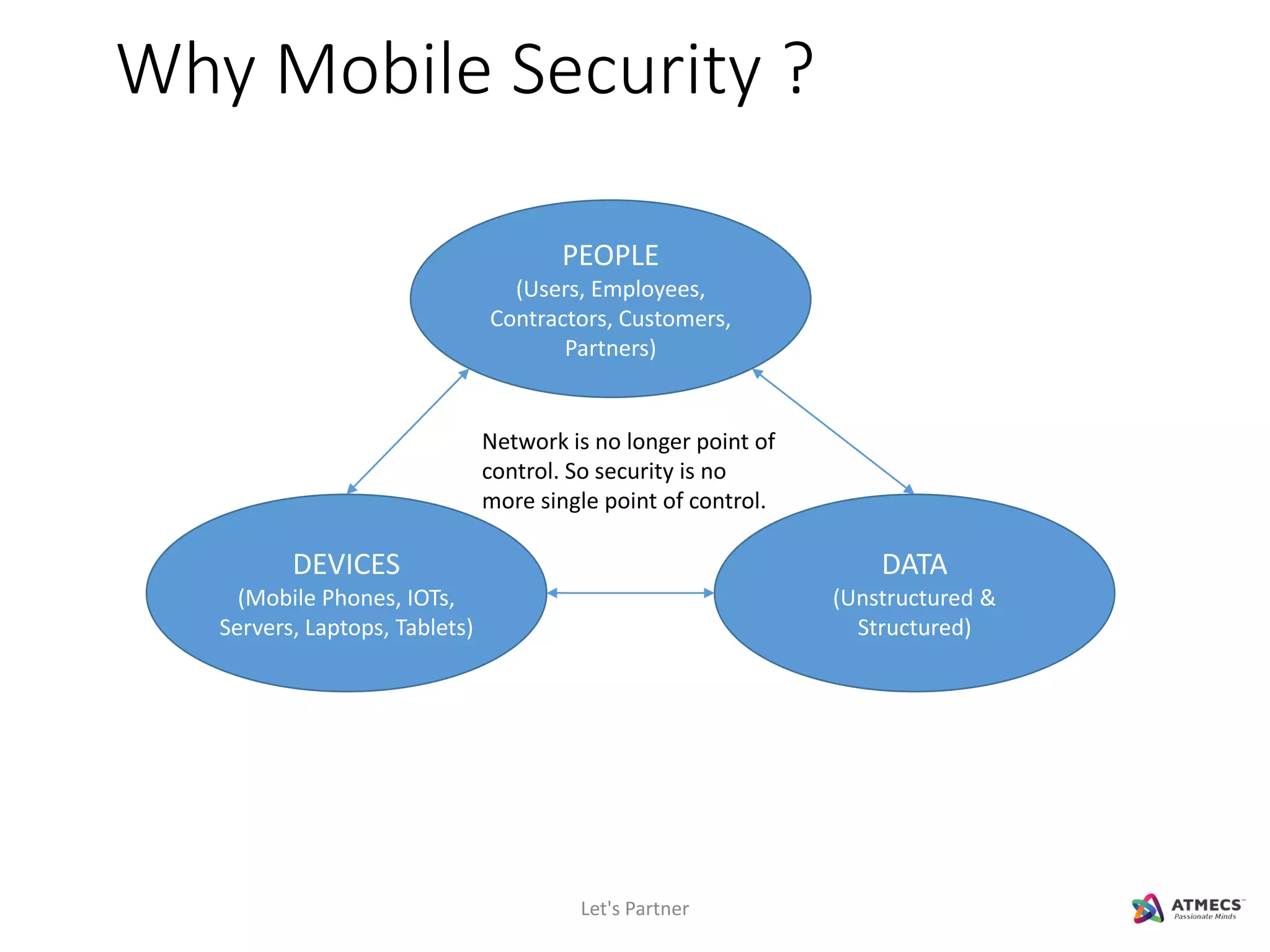
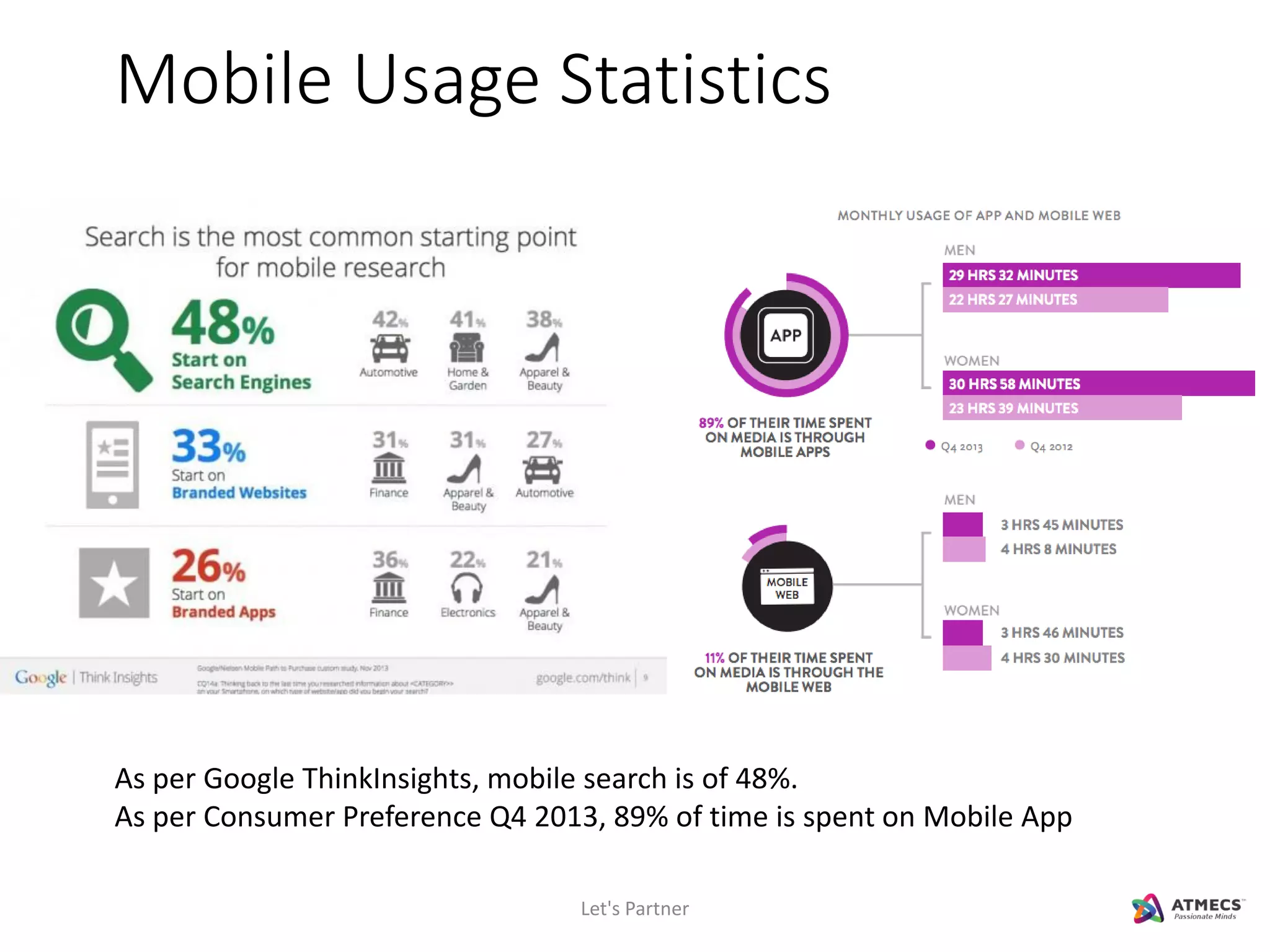
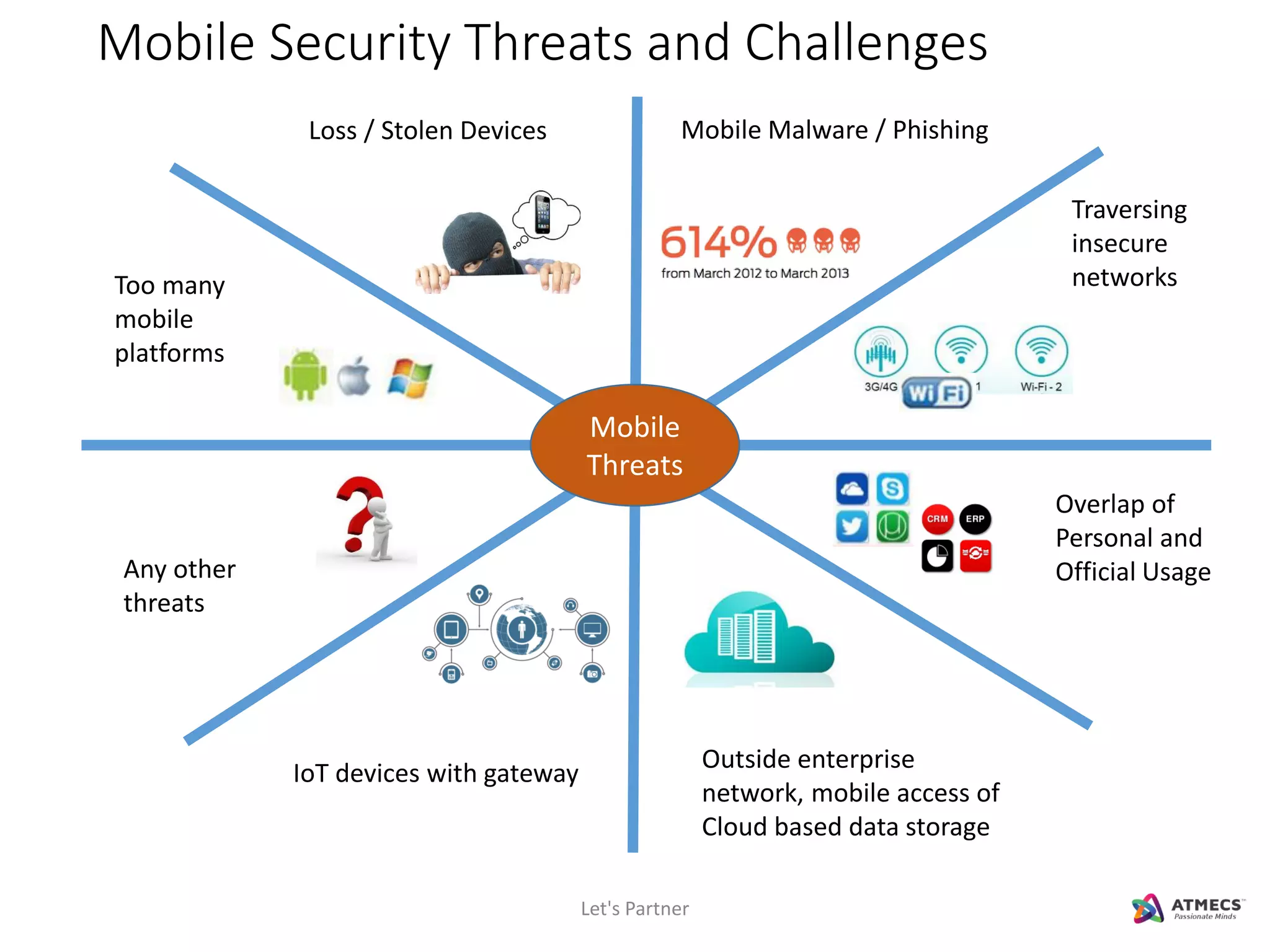
