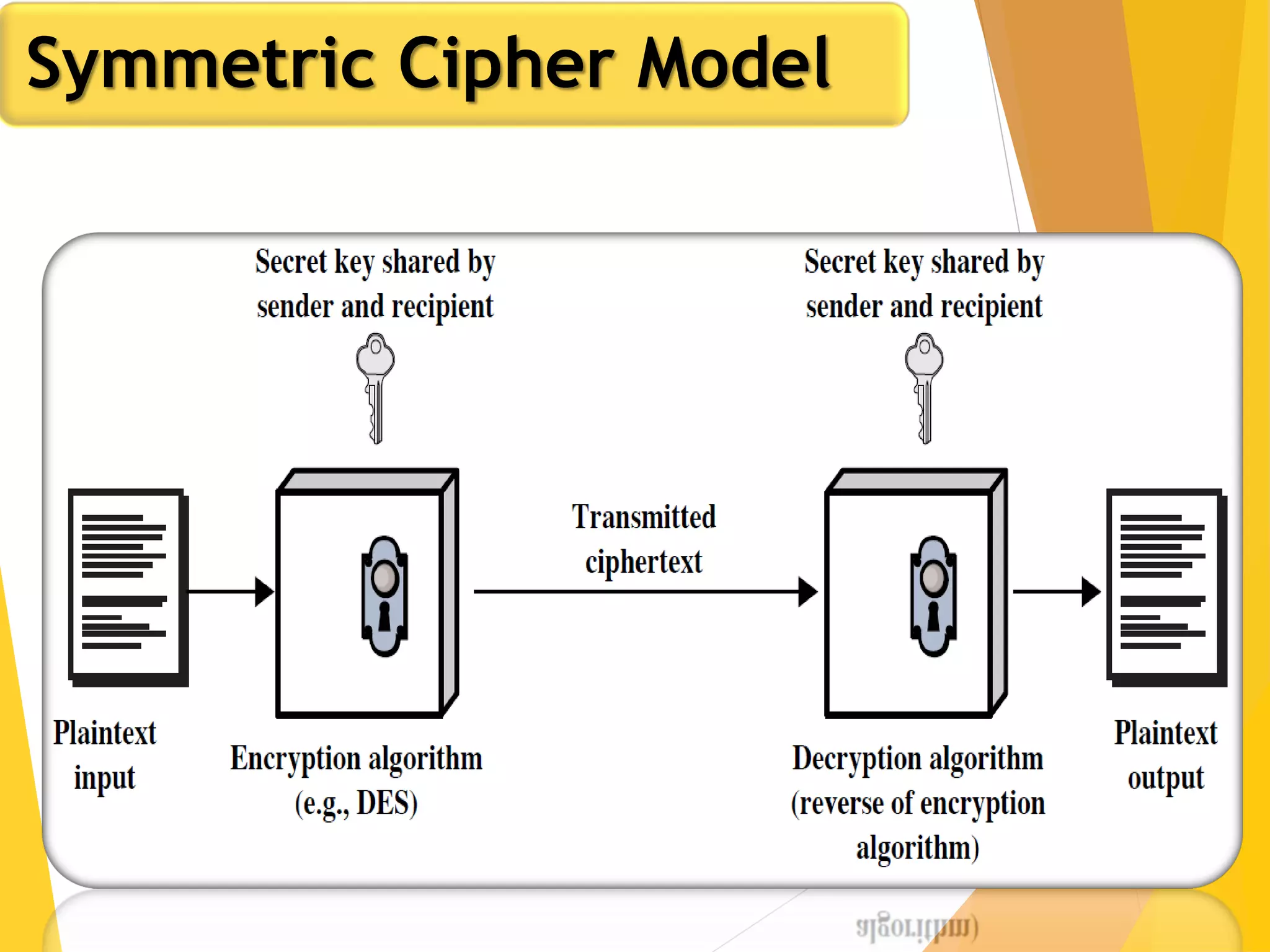
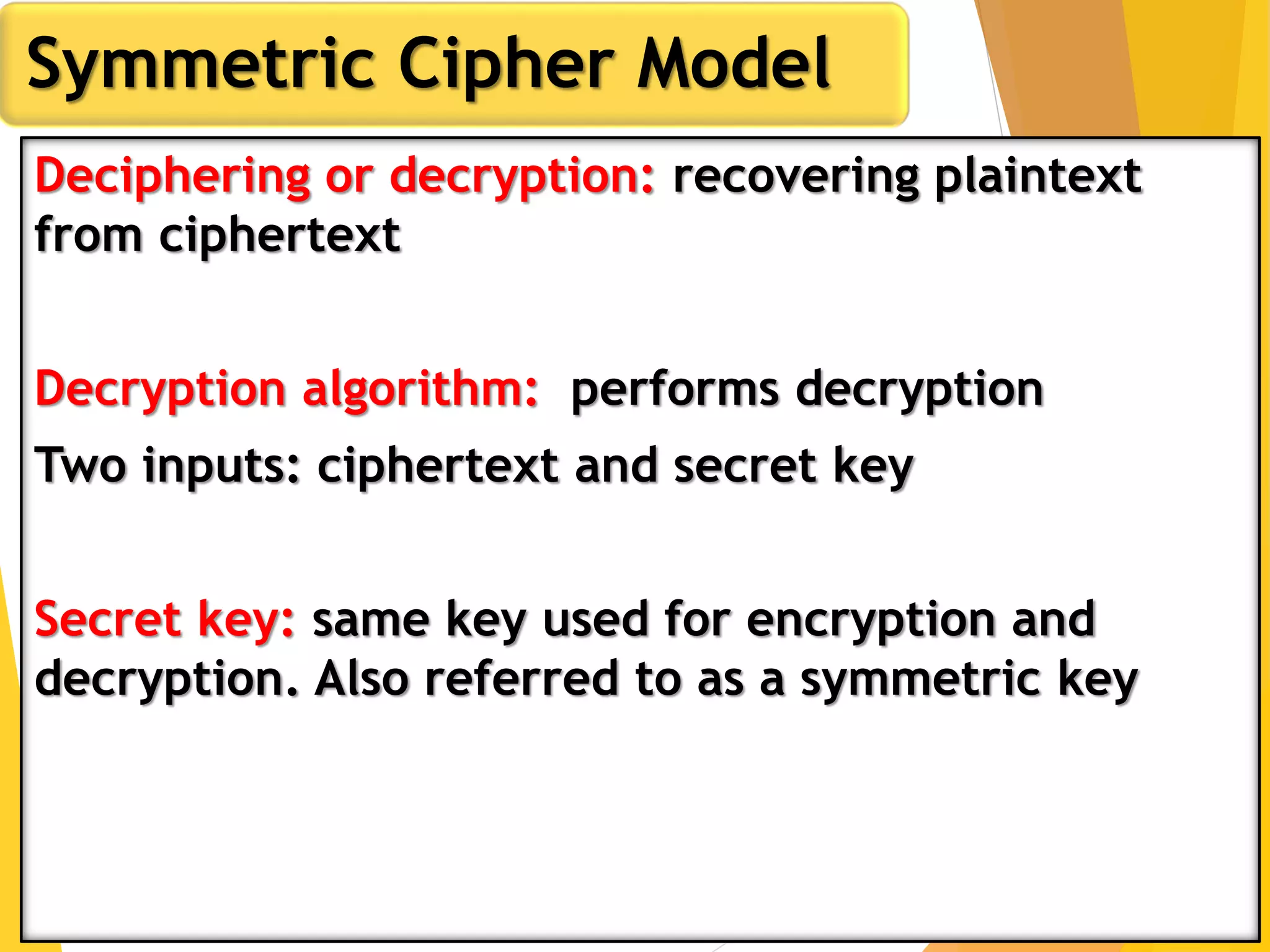
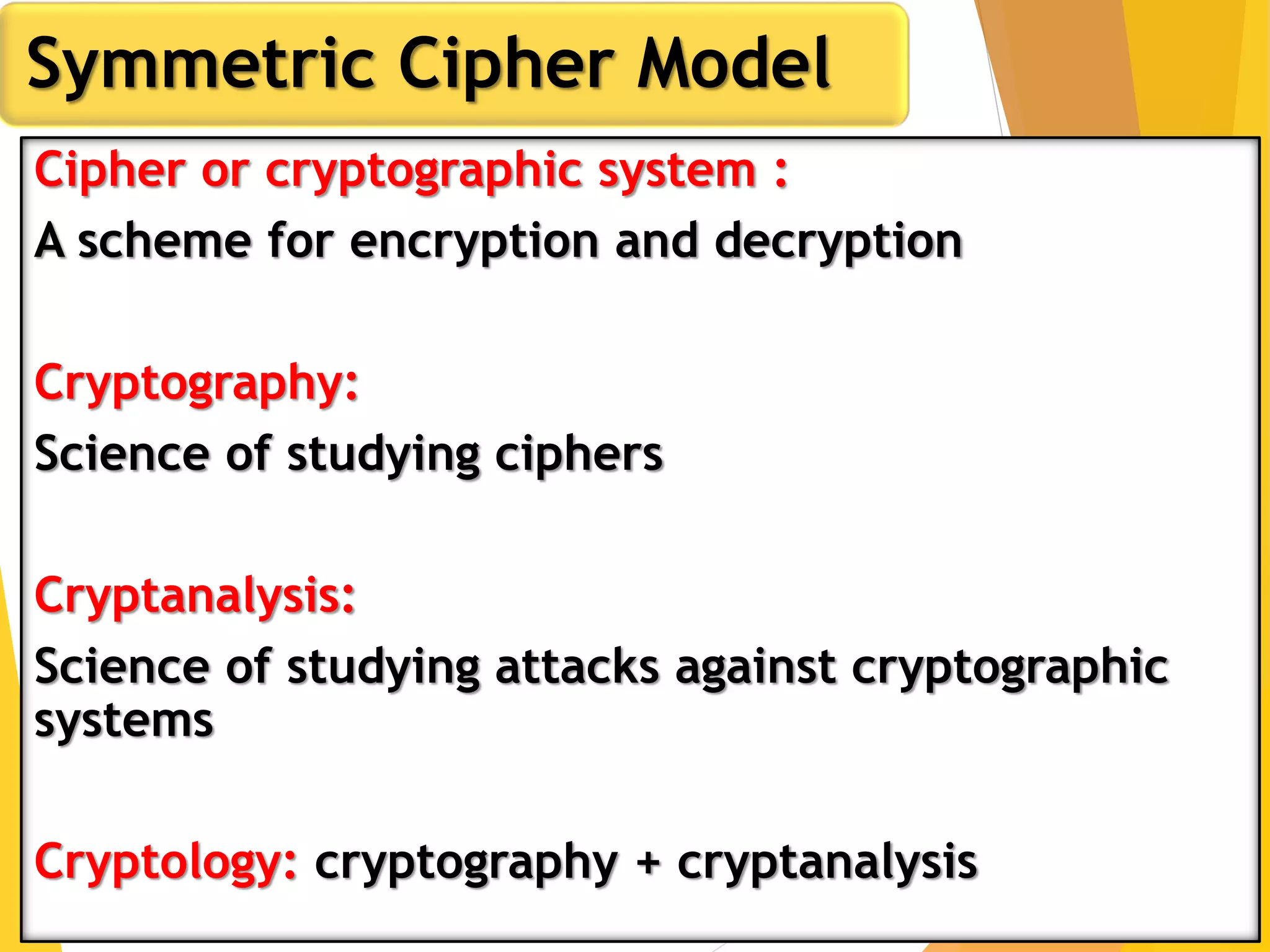
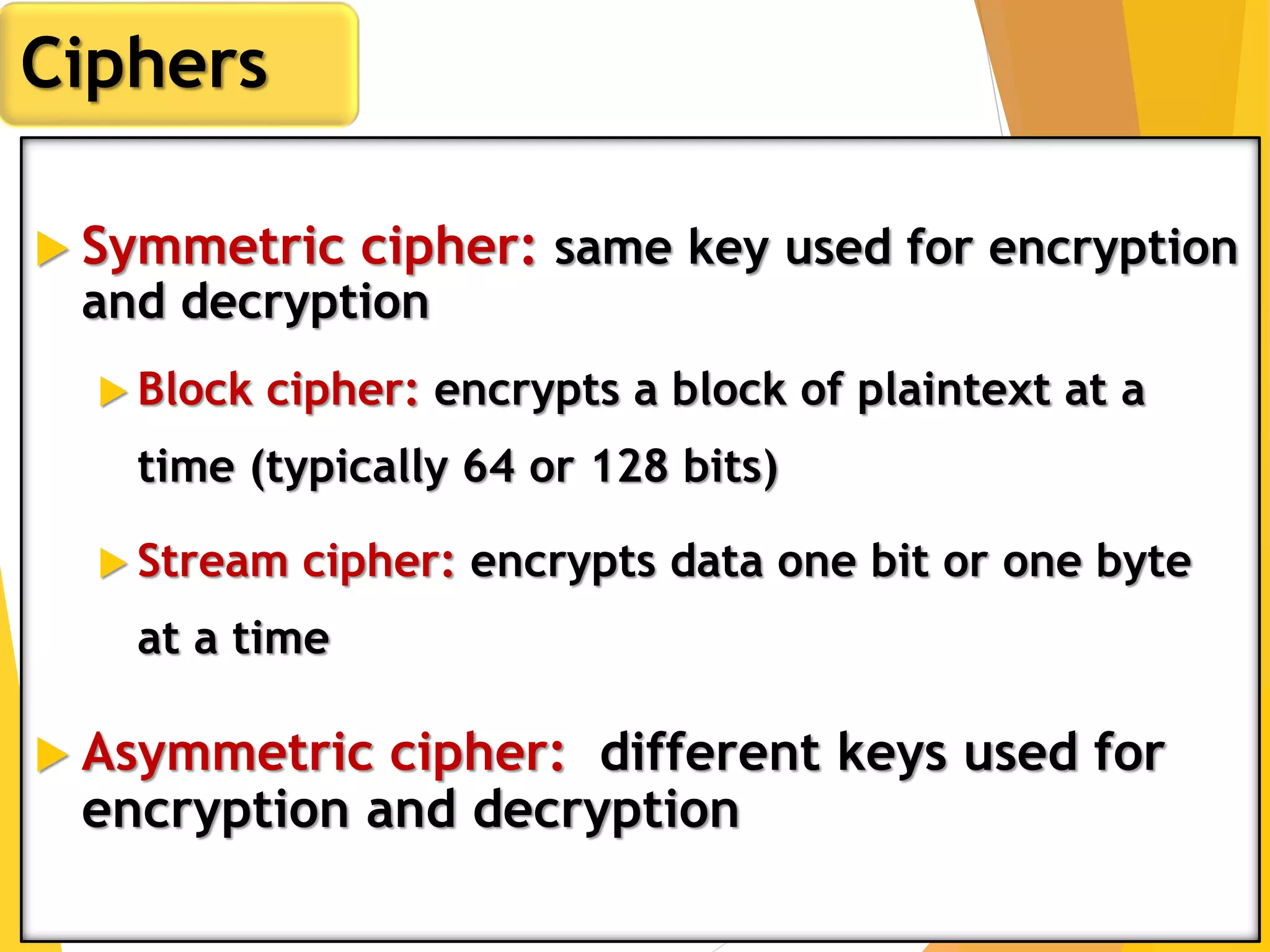
