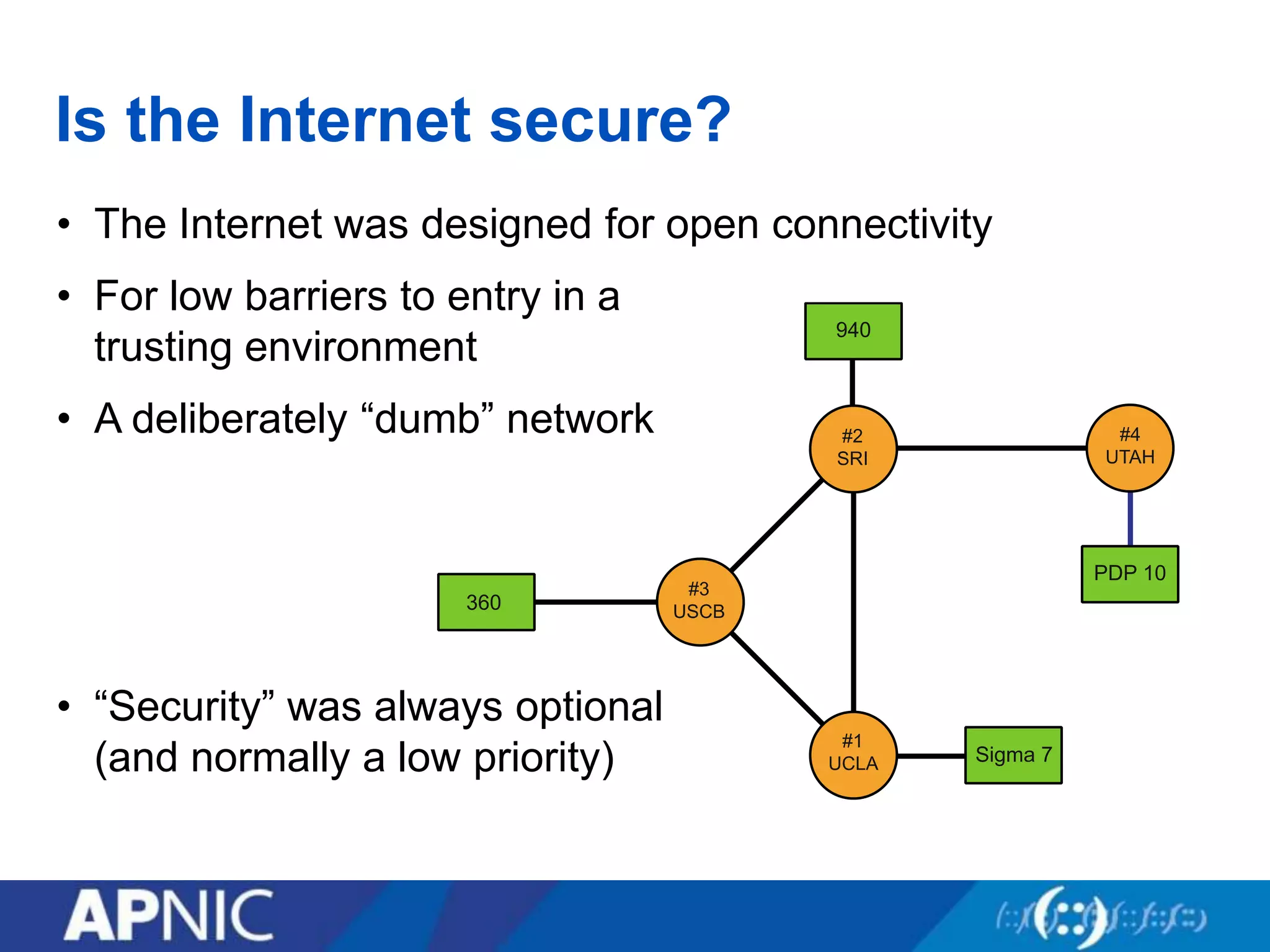
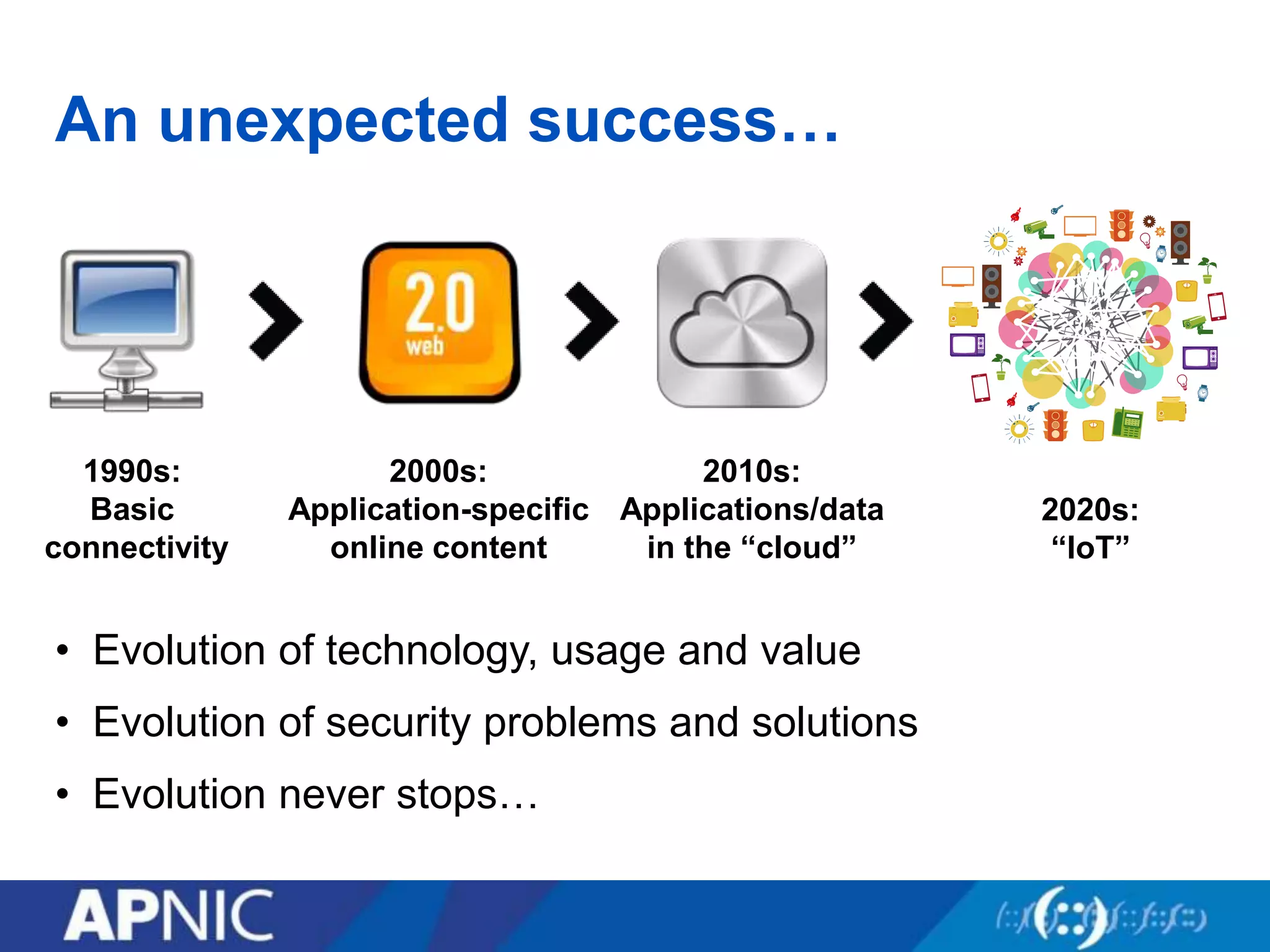
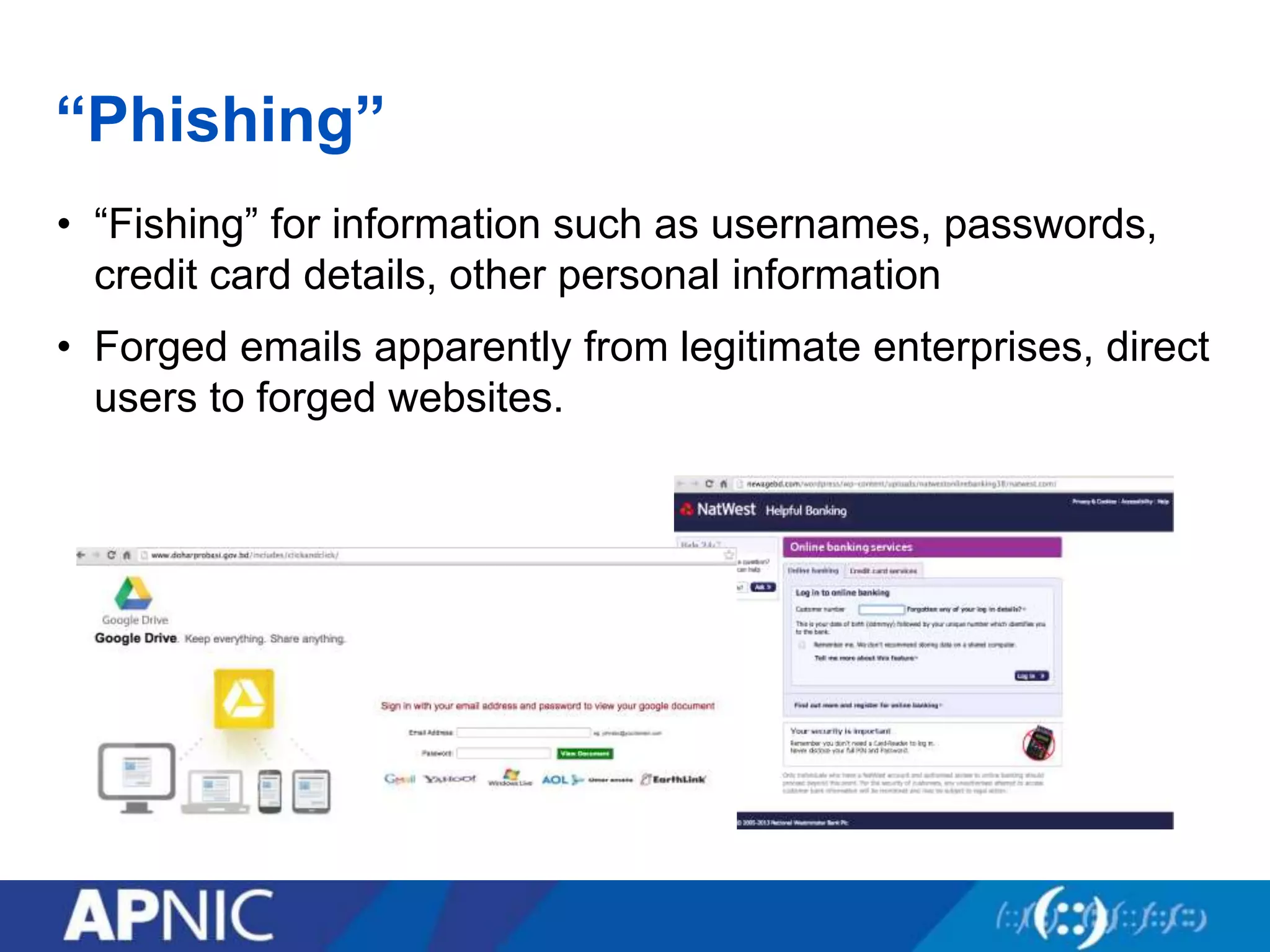
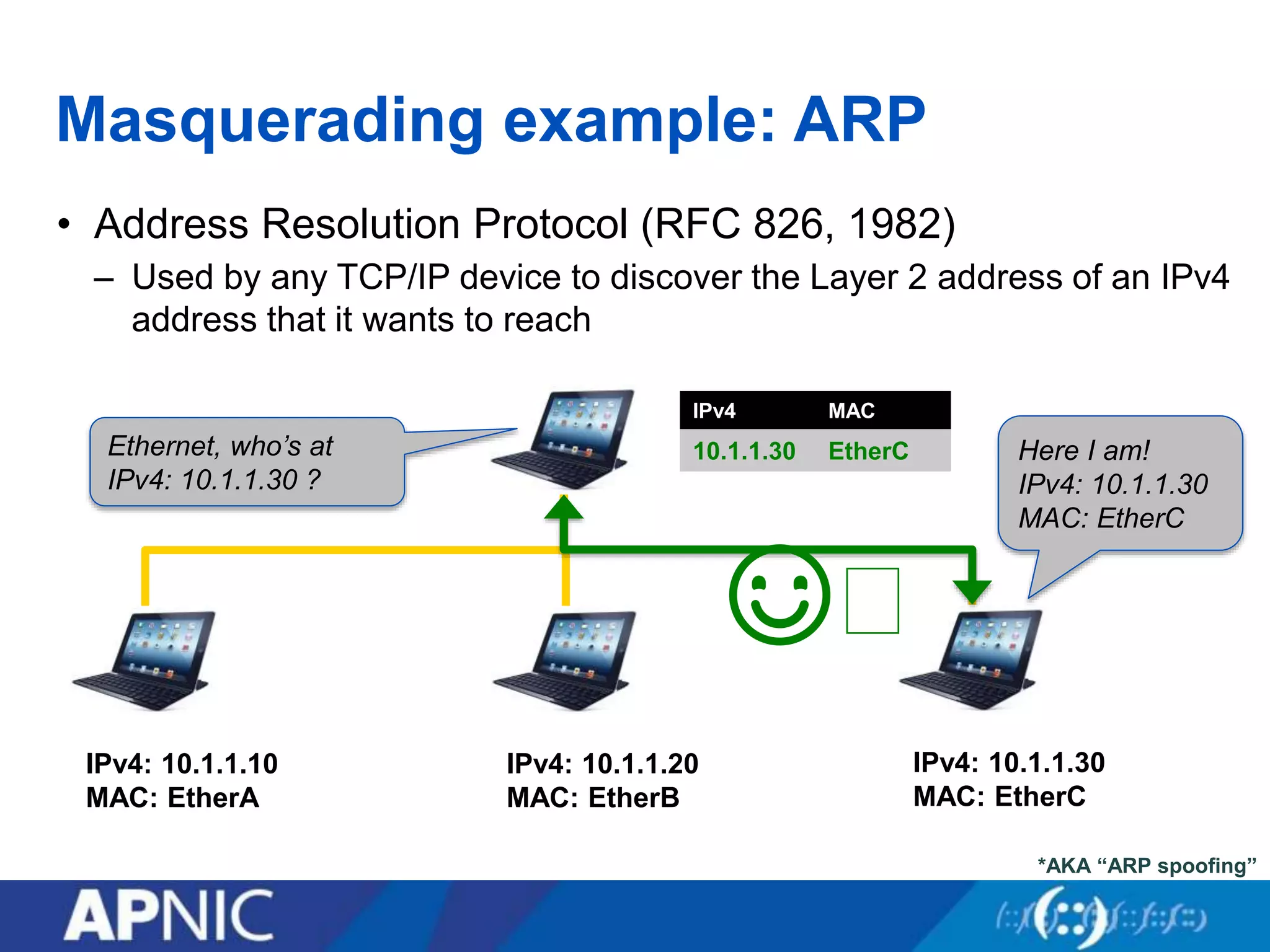
