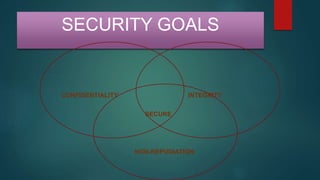
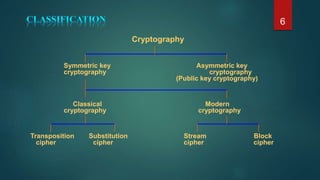
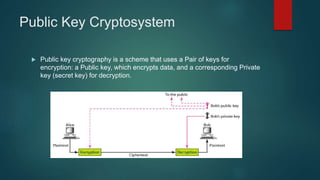
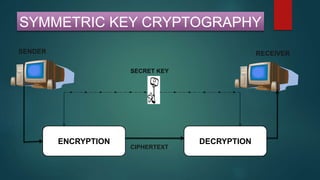
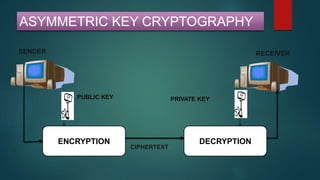
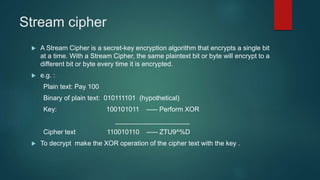
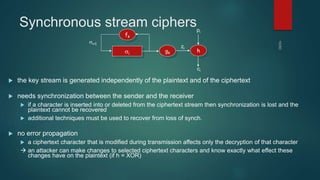
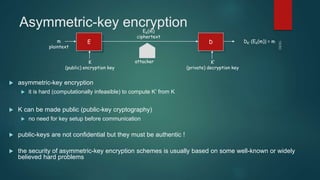
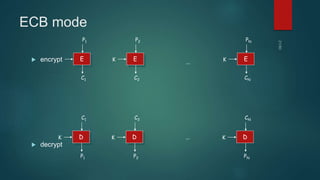
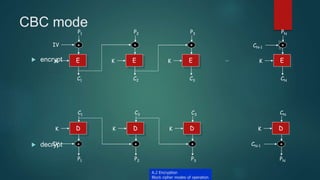
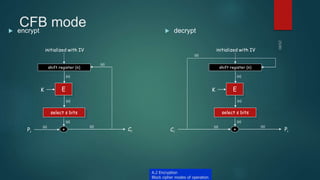
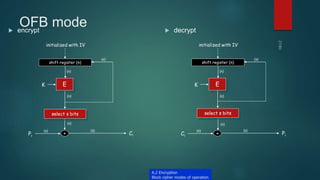
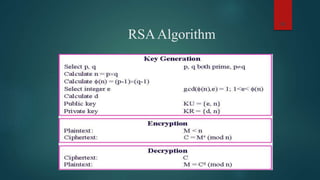
The document provides information about encryption and decryption techniques. It defines encryption as converting plaintext into ciphertext and decryption as converting ciphertext back to plaintext. It discusses symmetric encryption which uses the same key for encryption and decryption, and asymmetric encryption which uses public/private key pairs. Specific symmetric algorithms like DES and AES are covered as well as the asymmetric RSA algorithm. Different block cipher modes of operation like ECB, CBC, CFB and OFB are also summarized.