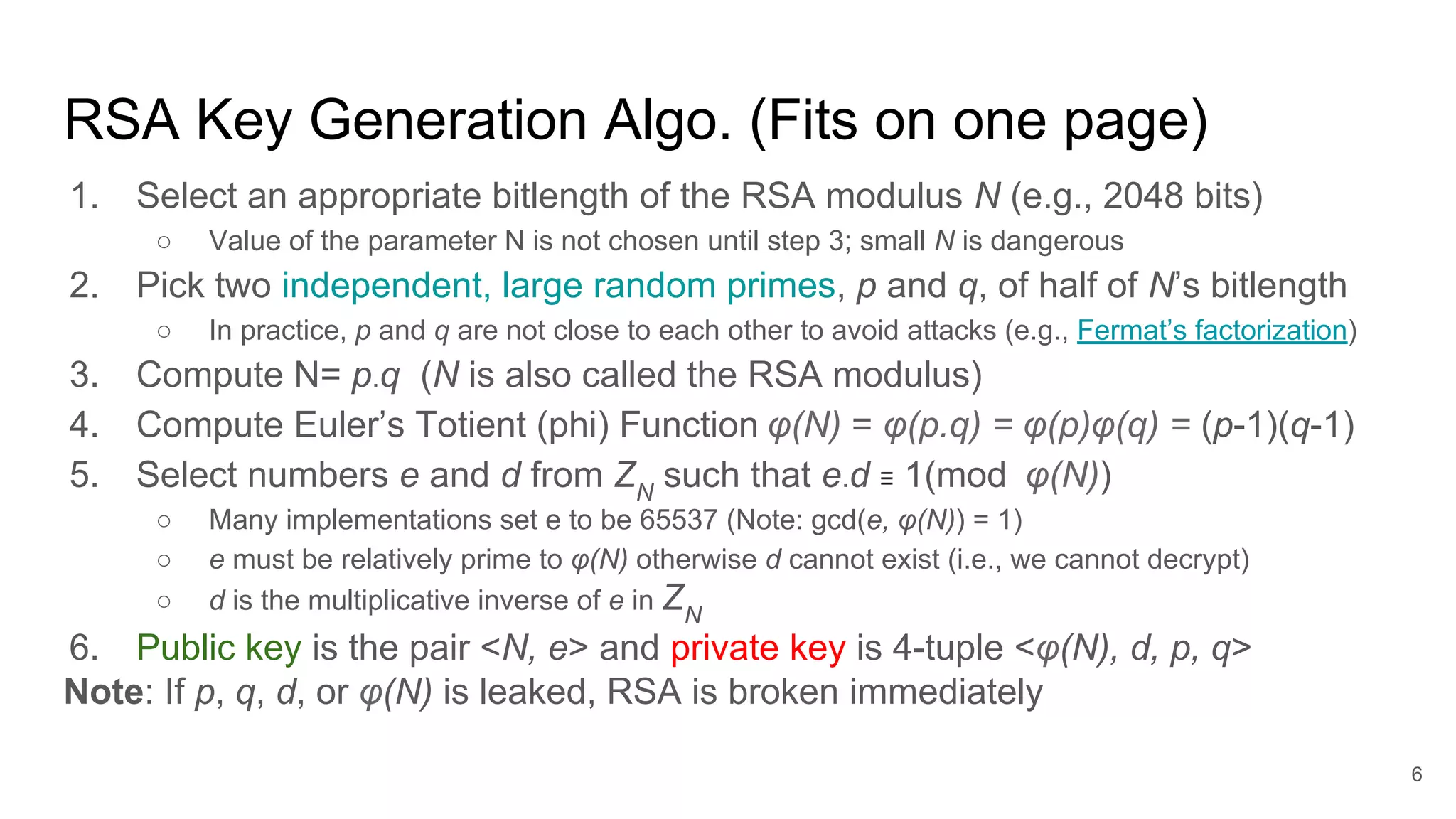
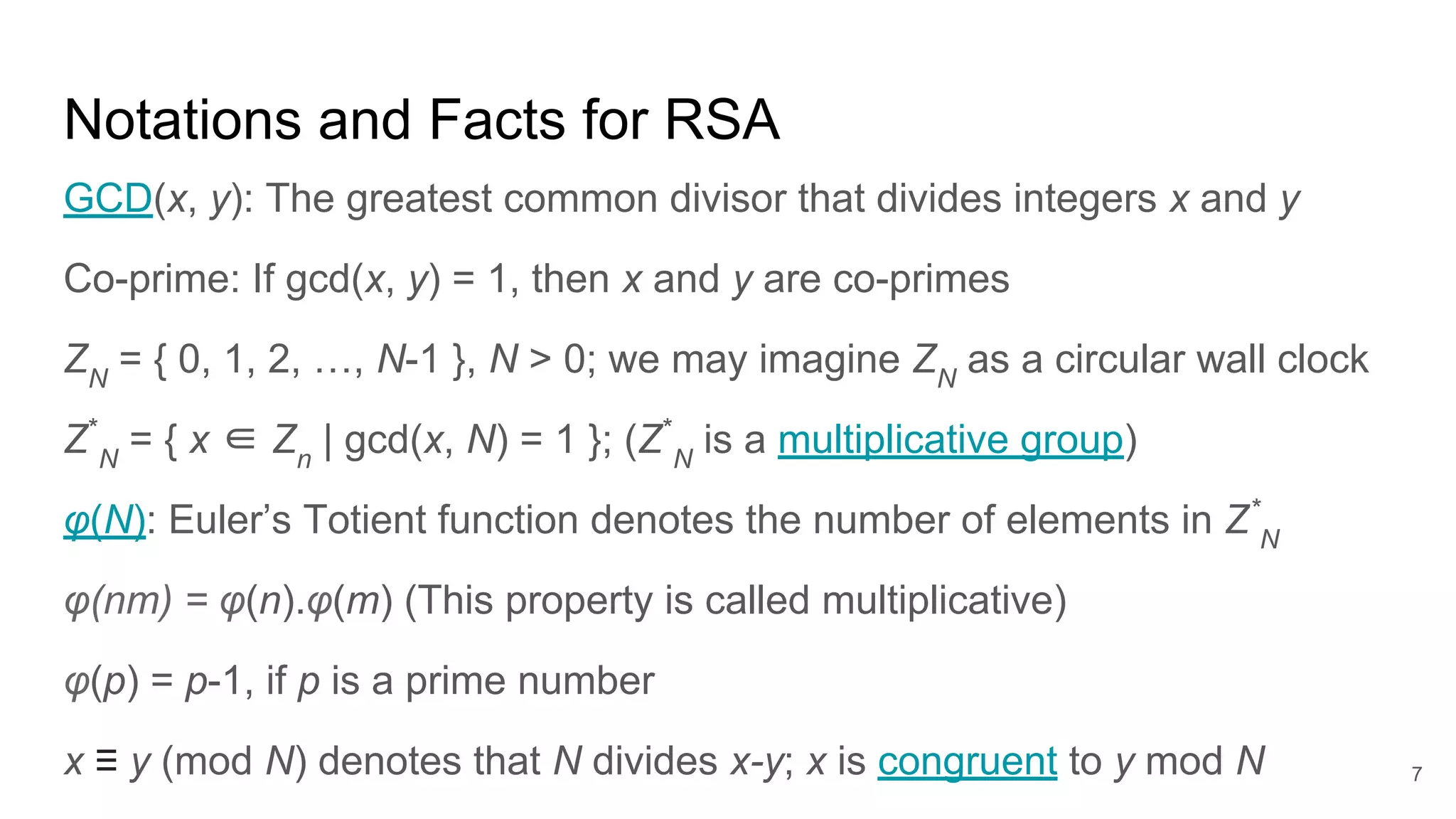
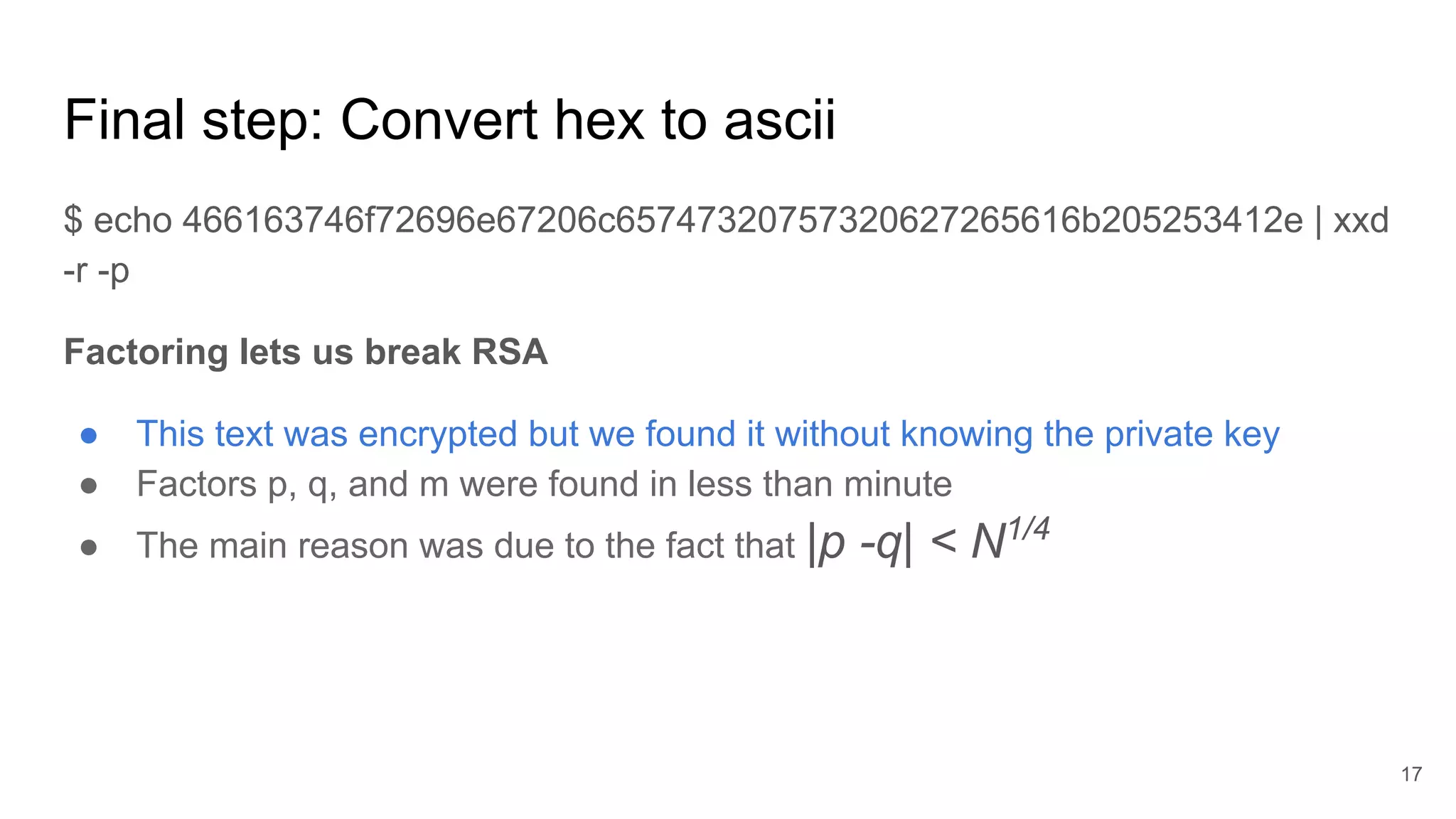
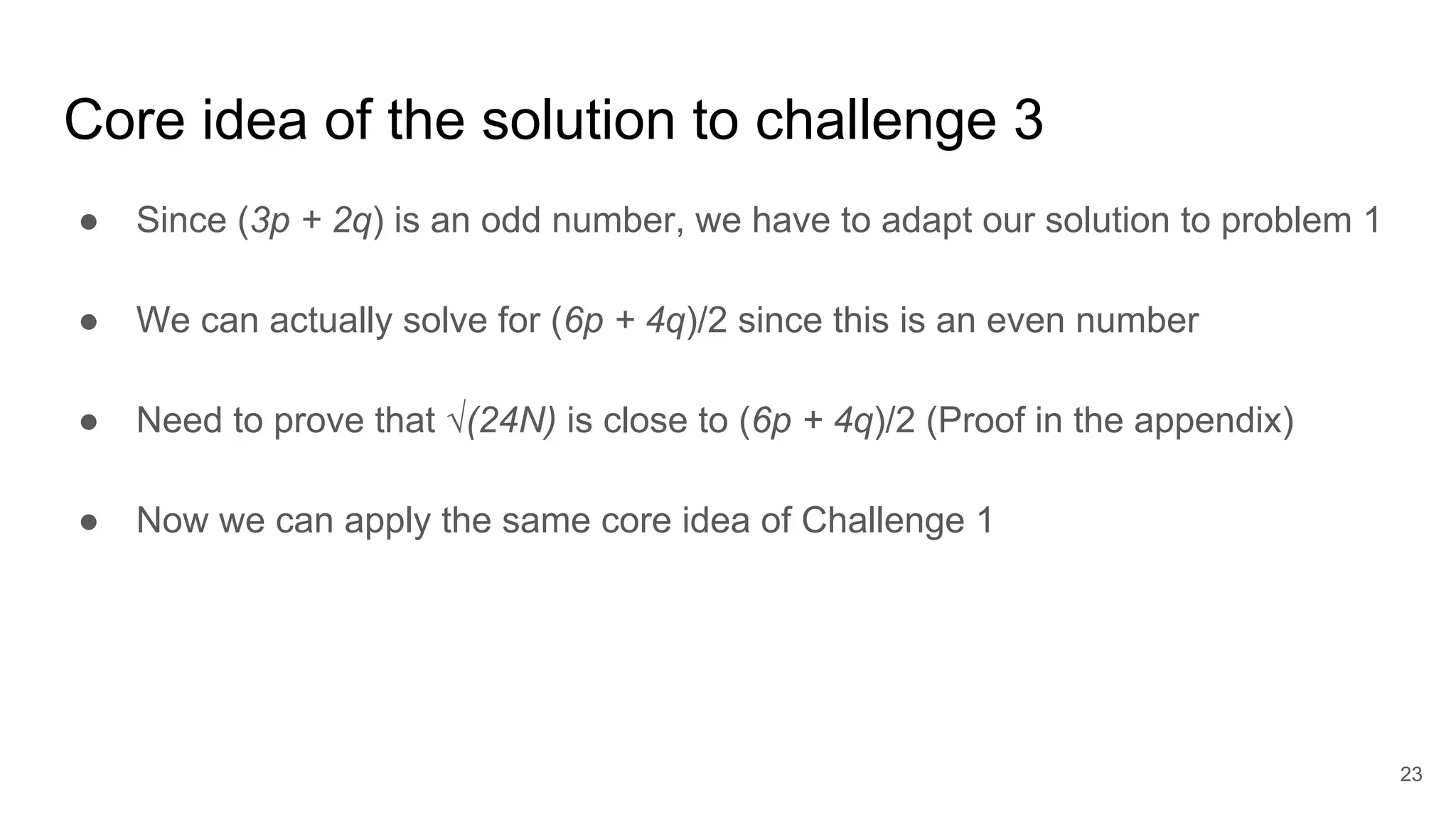
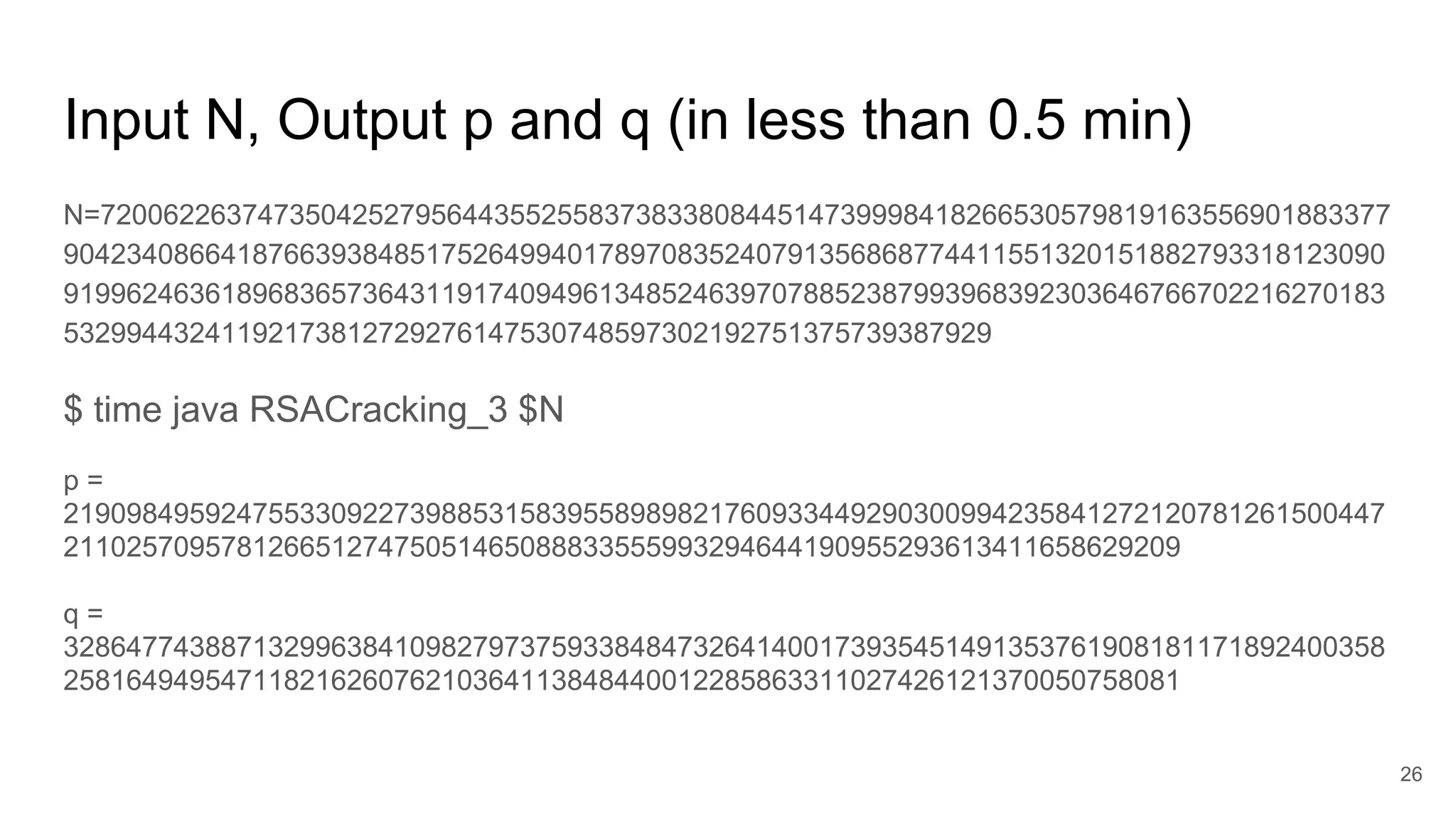
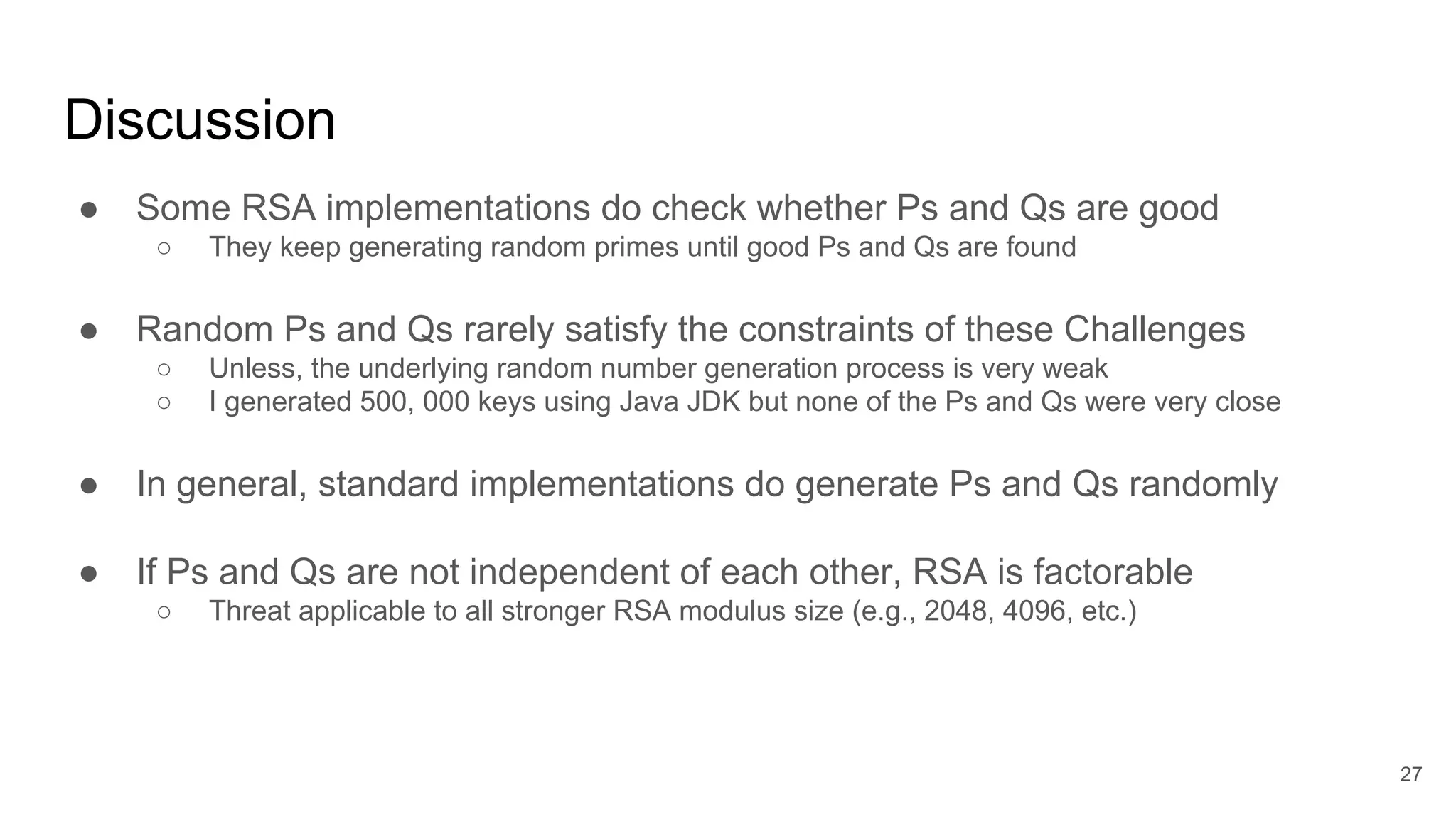
The document discusses solutions to online RSA factoring challenges when prime factors p and q are either not independent or close to one another. It outlines the RSA