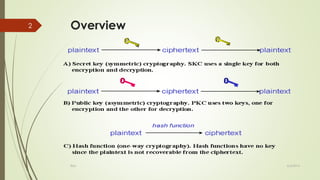
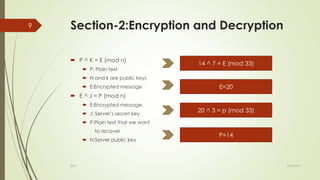
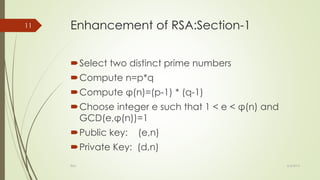
RSA is a public-key cryptosystem that uses both public and private keys for encryption and decryption. It was the first practical implementation of such a cryptosystem. The algorithm involves four main steps: 1) generation of the public and private keys, 2) encryption of messages using the public key, 3) decryption of encrypted messages using the private key, and 4) potential cracking of the encrypted message. It works by using two large prime numbers to generate the keys and performs exponentiation and modulo operations on messages to encrypt and decrypt them. There were some drawbacks to the original RSA algorithm related to redundant calculations and representing letters numerically that opened it up to easier hacking. Enhancements to RSA improved it by choosing