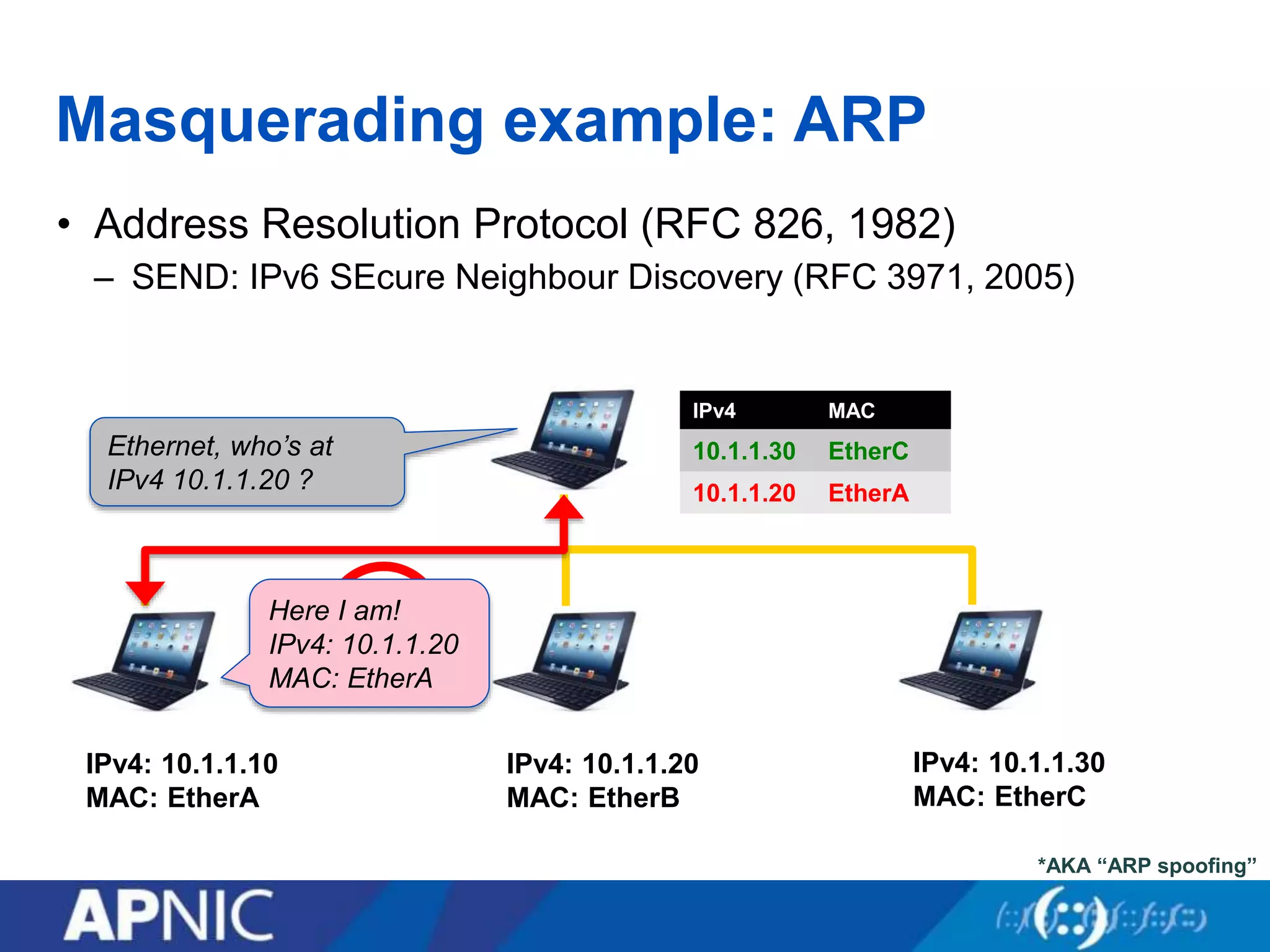
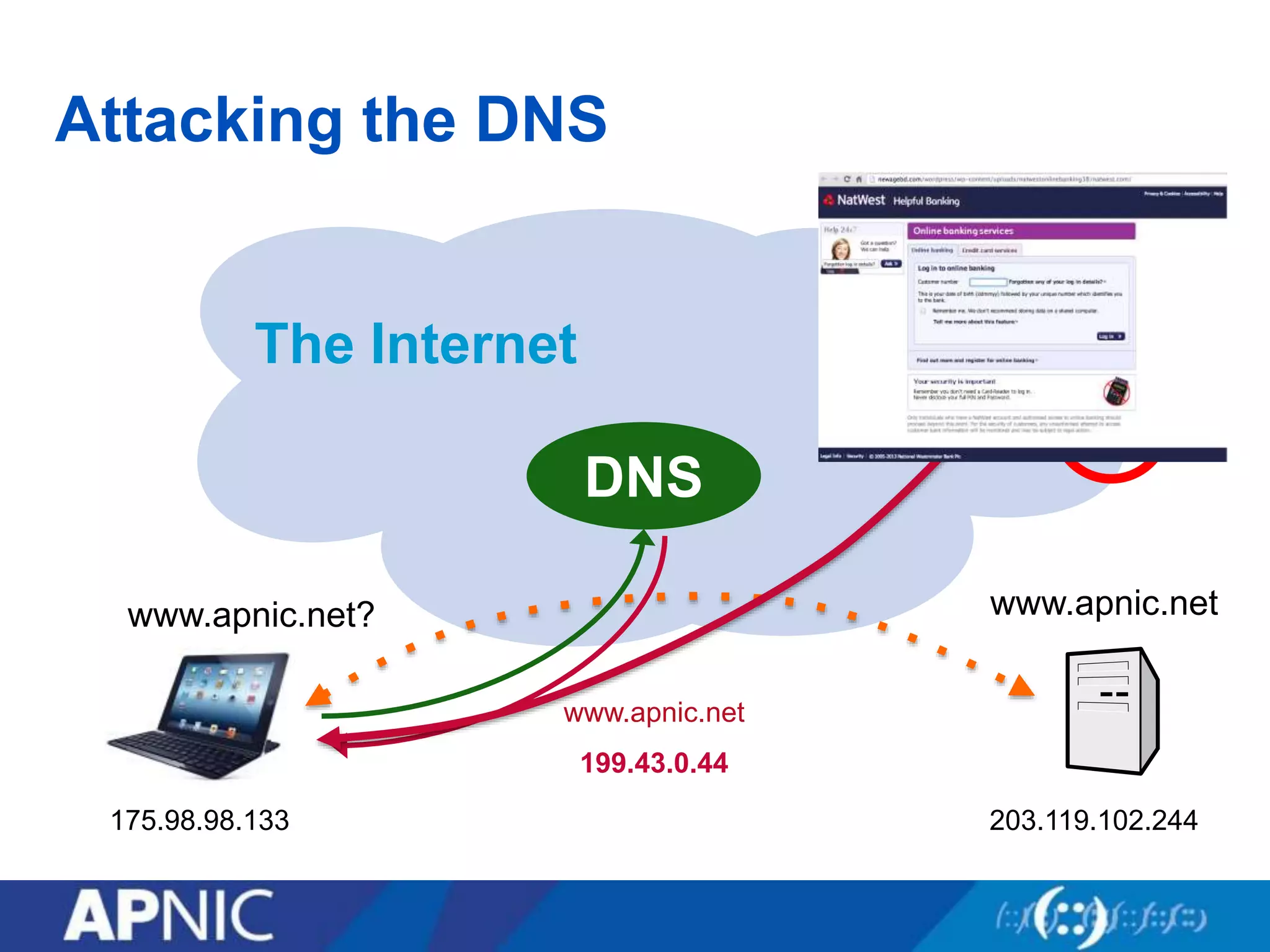
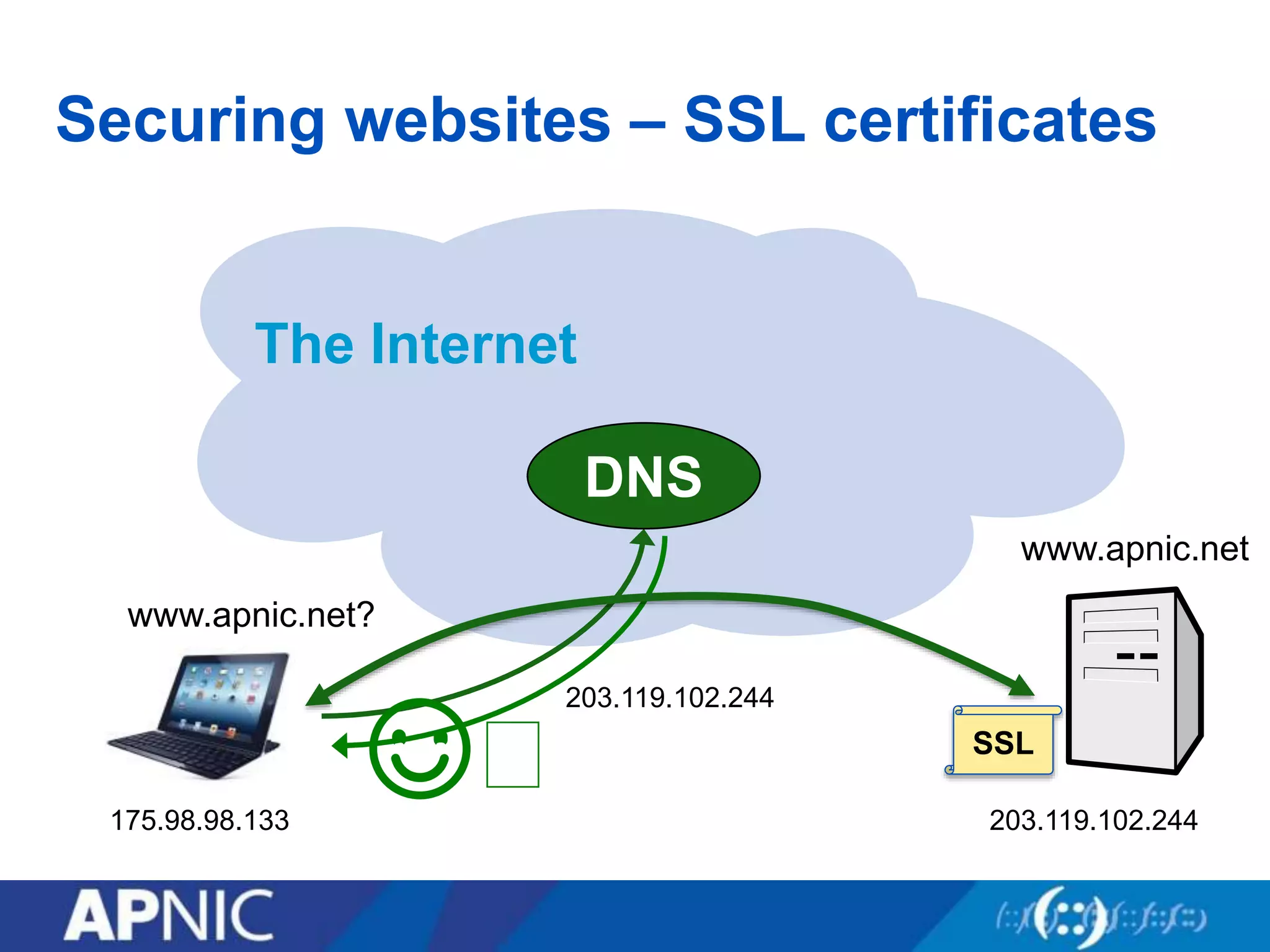
