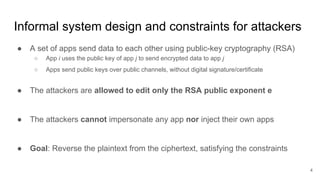
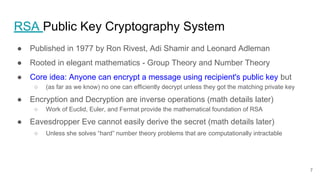
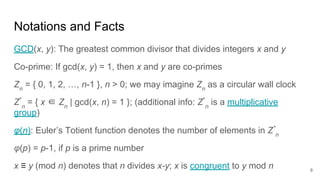
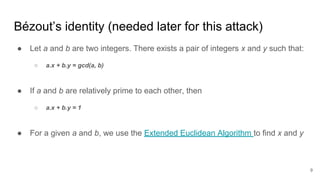
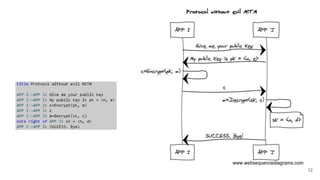
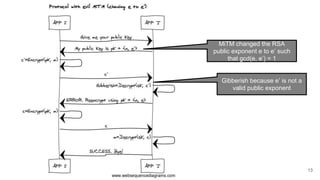
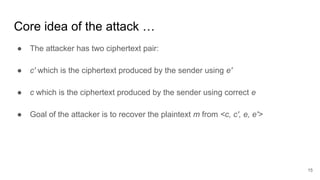
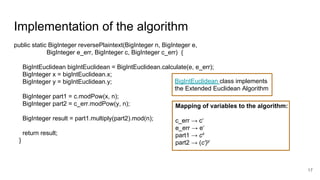
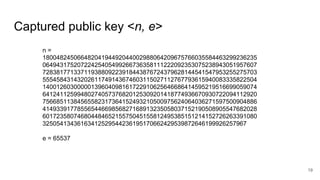
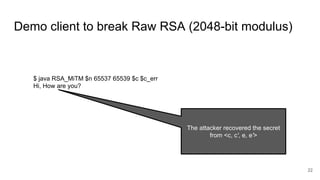
The presentation explains how to break unauthenticated RSA encryption by employing man-in-the-middle attacks to modify public exponents, allowing attackers to recover plaintext from ciphertext. It details the use of the extended Euclidean algorithm in the attack method, emphasizing the risks of using RSA without integrity checks or digital signatures. The findings highlight that such vulnerabilities can persist in systems employing public-key cryptography if proper safeguards are not implemented.