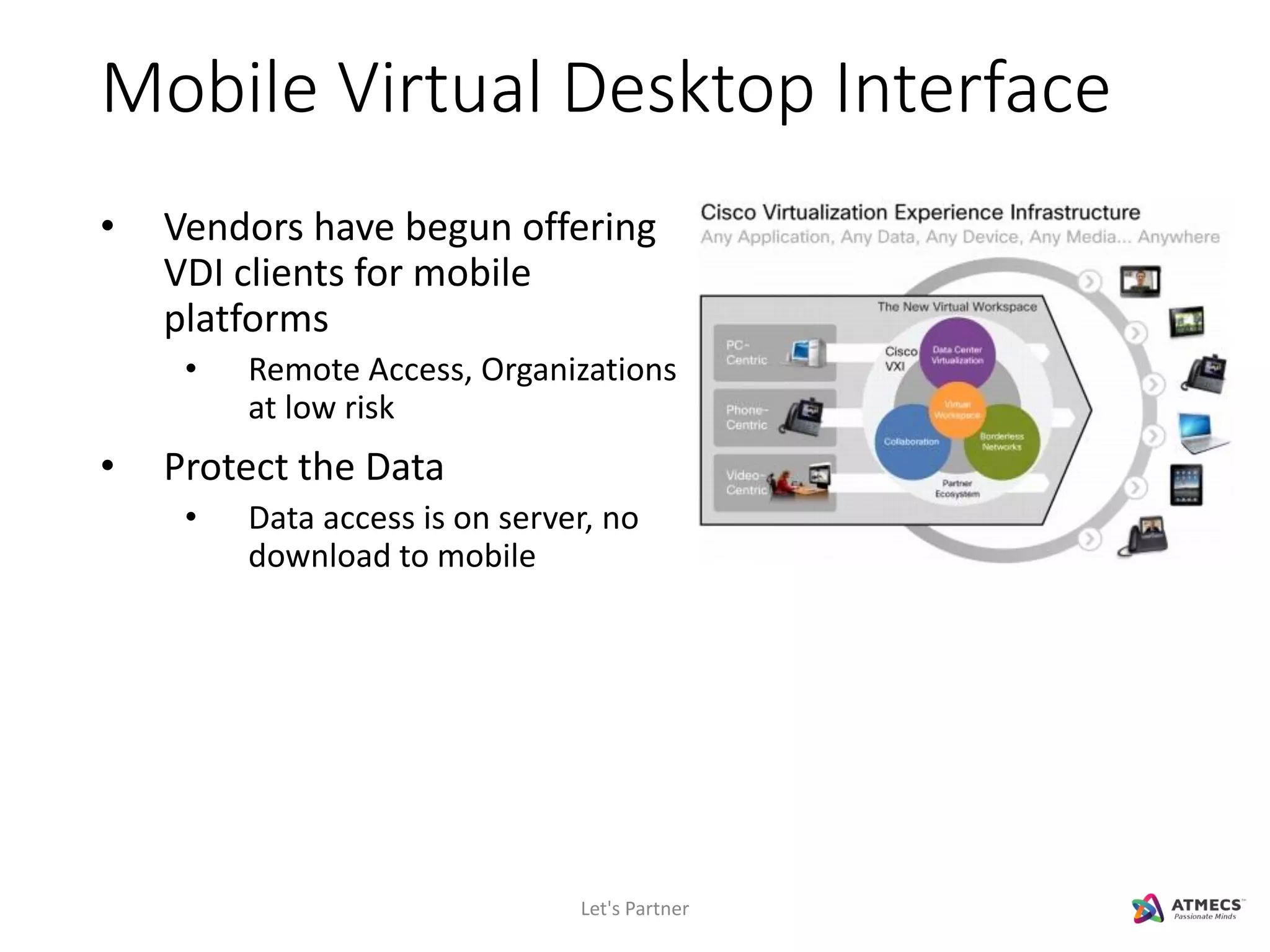
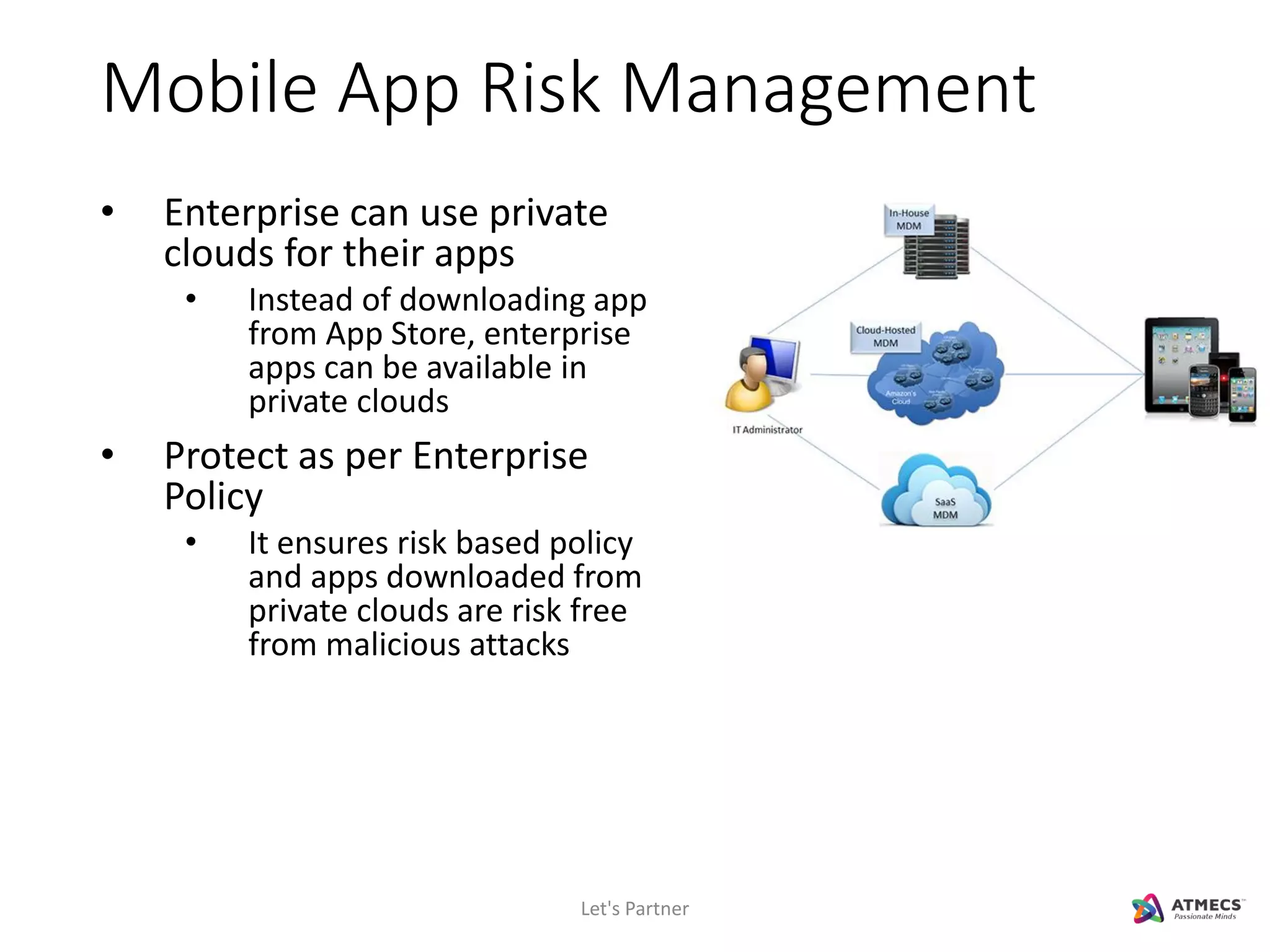
