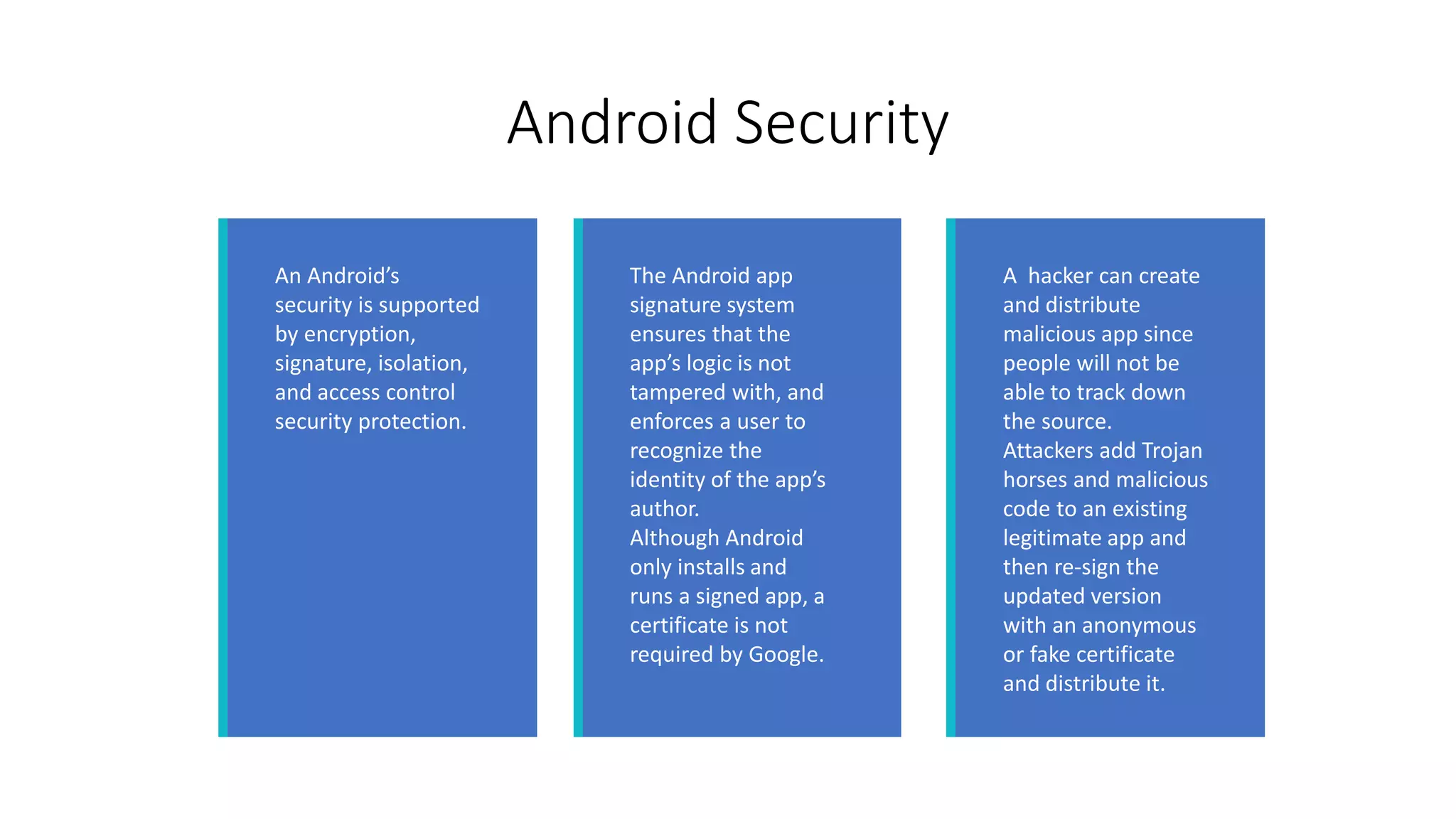
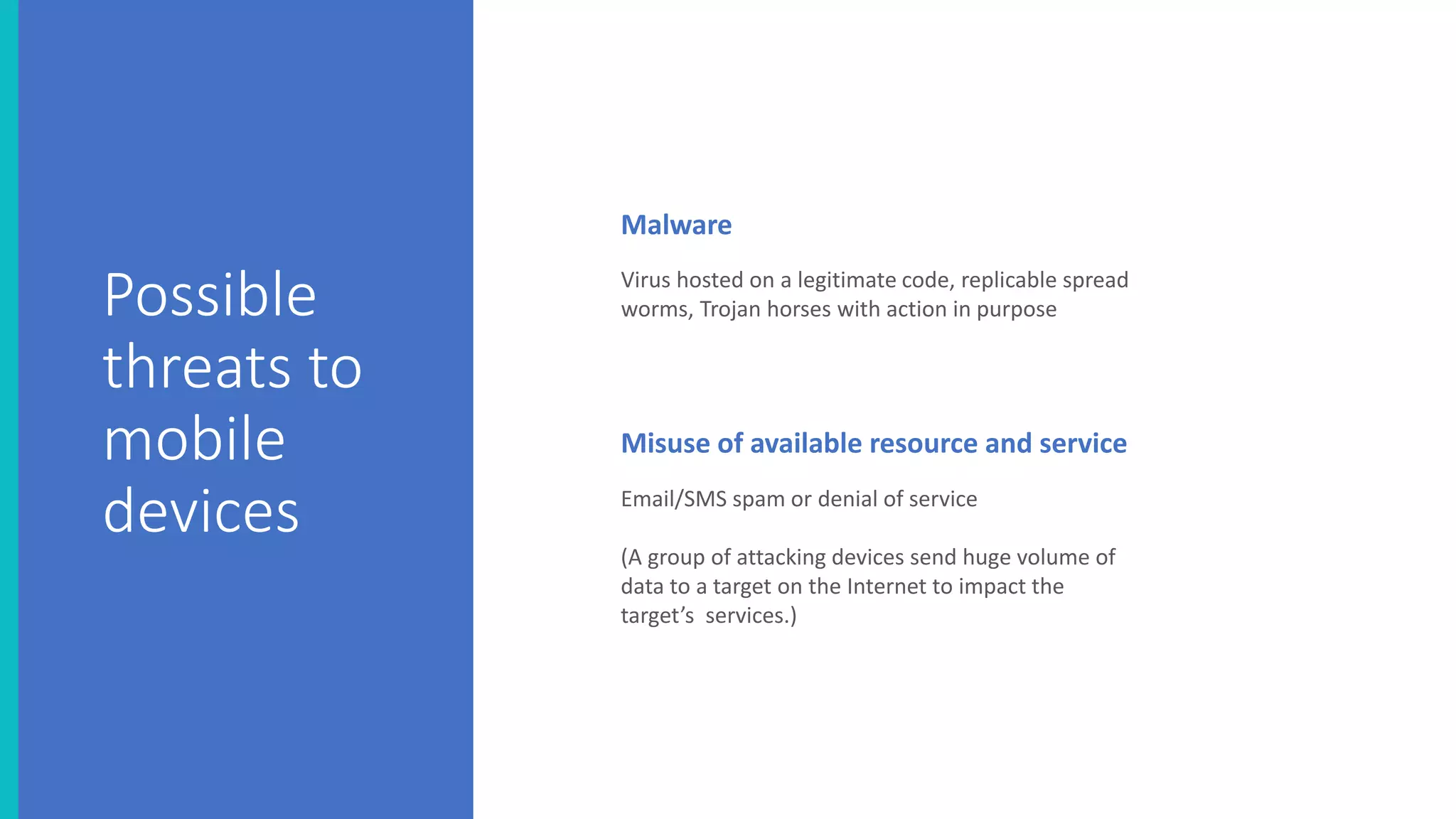
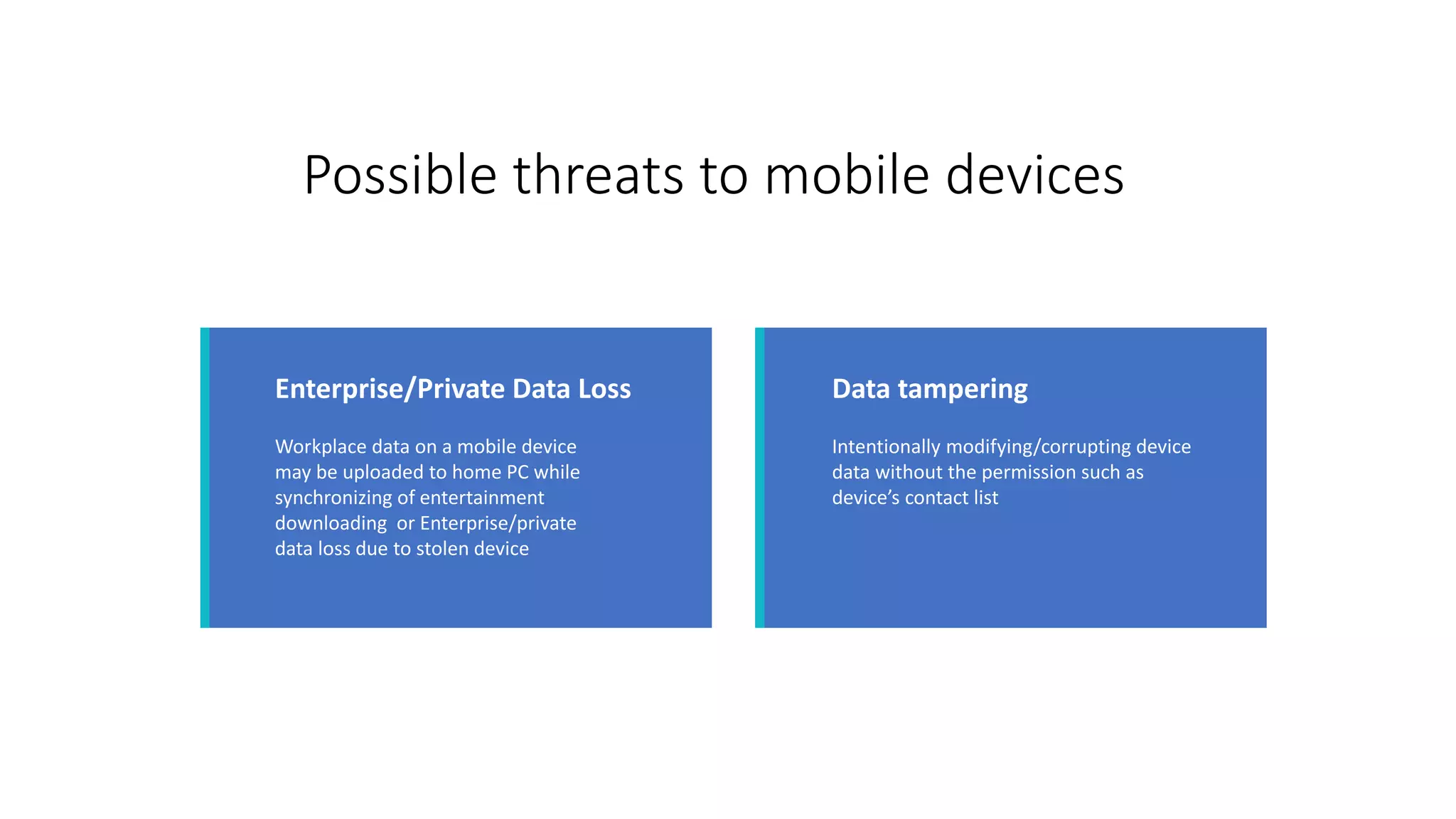
