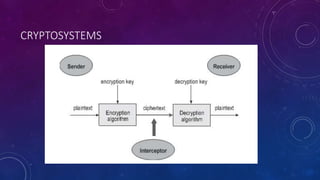
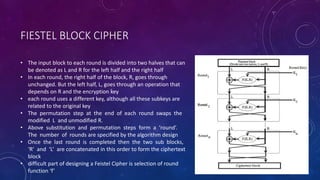
The document summarizes security issues related to e-commerce and encryption techniques. It discusses concepts like confidentiality, integrity, availability, authenticity, non-repudiation and describes encryption methods like SSL, digital signatures, and message authentication codes. It also covers encryption techniques like symmetric key encryption using DES/3DES and asymmetric key encryption using RSA cryptography. The document is presented by a group consisting of 5 members and contains details of security issues, encryption standards and methods.


























![TYPES OF CRYPTOSYSTEMS [1. SYMMETRIC KEY ]
Examples: Digital Encryption Standard(DES), Triple- DES(3DES), IDEA and TWOFISH](https://image.slidesharecdn.com/encryptiontechniques-180329025933/85/Encryption-techniques-31-320.jpg)


![TYPES OF CRYPTOSYSTEMS [2. ASYMMETRIC KEY]
• Different keys are used for encrypting and
decrypting the information
User have 2 dissimilar keys mathematically
related called private key and public key
Public key –public repository
Private key –well guarded secret
When Host1 needs to send data to Host2,
he obtains the public key of Host2 from
repository, encrypts the data, and transmits
Host2 uses his private key to extract the plaintext.
o Length of keys is large so slower
o Processing power of computer system required to run asymmetric algorithm is higher](https://image.slidesharecdn.com/encryptiontechniques-180329025933/85/Encryption-techniques-35-320.jpg)