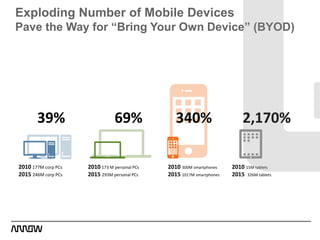
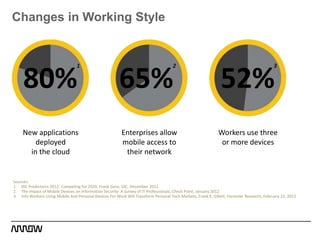
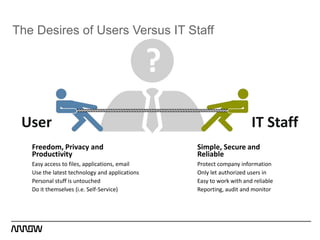
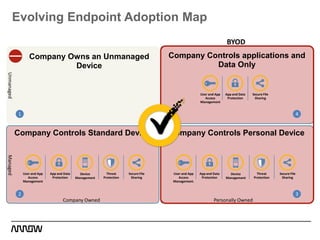
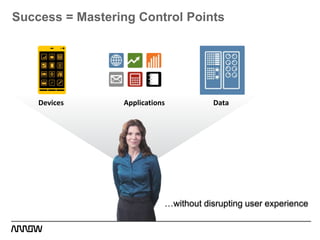
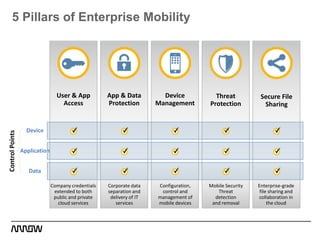
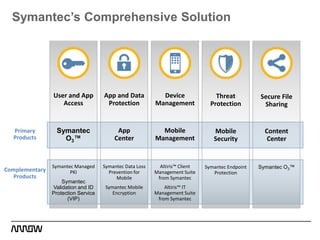
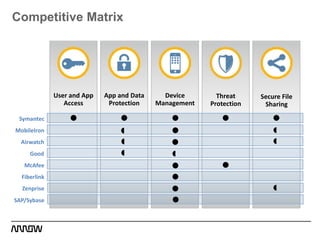
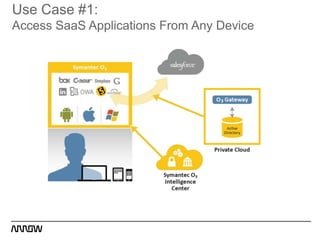
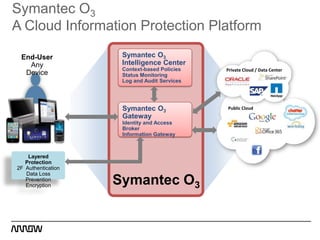
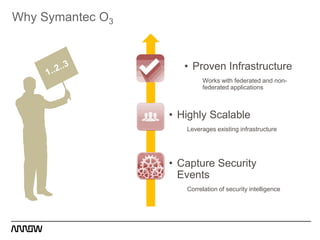
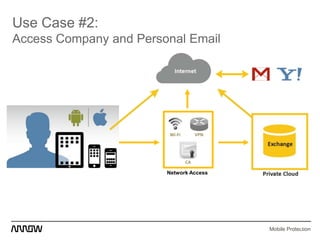
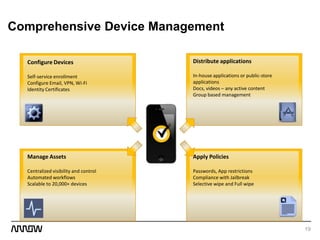
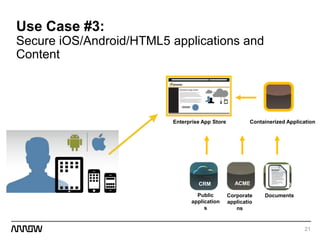
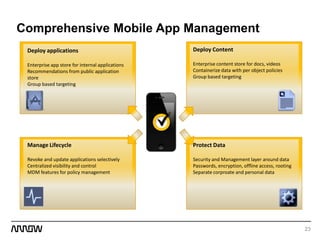
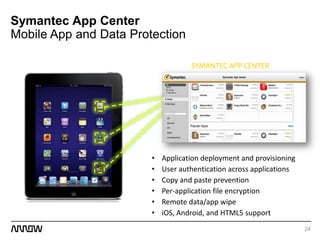
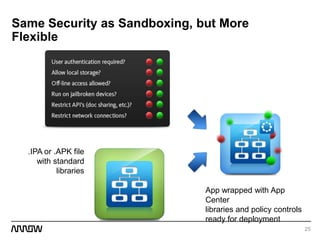
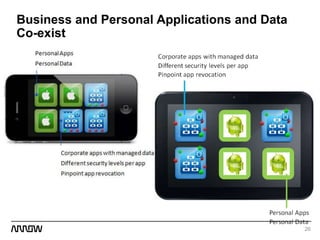
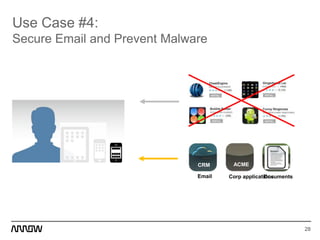
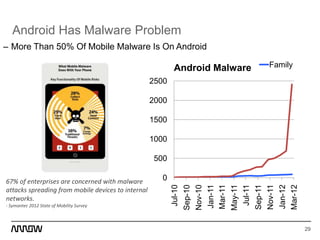
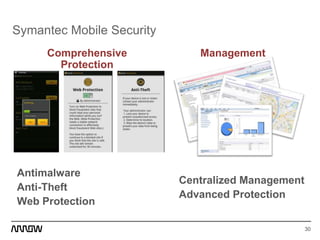
This document provides an overview of Symantec's enterprise mobility solutions. It discusses the growing mobile landscape and bring your own device trends. It then covers the five pillars of enterprise mobility: user and app access, app and data protection, device management, threat protection, and secure file sharing. Symantec's suite of products that address these pillars is presented, including Symantec O3, Mobile Management, Mobile Security, and App Center. Several use cases are reviewed, such as accessing SaaS apps and email from any device, securing iOS/Android/HTML5 apps and content, and providing secure email and malware protection. The presentation concludes with a summary of how Symantec brings it all together with an integrated approach