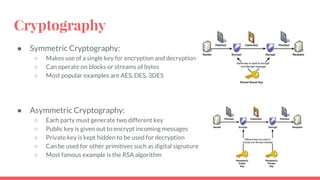
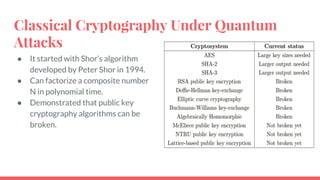
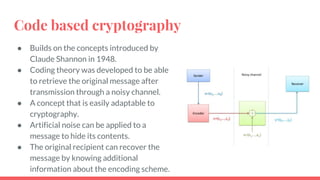
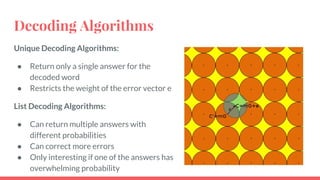
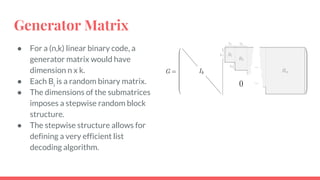
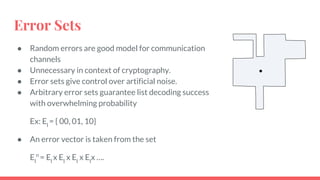
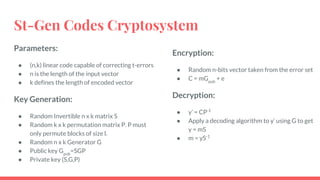
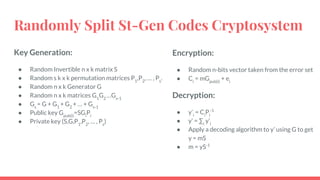
This document discusses post-quantum cryptography and code-based cryptosystems as an alternative that is secure against quantum computers. It describes the McEliece cryptosystem, which uses error correcting codes, and introduces staircase generator codes and randomly split staircase generator codes to improve efficiency and security. The randomly split staircase generator codes cryptosystem allows for both encryption and digital signatures using efficient procedures while providing 80-bit security levels against quantum attacks, though it has large key sizes of around 10 megabytes.