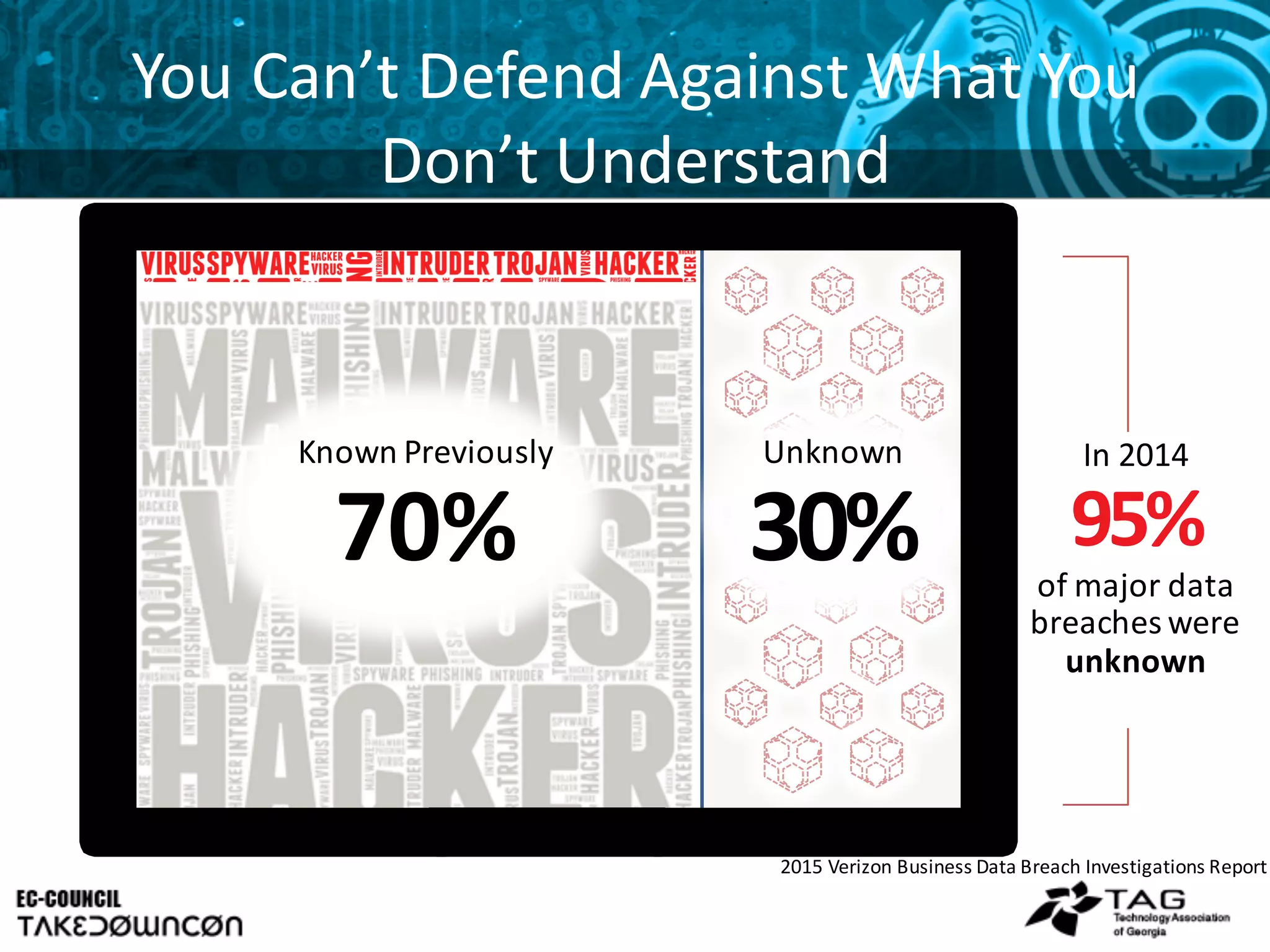
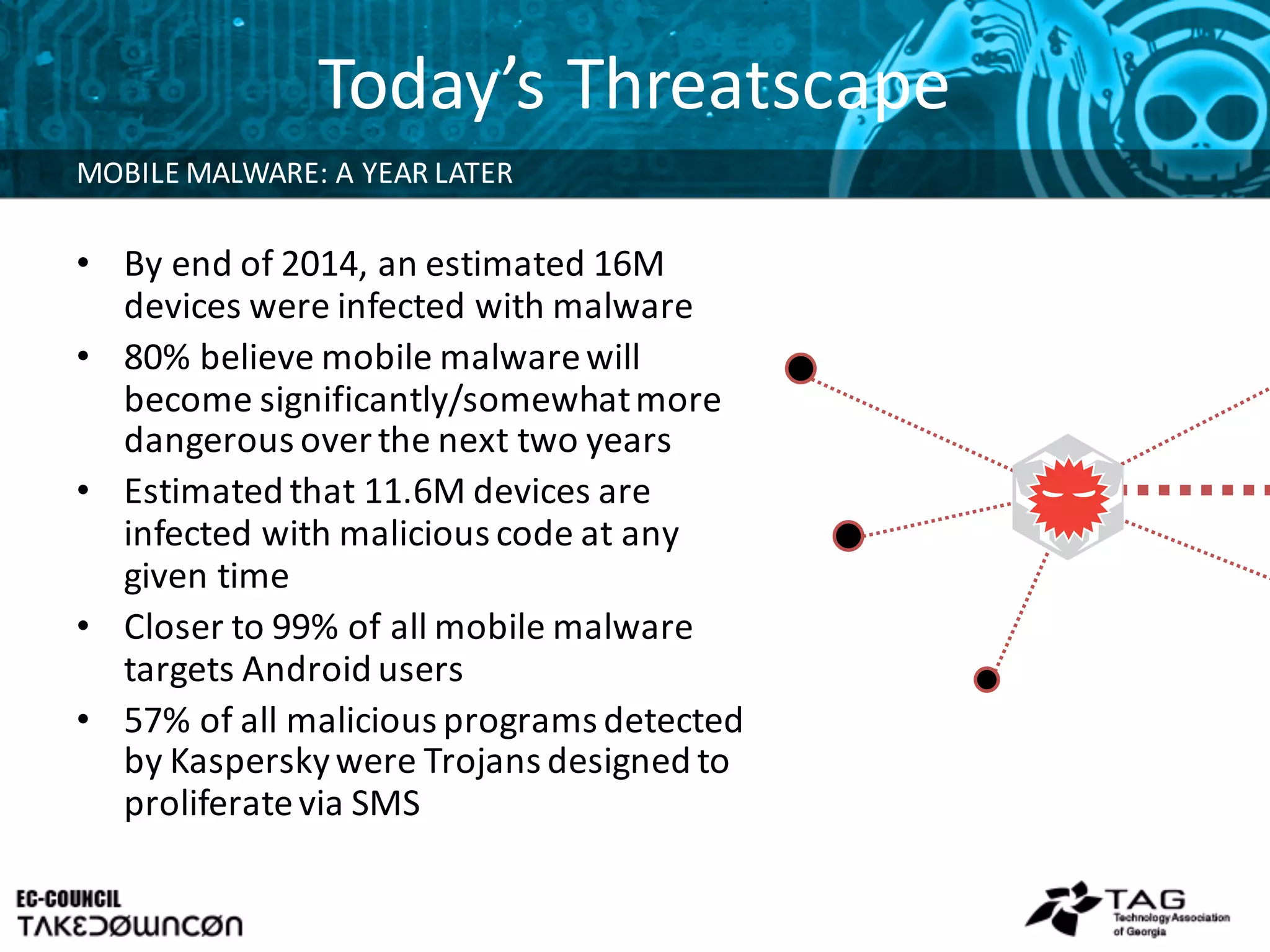
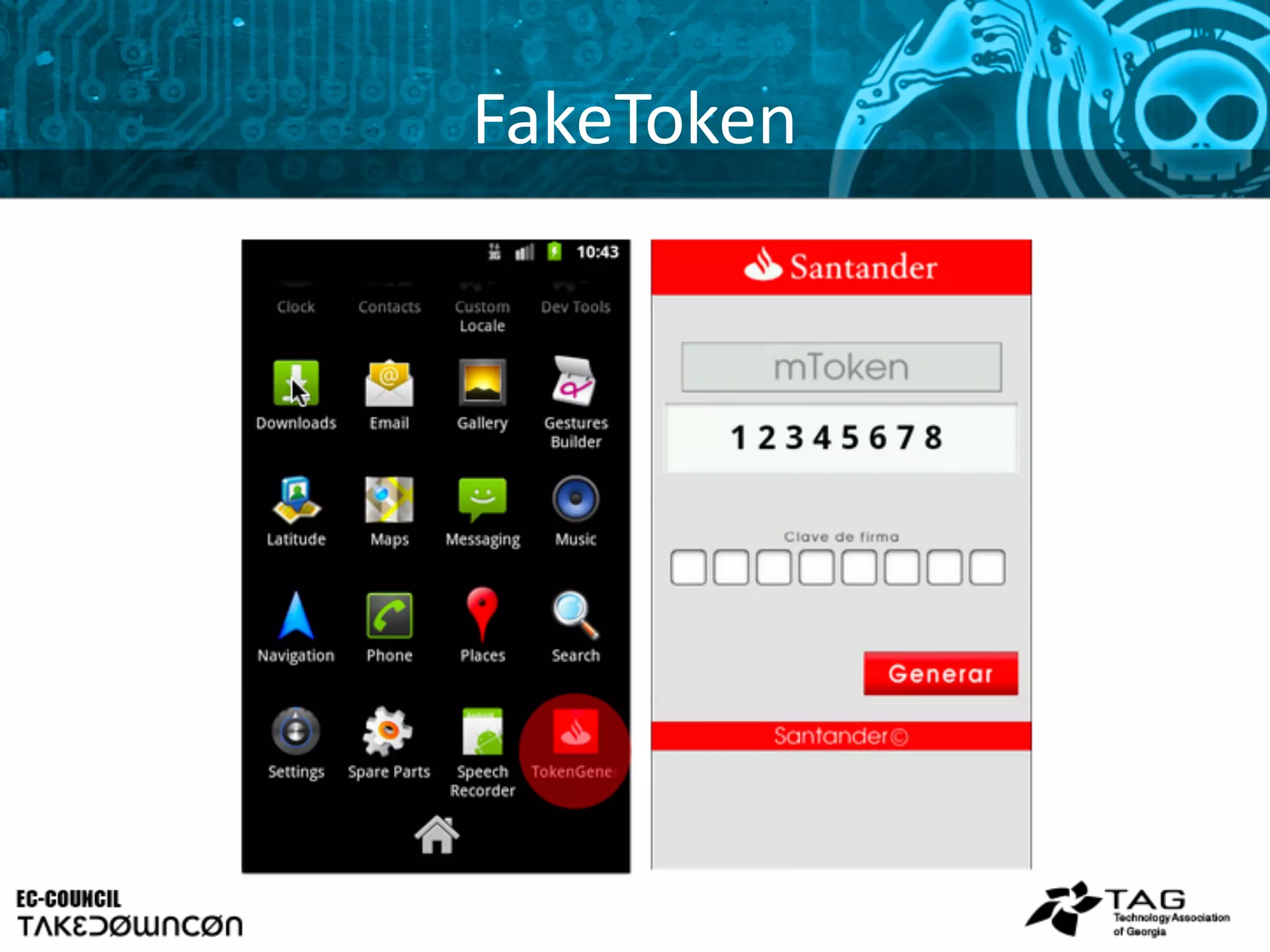
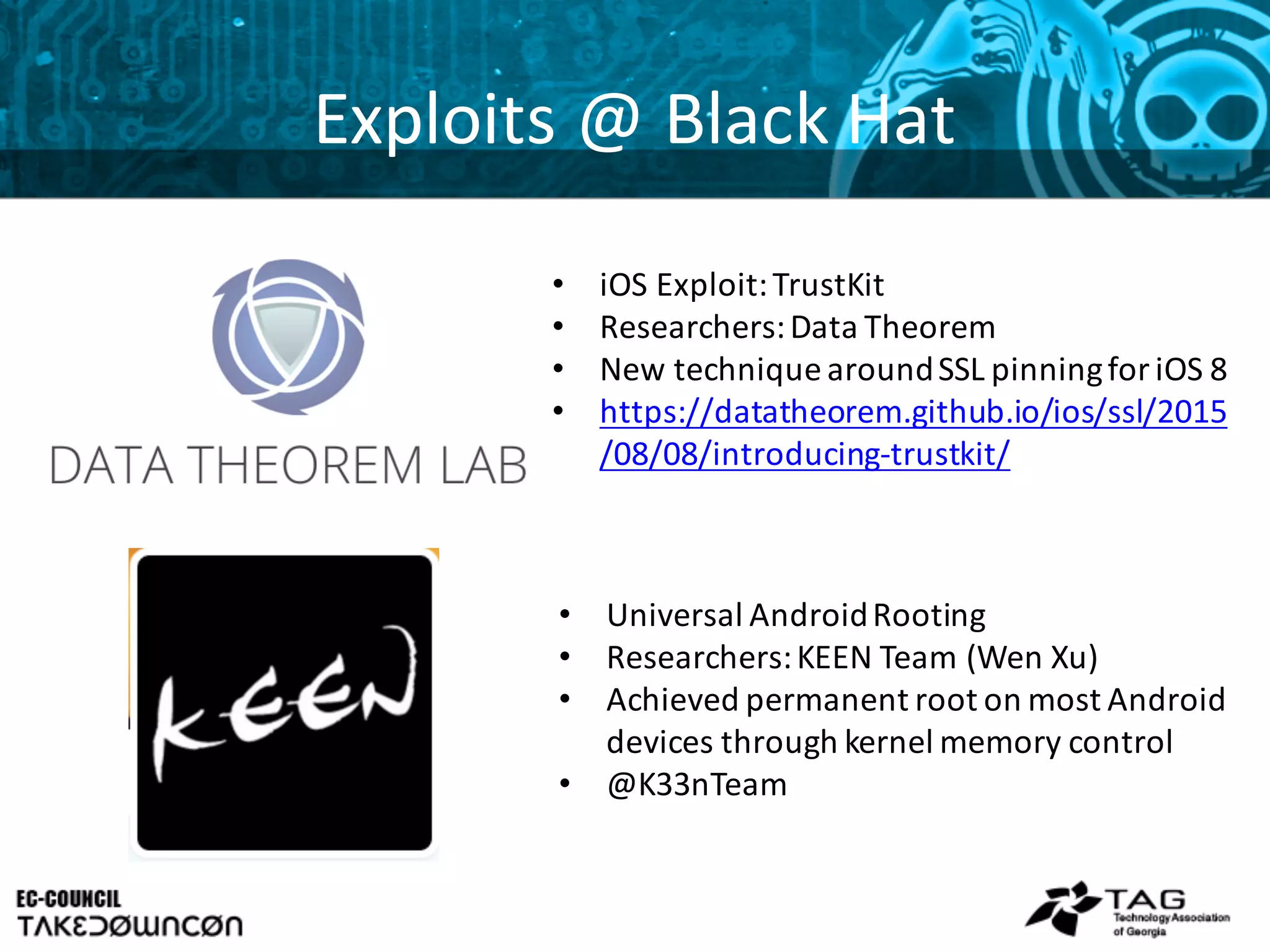
This document discusses emerging trends in mobile security and provides steps to improve mobile security. It notes that mobile threats are becoming more sophisticated and pervasive as mobile adoption increases in enterprises. Common mobile exploits like StageFright and FakeToken are outlined along with their impacts. The document recommends seven steps to tackle mobile security, starting with assessing risks, examining BYOD challenges, and determining appropriate access controls and roles.