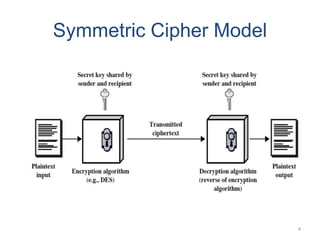
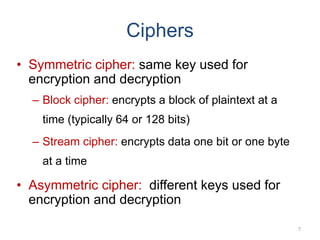
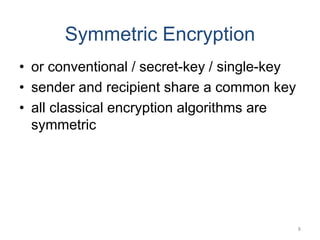
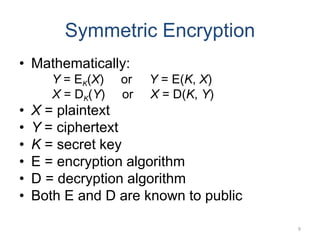
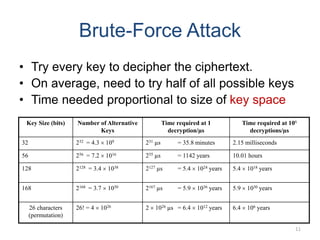
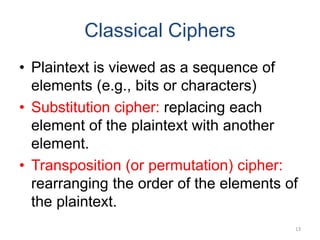
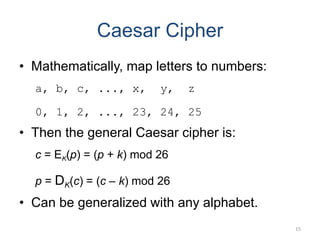
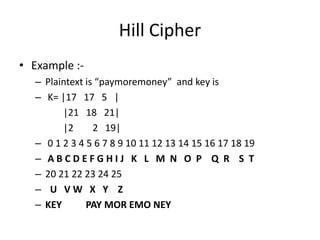
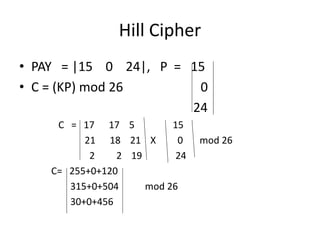
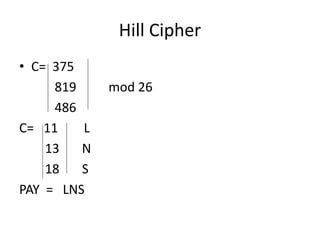
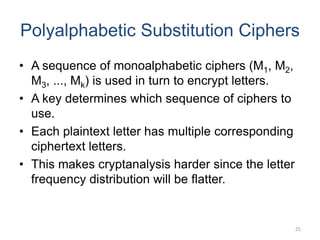
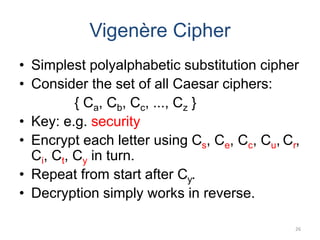
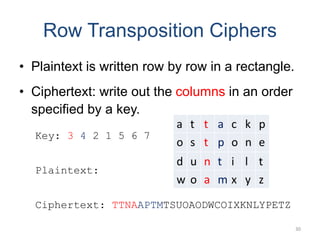
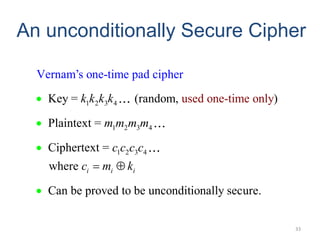
Classical encryption techniques include symmetric ciphers that use the same key for encryption and decryption, such as substitution ciphers that replace plaintext letters and transposition ciphers that rearrange the order of letters. More complex techniques include the Playfair cipher which encrypts digrams and the Vigenère cipher that applies a series of Caesar ciphers controlled by a keyword. Product ciphers combine substitution and transposition layers to strengthen security.