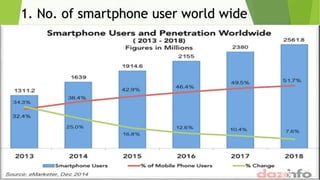
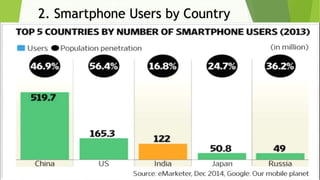
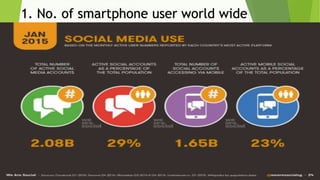
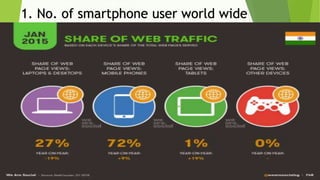
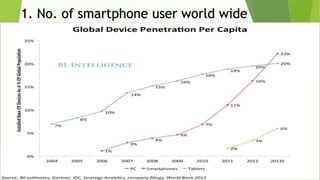
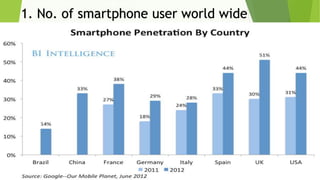
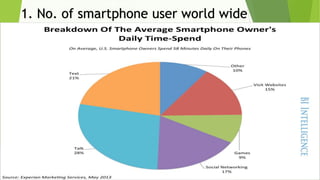
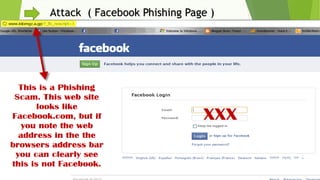
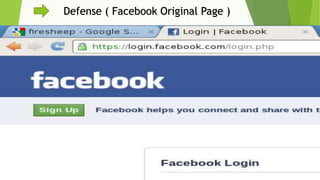
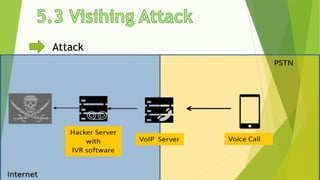
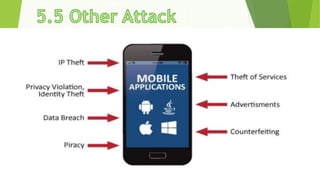
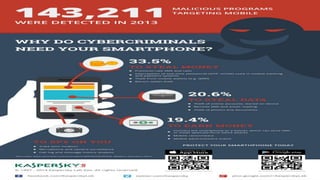
This document discusses various security risks associated with smartphones and methods to protect personal information. It outlines three major smartphone operating systems - Android, iOS, and Windows. It then lists interesting smartphone usage statistics and various attacks hackers can perform by accessing a user's smartphone like listening to calls, accessing internet browsing history, and stealing personal information. The document also provides examples of phishing attacks and ways to protect against them such as checking website URLs and SSL certificates. Physical theft of smartphones is also discussed along with using encryption and lock screens for protection. Downloading apps only from trusted sources is recommended to avoid malicious apps posing as legitimate ones.