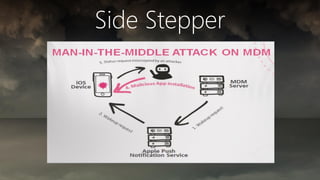
The document discusses the misconceptions surrounding mobile security and emphasizes the vulnerabilities of mobile devices, especially in relation to network attacks and malware. It highlights that mobile device management (MDM) and antivirus solutions may not provide adequate protection against threats, particularly on iOS and Android platforms. Key security measures include policy enforcement and advanced threat detection to mitigate risks effectively.





















![©2015 Check Point Software Technologies Ltd. 28
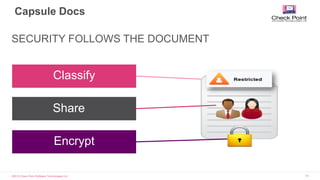
Threat Technologies
Advanced App
Analysis
Sandboxing (Emulation)
Advanced Static Code
Analysis
Uncovers new malware
and targeted exploits
Network Anomaly
Detection
Wi-Fi Man-in-the-Middle
(MitM) attacks
Evasive botnets and
time bomb malware
Host Threat
Analysis
Malicious
Configurations
Exploits and file system
manipulation
Threat Framework
Multi-dimensional
Risk/Trust assessments
Accurate risk
classifications to
effectively mitigate risk
[Protected] Non-confidential content](https://image.slidesharecdn.com/03mtpcapsule-160629104709/85/Mobile-Security-28-320.jpg)


![©2015 Check Point Software Technologies Ltd. 31
Taking Mobile Security Beyond
Mobile Threat Prevention
[Restricted] ONLY for designated groups and individuals
Mobile Threat
Prevention
Threat Prevention for
mobile devices
Capsule
Cloud
Protect laptops
when off the
business network
Capsule
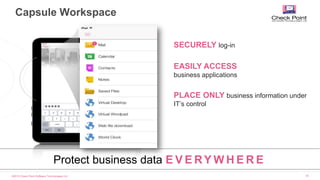
Workspace & Docs
Protect business data
on mobile devices
Target solutions for mobile use-cases](https://image.slidesharecdn.com/03mtpcapsule-160629104709/85/Mobile-Security-31-320.jpg)