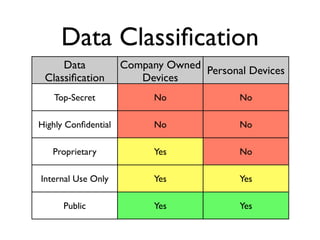
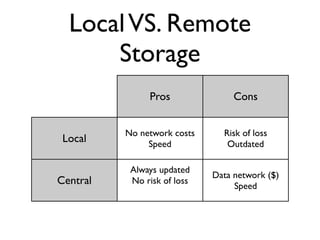
The document presents a detailed overview of mobile security risks, emphasizing the top risks including insecure data storage and weak authentication protocols. It discusses policies for managing company-owned vs. employee-owned devices, including the necessity for data classification and mobile device management solutions. The presentation also highlights best practices for secure mobile application development and risks associated with mobile device usage such as rogue apps and hotspot access.