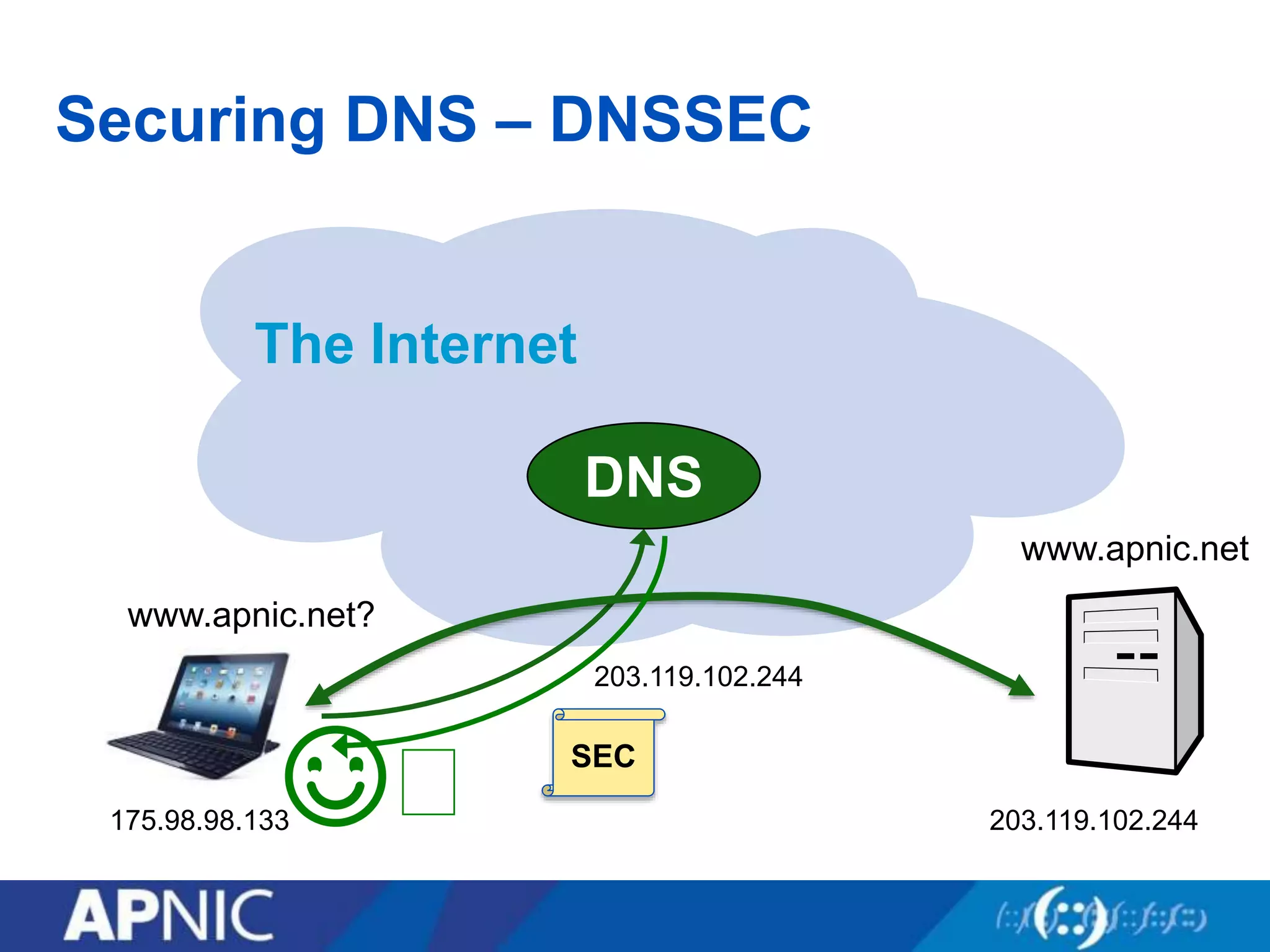
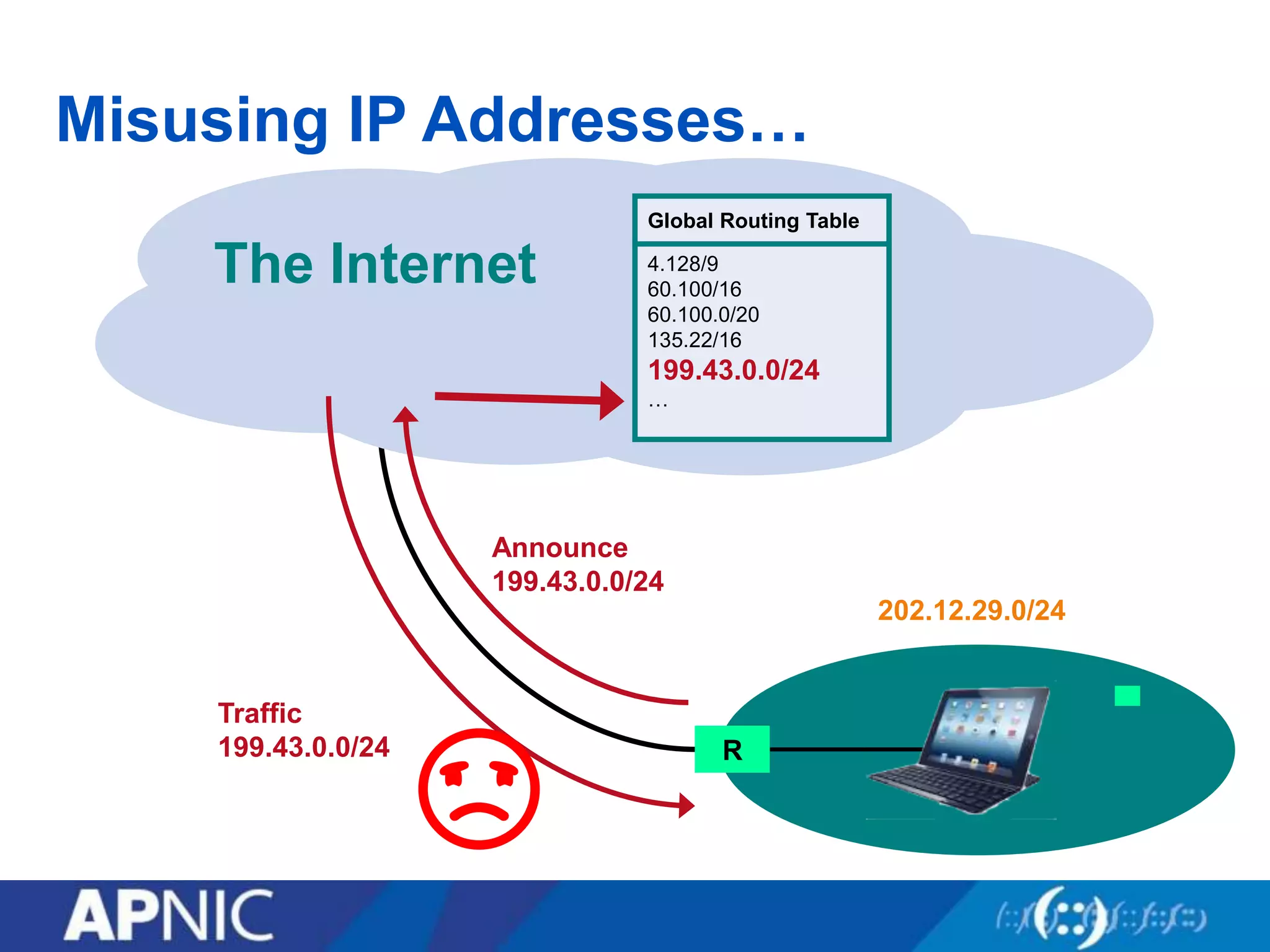
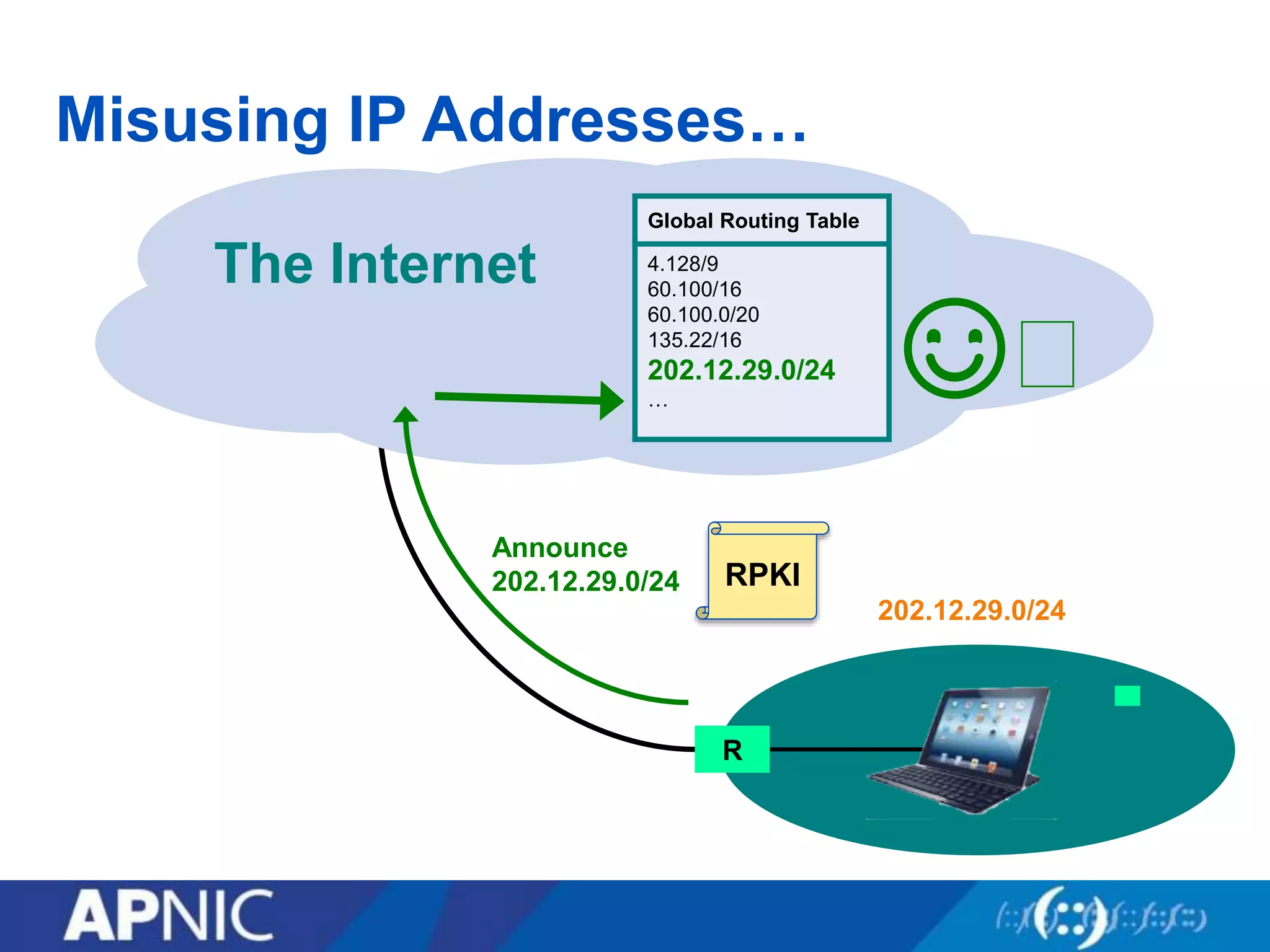
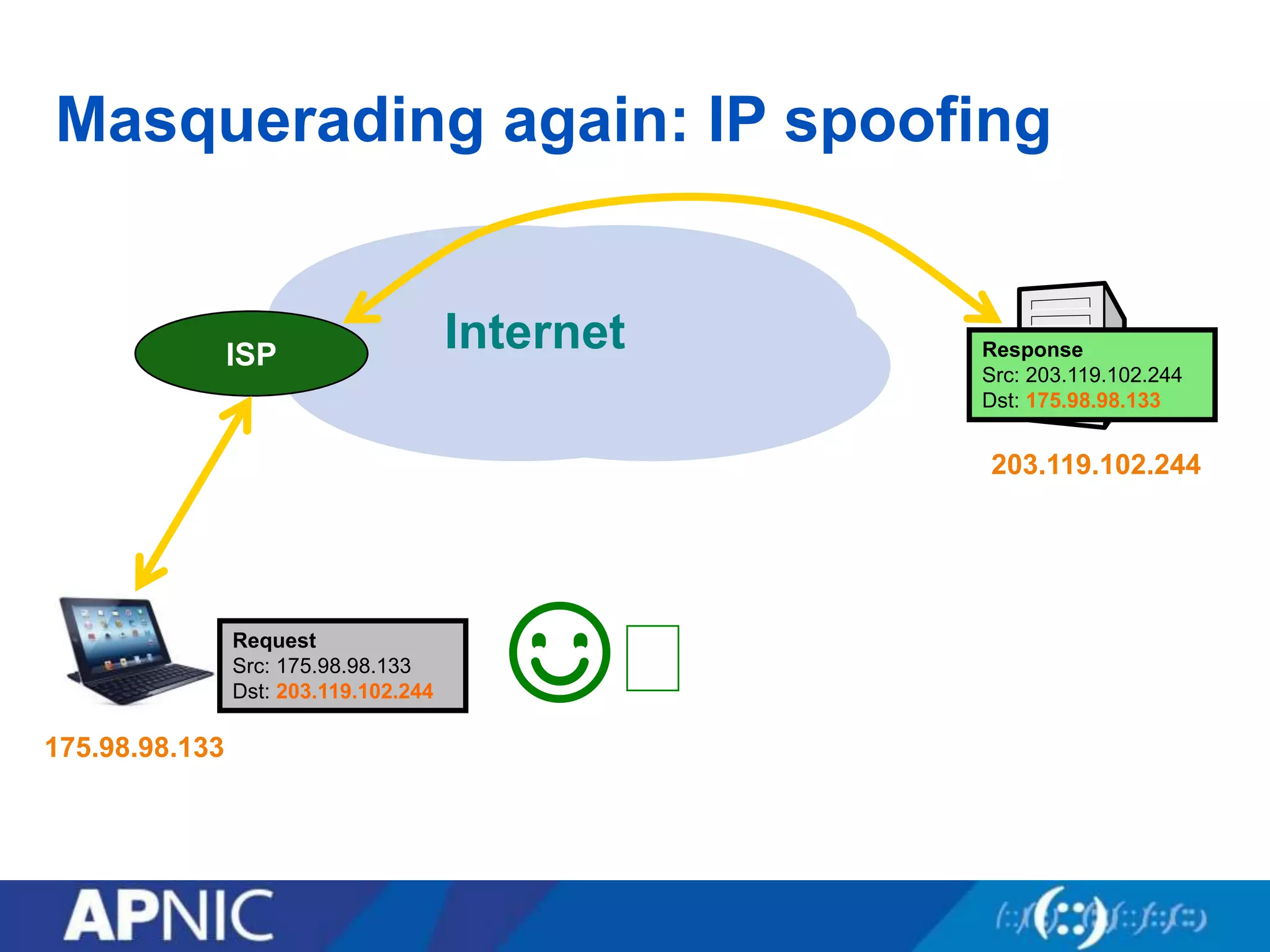