key generation algorithm, integer factorization challenges, and provides technical approaches and algorithms to derive private keys from public keys in these scenarios. The presentation emphasizes the mathematical principles underpinning RSA encryption and the vulnerabilities that arise when the conditions for prime number selection are not met.






![Challenge 1: Given an N, print p and q
public static void main(String []args){
BigInteger N= new BigInteger(args[0]); // Need to check args length
BigInteger A = bigIntSqRootCeil(N);
BigInteger x = bigIntSqRootCeil(A.multiply(A).subtract(N));
BigInteger p = A.subtract(x);
BigInteger q = A.add(x);
System.out.println("p = " + p);
System.out.println("q = " + q);
}
11
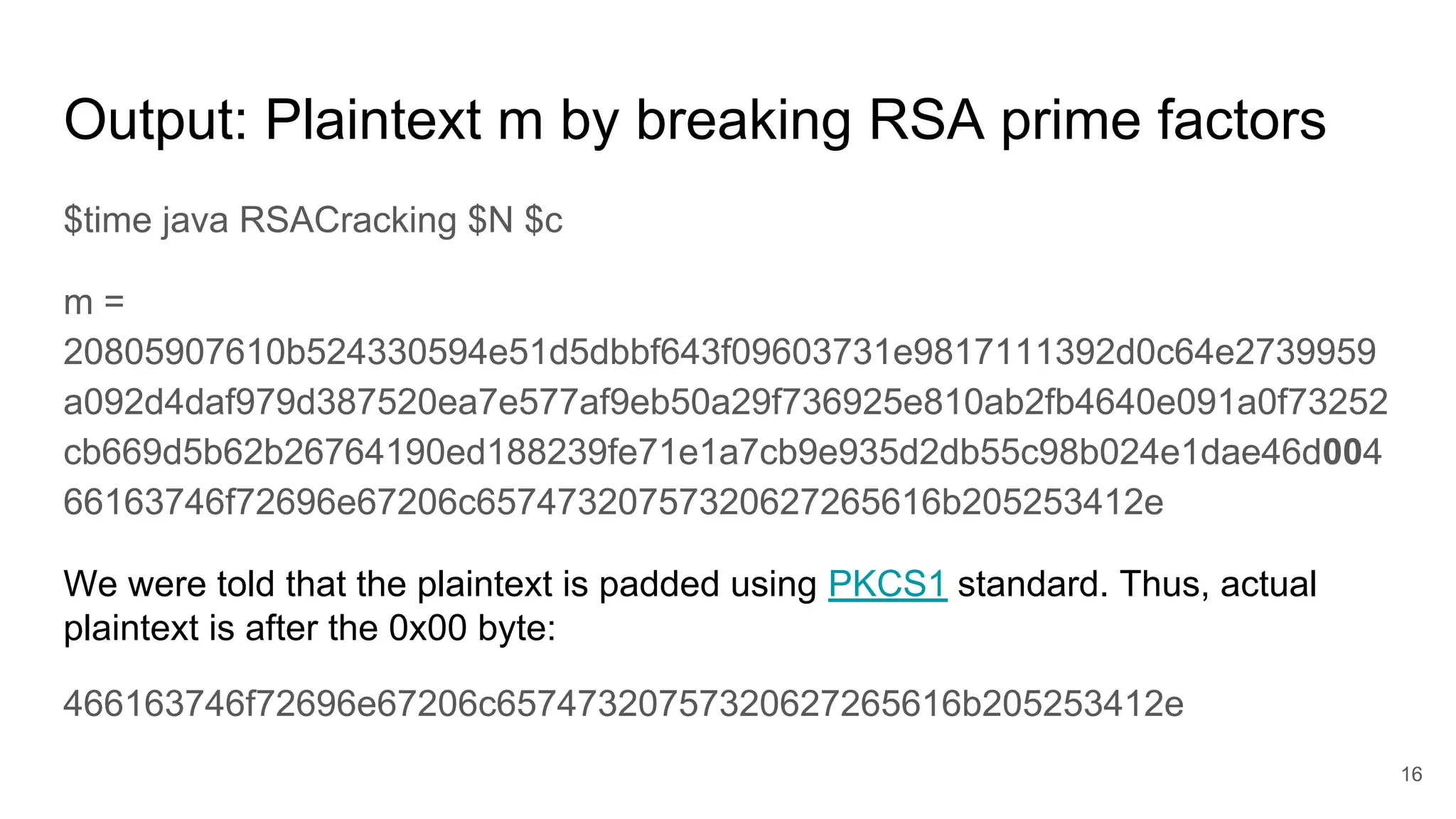
This program derives secret prime factors p and q from the given
