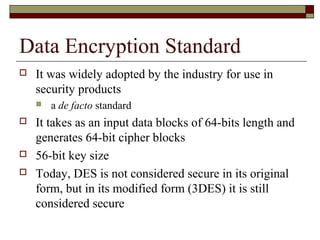
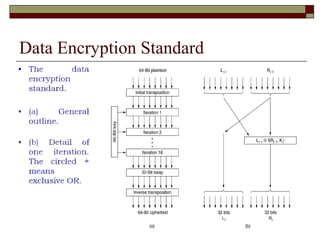
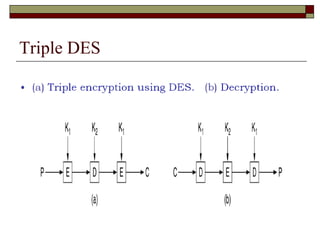
Encryption techniques like AES and Triple DES are used to secure data transmission over networks. AES encrypts data in blocks using symmetric encryption with variable key lengths up to 256 bits, making it more secure than older standards like DES with only a 56-bit key. Triple DES applies the DES algorithm three times with two or three keys, strengthening security compared to single DES. Stream and block ciphers differ in whether they encrypt data bits or blocks at a time.