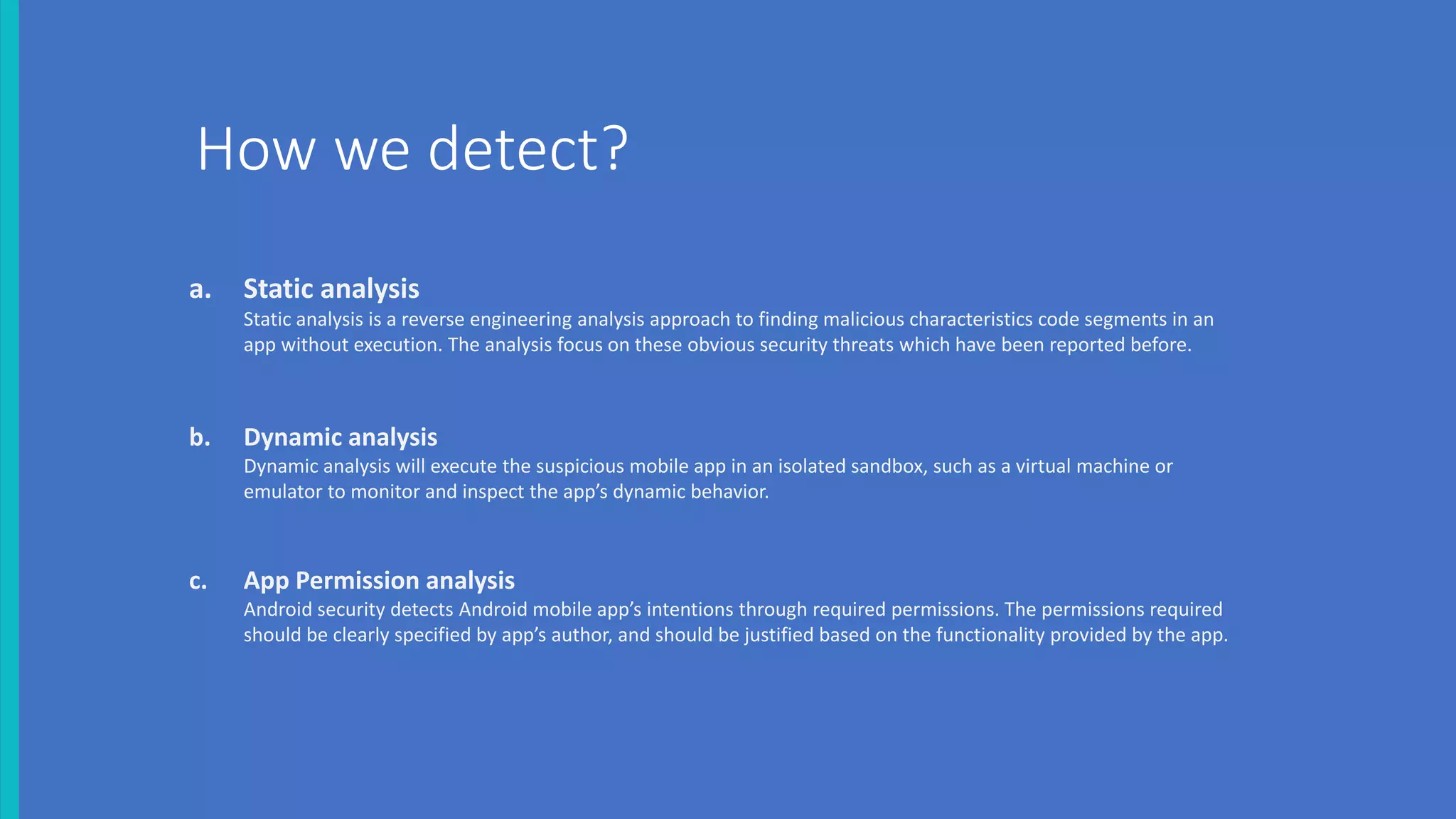
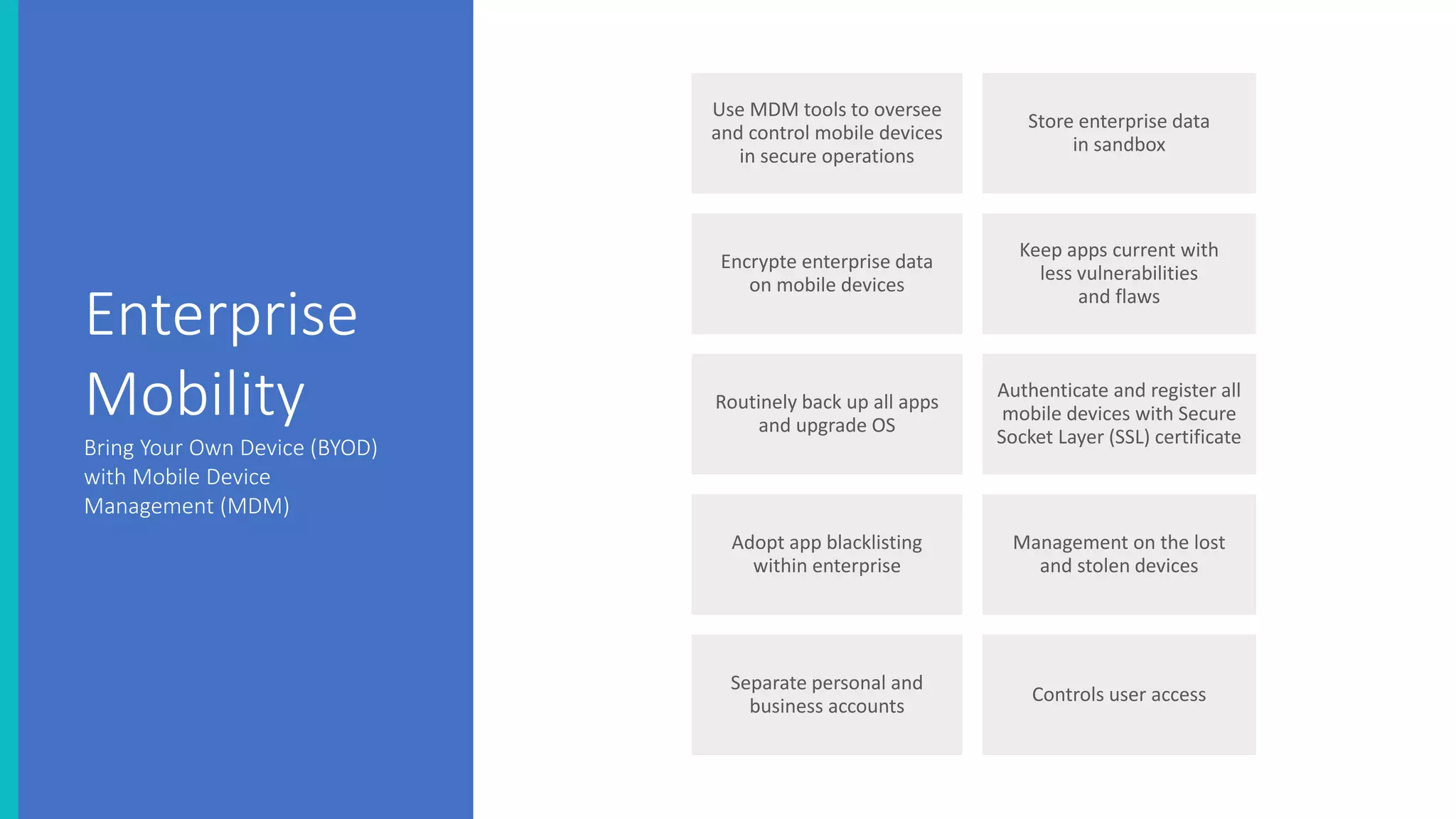
The document discusses the security threats associated with mobile apps and devices, emphasizing the vulnerabilities present in Android and iOS systems. It explains various forms of attacks, such as malware and phishing, as well as outlines security measures like static and dynamic analysis, app permission control, and mobile device management (MDM). Additionally, it highlights the importance of designing apps with security in mind to protect sensitive data.