public value N](https://image.slidesharecdn.com/solutionstoonlinersafactoringchallenges-180405234911/75/Solutions-to-online-rsa-factoring-challenges-11-2048.jpg)

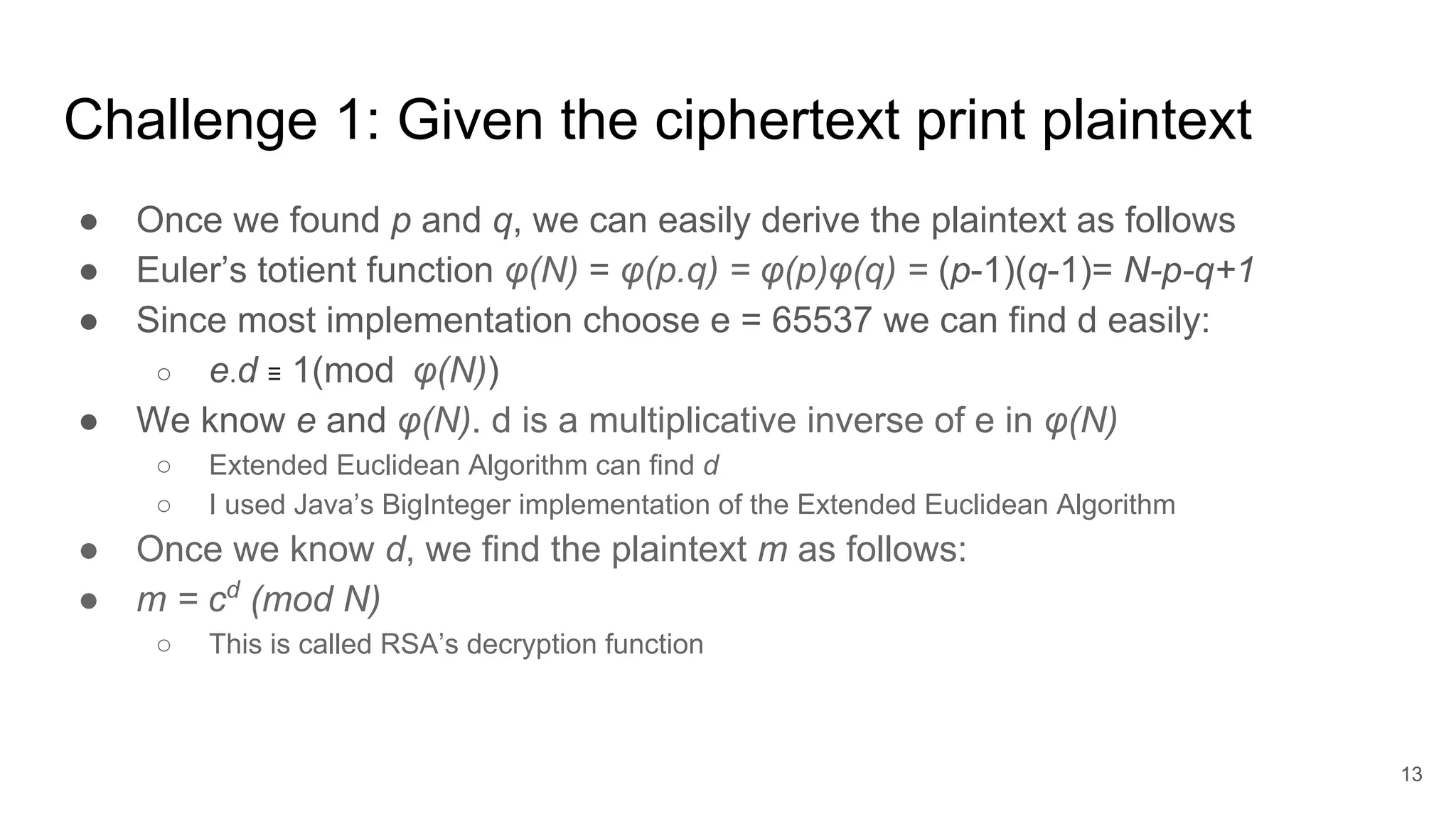
![Challenge 1: algorithm/pseudo code
BigInteger phiN = N.subtract(p).subtract(q).add(BigInteger.valueOf(1));
BigInteger e = BigInteger.valueOf(65537);
BigInteger d = e.modInverse(phiN);
