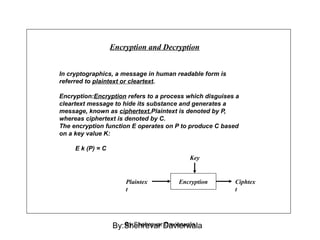
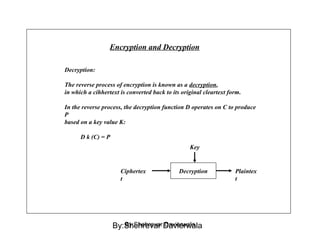
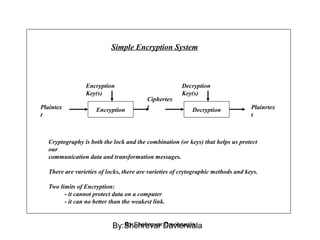
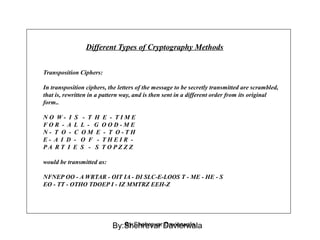
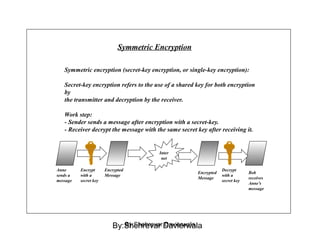
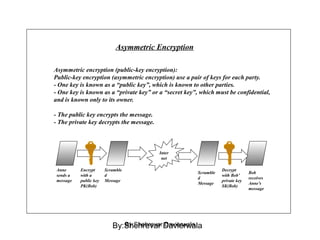
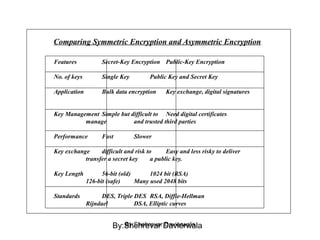
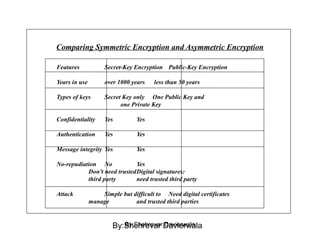
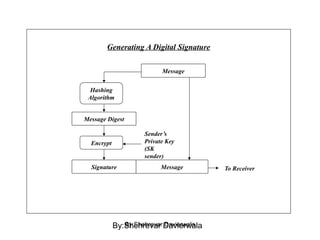
Cryptography is the science of keeping communications secure through various encryption techniques. There are two main types: symmetric encryption which uses a shared secret key for encryption and decryption, and asymmetric encryption which uses a public/private key pair. Symmetric encryption is faster but more difficult to implement for multiple parties, while asymmetric encryption using algorithms like RSA enables easy key distribution and digital signatures.