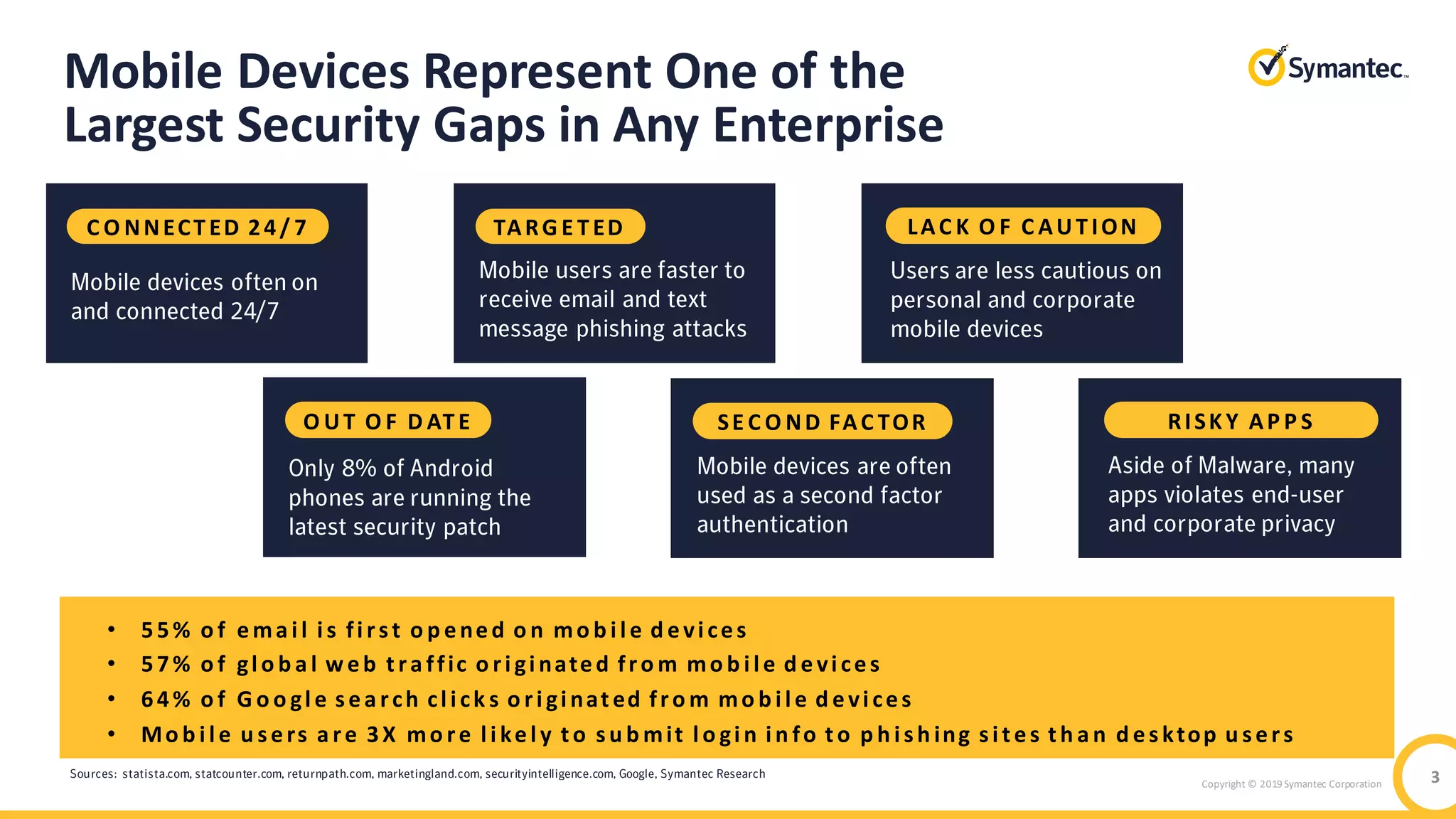
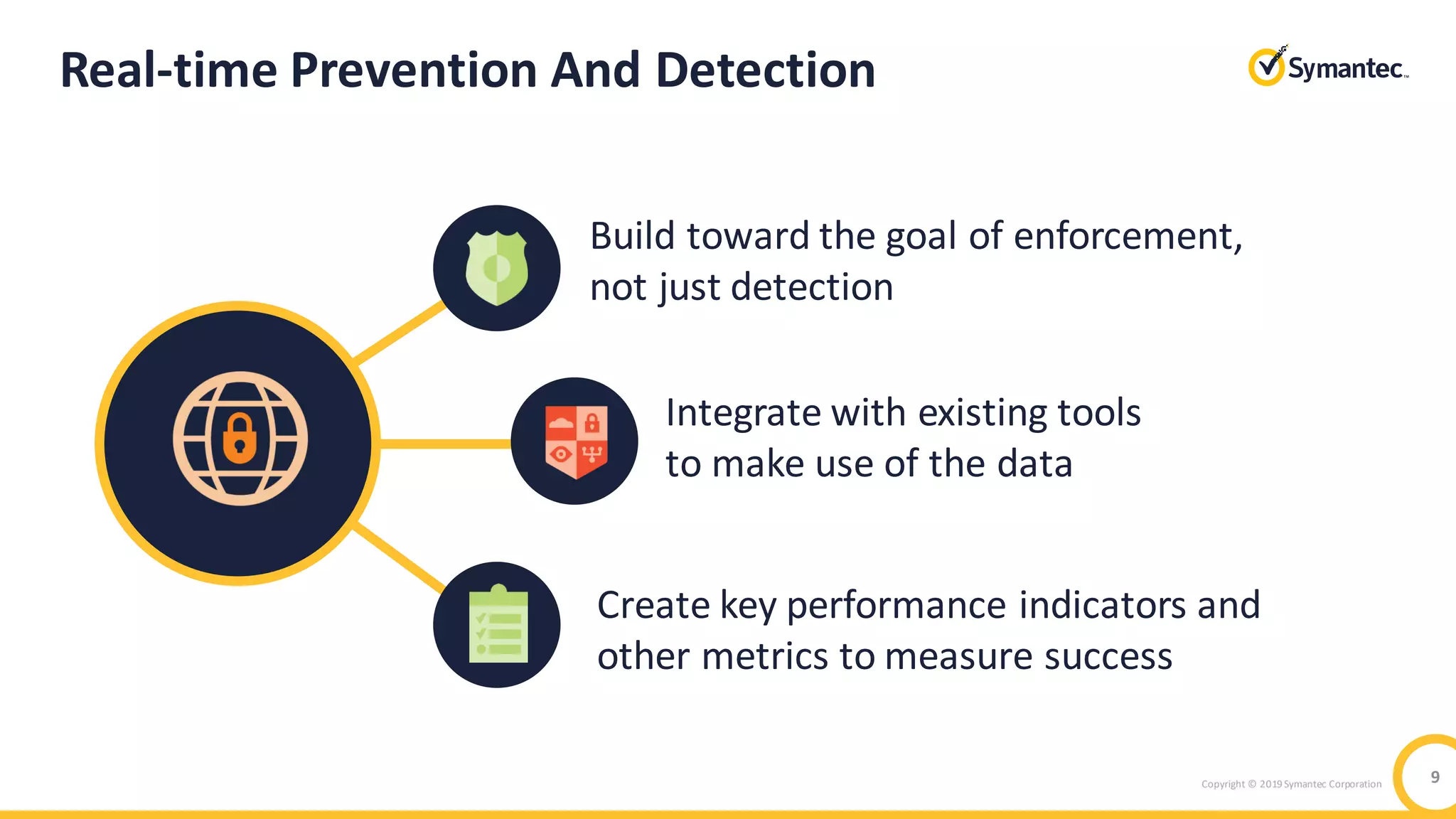
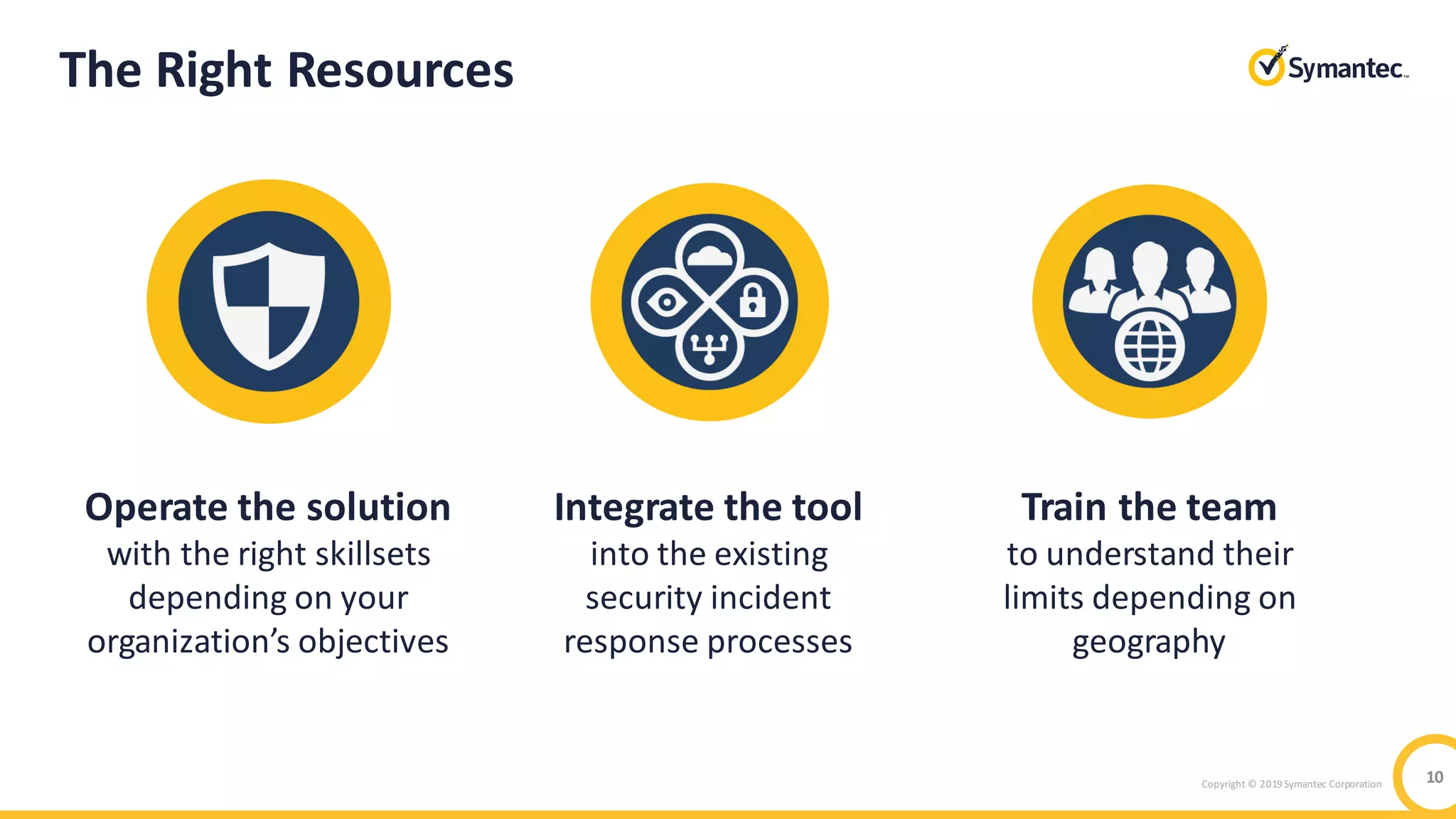
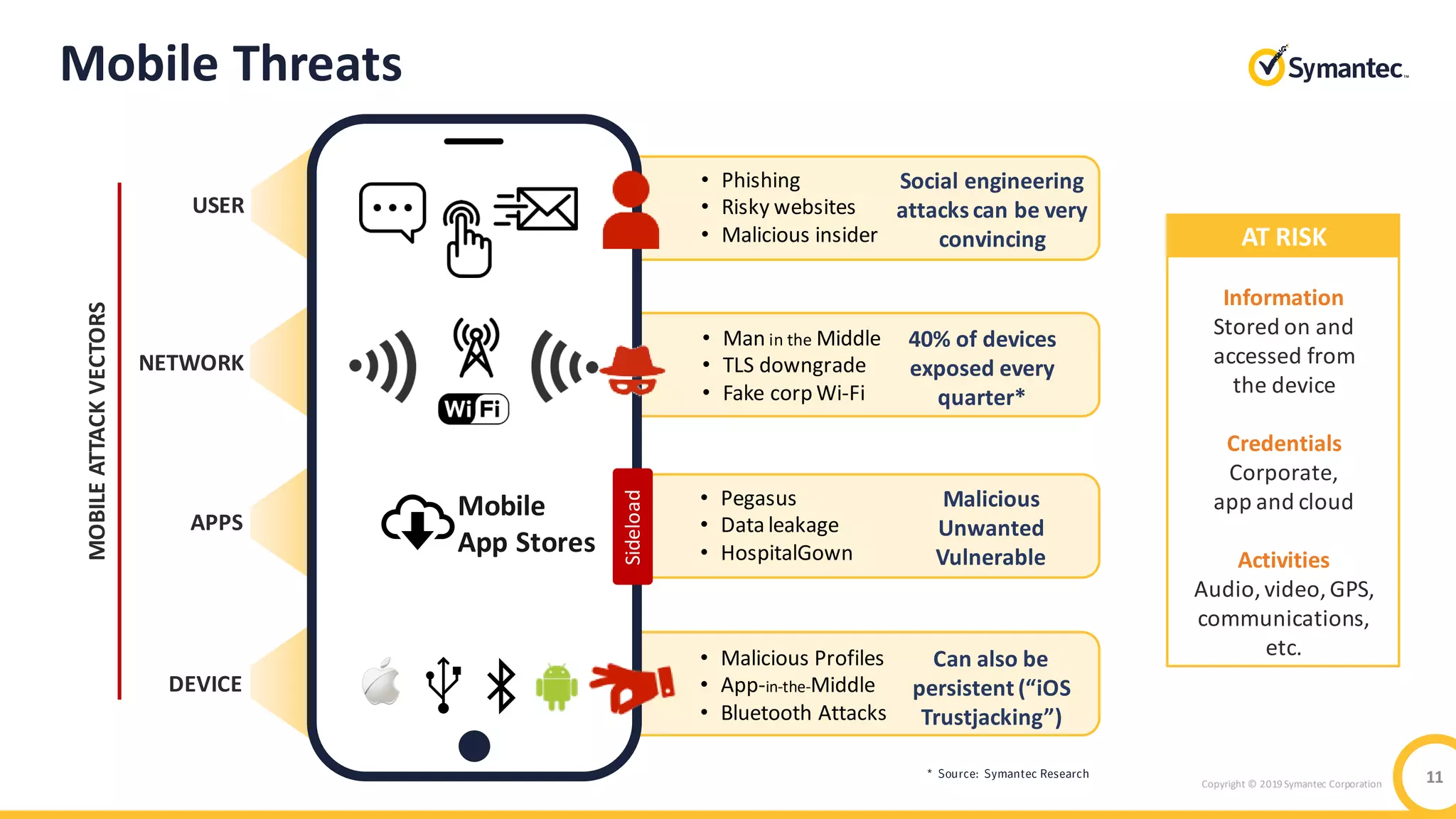
The document discusses the significant security risks mobile devices pose to enterprises, citing statistics on mobile usage and vulnerabilities. It emphasizes the need for a comprehensive mobile security strategy that includes building user awareness, securing both managed and unmanaged devices, and integrating real-time prevention measures. It also highlights Symantec's mobile security solutions and their effectiveness in protecting against various mobile threats.









![Copyright © 2019 Symantec Corporation 15
Holistic, Layered
Mobile Security
On-Device
Protection
Unparalleled
Mobile Research
(9 high severity
discoveries)
Public App
Crowd-sourced
Threat
Intelligence
“SEP Mobile provides advancedon-
device protectionand enforcement
techniques withnodependency on EMM
integration— criticalfor covering all
customers'endpoints.”
- IDC MarketScape:WorldwideMobile
ThreatManagementSoftware2018-2019
Vendor Assessment
Competitor 1
Competitor 2
“[SEP Mobile]has identifiednumerous
malware instances inthe past,whenother
solutions simply did not detect anythreats
on the device.”
Full capabilities on both iOS & Android with or
without EMM/MDM
SEP Mobile Market Leadership](https://image.slidesharecdn.com/symantecmobilesecuritywebinar-190816191728/75/Symantec-Mobile-Security-Webinar-15-2048.jpg)