BigInteger c = new BigInteger(args[1]); // Input ciphertext
BigInteger m = c.modPow(d, N); // m = cd
mod N
System.out.println("m = " + m.toString(16)); // Output plaintext
14](https://image.slidesharecdn.com/solutionstoonlinersafactoringchallenges-180405234911/75/Solutions-to-online-rsa-factoring-challenges-14-2048.jpg)









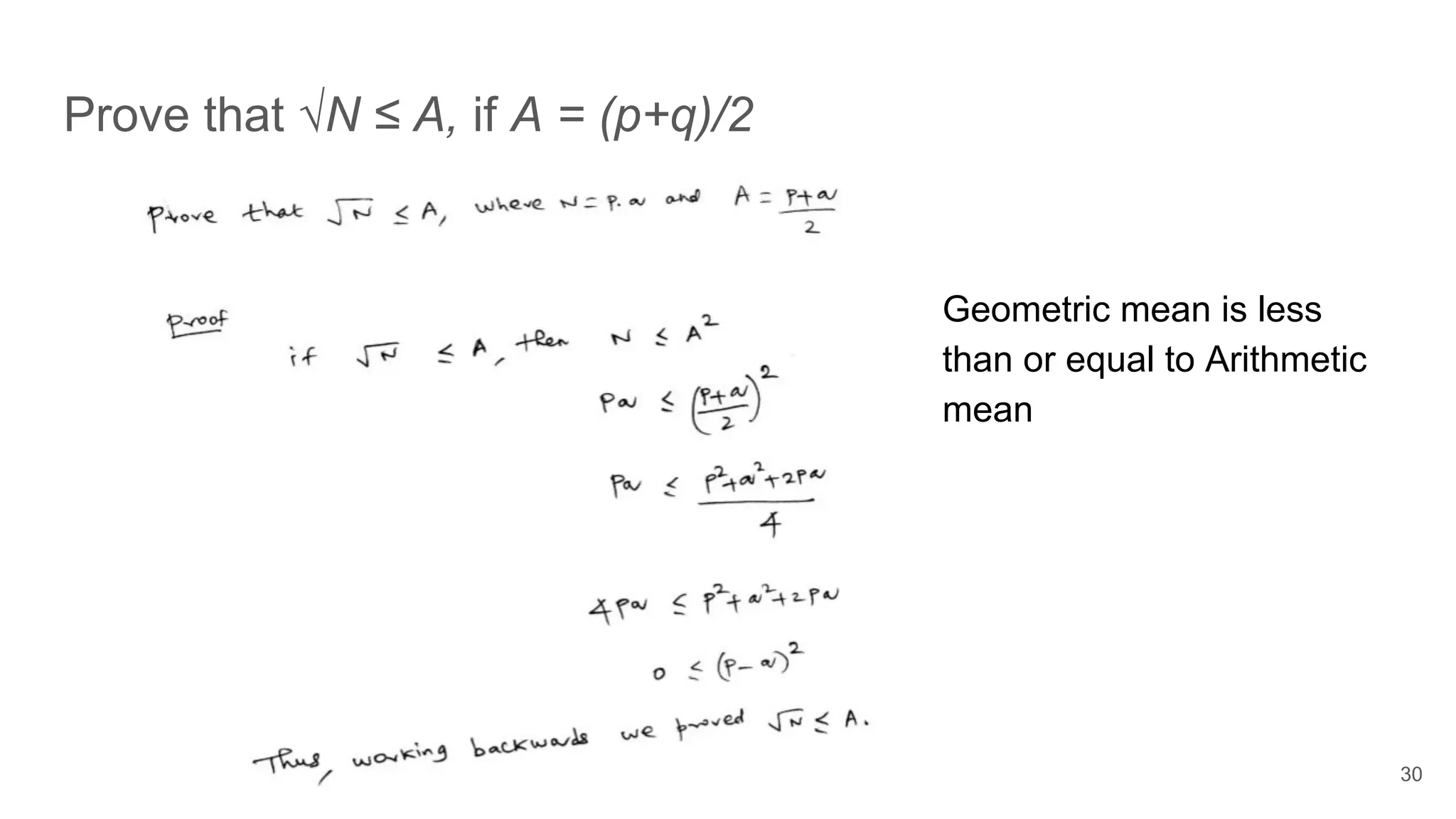
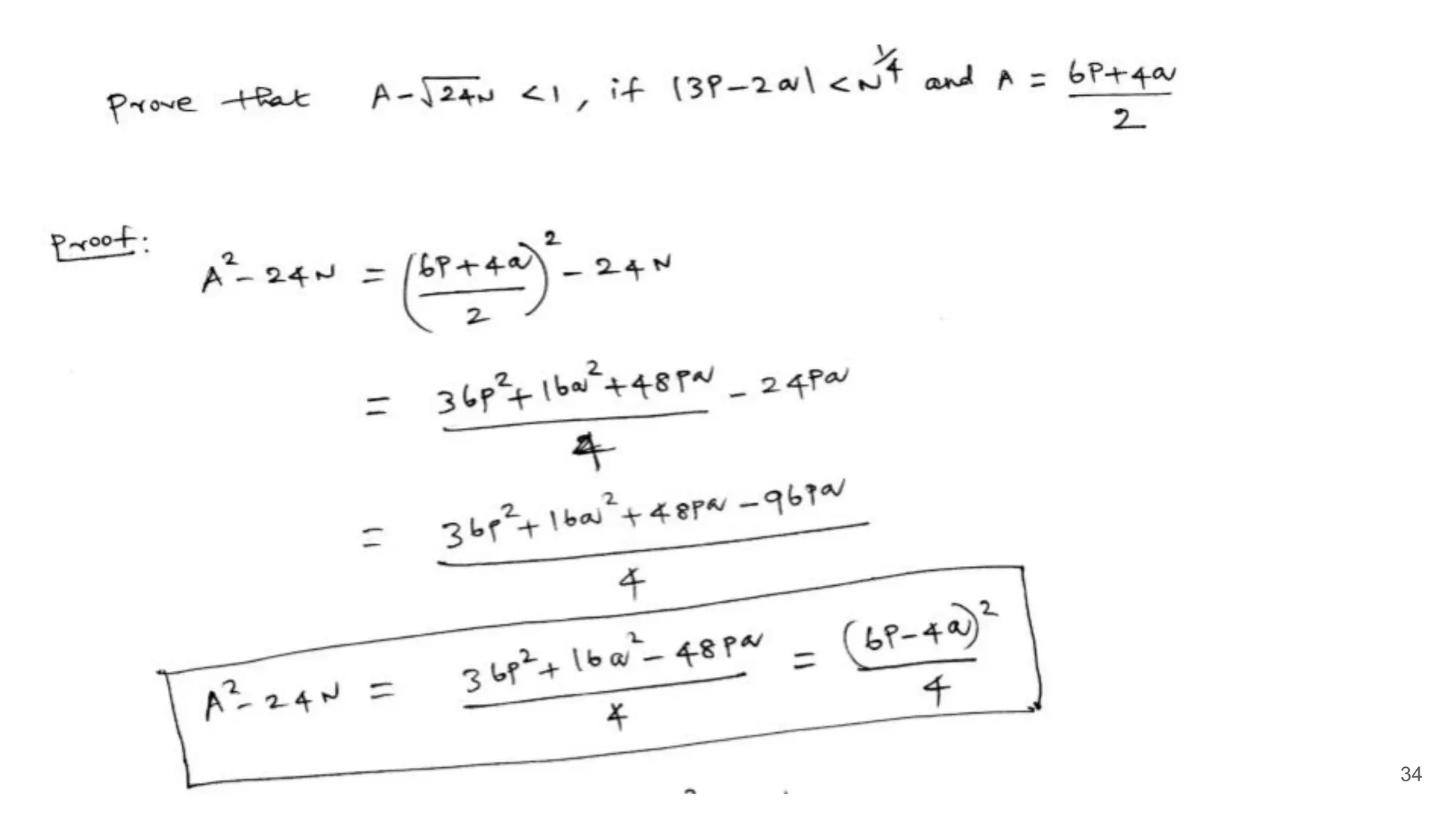
