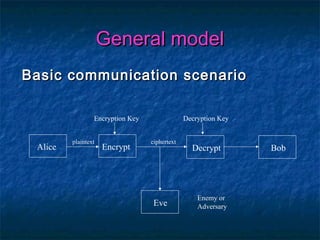
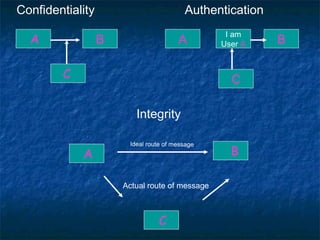
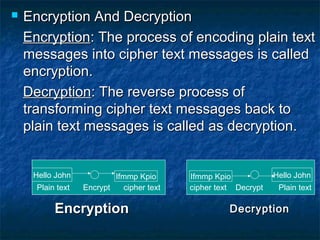
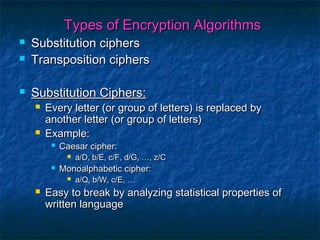
The document discusses cryptography and the RSA encryption algorithm. It begins with an introduction to cryptography and its uses. It then covers the history of cryptography, common security issues, and different cryptographic techniques like symmetric and asymmetric encryption. The document focuses on explaining the RSA algorithm, how it works using public and private keys, and why factoring large numbers makes RSA secure. It provides an overview of the key aspects of cryptography and the RSA algorithm.