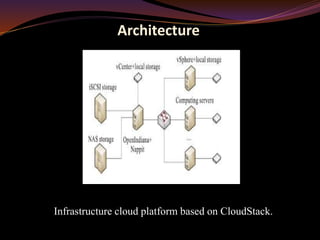
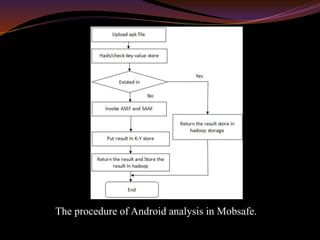
The document proposes a methodology called Mobsafe for evaluating mobile apps using cloud computing and data mining to filter out malware. It outlines a hybrid approach combining static and dynamic analysis for enhanced security, utilizing a cloud infrastructure with tools for automated analysis. Future enhancements may include web mining and machine learning techniques for improved malware detection.