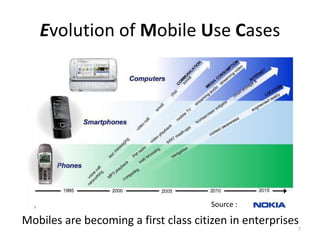
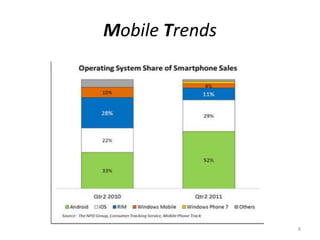
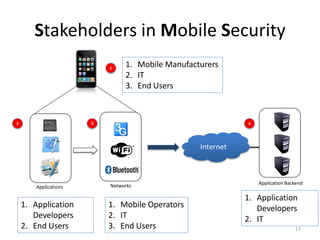
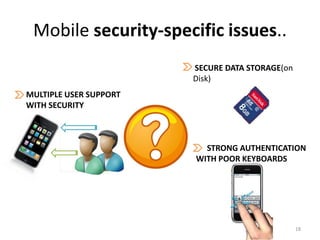
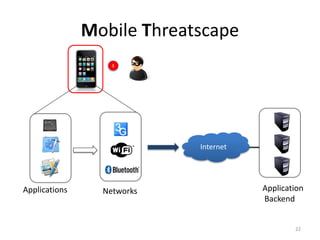
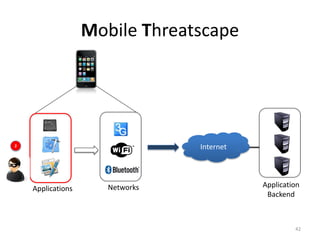
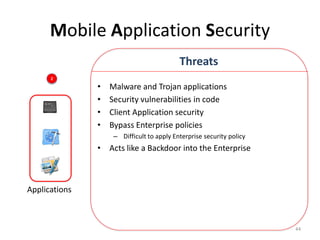
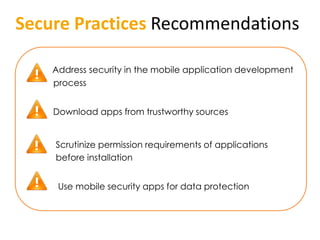
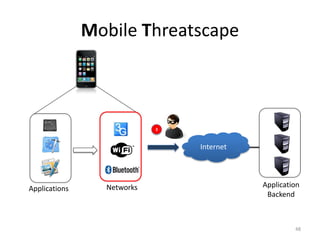
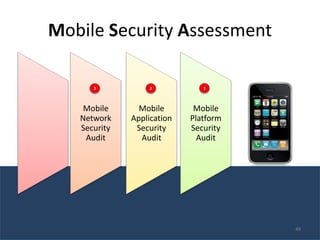
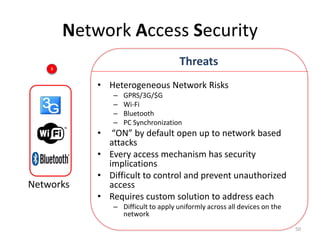
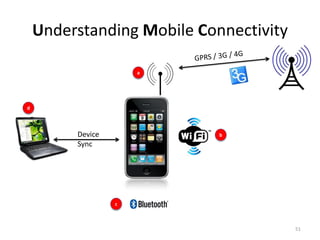
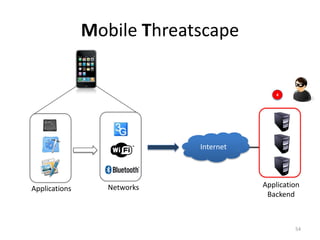
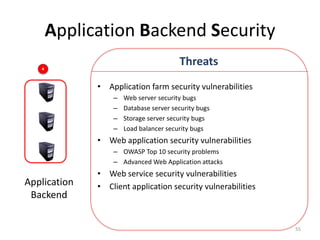
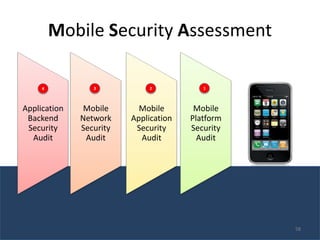
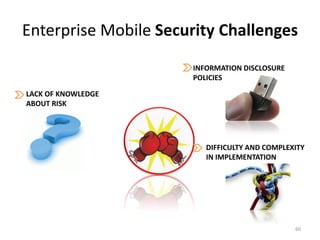
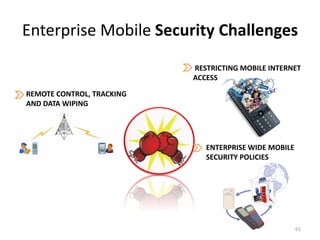
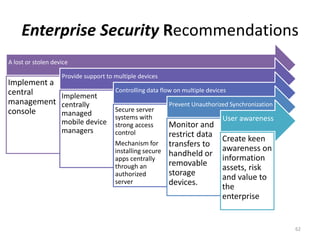
The document outlines the evolution and challenges of mobile security, highlighting trends, threats, and stakeholders involved. It emphasizes the need for robust security measures across various mobile platforms such as Android, iOS, and Windows Phone, while addressing specific vulnerabilities and attack vectors. Recommendations are provided for organizations to enhance mobile security practices and maintain enterprise security in a rapidly evolving mobile landscape.