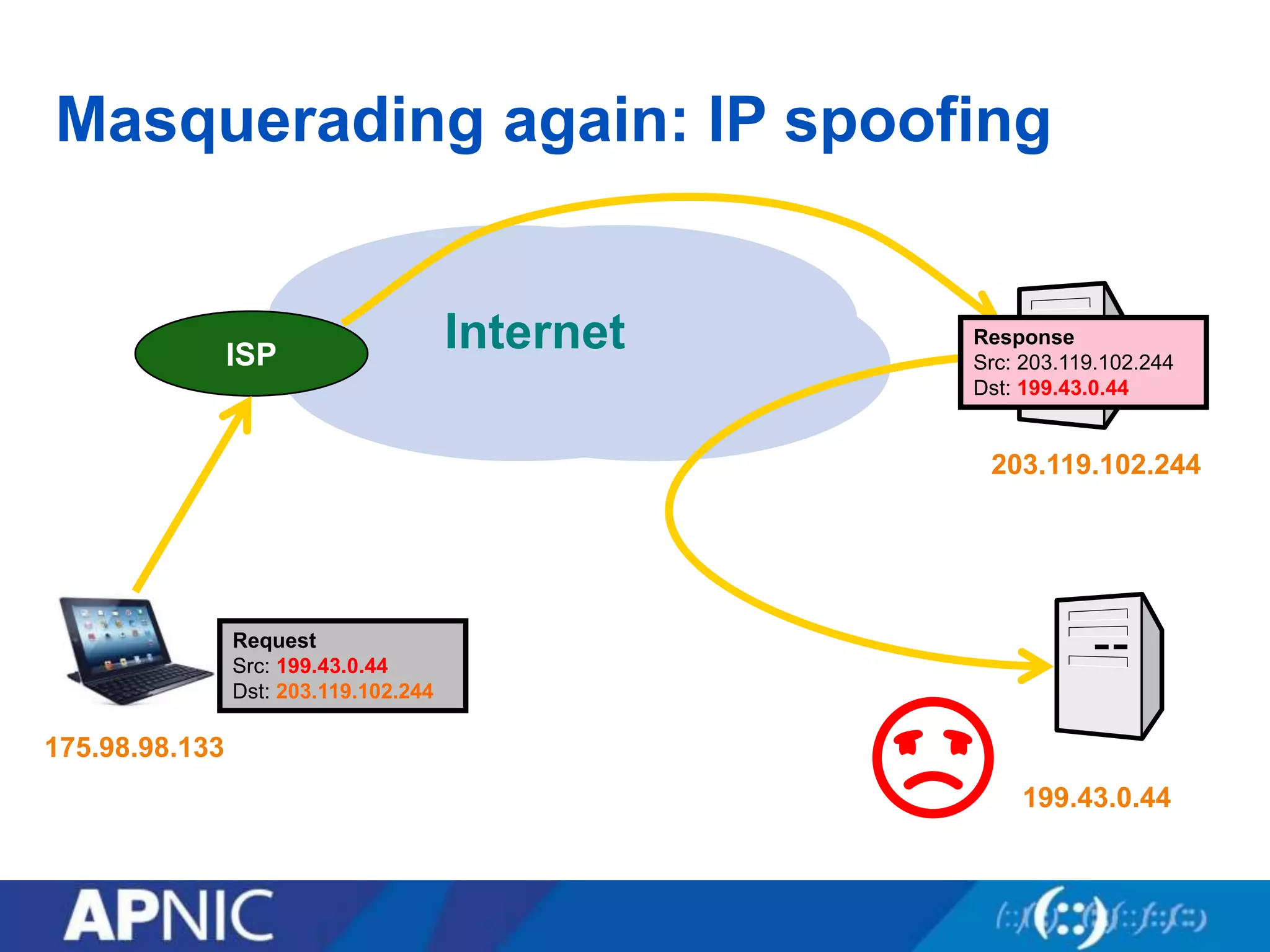
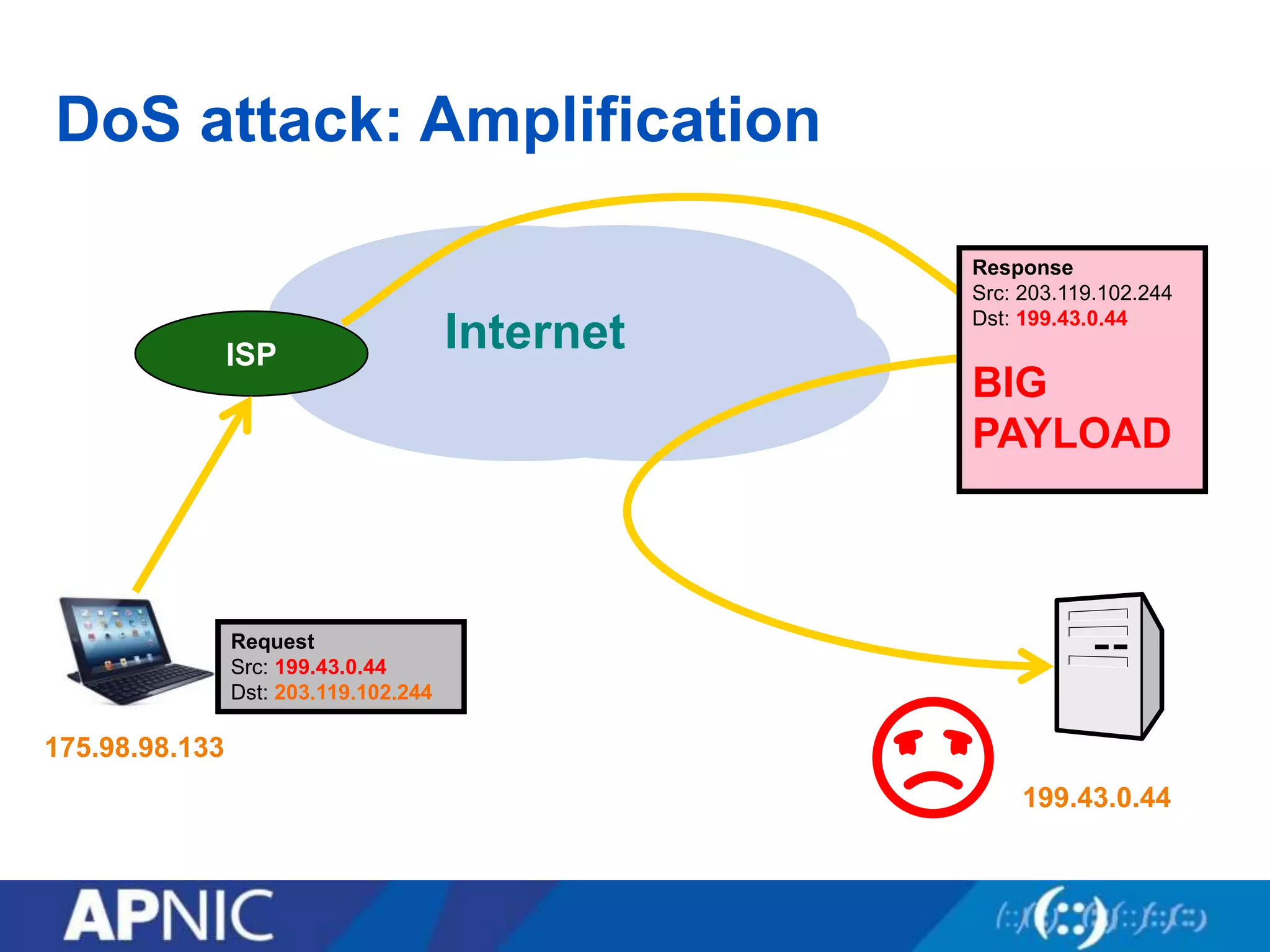
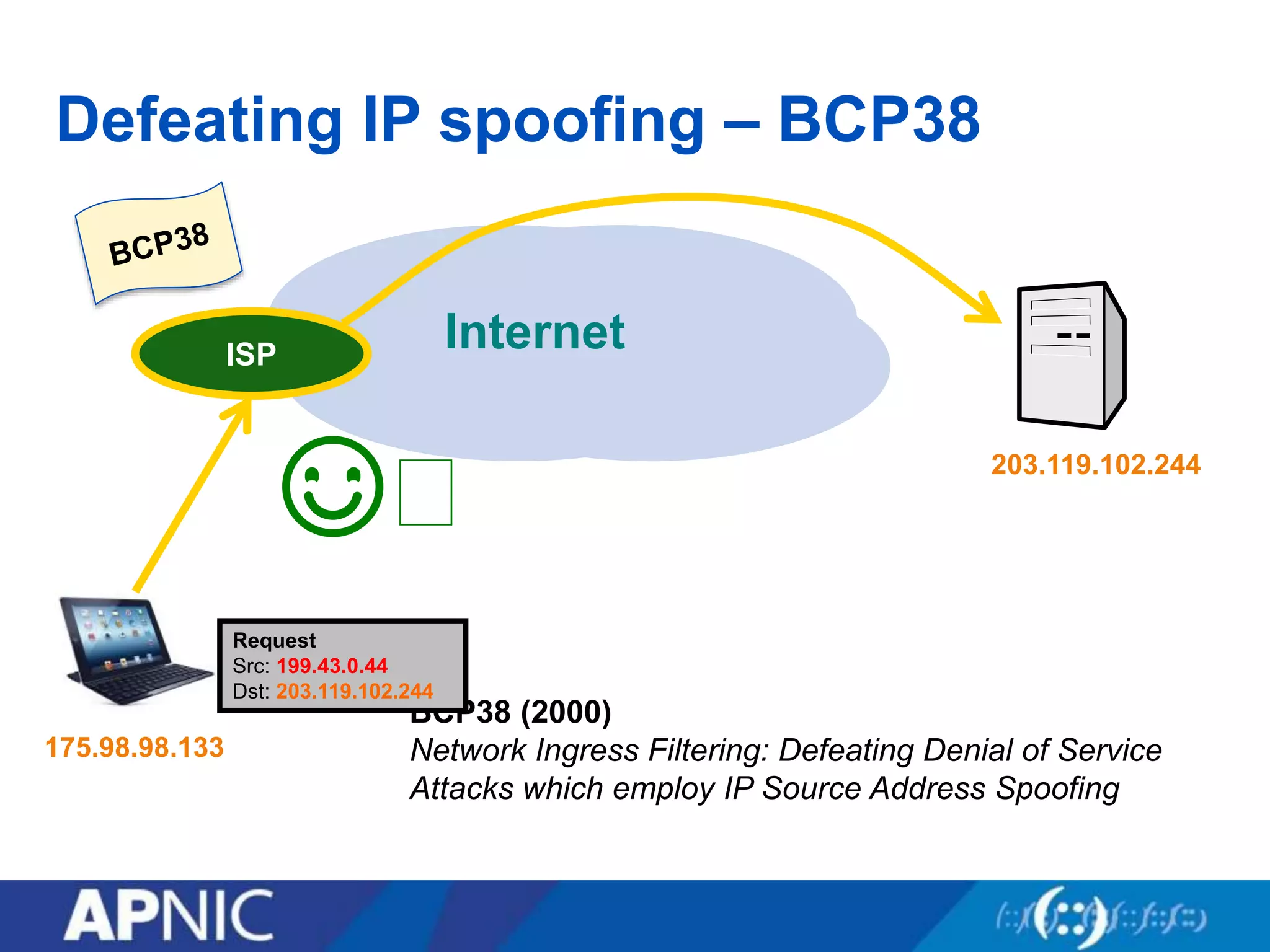
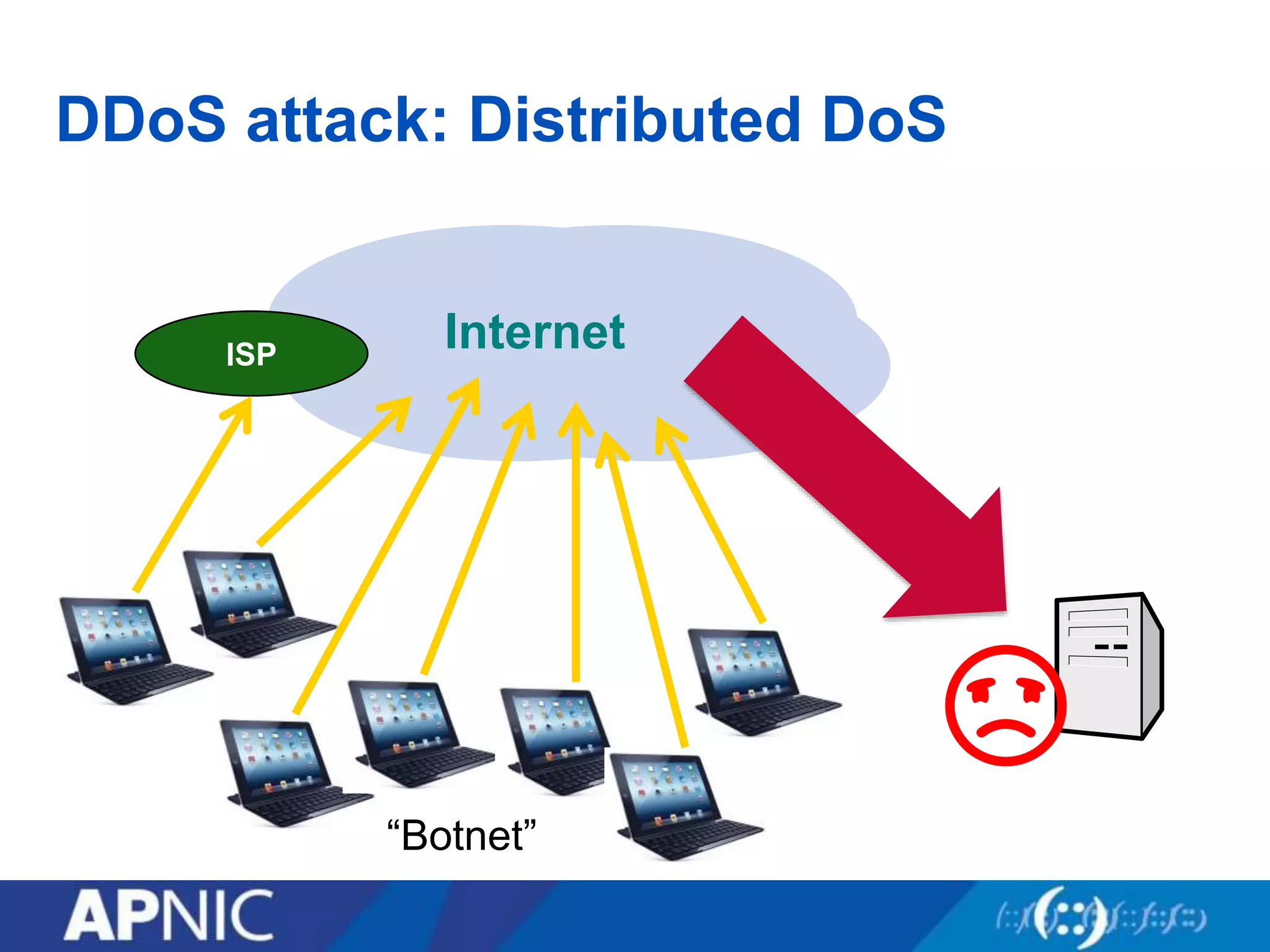
