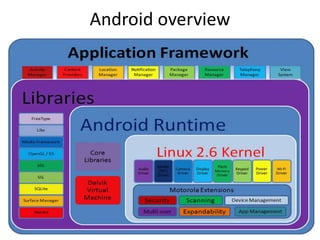
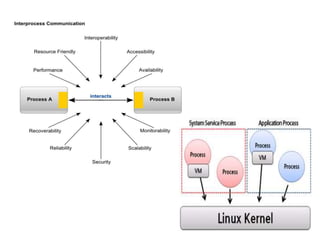
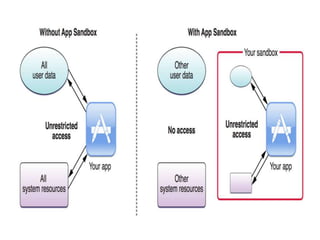
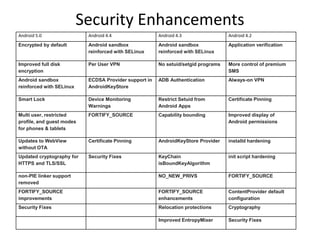
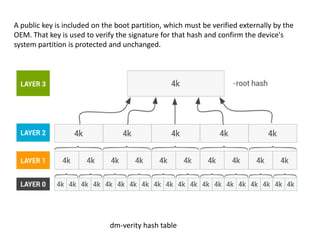
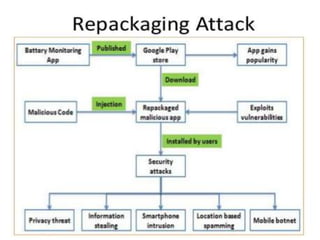
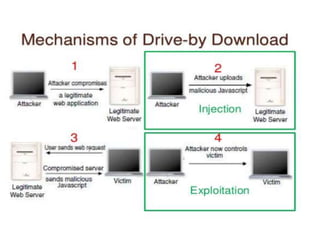
The document discusses various aspects of Android security. It covers kernel security features like process isolation and permissions. It describes how the application sandbox isolates apps and assigns unique IDs. It also discusses system security mechanisms like encryption, verified boot, and updates. Common Android vulnerabilities are outlined like rooting, repackaging apps, update attacks, and drive-by downloads.