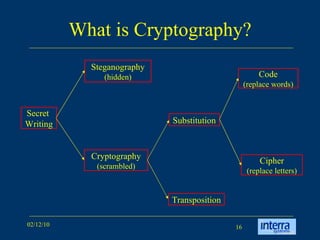
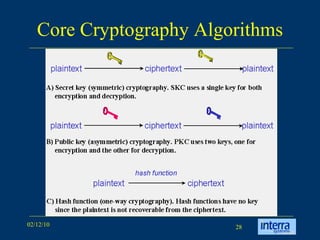
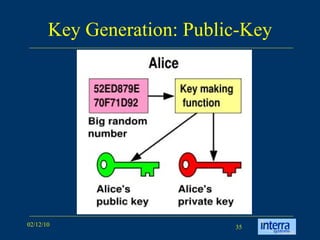
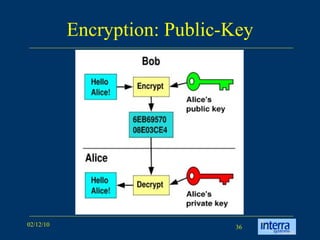
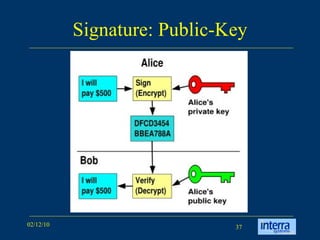
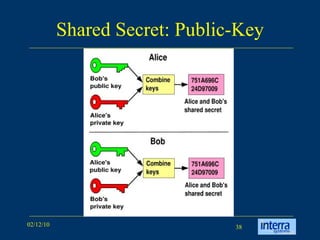
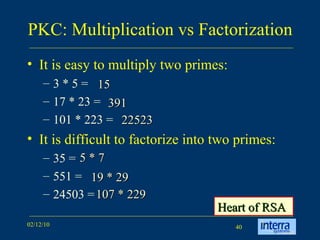
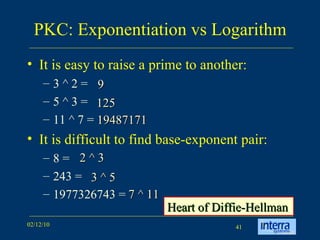
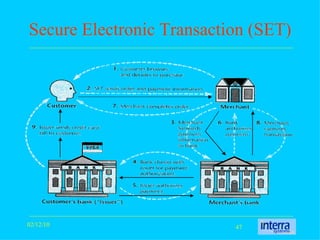
The document provides an extensive overview of cryptography, explaining its significance, techniques, and applications in modern communication. It covers basic concepts such as encryption and decryption, types of cryptography like symmetric and asymmetric, and notable historical ciphers such as the Caesar cipher. Additionally, it discusses practical uses of cryptography, including secure transactions, authentication, and hash functions, along with references for further reading.