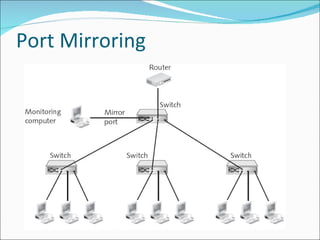
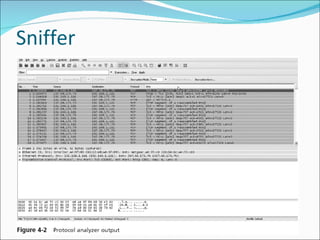
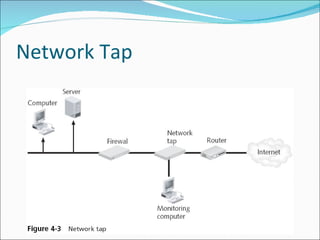
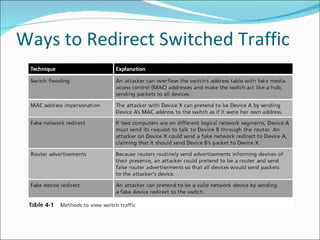
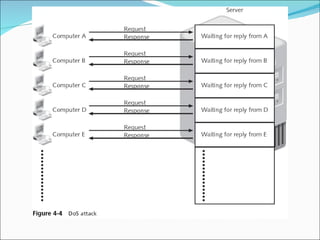
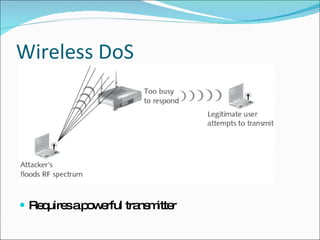
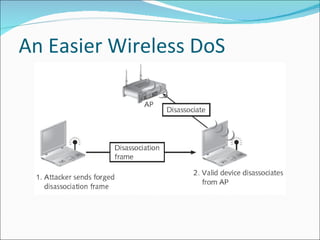
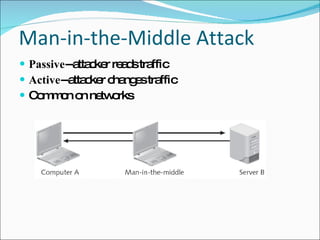
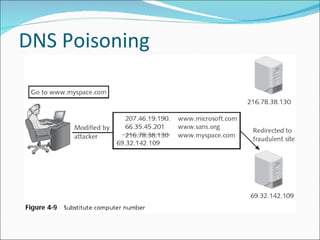
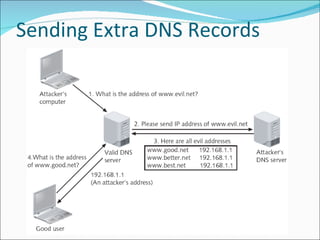
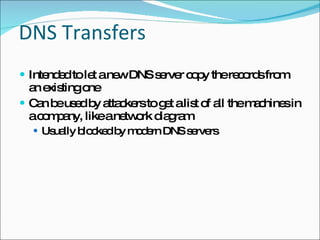
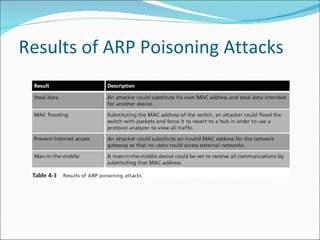
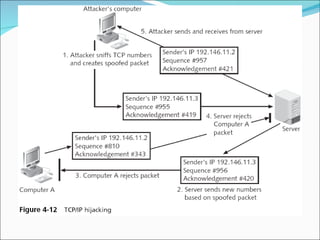
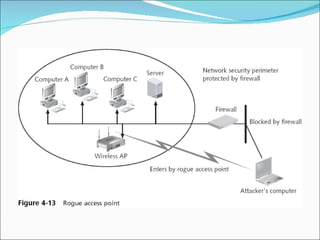
Chapter 4 discusses various network vulnerabilities and attacks, highlighting incidents like the 'Titan Rain' cyberattacks and the DDoS attack on Estonia. It covers methods of attack, including password vulnerabilities, denial of service (DoS), spoofing, and DNS issues, along with techniques attackers use to exploit weaknesses in network protocols. Additionally, it addresses countermeasures, such as using strong passwords and updated DNS server software to mitigate risks.