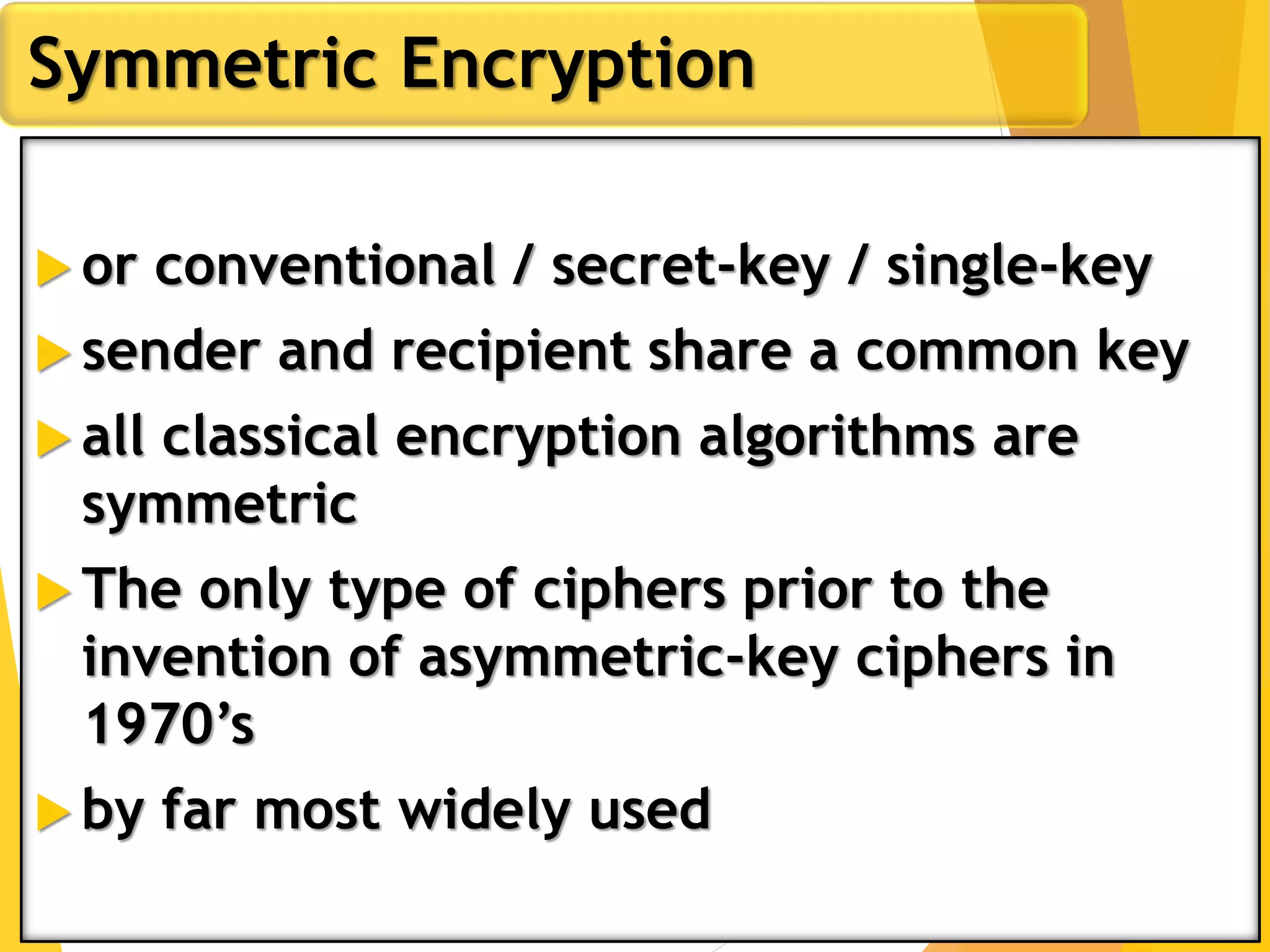
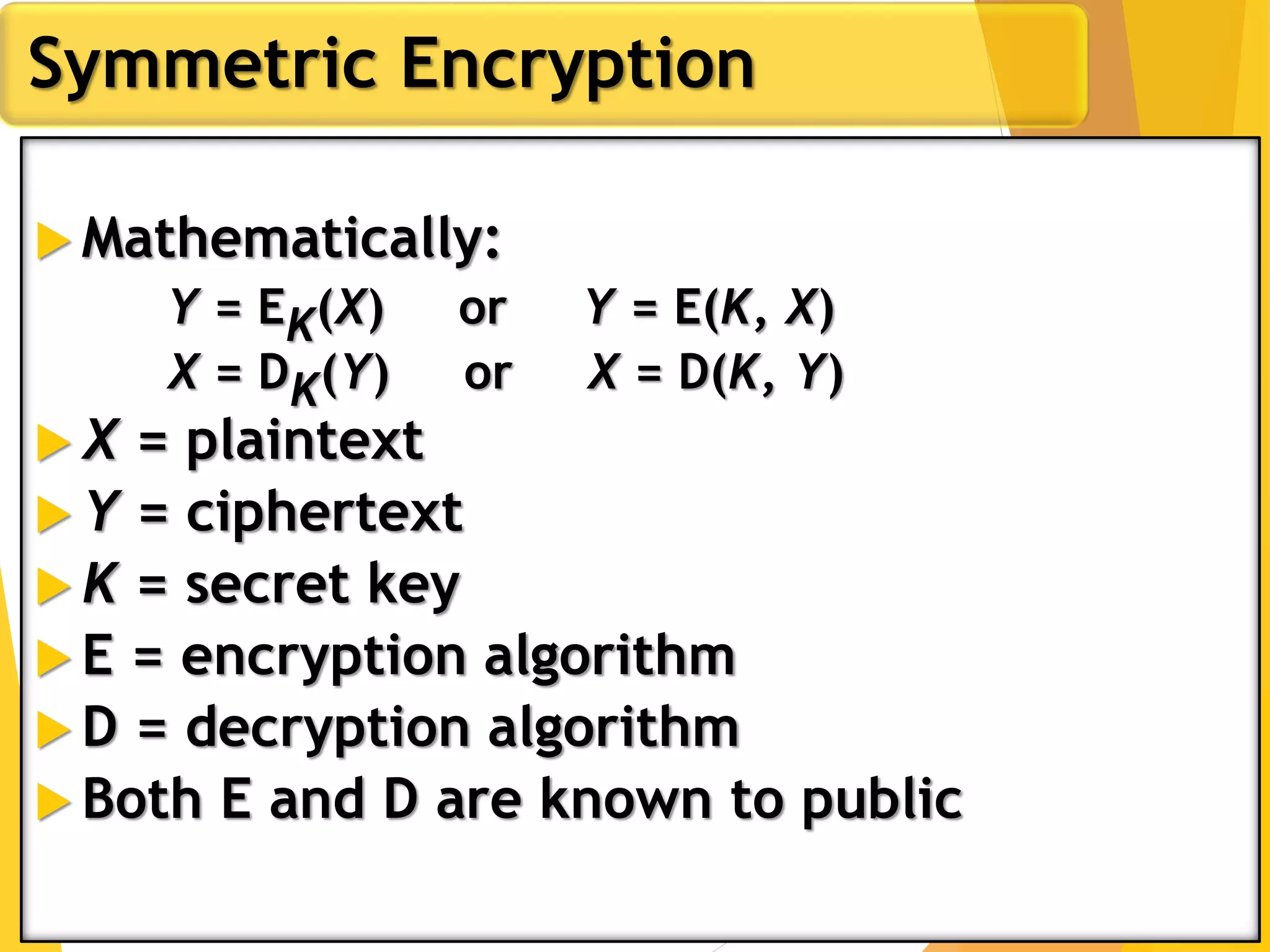
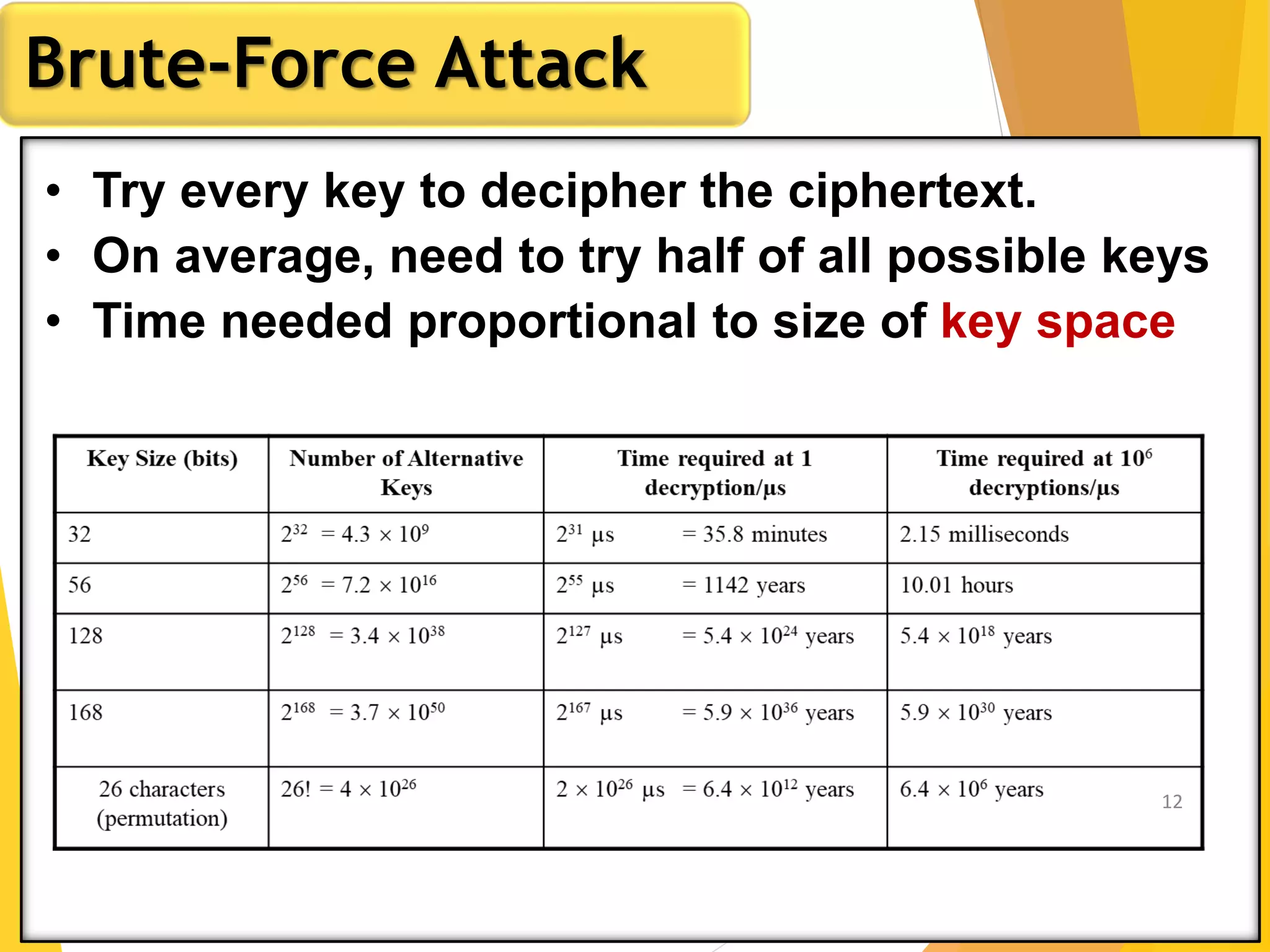
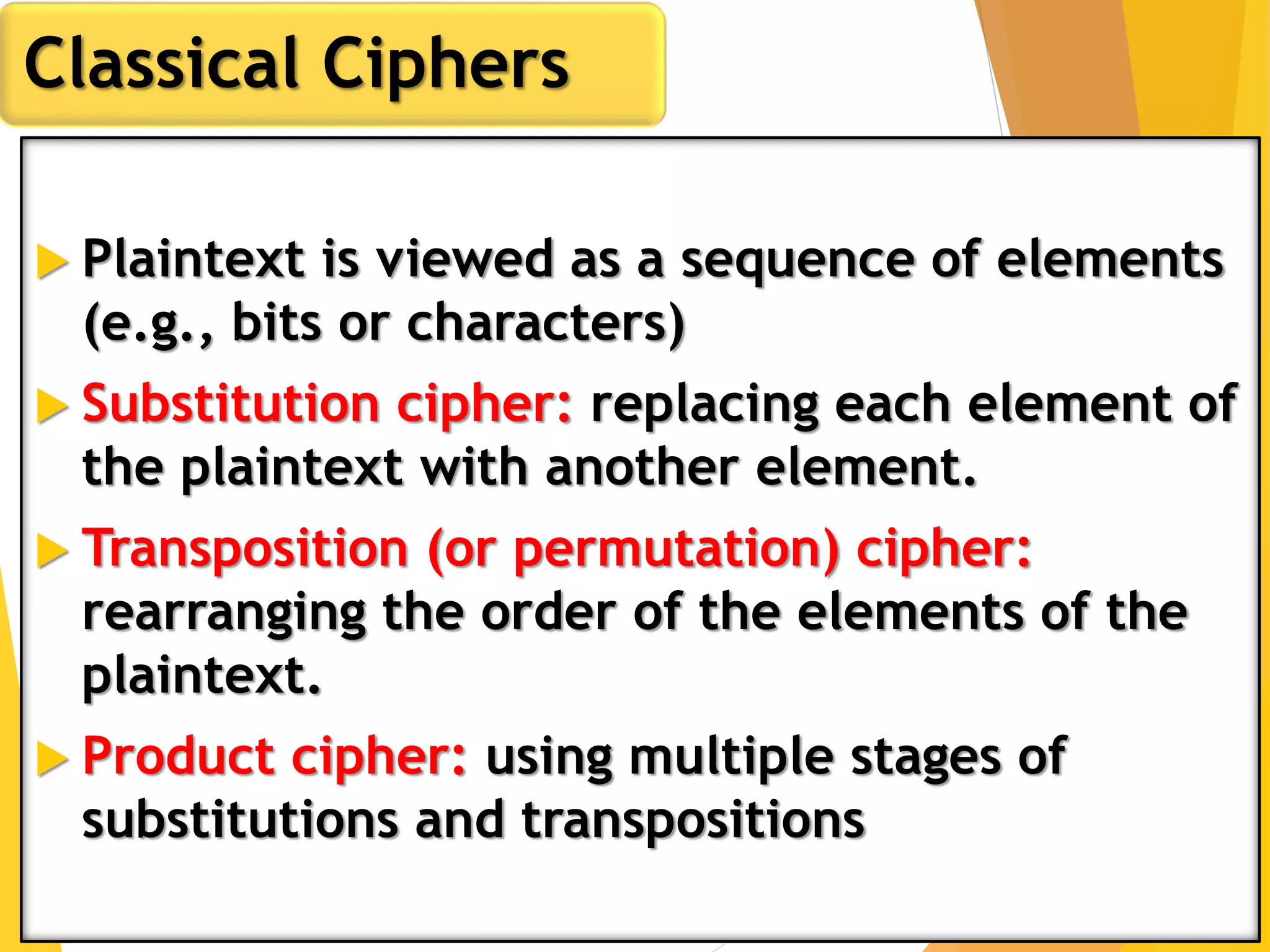
