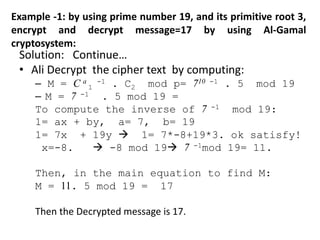
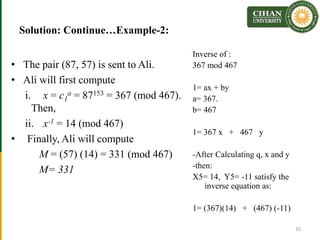
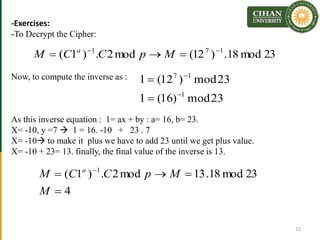
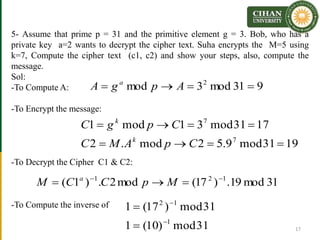
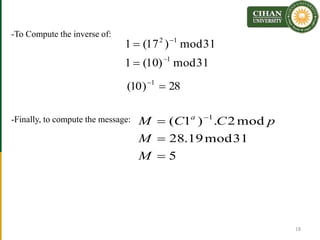
The document describes the Al-Gamal encryption algorithm. It begins with an overview of asymmetric cryptography and then provides details of the Al-Gamal algorithm including key generation, encryption, and decryption steps. It also includes two examples showing the encryption and decryption of messages using Al-Gamal. At the end, exercises are provided to help students understand and apply the Al-Gamal algorithm.