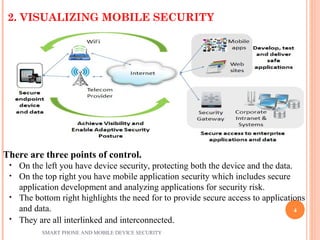
The document discusses smartphone and mobile device security, highlighting significant security challenges such as theft, malware growth, and the vulnerabilities of mobile applications. It explores what data smartphones collect and share, the various threats posed by hackers, government agencies, and thieves, and emphasizes the need for effective countermeasures like authentication and user awareness. Best practices for enhancing mobile security are also outlined, including using passwords, installing trusted apps, and regularly updating systems.