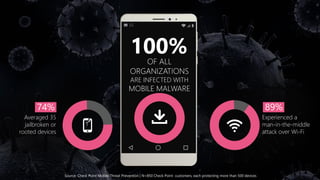
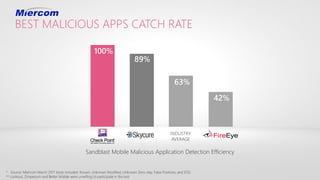
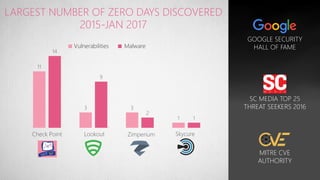
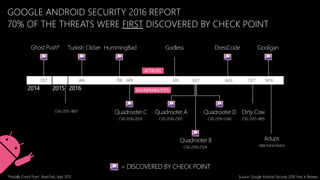
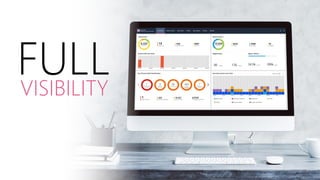
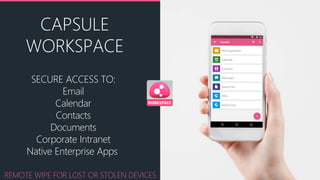
Mobile devices pose a significant security threat to enterprises as they provide a new window into corporate networks. Check Point's SandBlast Mobile solution uses advanced app analysis and a cloud-based behavioral engine to detect both known and unknown mobile threats across infection vectors. It provides full visibility and protection of mobile devices while integrating simply with existing EMM and security systems.