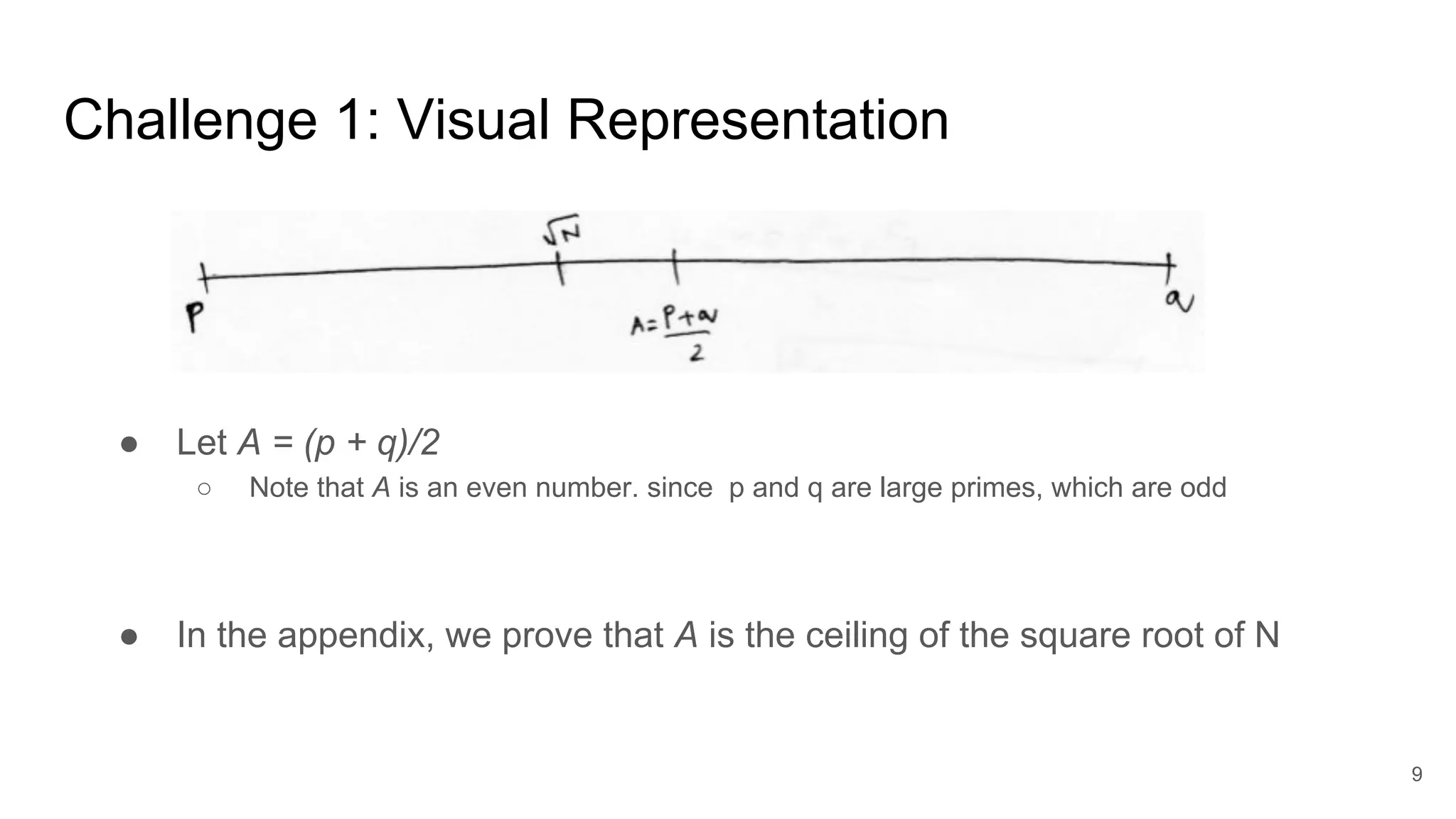
![Challenge 1: Prove that ceiling(√N) = A, if A = (p+q)/2
31
A2
-N= (p+q)2
/4 -N= (p-q)2
/4 [Since N= pq]
A - √N = (A - √N)(A + √N)/(A + √N)
= (A2
- N)/(A + √N) = (p-q)2
/4(A + √N)
We know that √N ≤ A [see previous slide for a proof]
A - √N ≤ (p-q)2
/8√N
≤ √N/(8√N) ≤ ⅛ ≤ 1 [Since |p -q | < N1/4
]
Since A is an integer, (A - √N) ≤ 1 implies that A must be the ceiling(√N)