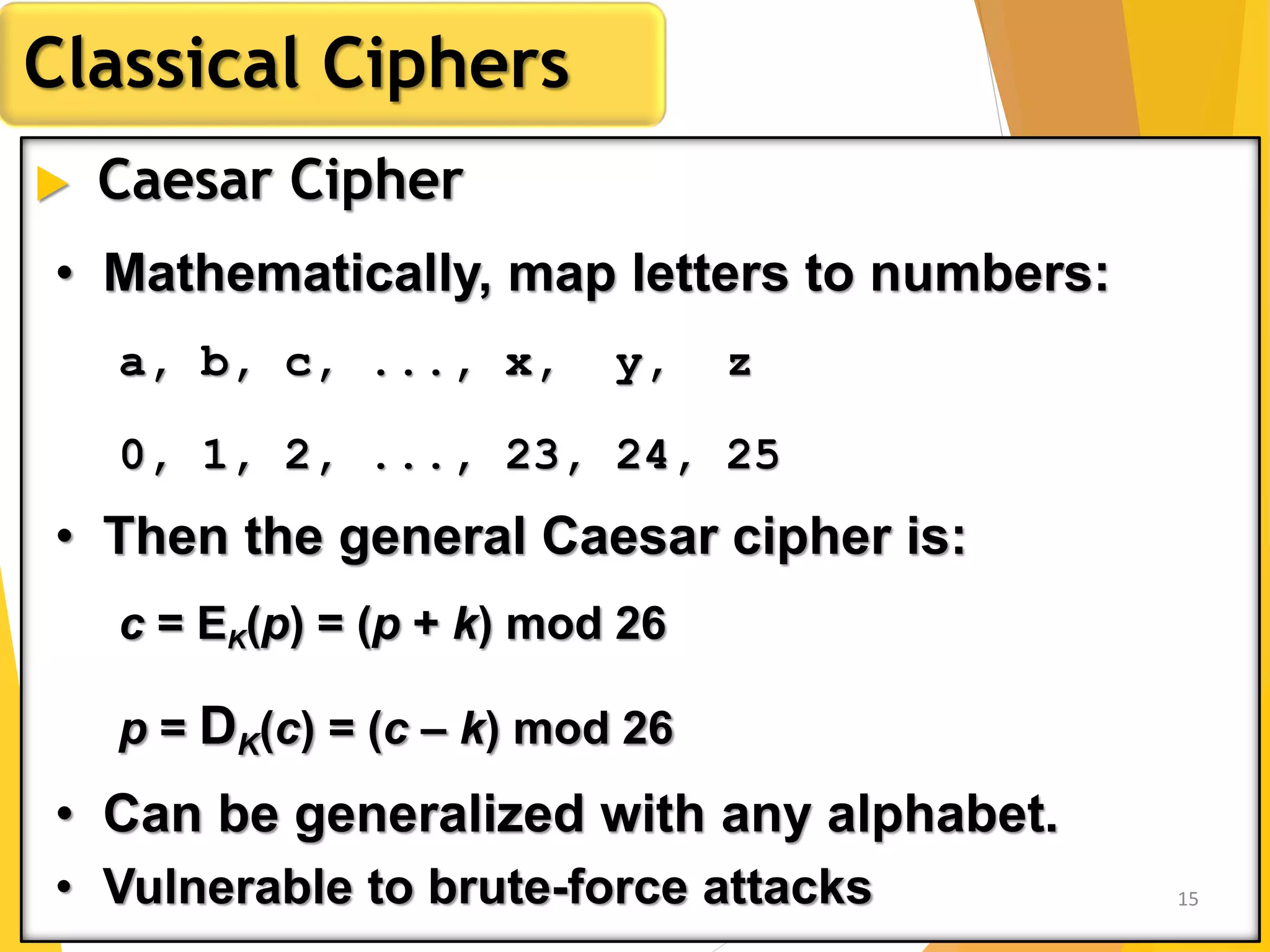
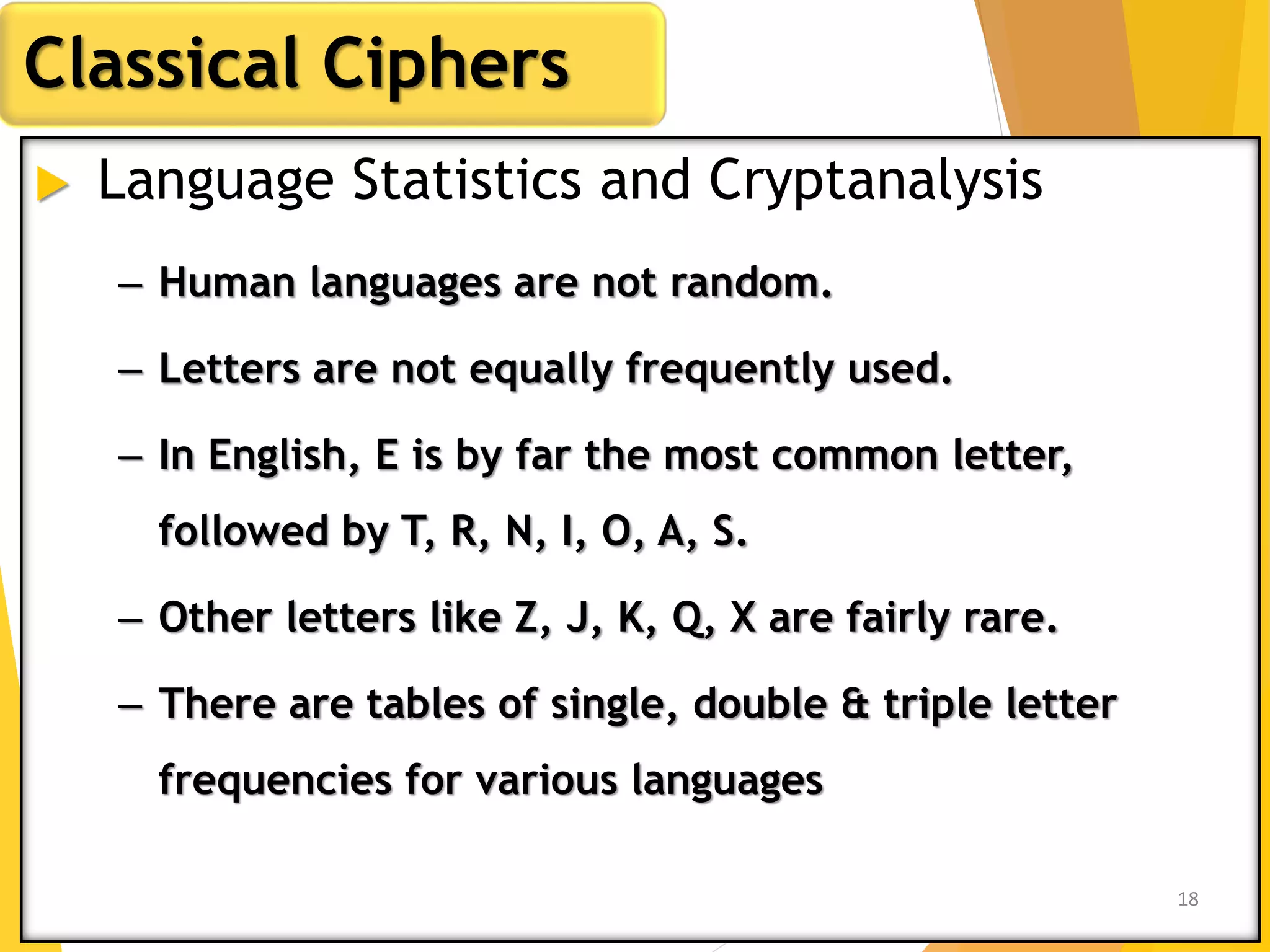
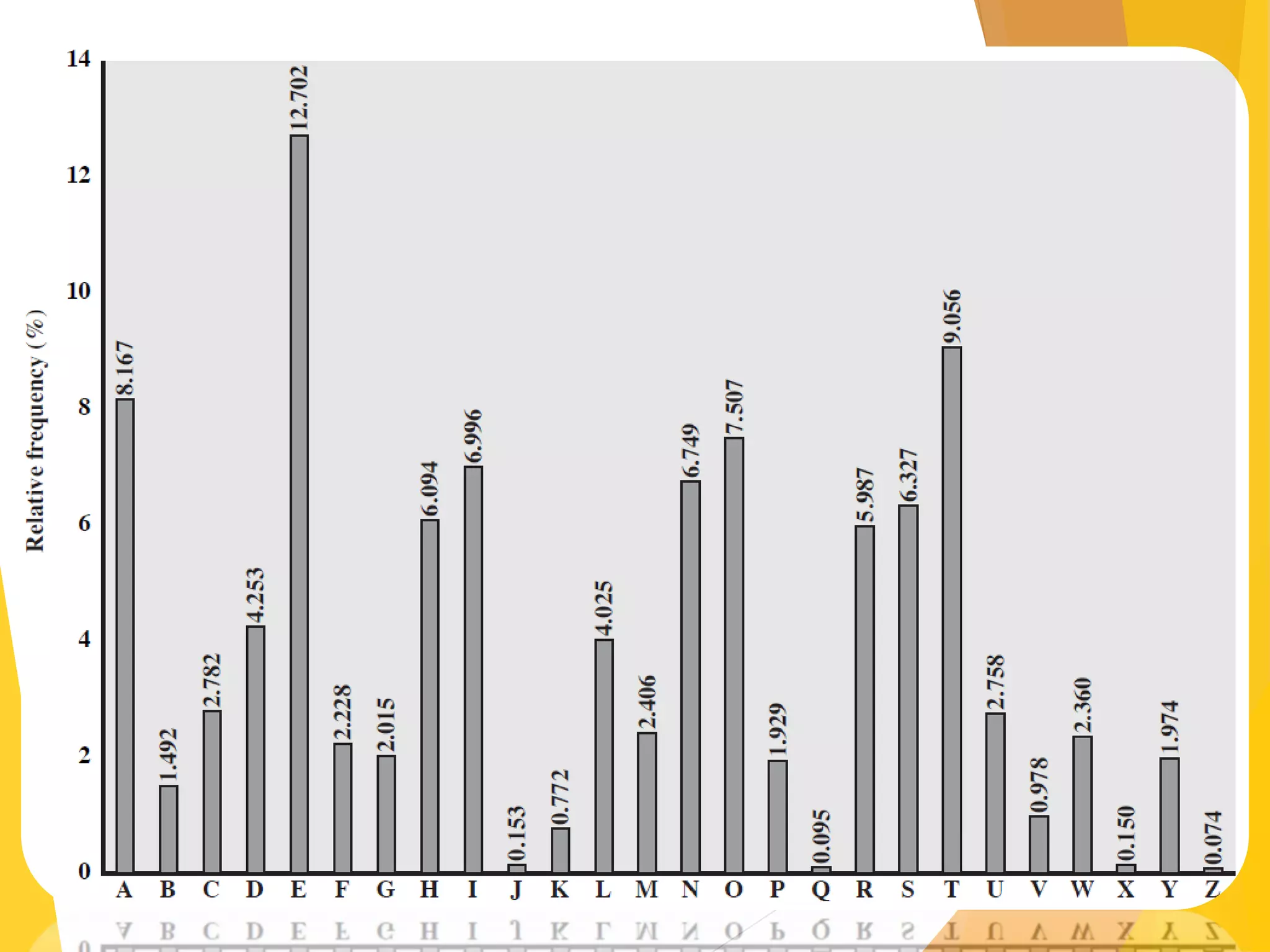
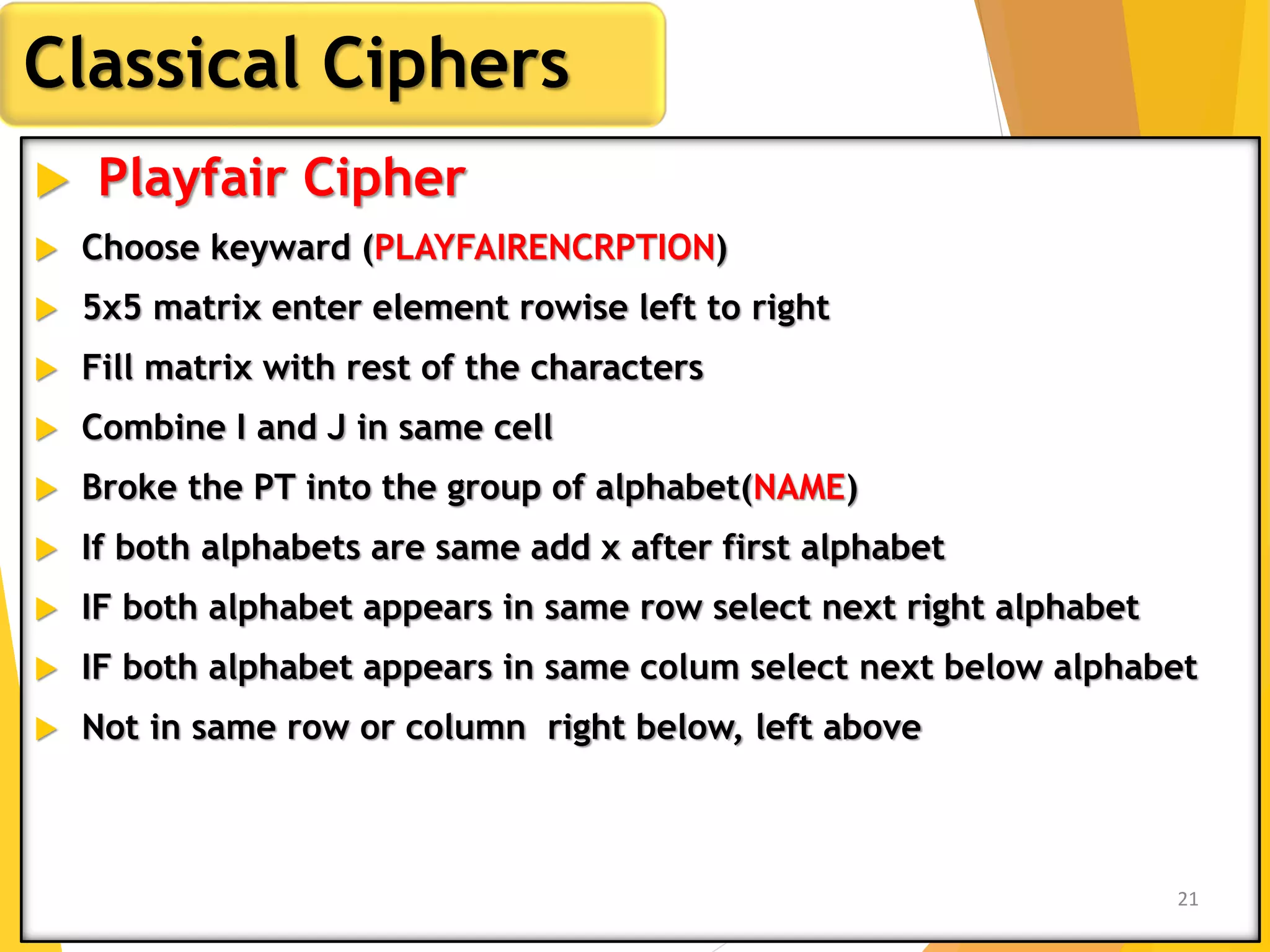
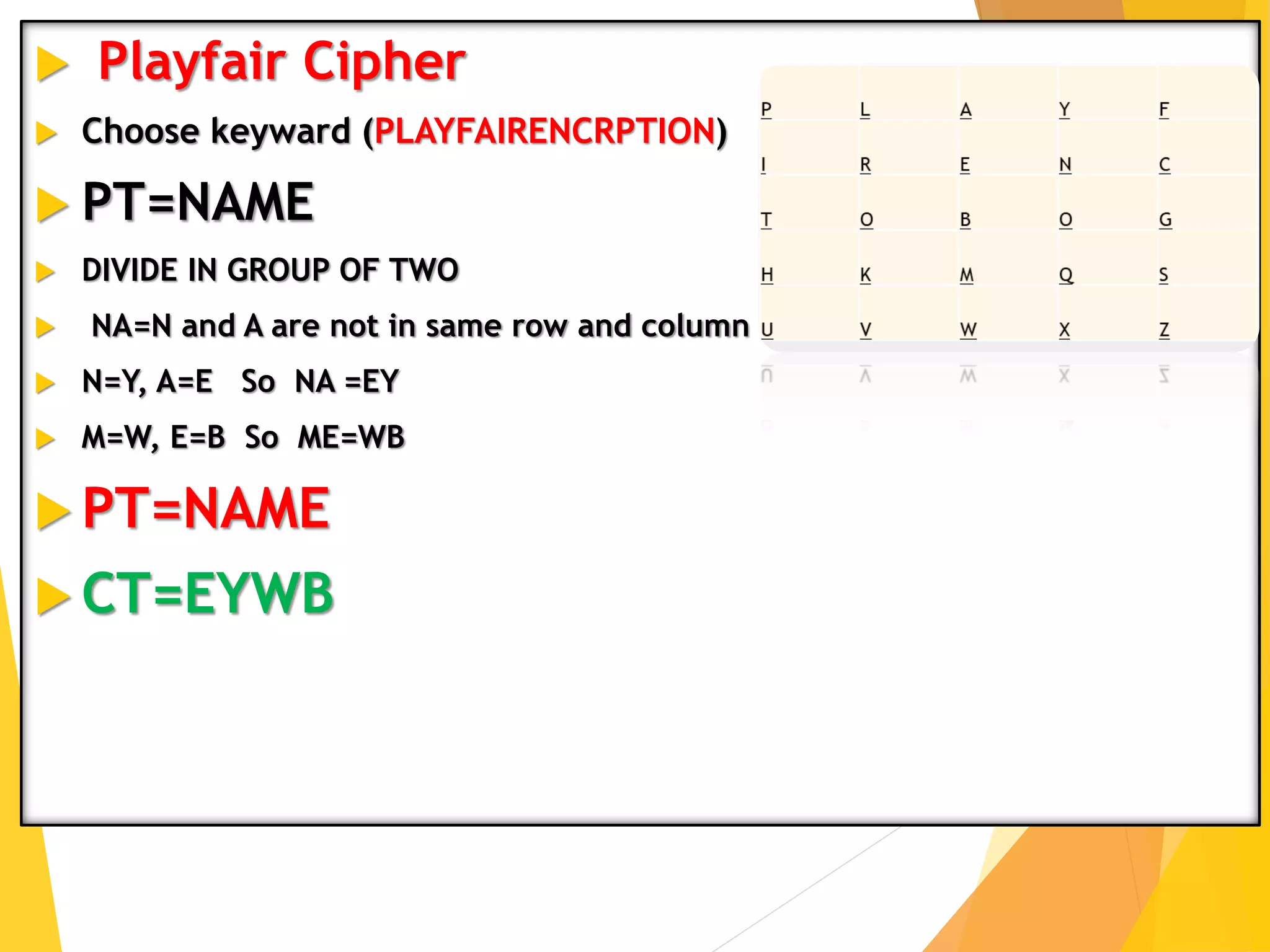
