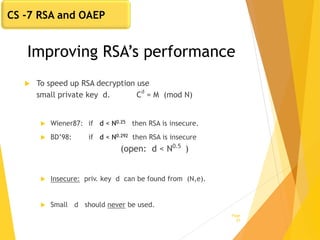
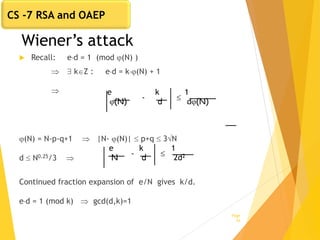
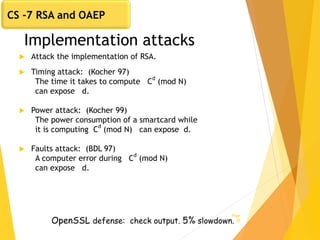
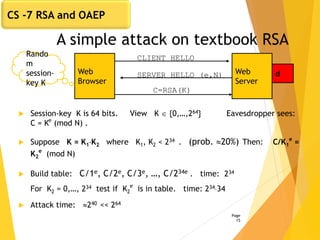
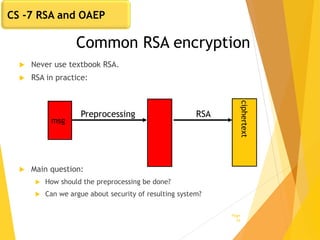
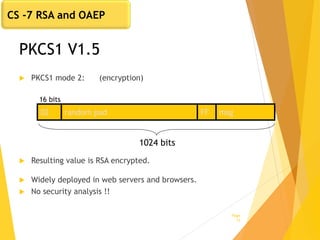
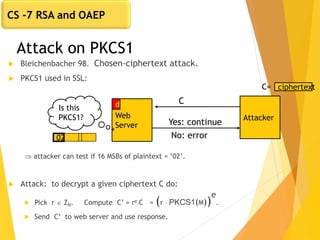
The document covers key concepts in network security, focusing on asymmetric key cryptography including RSA and OAEP, along with factors involved in public key cryptography. It discusses the vulnerabilities of textbook RSA, implementation attacks, and the significance of using secure key lengths and preprocessing functions to enhance security. Key methodologies such as prime factorization, secure message authentication, and the Diffie-Hellman key exchange are also outlined.







![The RSA trapdoor 1-to-1 function
Parameters: N=pq. N 1024 bits. p,q 512 bits.
e – encryption exponent. gcd(e, (N) ) = 1 .
1-to-1 function: RSA(M) = Me
(mod N) where MZN
*
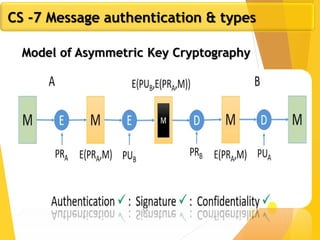
Page
13
Trapdoor: d – decryption exponent.
Where ed = 1 (mod (N) )
Inversion: RSA(M)d
= Med
= Mk(N)+1
= M (mod N)
(n,e,t,)-RSA Assumption: For any t-time alg. A:
Pr[ A(N,e,x) = x
1/e
(N) : ]<
p,q n-bit primes,
Npq, xZN
*
R
R
CS -7 RSA and OAEP](https://image.slidesharecdn.com/ntewroksecuirtycs7-200126162439/85/Ntewrok-secuirty-cs7-13-320.jpg)

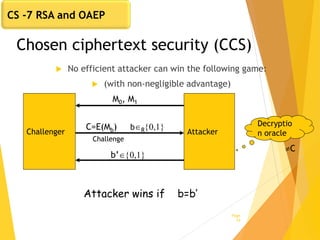
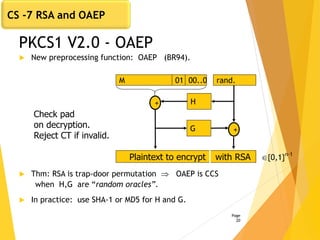
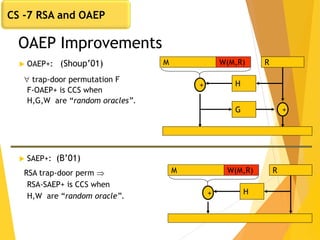
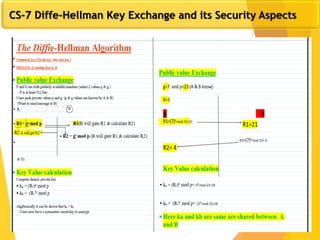
![Subtleties in implementing OAEP [M ’00]
OAEP-decrypt(C) {
error = 0;
if ( RSA-1
(C) > 2n-1
)
{ error =1; goto exit; }
if ( pad(OAEP-1
(RSA-1
(C))) != “01000” )
{ error = 1; goto exit; }
Page
22
}
Problem: timing information leaks type of error.
Attacker can decrypt any ciphertext C.
Lesson: Don’t implement RSA-OAEP yourself …
CS -7 RSA and OAEP](https://image.slidesharecdn.com/ntewroksecuirtycs7-200126162439/85/Ntewrok-secuirty-cs7-22-320.jpg)