This proof was given by Prof. as part of
the Challenge 1](https://image.slidesharecdn.com/solutionstoonlinersafactoringchallenges-180405234911/75/Solutions-to-online-rsa-factoring-challenges-31-2048.jpg)
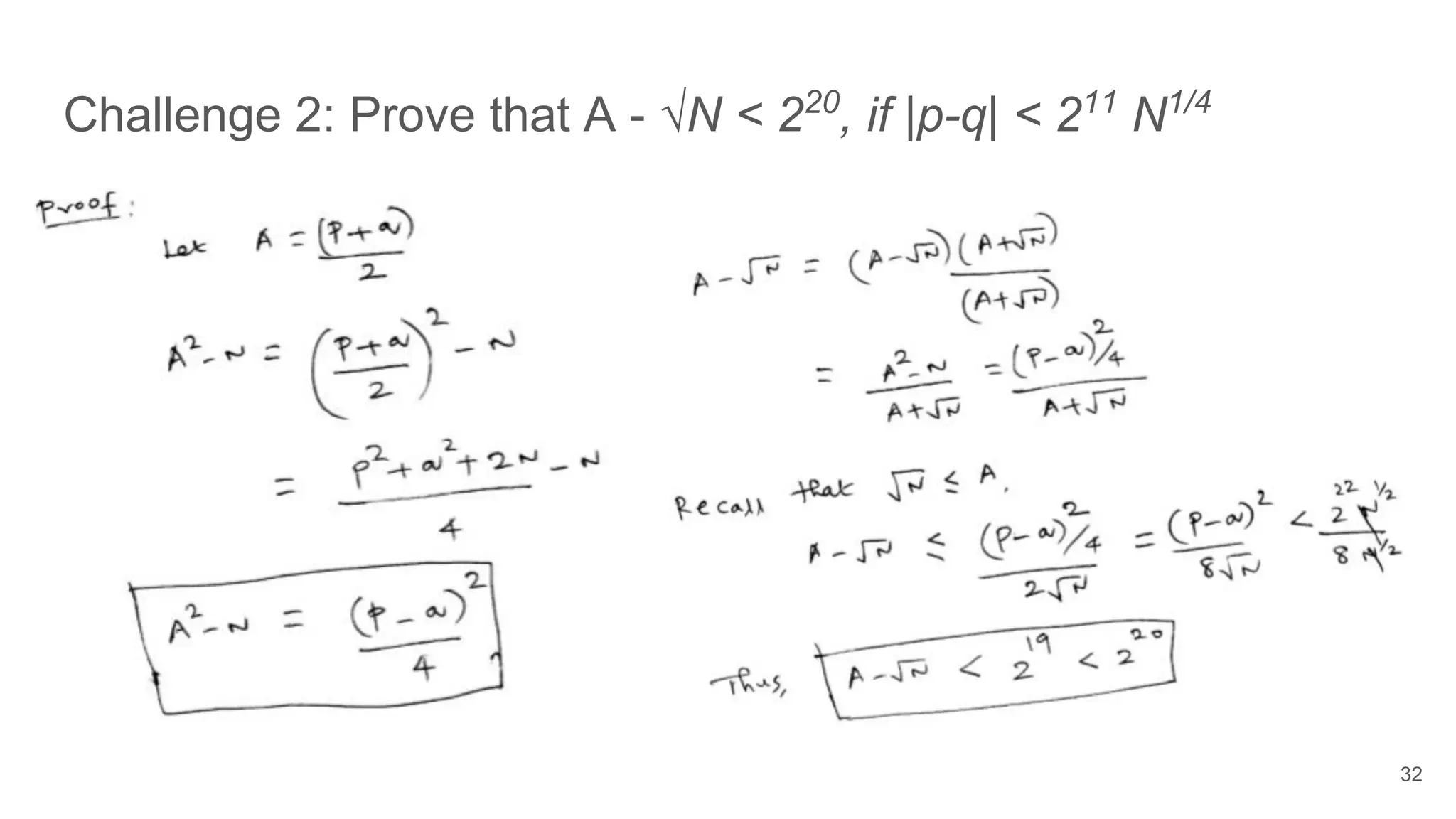
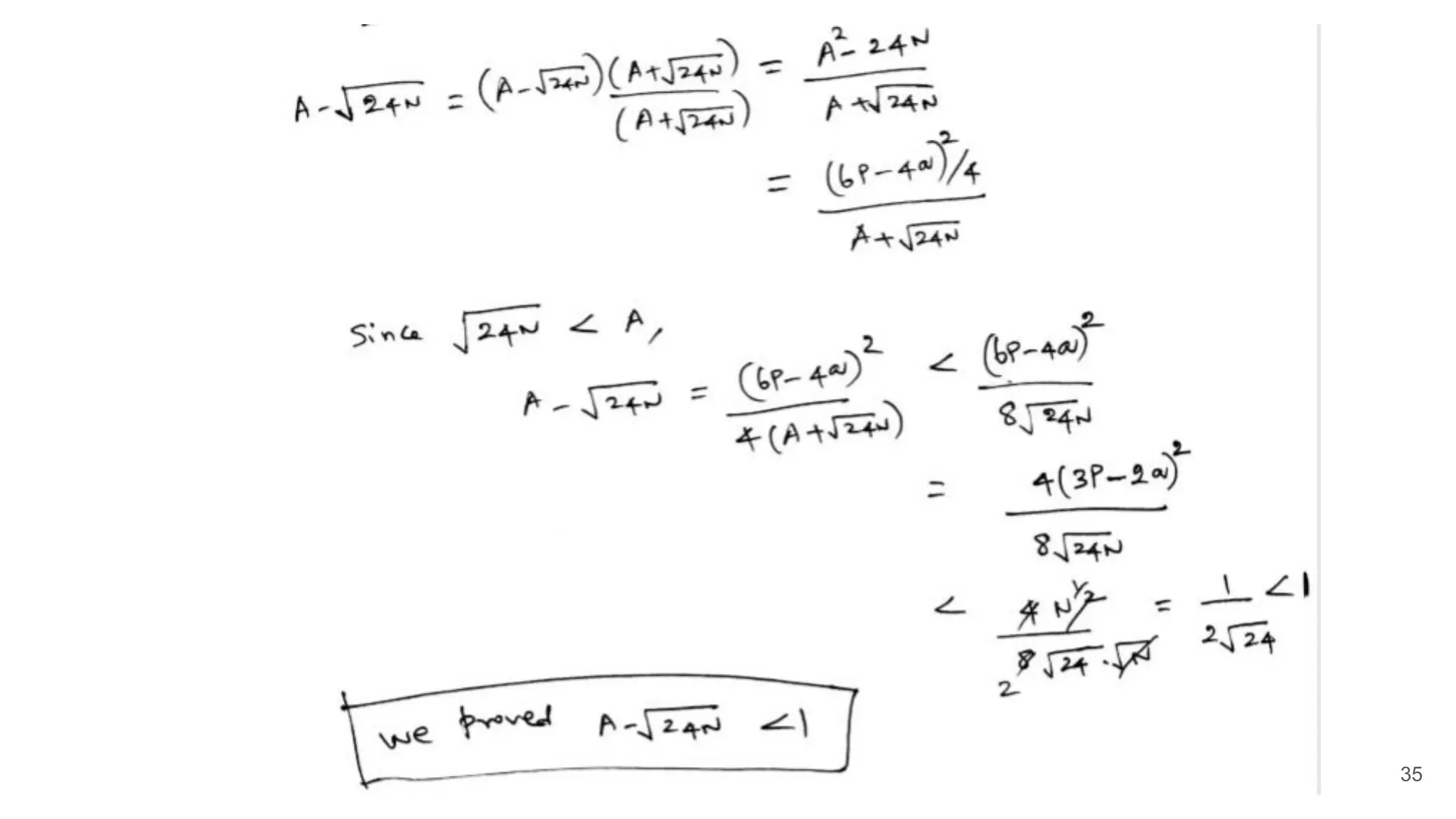
![Challenge 3: Prove that ceiling(√24N) = A, if A = (6p+4q)/2
33
A2
-N= (6p+4q)2
/4 -N= (p-q)2
/4 [Since N= pq]
A - √N = (A - √N)(A + √N)/(A + √N)
= (A2
- N)/(A + √N) = (p-q)2
/4(A + √N)
We know that √N ≤ A [geometric mean is less than or equal to arithmetic mean]
A - √N ≤ (p-q)2
/8√N
≤ √N/(8√N) ≤ ⅛ ≤ 1 [Since |p -q | < N1/4
]
Since A is an integer, (A - √N) ≤ 1 implies that A must be the ceiling(√N)](https://image.slidesharecdn.com/solutionstoonlinersafactoringchallenges-180405234911/75/Solutions-to-online-rsa-factoring-challenges-33-2048.jpg)