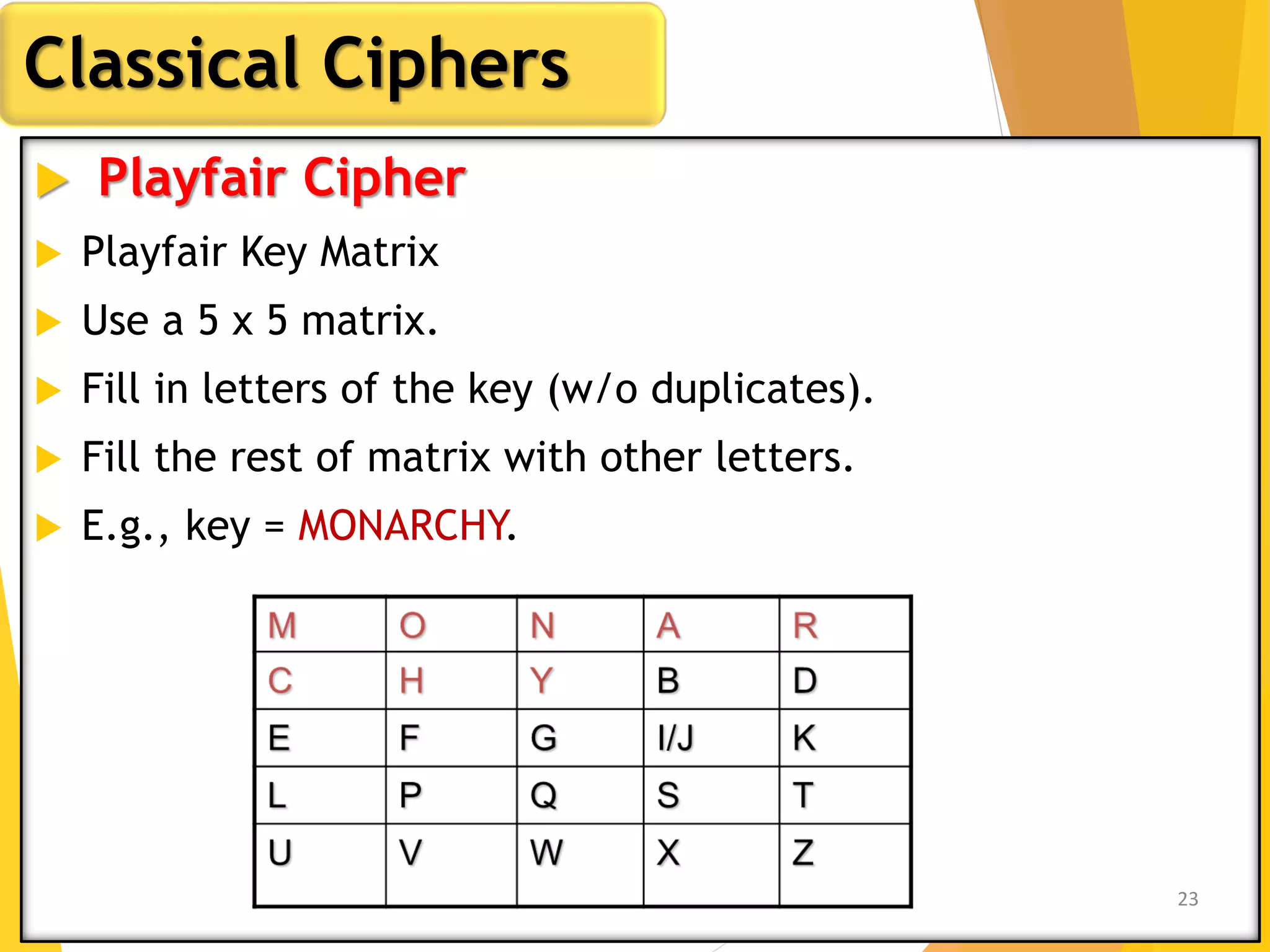
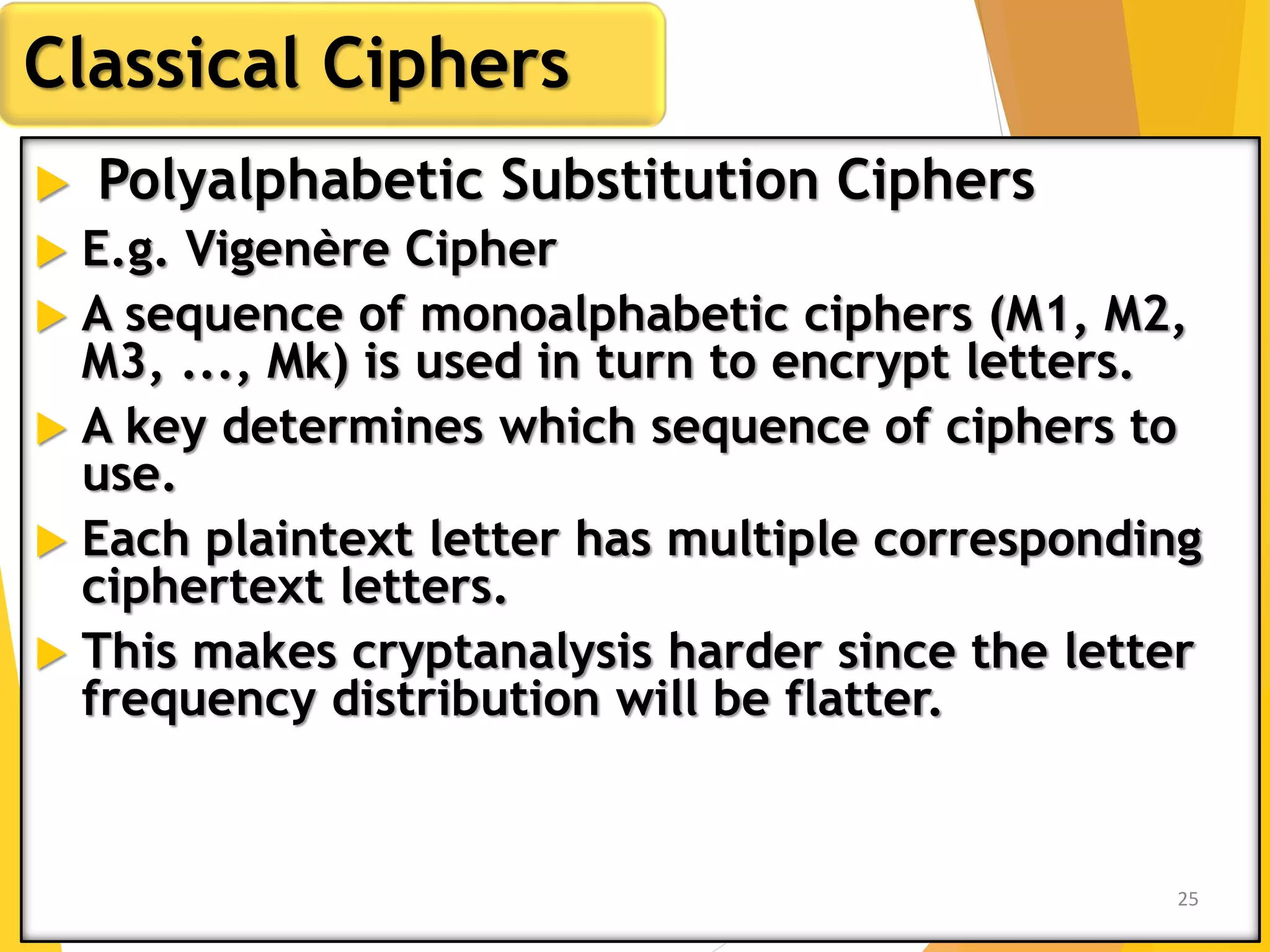
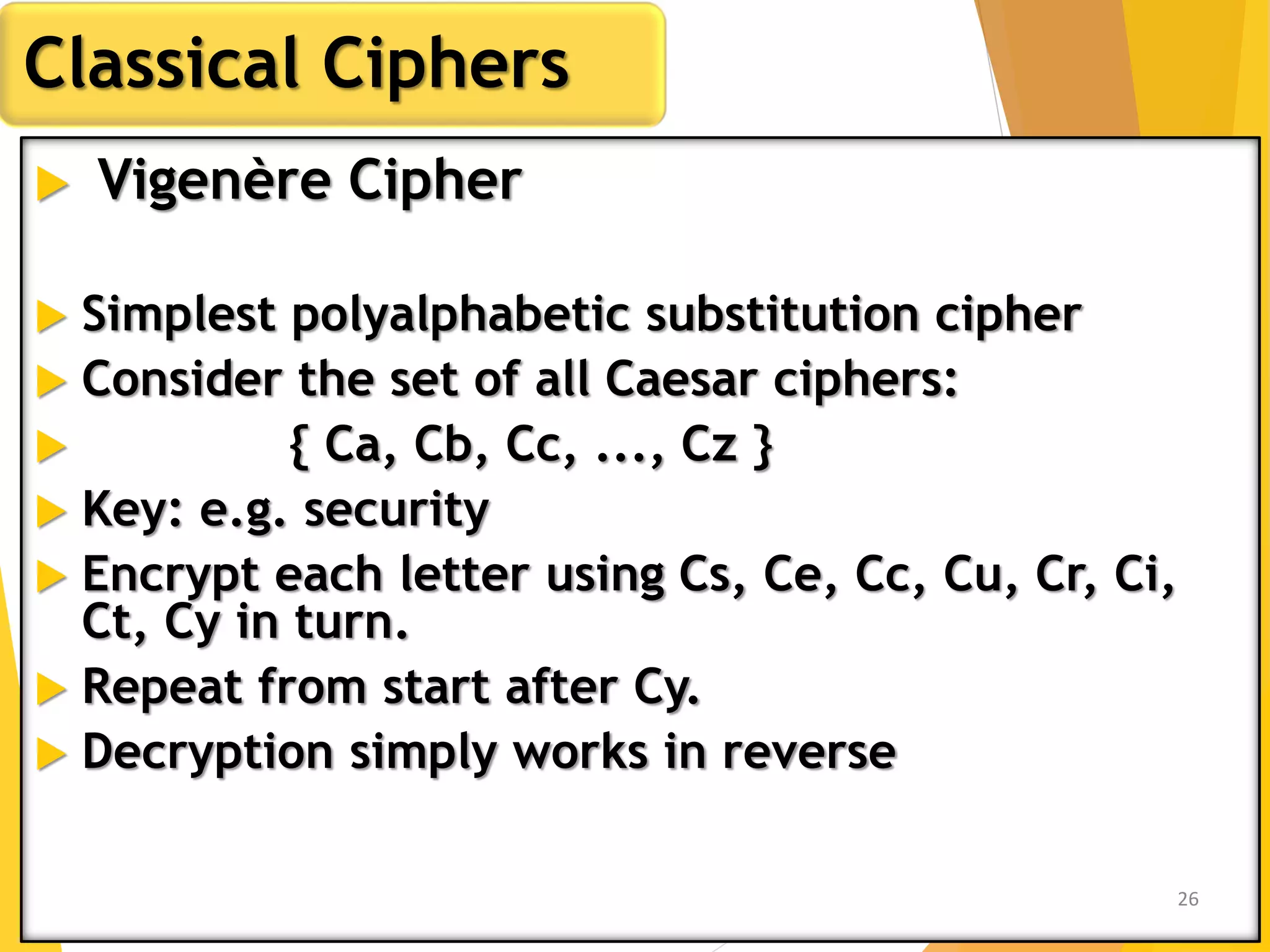
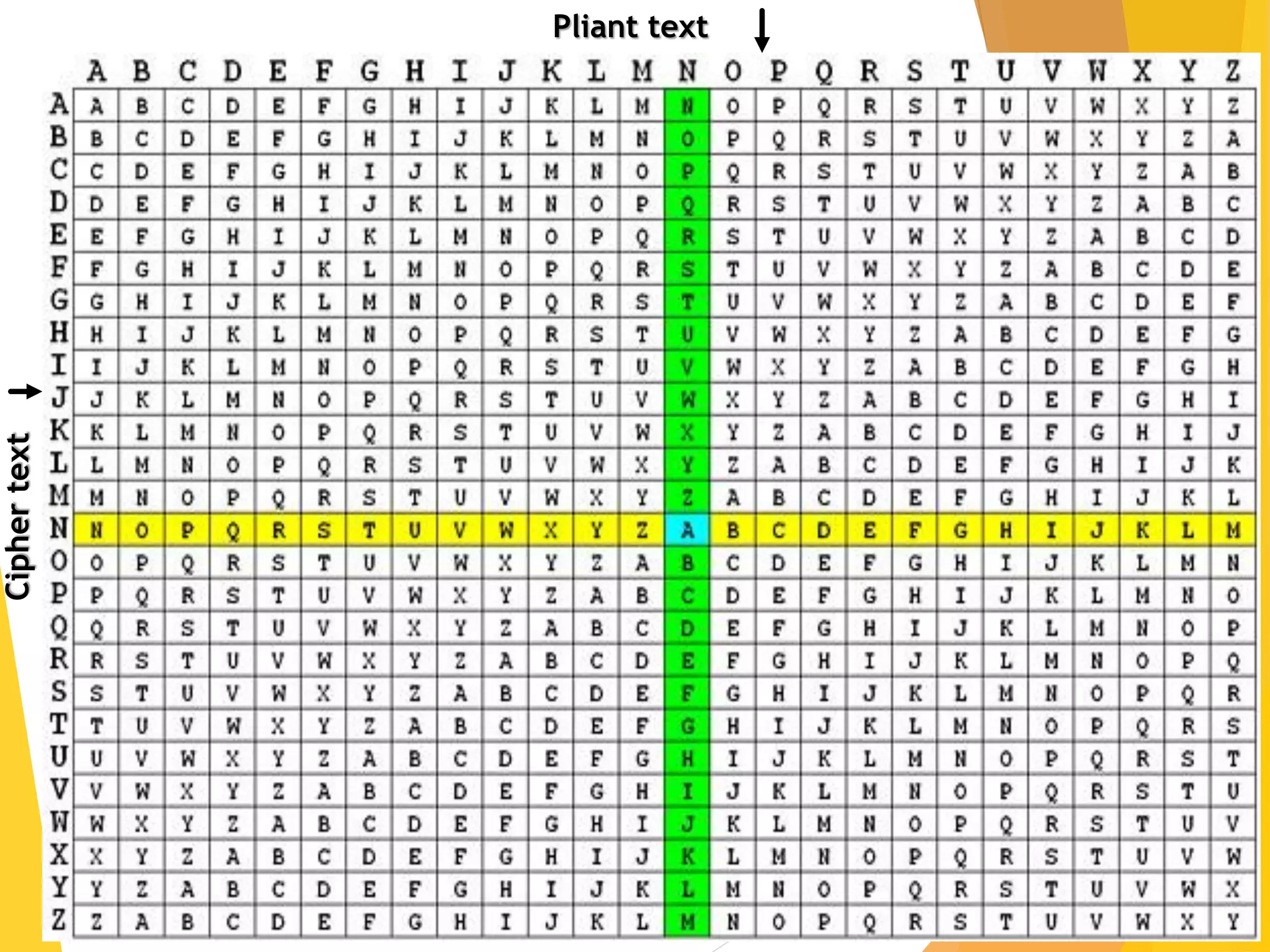
