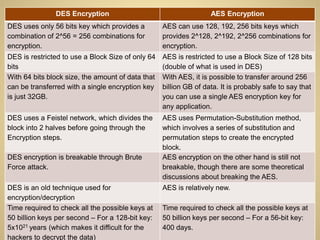
Cryptography involves encrypting data to hide its meaning. Encryption converts plain text into unintelligible cipher text using an algorithm and a key, while decryption reconverts cipher text into plain text. Symmetric key cryptography uses the same key for encryption and decryption, while asymmetric key cryptography uses different public and private keys. Common symmetric algorithms are DES, which uses a 56-bit key, and the more secure AES, which allows 128-, 192-, or 256-bit keys and a larger 128-bit block size. AES is considered more secure than DES due to its larger key sizes and stronger algorithm.