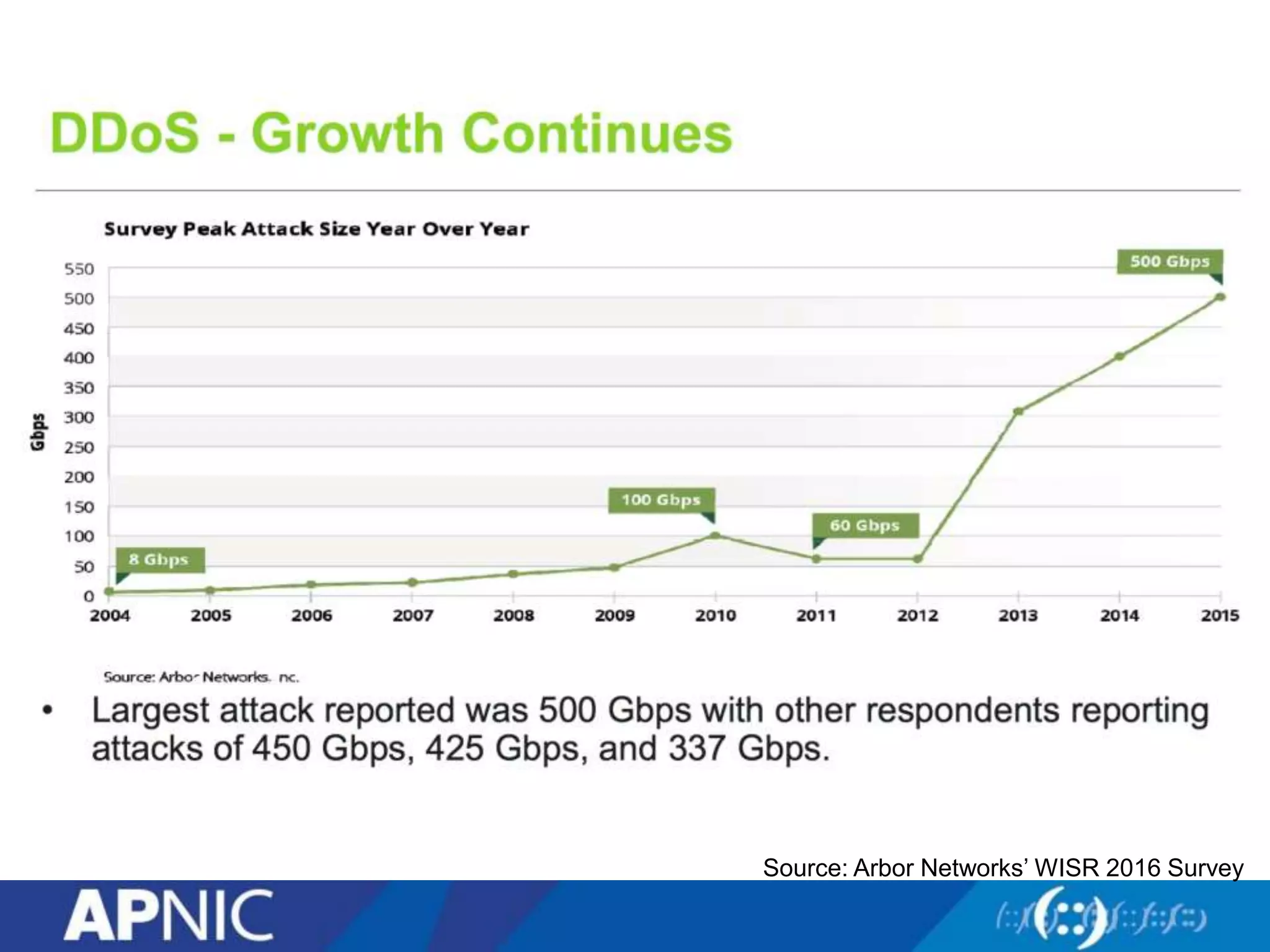
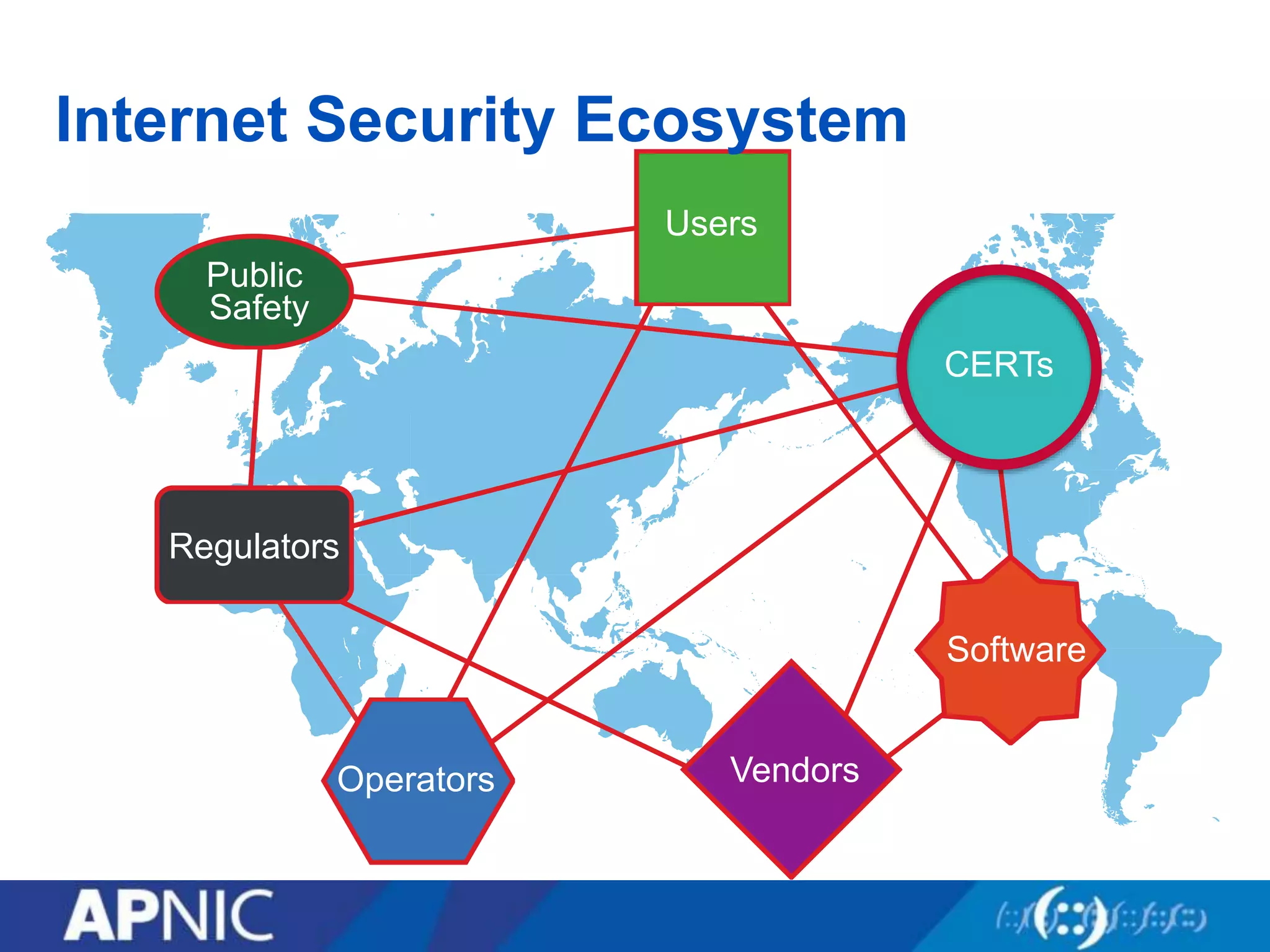
The document discusses the fundamental aspects of network security and the challenges posed by the design of the internet, which was created with a focus on openness rather than security. It highlights myths and the realities of internet security, including threats, vulnerabilities, and the evolution of technology, as well as the growing importance of securing services and networks. Key topics include social engineering, the implications of IPv6 and IoT on security, and the overall internet security ecosystem.