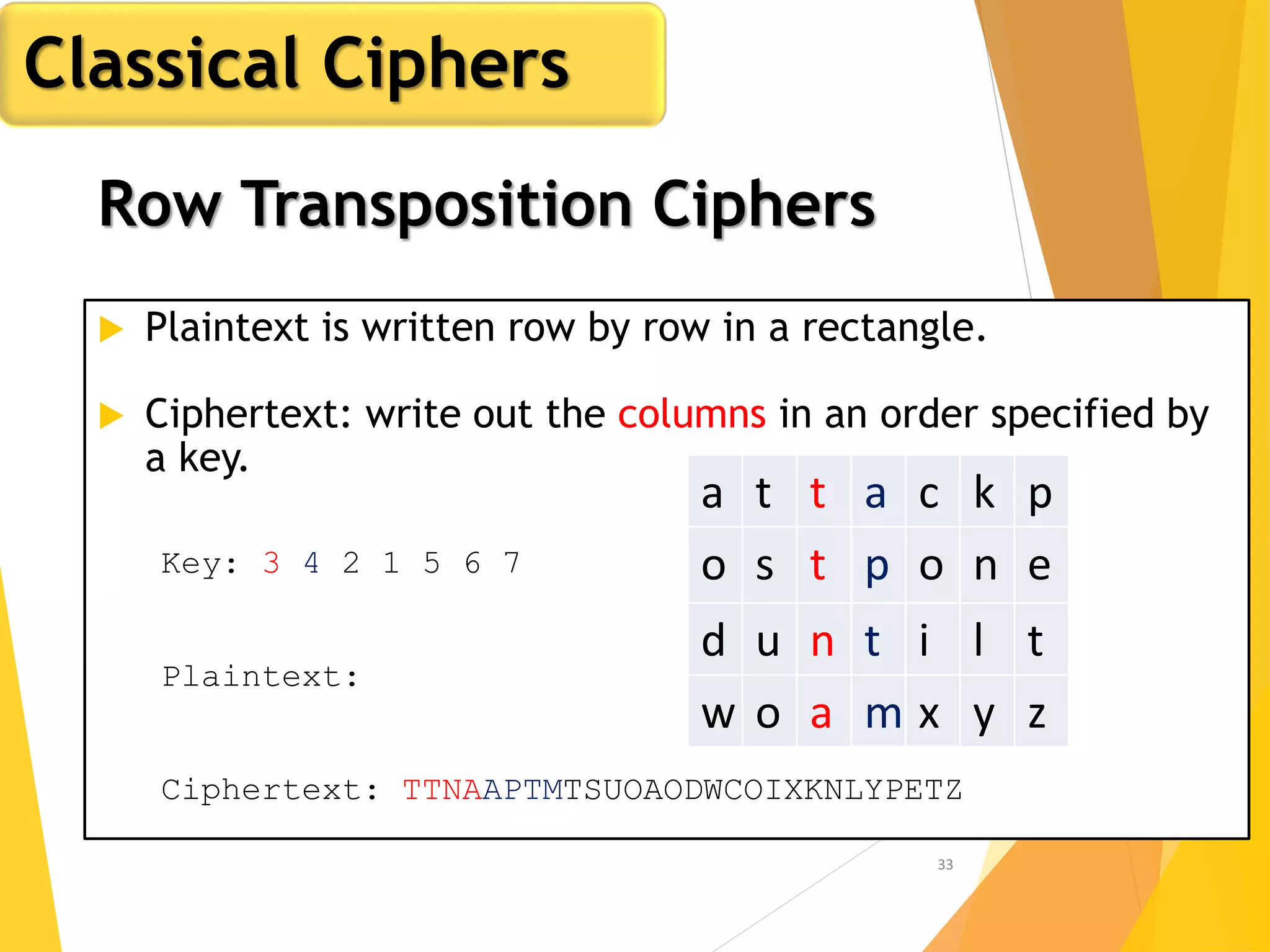
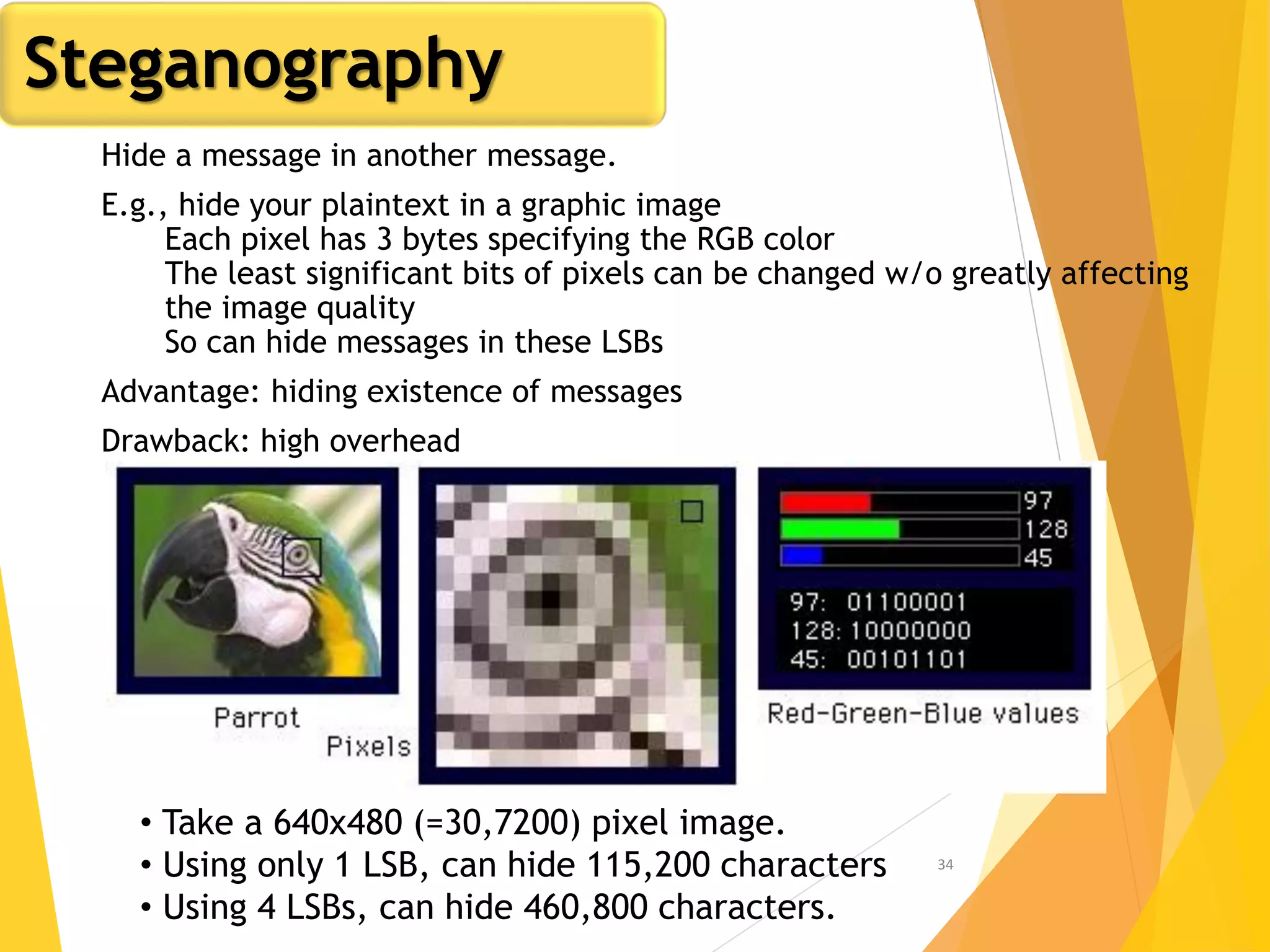
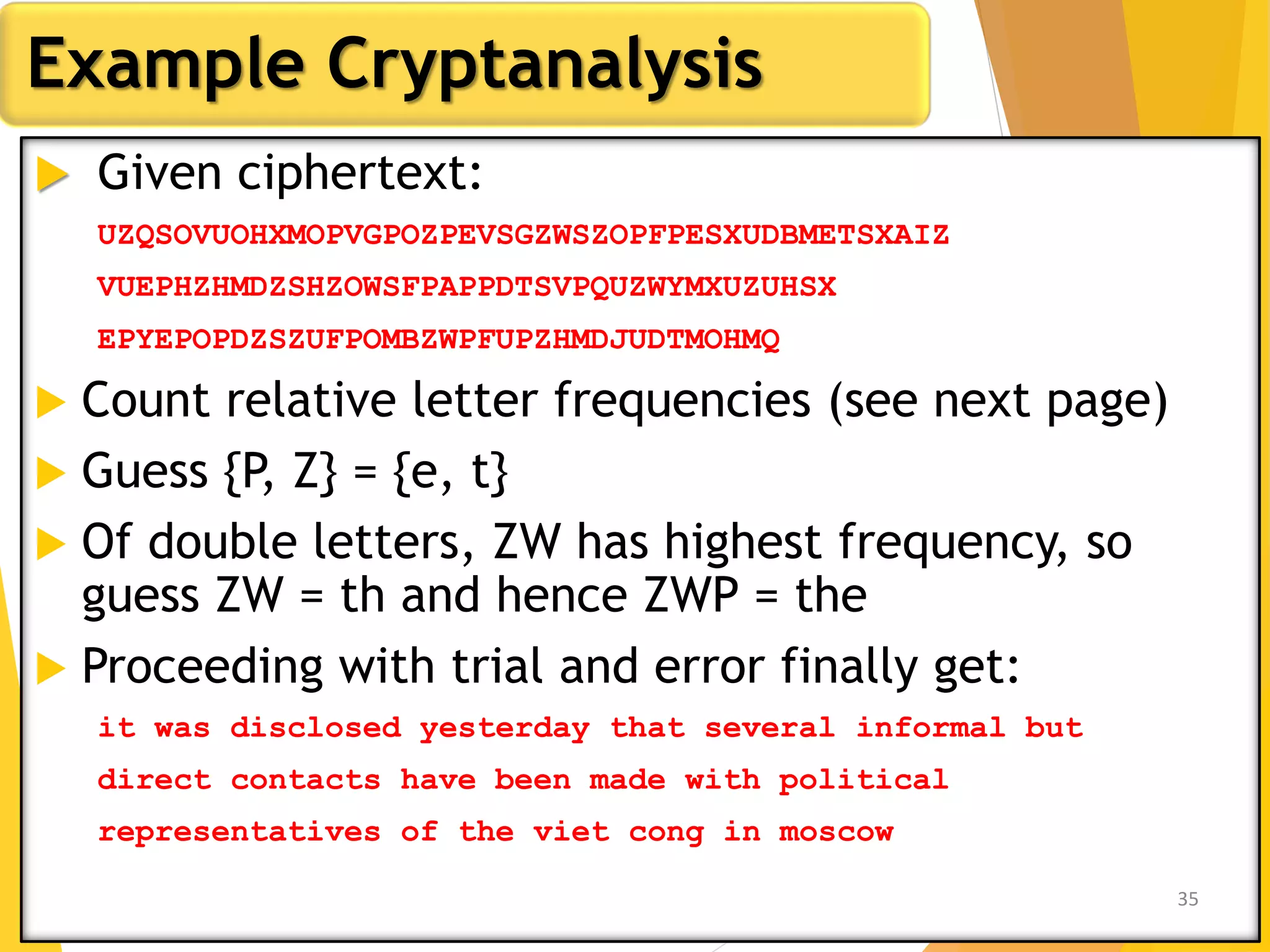
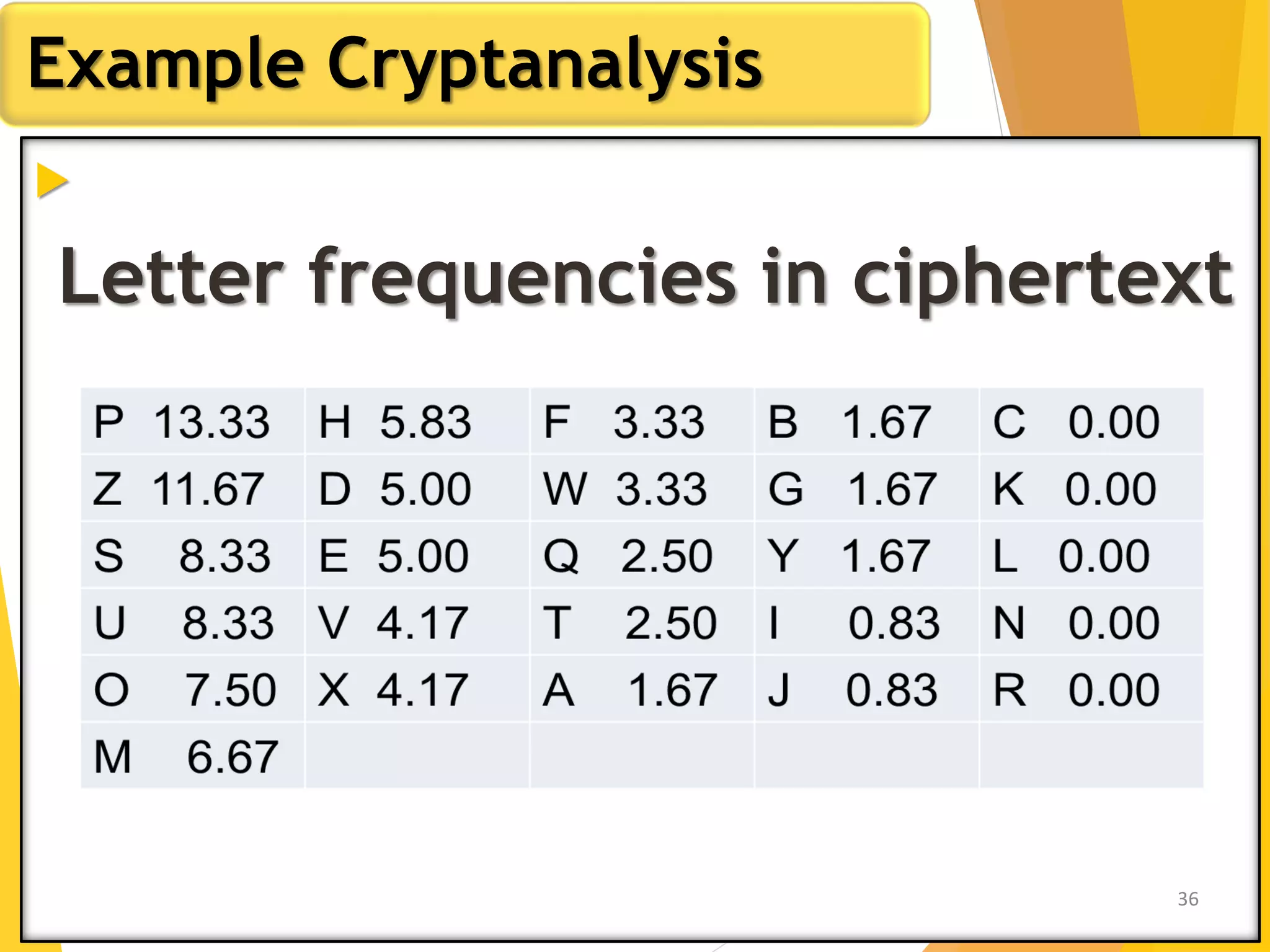
