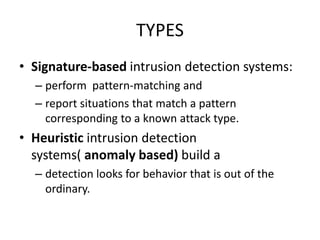
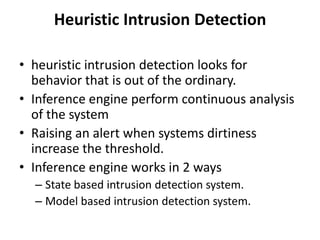
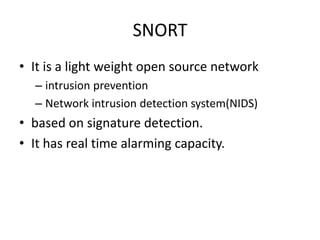
The document discusses intrusion detection systems (IDS) as a crucial layer of security to identify malicious activities that may bypass firewalls. It outlines different types of IDS, including signature-based and heuristic systems, their strengths and limitations, and various approaches for detecting and responding to attacks. Additionally, it highlights tools like Snort for monitoring network traffic and managing alerts.