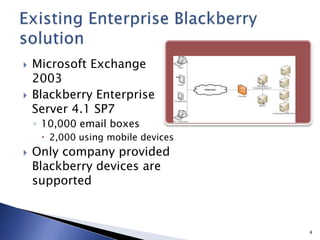
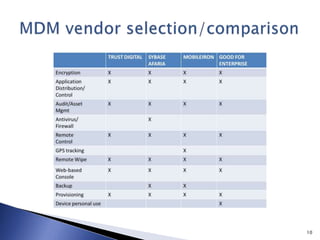
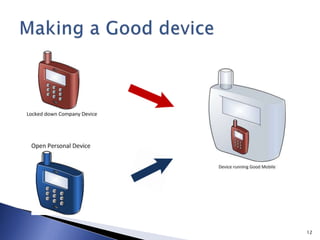
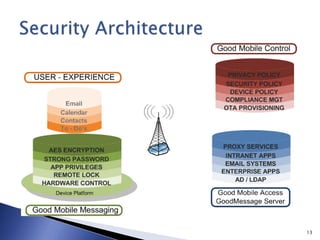
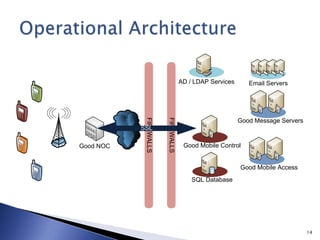
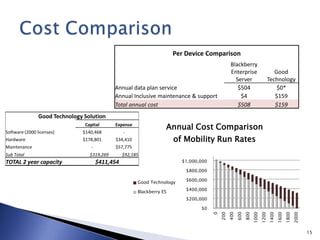
This document discusses mobile app security and the need for companies to securely provide access to internal systems and information for mobile workforces. It outlines requirements such as supporting the major mobile platforms while leveraging existing Exchange and Blackberry investments. The proposed solution is a Mobile Device Management system from Good Technology which would allow centralized management and security policies for employee-owned devices accessing corporate resources, at a lower cost than traditional Blackberry solutions.