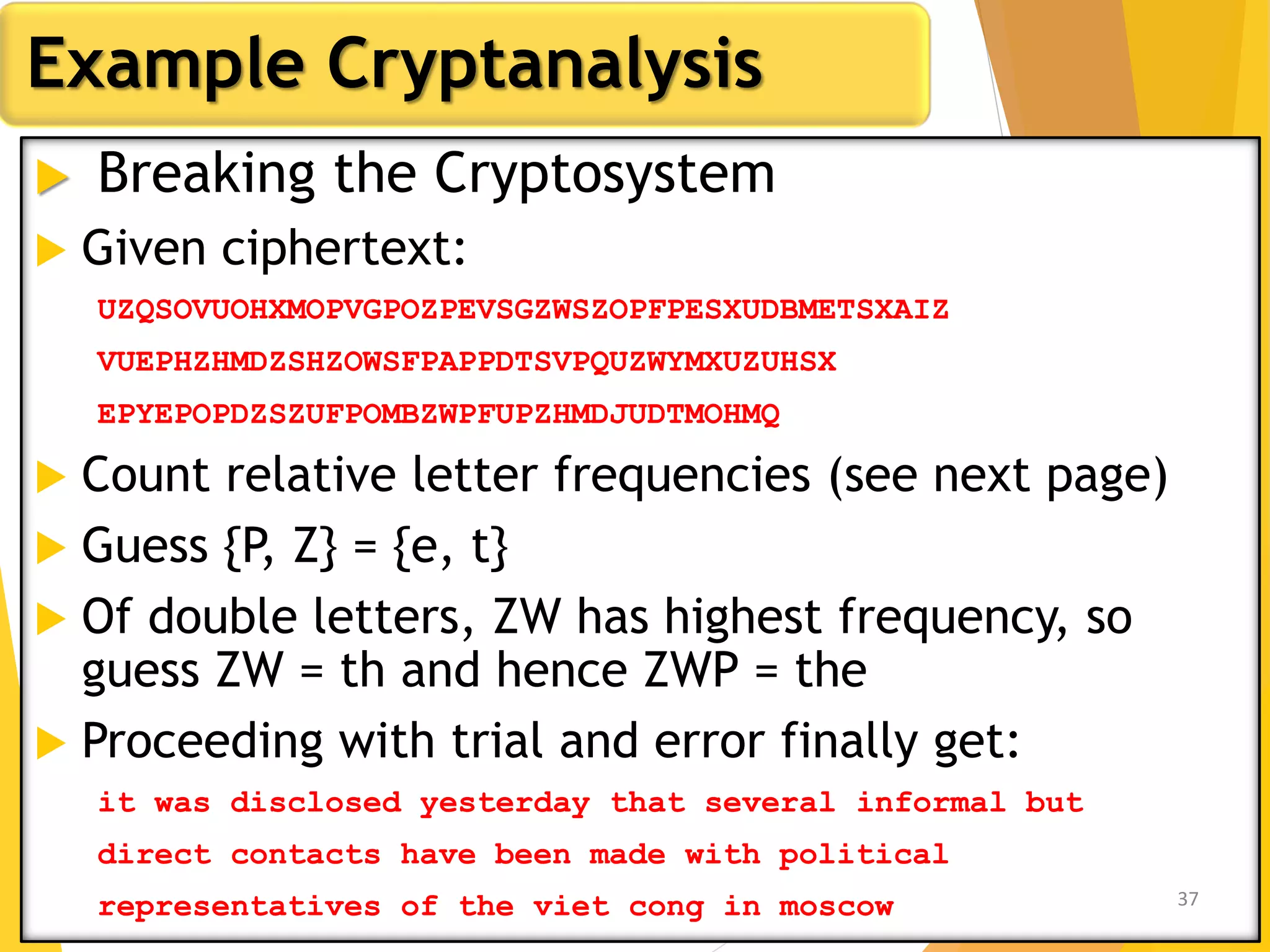
This document outlines the principles of network security, focusing on cryptography, classical encryption techniques, and various ciphers such as the Caesar cipher, Playfair cipher, and Vigenère cipher. It discusses symmetric and asymmetric encryption models, cryptanalysis methods, and the significance of key management in securing communications. Additionally, it covers the use of transposition and substitution ciphers, as well as steganography for hiding messages within other messages.