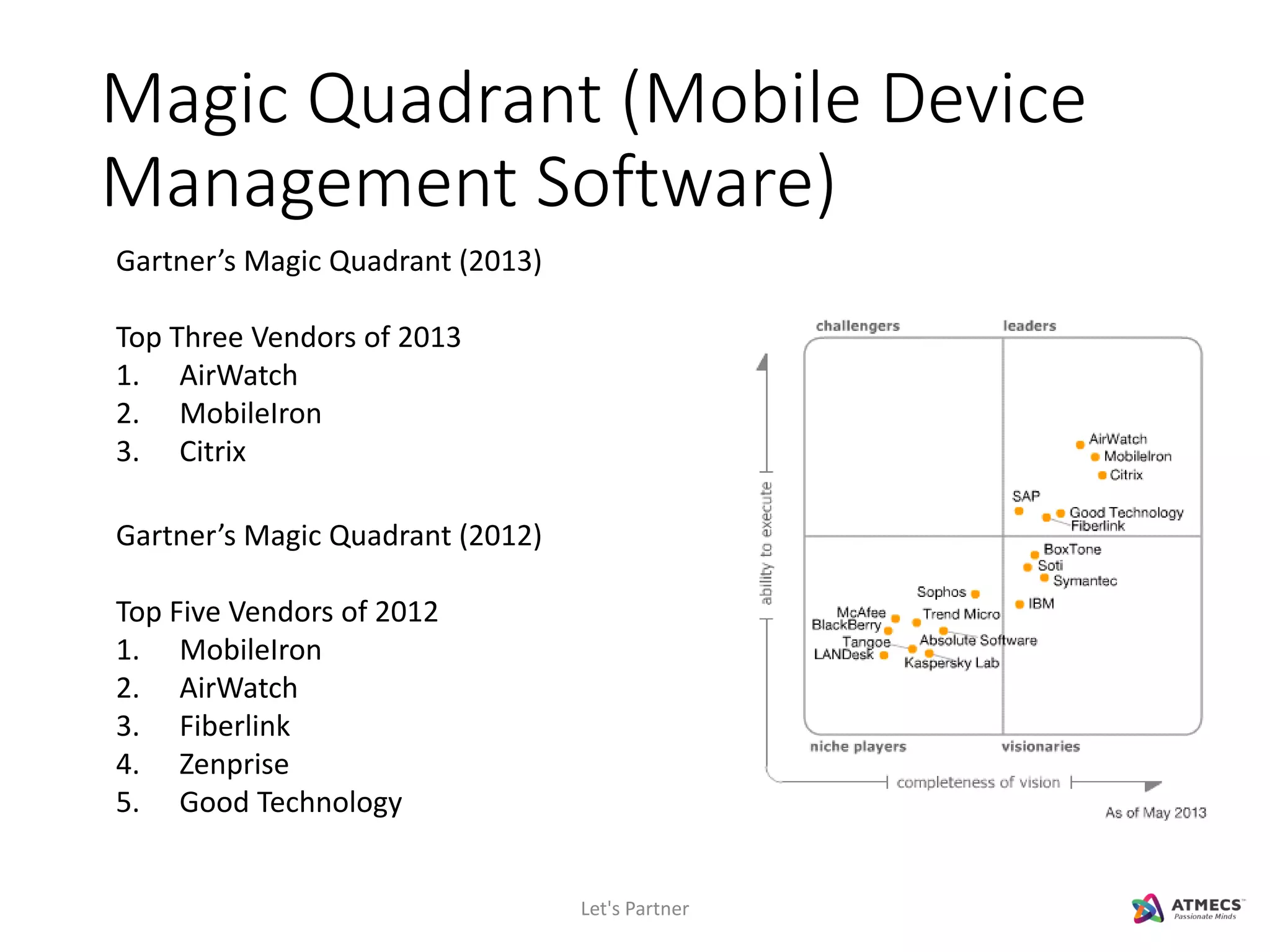
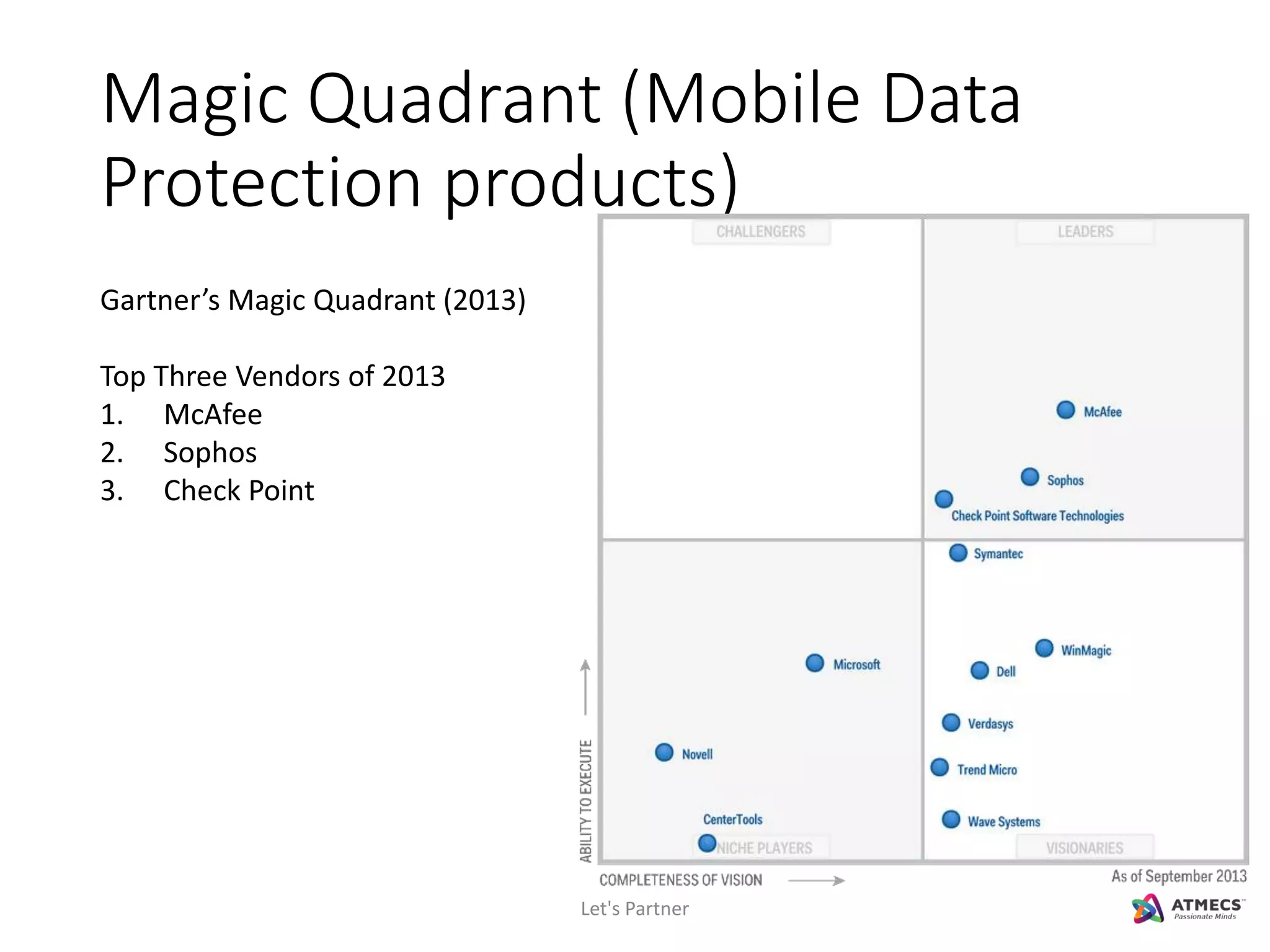
The document discusses mobile security and introduces ATMECS as a technology partner. It covers why mobile security is important due to increasing mobile usage and threats. It outlines various mobile security challenges and strategies including mobile device management, mobile application management, mobile device security, mobile data protection, and more. The document also references Gartner's Magic Quadrant reports on top mobile device management and mobile data protection vendors.